Proving you’re you without your second factor.

First my laptop, now my phone.
I went to take a photo of my dogs and apparently it was cuteness overload for my Google Pixel 4 XL, because it just shut down the moment I tapped the button.
I forced a reboot and took another photo, which worked. A few seconds later, while viewing the photo, the screen went crazy and the phone started squealing. I forced it off again. It came back one more time, worked for a bit, and then shut down one last time. All further attempts to revive it were unsuccessful.
I was now the proud owner of a Google Pixel 4 XL brick.
The biggest problem? The phone was my second factor for all my multi-factor-enabled accounts — and I was traveling. Could I sign in to my important accounts without it?
Become a Patron of Ask Leo! and go ad-free!

Losing my second factor
Particularly when traveling, losing your second factor for multi-factor authentication can be a problem. For SMS authentication, simply porting your phone number to a replacement phone works immediately. For Google-Authenticator-style authentication, an app like Authy lets you use multiple devices as your second factor. In all cases, it’s important to keep your account recovery and alternate verification methods up to date and ready before you need them.
Two-factor authentication
I’ve long been a proponent of what’s called “two-factor” authentication. The premise is that in addition to your account ID (often your email address) and password — two things you know — you also need to prove that you also have your second factor in your possession. Mobile phones are a common second factor, using either SMS to receive a code, or a smartphone app to generate a code entered when you sign in.
What it all means is that hackers can’t get in to your account, even if they know your password — they don’t have your second factor.
But now, suddenly, neither did I.
Traveling compounds the issue
Most services using multi-factor authentication allow you to say, “Don’t require two-factor on this device” after signing in once successfully with 2FA. The machine itself is “secure enough” not to require two-factor for every sign in thereafter.
I do this with my desktop computer at home so I don’t need two-factor after the first sign-in.1
My laptop is a different story. Since it’s portable and I’m traveling, I need to protect myself from loss or theft. That means I don’t take that shortcut. I require two-factor each time I sign in to accounts I protect with multi-factor authentication.
Without my phone, the very next account sign-in on my computer or tablet posed a problem: I didn’t have my second factor. I couldn’t prove I had the right to get into those accounts.
Fortunately, services have alternatives you can set up beforehand.
Some services make it easy
Google made it easy to sign in using an alternative. It prompted for my second factor as usual, but when I indicated I couldn’t use that method, it gave me the option to use any of several other second factors.
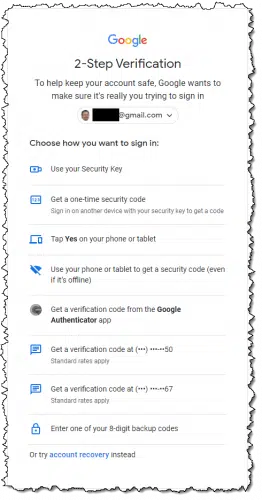
I simply chose one of the other techniques, and I was in.
Many services not only support this, but actively encourage you to set up additional recovery methods when you enable two-factor authentication.
Here’s the catch: just like your account recovery information, you must set this up before you need it.
Once you do, losing your second factor becomes merely an annoyance.
SMS is easy, but…
The appeal of SMS text messaging for two-factor authentication is that it’s tied to your phone number rather than your device. Replace the phone, port the number to the replacement phone, and SMS continues to work.
That portability is also its weakness, since “SIM swapping” is a social engineering technique where hackers transfer your phone number to their device. Fortunately, it’s still relatively rare, and mobile providers know to look for it. More importantly, SMS two-factor remains better than no two-factor at all.
I considered visiting my mobile provider’s local store, where all of this could have happened within a couple of hours. I elected to wait and have a replacement phone delivered to my home on my return.
Google Authenticator
The other approach for two-factor authentication that I recommend over SMS is using Google’s Authenticator app on capable devices. Or rather, using apps compatible with Google’s authenticator app.
I use Authy. The situation I found myself in is exactly why.
You can install Authy on multiple devices, and your two-factor codes are available across all of them. You can use any of these devices as your second factor. While I did not have Authy installed on my laptop,2 I had it installed on my iPad, which I also had with me.
If I needed to sign in to any site that used Google Authenticator for a second factor, I just reached for my iPad instead of my phone.
