Articles in Category: Security
They Set Up My Computer and Now My Ex Is Spying on Me. What Can I Do?
Trust is tricky when it comes to computers. When you add relationships to the mix, things quickly get complicated.
How Should I Password-Protect an External Hard Drive?
You want more than a password; you want encryption. Encrypting an external drive can be done with the right software.
How Do I Pick the Right Tools to Protect Windows?
There are many software programs that protect your system. I’ll review how I make my decisions and give you my advice.
What is a Digital Fingerprint?
Digital fingerprints are another way that websites might track you, should they want to. What can you do? Should you be worried?
What Is Smishing?
Smishing is simply text-messaging spam. Learn to recognize and respond appropriately to it.
I Got a Pop-Up Virus Warning. Is My Computer Infected?
Messages that indicate you have a problem and recommend a specific download as a solution are immediately suspect.
What is End-to-End Encryption?
If you’re sharing private or sensitive information, end-to-end encryption is an important term you need to understand.
Should I Clear Cookies Before I Travel?
Clearing cookies is an annoyance, but it protects your online accounts in case your machine is stolen.
Why Did My Security Software Not Detect a Virus on My PC?
Even with up-to-date anti-malware tools, you can still fall victim to malware. I’ll explain why by comparing your computer to your… bathroom?
Preparing Your Technology for Travel Abroad
Travel is exciting, but be sure to plan ahead for your technology to avoid things going wrong.
What You Need To Do About the LastPass Hack
A portion of LastPass was breached. Here’s why it’s not a disaster, and why I’m not leaving LastPass.
The Biggest Risk to Your Security
The biggest risk to your security might just be you. Learn why and what to do.
How Can I Protect Myself From Scams?
Scams are everywhere, it seems. I’ll cover some common ones, and share the single most important rule to protect youself.
Can a Data Breach Expose Multiple Accounts?
Data breaches rarely expose multiple accounts. There are rare scenarios where multiple accounts might still be at risk, though.
6 Reasons There Are Still So Many Security Breaches
When you think about the complexity of today’s systems, it’s kind of amazing that we don’t have more breaches.
If I Leave My Computer Always On, Am I More Likely to Be Hacked?
Leaving your computer on 24 hours a day rarely increases risk significantly, as long as you follow a couple of simple guidelines.
How Can I Delete an Old Account If I Can’t Log In?
If you’ve lost your password, there may be recovery steps. If you’ve also lost your email address, recovery becomes significantly more difficult.
I Lost My Phone With My Second Factor for Authentication. How Do I Recover?
My phoned died, and with it, all the two-factor authentication methods I’d used it for. Here’s how I recovered.
LastPass Password Manager and Vault
One of the challenges with current online safety advice is keeping track of multiple different secure passwords. LastPass not only does that, but does it securely across multiple devices.
I’m Told to Change My Password. Why?
If you’ve been told to change your password, do so, but do so in the right way. I’ll explain what that means and why it’s important.
Lock Your Computer When You Walk Away
If your device is not physically secure, neither the machine nor your data is.
Can Malware Infect Other Computers on My Network?
There are forms of malicious software that attempt to travel from machine to machine on your local network. There’s good news, though.
How Was My Bank Account Hacked When I Did Everything Right?
Even with all the right things in place, stuff happens. I’ll review the additional steps you can take to protect yourself.
Lost Gmail Account Recovery With No Phone or Alternate Email
The Google Account Recovery process may be able to help you get your account back. Maybe.
Protecting Your Privacy: Points of Vulnerability
Tracing the privacy and security of the path from your fingertips through the services you use to your information’s final destination.
How Do I Scan Nuclear Power Station Computers Without an Internet Connection?
Scanning your nuclear power station’s Windows computers for malware can present some challenges if the machines have been secured properly.
Would You Please Recover My Password?
Every day, I’m asked to reset lost passwords, recover hacked accounts, or retrieve lost information in them. Here’s my answer.
How Do I Prevent a Repeat of Ransomware?
All malware is scary, especially ransomware due to the damage it can inflict. Here’s how to avoid a repeat performance.
What VPN Should I Use?
VPNs protect from certain types of surveillance and more. I’ll discuss what they’re good for and what to consider when selecting one.
Am I Safe?
There is no such thing as absolute safety. But there are definitely steps you can take to be as safe as possible.
Someone Is in My Computer, Controlling it. What Can I Do?
When things behave unexpectedly, many people assume their computer has been compromised by remote hackers. Many of those people are wrong.
Is a Password-protected Windows Login Secure?
Your Windows log-in password gets you surprisingly little real security. I’ll look at why that is, why you might still want one, and what I do instead.
Why Your “Unimportant” Accounts Matter
Regardless of your initial thoughts, every account is important, and we are all targets.
How Do I Run a Full Scan Using Windows Defender?
A full scan scans things a more common “quick scan” bypasses. Here’s how to run one using Windows Security.
My Machine’s Full of Malware; Should I Get a New Computer?
For some reason, many people’s gut reaction to a malware infestation is to consider getting a new computer. That’s unnecessary.
How Hackers Use Malicious Attachments to Give You Malware
Another day, another report of hackers exploiting vulnerabilities. Here’s how you stay safe.
Will Using a Password Vault Thwart a Keylogger?
A password tool may bypass a few keyloggers, but not all. Think about your overall computer and account safety first.
What Do I Do If I’m Being Harassed, Bullied, or Stalked Online?
Online harassment is common problem, and prevalent among children. I’ll review some of the issues and steps to be taken.
Is Passwordless Authentication Safe?
Passwordless authentication removes the need for a password and replaces it with something else. But can that be secure?
What’s the Best Anti-Virus?
There just isn’t a best. Knowing that will (hopefully) lead you in a safer direction.
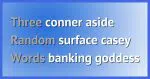
Do Random Words Make Better Passwords?
As few as three random words make better passwords than strings of random characters — but not, perhaps, for the reasons you think.
Responses to Your Three Common Password Manager Objections
Password vaults are a common recommendation by security professionals to improve your online security. Why do so many resist?
A Data Breach Has My Data. What Do I Do?
Data breaches are everywhere but what should you do if your info shows up in one? I’ll break down the risks, explain what really matters (hint: it’s not just your email), and give you steps to protect yourself. Don’t panic, but do get informed and stay safe.
How Should I Wipe My Hard Drive in Windows Before Giving It Away?
Erasing your hard drive before you give it away is important. Exactly how thorough an erase you need depends on your data and level of paranoia.
How Do Websites Keep Passwords Secure?
A high-level overview of how websites and services should store passwords security, so next time there’s a breach you’ll know what to look for.
Find Your Lost Bitlocker Recovery Key in Your Microsoft Account
BitLocker might be turned on without your knowledge. That’s fine, but make sure you have the recovery keys stored somewhere should you ever need them.
How Do I Access the Computer of Someone Who’s Passed Away?
If no preparations have been made beforehand, accessing the machine of a deceased loved one can be anywhere from easy to impossible.
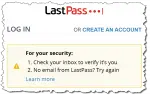
No Email from LastPass? Dealing with Sign-In Problems
While travelling, I signed in to my LastPass account only to be told I needed to confirm an email message that never arrived — or so I thought.
What if I Forget My Passwords If I Use Two-Factor Authentication?
Two-factor authentication is different than passwords, but they both share important recovery steps if there’s a problem.
How Do I Safely Back Up an Infected Drive?
Once your machine is infected, system backups are likely to include the infection, but are still important. I’ll look at what steps to take.