You may be using BitLocker and not even know it.

I’ve recently run across a couple of cases where people have discovered that their system drive was BitLocker encrypted without their having turned encryption on.
I’ll admit that I believe this may have happened to me some time ago. Since I want BitLocker on, I probably thought nothing of it and moved on.
But there’s something important you weren’t pestered about in this process: the recovery key.
Become a Patron of Ask Leo! and go ad-free!

BitLocker may be enabled by default without your knowledge. You can examine all the BitLocker recovery keys associated with your Microsoft Account by visiting https://account.microsoft.com/devices/recoverykey, or you can examine the state of each drive, and back up its recovery key manually, by right-clicking on the drive in Windows File Explorer and clicking Manage BitLocker. Either way, if you’re using BitLocker, make sure to back up your recovery key.
Traditional BitLocker setup
If you explicitly turn on BitLocker full-disk encryption, at some point in the process you’ll be encouraged to save the recovery key.
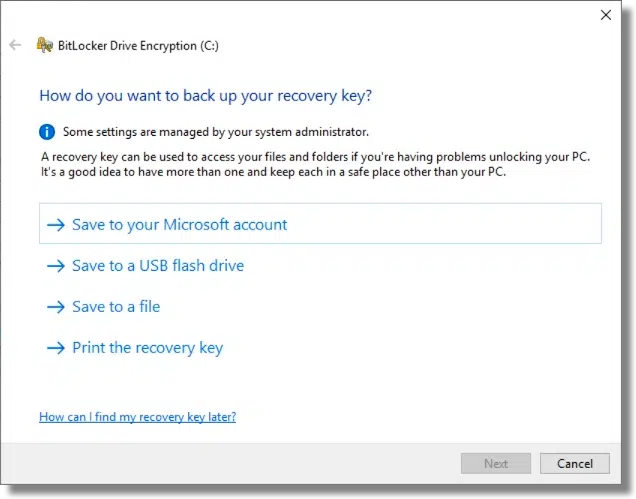
It’s important that you take at least one of these options, if not more than one. The recovery key is your way back in should you lose the ability to sign in to Windows normally, or should you ever need to move the drive to a different machine.
It’s important to keep somewhere safe to avoid possibly losing access to everything on that drive, should something go wrong.
Great. But what if you didn’t take this path?
BitLocker on by default?
It turns out that several computer manufacturers are delivering machines with BitLocker turned on by default.
Who knew?
That has several implications:
- You may be using BitLocker right now and not even realize it.
- Your hard drive is more protected than you thought, whether or not you think you need that extra protection.
- You probably didn’t walk through the process of turning on BitLocker, and thus weren’t prompted to save your recovery key.
Personally, I’m just fine with BitLocker being on. You can turn it off, of course, if you don’t feel the same way.
It’s that last point, though, that has me the most concerned, and the reason for this article: the recovery key.
The quick way: using your Microsoft Account
Visit this URL:
https://account.microsoft.com/devices/recoverykey
This page lists all the BitLocker keys associated with your Microsoft account.
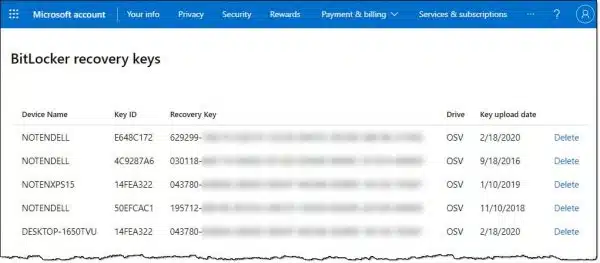
Shown above is the list that shows in my personal Microsoft account. There are several interesting things to note.
- One machine is listed multiple times. Each likely represents a reinstall of Windows and a re-creation of the BitLocker encryption. Technically, I probably don’t need the older ones, but there’s no reason not to leave them there, just in case.
- One machine doesn’t have BitLocker on any drives. It’s likely it’s a machine on which I turned BitLocker off.
- One machine’s name is incorrect. This implies that the key was saved before I changed the name of the machine from it’s auto-generated default to my own NOTEN-based naming scheme.
If you use BitLocker, see if any keys are listed here. If they are, then further back up this information somewhere else, just for safety. Take a screenshot of the page and save the image in a safe place, for example.
This is great, particularly if you suddenly need a recovery key for a drive you didn’t realize had BitLocker enabled.
My question, though, is how do I know if these are up to date?
I don’t.
The accurate way: backup your recovery key
Right-click on the drive in Windows File Explorer.
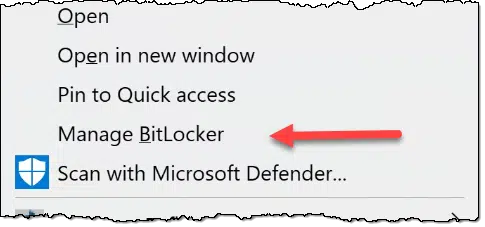
If the menu includes “Turn on BitLocker”, then BitLocker is not enabled for this drive. There’s nothing you need do. (If the menu has no Bitlocker option at all then you probably have the Home version of Windows without BitLocker support.)
If, however, it says “Manage BitLocker”, click on that.
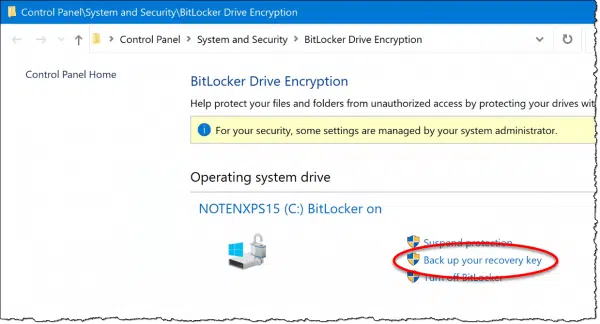
Click on Back up your recovery key, and you’ll be given the options shown earlier to do exactly that. My suggestion is that you back up to both your Microsoft account (so as to be listed online, as I showed earlier) and in some other form. Once you have that other form, make sure to store it somewhere safe where you can find it if needed.
Whole disk encryption is a valuable approach to securing data, particularly on laptops and other mobile devices. BitLocker is a fine solution for Windows, but it’s important to make sure you have those recovery keys available should you ever need them. Particularly since BitLocker might be turned on without your knowledge, it’s doubly important to check.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!




