Articles in Category: Security
What Should I Do About the Latest Breach?
Yet. Another. Breach. Don’t panic, I’ll walk you through what you really need to do next. From checking if you’ve been exposed to strengthening your account security, it’s all here in simple terms.
How to Share Two-Factor With Another Person
Two factor authentication is one of the most important things you can set up to protect your accounts. Even so, it’s possible to share certain 2FA types with multiple authorized people. I’ll show you how I do it.
How to Run a Full Scan Using Windows Security
Here’s my step-by-step guide on how to run a complete malware scan using Windows 10 and 11’s built-in Windows Security.
Two-Factor Authentication: It’s Not as Complicated as You Think
There are some persistent myths about two-factor authentication that stop people from adopting it. I’ll clear them up so you can use this simple yet powerful security feature with confidence.
I Run Security Software. Why Do I Still Sometimes Get Infected?
Any security software can miss something, no matter how good. It’s important to understand why this is and what you can need to about it.
Size Matters! (When It Comes to Passwords)
The results are in for last year’s most common passwords. The implications are depressing.
Passkeys and Hardware Keys
Passkeys and hardware authentication keys are completely different but partially related. You can use some, but not all, hardware keys as passkeys. I’ll clear up the confusion, and tell you what to look for.
What Is a Passkey?
Passkeys are a new form of signing in that promise to be easier and more secure. I’ll walk you through some of the high level concepts and how they work, and how they keep you safer than passwords.
How Can I Securely Delete Everything Except the Operating System?
Before giving away a machine or returning a loaner, it’s important to remove your personal information from it. That may be both harder and easier than you think. I’ll show you where traditional suggestions fail, and what you need to do instead.
Is Internet Provided by My Landlord Safe?
Connectivity is becoming an added perk in some housing situations. Make sure you know the risks and alternatives when someone else provides your internet connection.
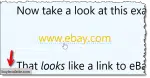
How to Hover Over a Link to Check It’s Not a Scam
When it comes to links on webpages and HTML email, what you see is not always where you go. Hovering over a link is an important technique to look before you leap.
How End-to-End Encryption Protects Your Messages and Where It Fails
You would think that for such an important concept as end-to-end encryption there’s be some agreement on exactly what it means. Sadly, not so. There’s the correct definition, and then there’s the marketing definition. One protects you, the other not so much.
Many Ways Your Account Can Be Hacked and What to Do About It
There are many ways accounts can be compromised. There are also many simple ways you can protect yourself.
Can You Really Know Your PC Is Clean and Malware-Free?
It’s common to want confirmation your machine hasn’t been compromised in some way. We can get close, but we can’t prove it.
Passkeys Are Never the Only Way In
Losing a device with a passkey to one of your accounts will not lock you out.
How Does Security Software Protect Me After Windows 10 End of Support?
Security updates and security software have different jobs, and that difference matters.
How Do I Know If My Hard Disk Is BitLocker-Encrypted?
Your hard disk could be BitLocker encrypted without your knowledge.
Protecting Your Data: Why I Avoid Most Pre-Installed Security and Encryption Software
External hard drives often come with security and backup software. I’m not convinced it should be used.
BitLocker vs. Cryptomator: Why I Use Both (and When You Should, Too)
Use different tools for different purposes.
What Happens If I Lose My Microsoft Authenticator App?
Microsoft Authenticator is not necessarily two-factor authentication, but the two do share one important characteristic: the need to prepare for loss.
Does a VPN Protect Me From Telemetry and Other Data Gathering?
VPNs don’t impact data tracking or collection. We’ll look at why that is and what you might want to do about it.
Cryptomator vs VeraCrypt: Which Do You Want?
Cryptomator and VeraCrypt are both excellent encryption tools. We’ll look at how to choose the right one for your situation.
How to Back Up 1Password and Why You Should
Backing up is important, and that includes your password vault.
Should I Always Sign Out of My Online Account?
It is safe to stay signed in to your online account as long as you’re protected from a few specific scenarios.
Do Not Search for Support Phone Numbers
You want a phone number to call. Scammers known this and try to insert themselves in the process.
Think Before You Share: Protecting Yourself From Email Harassment
It’s so common to give away personal information, we don’t think twice about it. Let’s start thinking twice.
How to Recover When You Lose Everything Traveling
Imagine you’re traveling overseas and all your digital “stuff” is lost. What do you do? How do you reconnect?
Does Turning a Computer Off at Night Keep It Safer From Hackers?
There are reasons to turn your computer off at night or leave it running. Getting hacked isn’t one of them.
How Do I Make Sure Malware is Gone?
Of course we want to be certain malware has been removed. Unfortunately, certainty is difficult to come by.
More Tips to Protect Yourself from AI Scams
AI has entered the chat. And the email. And the voice call. And the video. And it’s making scams even harder to detect.
Online and Phone Scams: What to Watch For and How to Stay Safe
Know the characteristics of online and phone scams, and don’t be afraid to take steps to protect yourself.
Why Do Services Like Google and Microsoft Ask for a Phone Number?
Many online services request your phone number. I’ll look at how that’s typically used and why it’s a good thing.
Secure Your Most Important Accounts
Experts always recommend securing your “most important accounts”. Great. Which accounts would those be?
Why Your Computer Has Probably Not Been Hacked
I regularly hear from people who believe their computer has been hacked and is under someone else’s control. It’s very rarely the case.
Think 2FA Is Bulletproof? Here’s Why You’re Still Vulnerable
Two-factor authentication is one of the most important ways you can secure your online accounts. But that doesn’t mean you’re done.
How AI is Revolutionizing Scams: Can We No Longer Trust Our Eyes or Ears?
Scams are bad enough. Throw AI into the mix, and things only get worse.
Why Encryption Backdoors Are a Horrific Idea
A phrase we’ve heard more and more often in recent years is encryption backdoor. The concept is simple: government agencies want to be able to monitor otherwise encrypted communications. The concept is flawed.
How to Add Two-Factor Authentication to Your Google Account
Adding the most common and secure form of two-factor authentication to your account.
Is Automatic Sign-in Safe for My Email?
Having your email automatically or continually signed in to can be a security risk in some situations, but very convenient in others.
Going Passwordless Without Going Passwordless
Passwords are dying. On some services, you can start playing with the process by creating a secure password… and then forgetting it.
What Security Software Do You Recommend? (2024 Q4 update)
Here are my latest recommendations for specific security software and techniques.
Is a Periodic Password Change a Good Thing?
Conventional wisdom says to change your passwords periodically. I disagree.
What Is Ultra AV, and Why Did it Show Up On My Machine?
If you’ve suddenly found an unfamiliar antivirus program running on your computer, you’re not alone.
Is My Smartphone or Smart Device Listening In on Me?
It’s not uncommon to think our smart devices are listening in when advertisements seem to follow our discussions.
Is a Passkey Two-Factor Authentication?
Passkeys are secure, but they’re not two-factor authentication in and of themselves. I’ll run the scenarios that explain why that is and when 2FA might be involved as well.
What If I Lose Everything When Traveling?
I hear from people who are concerned that they’ve put so much security in place they’ll keep themselves out in case of emergency.
Social Security Number Compromised — What to Do?
Billions of records of personal information, including Social Security numbers, has been exposed. What to do?