Articles in Category: Security
How Can Four Random Words Possibly Be More Secure Than 16 Random Characters?
Passphrases are just as secure as passwords — perhaps even more so — and are easier to remember if needed.
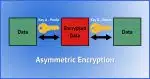
What Is Public Key Cryptography?
Public key encryption is the workhorse of security online. I’ll review just what it is and how it’s used at a high level.
How Does a Hardware Security Key Like YubiKey Work?
Hardware security keys like YubiKey provide an extra-secure level of two-factor authentication.
Can’t I Just Delete My Hacked Account?
Deleting an account you don’t have access to is kind of the same as deleting an account you don’t own.
Privacy Begins with the Operating System
Your operating system sees everything you do—and that means it holds the keys to your privacy. I’ll look at how much trust you place in Windows, Mac, Linux, or mobile systems, why that matters, and what steps you can take to protect yourself wisely.
Why ANY Two-Factor Is Better than No Two-Factor
Headlines are proclaiming that two-factor authentication has been hacked. That in no way means you shouldn’t use it. Your account is still much safer with two-factor enabled.
Can I Still Use LastPass Safely?
Selecting another password manager is now the common recommendation. I’ll review what you can do if you elect to keep using LastPass.
Is “Juice Jacking” Real?
The FBI released a warning against “juice jacking”, but is it really something you need to worry about?
My Computer’s Been Compromised. What Should I Do?
The news is grim if someone’s broken into your computer, but there are steps to take to prevent it from happening again.
Will AI Crack Your Passwords?
We’re seeing AI associated with many things. Cracking your passwords is now on the list.
What’s the Best Password Manager in 2025?
Overwhelmed by too many password manager choices? I’ll walk you through the best current options, what makes them different, and how to pick the one that fits you best. The most important step? Start using one today for safer, easier, and more-secure logins.
How Do I Prevent Credit Card Theft?
There are some practices to help you avoid having your credit card compromised, but most card theft is out of your control.
Can I Check for Malware before Downloading Something?
Files cannot be checked for viruses before being downloaded, but there are precautions you can and should take.
If Someone Gets Into My Gmail Account, Can They Get Into Others?
Like a row of dominos, gaining access to one account can lead to others being compromised.
Why You — Yes, You — Are a Target of Hackers
Even if your bank account is zero or you’re just not that interesting, hackers are still after your accounts. Here’s why, and what you can do.
Are Facial Recognition and Fingerprint ID Safe?
Facial recognition and fingerprint ID are quick, convenient approaches to signing into or unlocking your devices. But are they safe enough?
What Encryption Software Do You Recommend?
There are many different tools for encryption. The right one depends on what you’re attempting to accomplish.
Why Is It Important to Have Different Passwords on Different Accounts?
Using a different password for every login is crucial — and it doesn’t have to be difficult.
How Can a Hacker Try All Possible Passwords If Systems Block Failed Login Attempts?
Some hackers go for the low-hanging fruit and try the most common passwords, but there is one scenario where brute force works very well.
Your 6 Strongest Practical Password Techniques, Ranked
Six practical approaches to generating passwords, ranked from best to worst.
How Long Should a Password Be?
For years, the standard practice has been to assume that eight-character passwords made up of sufficiently random characters was enough. Not any more. Not even close.
How Do I Remove Malware from Windows 10 or 11?
Trying to remove malware? I’ll walk you through the steps and options, from simple to hard, including the only approach that’s guaranteed to work.
It Pays to Be Skeptical
If we would all be a little more skeptical, we’d be safer and the internet would be a more trustworthy place.
12 Steps to Keep from Getting Your Account Hacked
Here are the steps you need to take to prevent losing your account forever to a hacker.
Internet Safety: 7 Steps to Staying Safe Online
Staying safe online doesn’t have to be overwhelming. I’ll show you seven practical steps anyone can follow to protect themselves from malware, scams, hackers, and everyday digital dangers.
What to Do About the LastPass Breach
The most recent LastPass security incident has many people concerned.
How Do I Delete Google Search History?
Deleting your search history can seem simple, but there are complications worth knowing about if you need to be thorough.
Can My Neighbor View My Internet If I Use Their Wireless?
Using any shared internet means other users on the service might be able to see what you are doing. Extra security steps may be necessary.
Should I Use My Password Vault for Two-Factor Authentication As Well?
A new feature in some password vaults has us thinking about security implications. Bottom line: use two-factor authentication.
A One-Step Way to Lose Your Account Forever
I see people lose access to their most important accounts all the time. It’s often their own fault that they can’t regain access.
A Lost-Second-Factor Tale of Woe and How to Avoid Your Own
A tech journalist lost his phone and encountered issues recovering a two-factor-protected account. We can all learn from his experience.
Please Set Up and Maintain Account Recovery Information
Account recovery information is an important yet often overlooked part of account security. Managed poorly, it can lead to permanent account loss.
What Should I Assume About Workplace Technology Monitoring?
Many employers can and do monitor the technological activity of their employees. Here’s what you need to consider doing.
How to Back Up Encrypted Data
Encrypting your data is important for security, but it also adds risk that’s easy to overlook when backing up.
They Set Up My Computer and Now My Ex Is Spying on Me. What Can I Do?
Trust is tricky when it comes to computers. When you add relationships to the mix, things quickly get complicated.
How Should I Password-Protect an External Hard Drive?
You want more than a password; you want encryption. Encrypting an external drive can be done with the right software.
How Do I Pick the Right Tools to Protect Windows?
There are many software programs that protect your system. I’ll review how I make my decisions and give you my advice.
What is a Digital Fingerprint?
Digital fingerprints are another way that websites might track you, should they want to. What can you do? Should you be worried?
What Is Smishing?
Smishing is simply text-messaging spam. Learn to recognize and respond appropriately to it.
I Got a Pop-Up Virus Warning. Is My Computer Infected?
Messages that indicate you have a problem and recommend a specific download as a solution are immediately suspect.
What is End-to-End Encryption?
If you’re sharing private or sensitive information, end-to-end encryption is an important term you need to understand.
Should I Clear Cookies Before I Travel?
Clearing cookies is an annoyance, but it protects your online accounts in case your machine is stolen.
Why Did My Security Software Not Detect a Virus on My PC?
Even with up-to-date anti-malware tools, you can still fall victim to malware. I’ll explain why by comparing your computer to your… bathroom?
Preparing Your Technology for Travel Abroad
Travel is exciting, but be sure to plan ahead for your technology to avoid things going wrong.
What You Need To Do About the LastPass Hack
A portion of LastPass was breached. Here’s why it’s not a disaster, and why I’m not leaving LastPass.
The Biggest Risk to Your Security
The biggest risk to your security might just be you. Learn why and what to do.
How Can I Protect Myself From Scams?
Scams are everywhere, it seems. I’ll cover some common ones, and share the single most important rule to protect youself.