It’s a feature that can make two-factor easier to use — but at what risk?
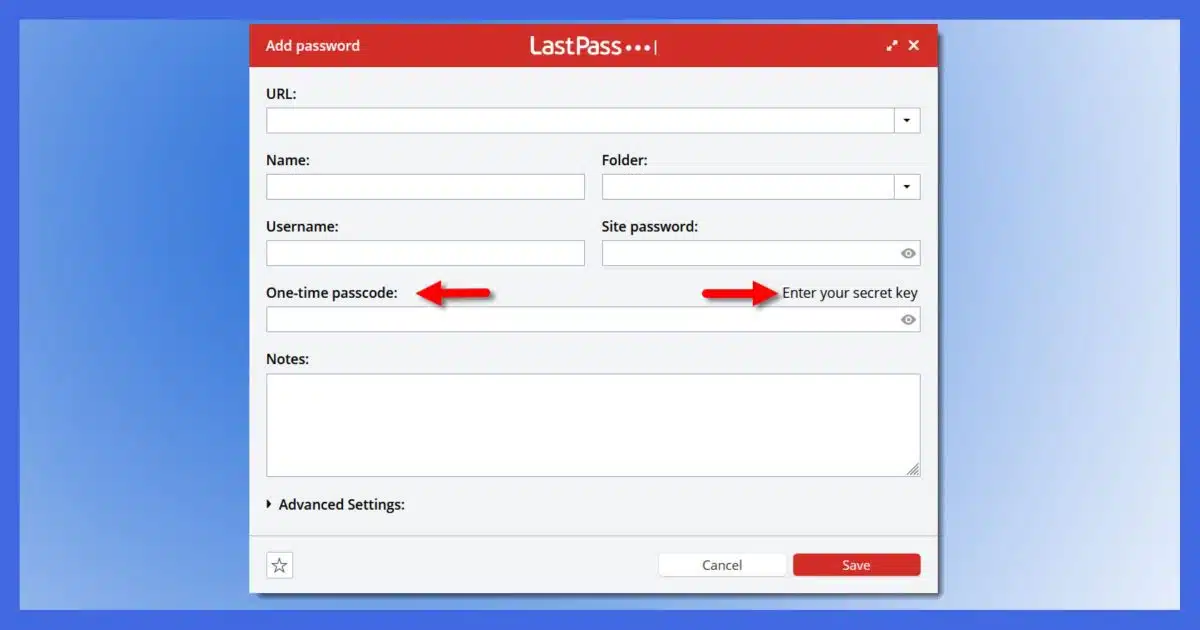
It does seem somewhat counter-intuitive, doesn’t it? LastPass added that feature as well. I have yet to fully play with it, but I certainly have thoughts.
The short thought is that anything that makes two-factor authentication more likely to be used can’t be all bad.
Become a Patron of Ask Leo! and go ad-free!

Password vaults and two-factor authentication
Password vaults that offer to act as your second factor, perhaps even automatically entering the two-factor code for you as you sign in, make two-factor easier to use. While there’s a tiny (tiny!) additional risk in keeping your two-factor keys in your password vault, it’s totally worth it if it gets you to use two-factor authentication more consistently.
TOTP, aka two-factor authentication
TOTP stands for Time-based One-Time Password. More commonly, it’s the Google-Authenticator compatible two-factor authentication mechanism.
The process is simple: you set up two-factor by pairing your smartphone with your account, usually by scanning a QR-code that contains a secret key. The authenticator application displays a random-looking number that changes every 30 seconds. It’s not random; it’s the result of an encryption algorithm involving the secret key. Your ability to enter the correct code at the correct time proves you are in possession of your second factor: your phone.
Thus, two factors are required to sign in:
- Your password
- The authenticator code
Some password vaults have taken steps to make this a little easier.
Password vaults and 2FA
That QR code contains an encryption key. (It’s also possible for you to display the key in text form in case you’re unable to scan a QR code).
Password vaults like Bitwarden and (some versions of) LastPass (shown above) have incorporated the open-source Google Authenticator algorithm so that they can also act as your second factor. But they take it a step further.
First, for an appropriately configured account, the vault knows:
- Your user ID
- Your password
- Your two-factor secret key
That means the vault software could enter your user ID, your password, and the current two-factor code for you automatically.
But is that a good thing?
The small risk
In theory, if someone were to gain access to your vault, it would give them the first and second factors (passwords and two-factor codes).
The good news is that this is highly unlikely. Not only do we tend to be more careful with our vault’s security, but there are multiple steps in place to prevent someone from randomly gaining access. It’s possible, but highly unlikely. Even if a hacker was to breach the provider (BitWarden, LastPass, whomever else) they could not gain access to this information.