Do this
Use two-factor authentication whenever it’s available.
Then set up the recovery mechanisms provided by the service. Not only will this protect you in case you lose your second factor, but it’ll also dramatically increase your ability to regain access to your account should you lose it for any reason.
Use my experience above as an example of what you might set up, just in case.
Then, subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: Some services require the second factor periodically, such as every 30 days. If you clear cookies, two-factor will be required on the next sign in.
2: A decision I wrestle with. Even though access to Authy is itself protected by a password or PIN code, having it on the same device that might be stolen seems questionable. And yet, I have it on the iPad…




Just a comment on SIM jacking or swapping. I once received an email at 10 pm on a Sunday confirming an e-transfer if $780 from my bank account which of course I did not do. I immediately called and had to cancel my Visa, close 3 bank accounts and more. Then I received an email from Amazon saying that they had not received the 6TB hard drive that they sent me a replacement for. That happened to be my last Amazon purchase made. Then Air Canada sent an email saying that they had locked down my Aeroplan account due to “suspicious activity”. Yes tey even went after my points!
Long story short, I was somehow SIM jacked. I have a Virgin Canada cell phone account and according to Virgin, they have now locked it down so hard that even I could not switch to a new phone without great difficulty. I never learned how it happened but I did see an example on TV of how a young mom holding a crying baby for sympathy can sweet talk a cell phone customer service rep into reminding her what her password is. I also suspect this info can be grabbed electronically right from your pocket by criminals with the right scanning tools on the street.
If only all services had alternative recovery mechanisms…..
They’re supposed to. In fact I’m not aware of any that don’t. Most commonly people fail to set them up in the first place, OR they don’t update them when things like recover email addresses and phone numbers change.
There are only two (but essential) services I use Google Autbenticator on: GMail, and PayPal. (If I could use it on my bank account and credit card, I would, but neither one accepts that particular form of 2FA.)
As you’ve just pointed out, Google’s alternative options are extensive, so I’m not worried about my GMail access.
PayPal, I’m not nearly so sure of. But they do have my cellphone number, and could verify me that way, if need be. :/
You wrote:
“I was now the proud owner of a Google Pixel 4 XL brick.”
Congratulations! 🙂
I’m still using my Google Pixel 2XL and glad it has lasted longer than your Google Pixel 4!
I allow accounts to “remember” my laptop for 2FA, reasoning that the laptop is encrypted, and therefore unusable without guessing my 18-character password. Far more difficult than the 7-character PIN that unlocks my phone. Am I foolish?
Not foolish. That’s secure
I’m still on my original Pixel 1!! Just wondering if you are going to go for a Pixel 6 or 6 Pro? I am close to where I have to make a decision soon…..
I went with the Pro. Quite happy with it.
I was told by my credit union that they were no longer to send @FA codes to email addresses and would only use a phone, even a land line. Then I cleared my cache and when I logged in again, they sent to my email[?], so what the truth, if anyone knows?
FWIW, one can install the stock Google messaging app as a web app on any PC (can also be accessed via a browser). This has gotten me by on the rare occasion my phone is out of commission for a short period of time and I need to communicate or use text as 2FA.
Also, I have a Google voice account which is a great fallback since all contacts are synced and both voice and text can be used via any browser.
Jason Howell of TWIT once got himself locked out of his accounts when he set-up his Google Voice as his number for authentication. It was a real circular Catch-22 situation.
Unfortunetly many banks will not use VOIP sms for sending authenication.
Thanks for this informative article, as I have had this question sitting in the back of my mind for quite some time now. Up to this point in time, whenever we have a power outage here in the Philippines (which is several times a month), when signing into our U.S. Financial Institution, we get a notification that before we can proceed any further, we need to prove to themselves (2-Factor Authentication) that this is indeed a personal or private computer and, we then select my wife’s Cell Phone Number for them to send us a 6-digit code (which we enter into a box) before being allowed to proceed any further.