This only applies to Professional versions of Windows and higher. Home versions of Windows don’t offer Bitlocker.
So, if you right-click on the c: drive in Windows Home, “Manage BitLocker” won’t show up in the pull-down menu.
Partly Wrong. Your description suggests only Windows 10 Pro is able to encrypt with BitLocker. You are right about the Context Menu in Pro containing the “Manage BitLocker” entry and Home not containing it. For Windows 10 Home users, you must go the Control Panel to do this. (Control Panel > System and Security > Device Encryption)
I recently purchased (2020) Lenovo IdeaPad laptop (IdeaPad 5-15ILL05-81YK) that came with an installed Intel TPM chip, and Windows 10 Home. The Windows installed TPM driver was present and the BitLocker encryption was turned on by default. During the initial Windows Setup, a notice appeared to “Back up your Encryption recovery Key”, which I did.
I assume the determining factor as to whether BitLocker is present and activated in Windows 10 is the decision of the OEM to install a TPM chip or not on your PC, rather than which edition of Window10 is installed.
Bit Locker is not available in Windows Home versions. You can use a program like Veracrypt to encrypt your system drive.
https://answers.microsoft.com/en-us/windows/forum/all/bitlocker-on-windows-10-home-edition/4fd2eecd-2931-4709-ad4e-85bbf3e241f0?auth=1
I’m just a bit horrified by the intricacies around Bitlocker. My status is Bitlocker is not turned on. I believe my PC is fully able to meet the hardware requirements of TPM >1.2 (2.0), UEFI, Secure Boot, PCR7, Device Encrption Support, etc. I admit that a check of SYSINFO shows that elevation must occur before the status of PCR7 and Device Encryption can be viewed but I’m not going down that road just to find out.
What is horrifying is that OEMs would cavalierly set Bitlocker on and, I suspect given the suspect state of the art of typical system set up instructions, perhaps not fully cover the ins/outs of Bitlocker Recovery Key. I just read elsewhere that a windows update can change the Bitlocker status and Recovery Key. How’s that for a kick in the pants!?
I’m not anti-encryption and use it for password systems and selected files/folders but who is minding the store for the unsuspecting user? I think computers are getting more and more “weasely” every day. My apologies to actual weasels.
Hi there!
I am looking for any informations that could help me recovered the Bitlocker key when the computer is already locked by bitlocker. None of our microsoft accounts has a recovery key and, of curse, as we didn’t know that we have this on the computer we never trying to save a recovery key.
What could be done?
Nothing that I’m aware of. That’s kind of the point of Bitlocker: to prevent unauthorized access. Hopefully you have an image backup of the computer. Failing that I know of no way in.