And the second factor remains in force. If anyone ever discovers your password by other means, your account is still securely protected.
The pragmatic spectrum
I see account security as a spectrum.
- Good: use a password vault.
- Better: use a password vault and 2FA, keeping your 2FA tokens in the vault.
- Better still: use a password vault and a separate 2FA method (i.e., Google Authenticator or compatible app).
- Best: use a password vault and a separate physical 2FA device such as a YubiKey.
The increase in security between “good” and “better” is massive. Adding two-factor is a significant increase in security.
The increase in security between “better” and “better still” is small. The risk of someone gaining access to your password vault is very small, and if the convenience is enough to get you to enable two-factor authentication, then it’s totally worth it.
Do this
Given that the perceived inconvenience of two-factor authentication often keeps people from even trying it, letting the password vault handle it for you seems like a perfectly fine way to improve overall security.
I say, go for it.
Something else to go for: Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




I’ve set Bitwarden to use 2FA to log into my vault. In my situation, the second factor is a Yubikey. On my laptops, I’m able to set Bitwarden to not require a separate log in when I sign into my Microsoft account, for convenience.
If I have to use Bitwarden on my wife’s PC, I need to have the Yubikey to access my vault. I’ve setup her PC the same way as my laptops and if I need to access her vault on my laptop, I need her Yubikey. (I’m the household IT person and the one who sets everything up.)
Since we use pass phrases, including punctuation, and 2FA for our vaults, I believe it to be very unlikely for one of our vaults to be compromised. We also have more than one Yubikey linked to our accounts, with the spares safely stored with our other recovery materials.
So with all that done, using the TOTP feature in Bitwarden is not a security risk. I discovered that I can use the codes I saved for the Yubikey Authenticator app with Bitwarden as well.
It has taken me some time and effort to set all this up, but I’m confident that I’ve set up a system where a single failure (lost phone or Yubikey) isn’t going to be a total disaster. I’ve created a document with instructions for how to use all this and printed a copy which is stored with my will. And I review it periodically to ensure it is up to date. So my heirs won’t be caught in the situation of not being able to access my computer or accounts.
YubiKey is pretty much the most secure 2FA, but sadly, it’s not free and not enough places use it. but I got a couple of keys a while ago now when the price was good as I just bought two of the basic standard USB ones, which you need two keys at the minimum (see my reply below to ‘Mark H’ for more info on why).
but one thing I wish more sites would use is 2FA using a email address as I prefer that over smart phone junk (even though I could see how this might be slightly more insecure for some people vs a smart phone type of 2FA, especially if they are using the same weak password on multiple accounts etc as once someone gets their email, then 2FA using a email would not really help at this point where as with a smart phone they would still be good). because in my case my email is quite secure (as I got YubiKey tied to it, well actually two which is a minimum standard to ensure you won’t get locked out of your account) and a random site using email for 2FA it’s easy enough for me to use as they can simply send a one time code there just to enter when signing into a random website using 2FA.
ill usually avoid 2FA if it’s not using email (or YubiKey) because I just straight up don’t like using smart phones in general online as I tend to almost entirely use a desktop computer for online access, especially general day-to-day.
I do use a password manager though and have been for many years now, probably somewhere around 2005-2007, so probably about 15+ years or so.
@ Mark H. ; if your not aware of it, for say a Google account for example, you really need a minimum of two YubiKey’s registered to your account otherwise you are at potential risk of losing the account. because for example if you only have one key registered to the account and you lose that key, you are likely locked out of the account. but if you have two YubiKey’s registered you simply use one key like usual, and keep the backup stored in a secure location. this way if you lose your primary key, you can use the backup to get into the account and remove the lost/stolen key and then simply buy another key and register it to your Google account and you now have two keys registered to it once again. while some could opt for other ‘backup’ 2FA to the YubiKey it would defeat the purpose of using a YubiKey in the first place since the 2FA is only as strong as the weakest link basically. that’s why on my Google account the ONLY way I can get in is using my two YubiKey’s (my primary one, and a backup stored in a secure location on the off-chance I happen to lose the primary one).
that general principle would apply to YubiKey’s in general.
I have looked in LastPass for my accounts that use Google Authenticator and I see no place for in LastPass for a TOTP or a secret key. Does anyone have any idea why or how to fix it? Why is my LastPass different?
Not all plans have it. I don’t have it on my personal account, for example, but the business account seems to. Other password managers include it natively, hance the generic nature of the article abocve.