However, we are planning on taking an extended 3-month trip from the Philippines back to the U.S. in a couple of years and of course, will be required to use a Two-Factor Authentication when communicating with our U.S. Financial Institution. Yet, I can’t very well take my personal computer back to the U.S. and, that might mean either purchasing a lap top (either in the Philippines or the U.S. ) or possibly using my wife’s tablet (which I have never used), to stay in contact with our U.S. Financial Institution and possibly reading emails. What are your thoughts, as I am stymied?
You have multiple options.
First & main issue is what options does your bank offer?
The easiest is to take your wife’s phone with you. Your risk is excessive roaming charges if she receives a lot of voice calls. Her service provider might offer a SMS Roaming service (text messages go thru, voice calls go to voicemail). You should turn-off cellular data roaming to avoid excessive data-charges.
I’ve done this for several years while in the USA to manage banking in my home country. I do the same with a GoogleFi phone for managing my US bank account.
Next option is similar. Get a cheap local burner phone to take with you & switch the 2FA to it before you leave. Make sure the phone service supports roaming in the USA.
If your bank supports 2FA via e-mail. That’s one of the most flexible options. If you’re reasonably paranoid, get an e-mail account that you only use for this purpose. You will need to travel with a device (like your wife’s tablet) that can be used to access the e-mail account.
You also need to work out a recovery plan for the scenario where phone or tablet are lost or fail.
If your bank supports 2FA on a app like Google Authenticator, Microsoft Authenticator or Authy, then I’m with Leo in recommending Authy (I use all three).
Your bank might have an bank app that you can load on a tablet or phone to manage authentication.
I travel between the US and Germany. I used to have two phones one for the US and one for Germany. When I did banking in the US on my German account, I got my authentication code on my German phone and vice versa. In my case, there are no roaming charges to receive texts or use my bank’s authenticator app. If there are roaming charges to receive a text, they would only be a few cents. I ignore any voice calls when I’m traveling unless the call is important. All of my friends use WhatsApp or another free messaging app to communicate.
Now I have a phone with a dual SIM card which makes it even easier.
I have two annoying issues with 2FA:
1. A couple of years ago we were all encouraged to improve the security of our passwords. The recommended standard was 16 characters including uppercase, lowercase, symbols and numbers. We were told that this standard would take a hacker 400 years to unravel. During that time I have changed my passwords to exceed this recommendation. So if my passwords are secure, why do I need 2FA?
2. I live in a rural environment. My mobile signal is very weak and can only be relied upon in one corner of our dining room. To collect my 2FA code I have to leave my office, walk some distance, write down the code and get back to my computer before it times out. This is particularly difficult as I have limited mobility. In some cases the 2FA code can be emailed but this is often slow and the site times out beforehand.
I’m not a fan of 2FA.
1. I’ll give sone examples: someone installs a keylogger on your device and gets your password. The website you visit may not encrypt your password, and they get hacked. And there are other ways your password could be compromised.
Sorry for the delay, away on business. So, as passwords offer minimal protection and in order to maintain our sanity, it seems, therefore, we should use reasonably simple (6-10 characters) passwords and work with the inconvenience of 2FA.
2FA verification is a usually minor inconvenience. The well-designed ones recognize your computer or device after the first time and the machine itself becomes the second factor and you don’t have to jump through any 2FA hoops after that,
If someone installs a keylogger to get your password you’re out of luck, even if have a 128-character long password. As for the claim that it’s a “security measure” that it’ll take someone 400 years to find your password, that’s just an advertising claim to make you feel good. Crooks are much smarter than that and there are much easier and faster ways to get your password – IF someone really wants it.
I pay $10 a year for Bitwarden that besides securing my passwords also generates my 2FA codes and I can access it across multiple devices. The catch is I require 2FA to sign into Bitwarden on non-trusted which I use Google Authenticator for. Using Bitwarden to fill the 2FA is much more convenient.
My phone was destroyed on a recent trip. Still had my ipad and a laptop and thought I could get by without issue. NOPE. So many services now require you have your phone to obtain texted code numbers, no exceptions. A few I could TRY to work around by giving the hair color of my best friend’s, father’s, sister in-laws second favorite cat and other similar, stupid, totally unmemorable security questions. But many like UBER, stubbornly require the SMS codes only. Even if you try to setup a new account they still require a phone number to SMS a code to. And I thought 2 factor authentication couldn’t be made any more irritating.