Without it, you risk losing your account forever.
It might be as important as backing up. It’s certainly close.
The number of people I hear from desperately trying to regain access to their accounts would surprise you.
The number of people who’ll never regain access would surprise you more. I see it at least daily.
It doesn’t have to be that way!
Become a Patron of Ask Leo! and go ad-free!

Set up recovery info
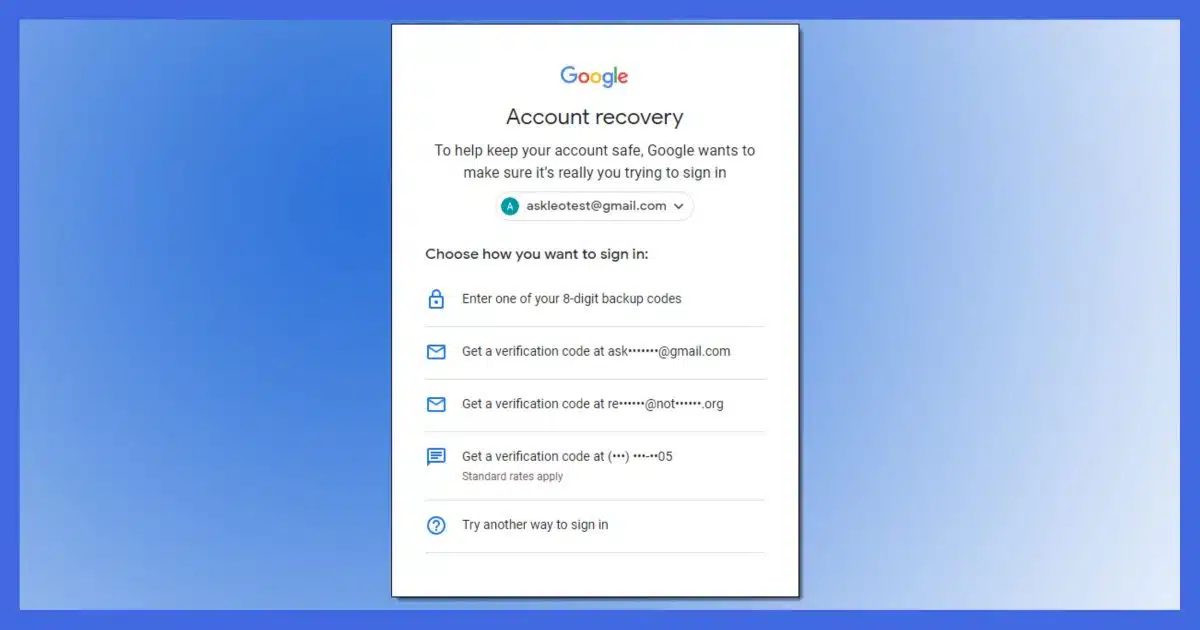
Recovery information is crucial to regaining access to your account if you can’t sign in for any reason. Make sure not only to set it up, but keep it up to date. I see many accounts permanently lost because recovery information was either out of date or never set up at all.
Recovery information has one purpose
You know you are who you say you are.
If you lose your password, all indications are that you are not who you say you are. If you were the rightful account holder, after all, you would know the password.
I know, I know! That’s not the case if someone has hacked you or you lost that little green notebook with all your passwords scrawled in it. But the service has no way of knowing that. Your username/password combo1 is how you prove to them you are who you are.
What most services do realize, though, is that people are people. Sometimes we forget our password. Sometimes our accounts are hacked.
Recovery information is an alternate means for you to prove you are who you say you are and should be given access to the account.
You must set up recovery information before you need it
The reason recovery information works is because you set it up while you have access to your account. It’s information you add to the account in case of future problems.
Hopefully, you’ll never need to use it. But you must set it up, just in case.
If you never set it up, then should your password ever stop working, you’ll have no way to prove you are authorized to access the account.
You must keep recovery information up to date
Honestly, most people facing account loss due to failed recovery attempts did set up recovery information when they set up their accounts. That’s good, but it’s not enough.
Many of these accounts are years old (and that’s one reason you care so much about it). The recovery information you might have configured back then falls out of date. Maybe your recovery phone number is no longer in use, or your recovery email address has long since disappeared, for example.
Out-of-date recovery information is just as bad as not having it at all. It might even be worse if it gives you a false sense of security.
You must keep it up to date. Check it periodically (some services now occasionally prompt you to do this), and/or proactively update it when something changes.
Type of recovery information
These are the kinds of things we’re talking about here.
Alternate email addresses. Make sure you still have access to the email account to which the recovery code will be sent. If you do not, recover that account or configure a different one.
Mobile phone number. Contrary to conspiracy-minded folks, this is not used to gather more tracking data on you. (The mobile services already have plenty.) Make sure that any mobile number configured in your account is a number at which you can currently receive a text message. If you change numbers, make sure to change your recovery information. If you lose your mobile, replace it quickly and have your phone number ported to the new device; text messages are tied to your mobile number, not a specific device.
Landline phone number. This is less common, but some services allow you to use a landline and call you with a recorded confirmation code in case of recovery. Like a mobile number, if your landline number ever changes, make sure to change it in your account recovery information.
Recovery codes. This is also less common, but doesn’t suffer from issues relating to change. Some services let you generate one or more “recovery codes” — random numbers that, in the event of password failure, can be used once to sign in to your account. The issue here is that you must create and save them somewhere secure so they’re available when needed.
Secret questions. Some services still use them, but they should not. It’s been shown that they’re often guessable and significantly less secure. If you have a choice, use one of the alternatives above. If you have no choice, make sure you do not forget the answers to the questions you choose.2
Do this
Set up account recovery information and keep it up to date.
You run the very real and serious risk of losing access to the account if you do not.
For other ideas on staying safe, reducing risk, and using your technology with more confidence, subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: Plus your second factor, if you have that configured.
2: I used to be surprised at how often people forget their answers, but it makes an odd kind of sense. When setting up the account, they don’t want to answer the questions or want to answer them extra-securely, so they enter nonsense. Later, when the account is important enough to need recovery, they can’t remember the nonsense answers.




This is another scenario where a password manager comes in handy. I currently use Bitwarden and have used LastPass before that.
Both allow notes to be attached to the pass cards for each account for answers to secret questions and recovery codes. In the event that one needs that information, it will be readily available.
Some of the answers to my secret questions are so ridiculous, there is no way I can remember them.
Having had to assist another person after he got locked out of his computer after too many failed attempts to login using his Microsoft account and what it took to do so (resulting in a 30 day waiting period), I made sure that account recovery methods for everyone in the household was setup and available if and when the situation arises again.
What if you forget the password to the password manager? I use a long password I can easily remember and 2FA to login to my Google account and I store all my passwords in the Google account, I don’t think I need another password manager. I trust Google, their services works for me. Therefore I have several ways to reset my Google account configured.
When logging in to my Google account on a new device I have two updated smartphones and two Yubikeys I can use as rhe second login factor.
If you forget your password manager’s password, you won’t be able to recover the contents of your vault.
Unless, of course, you’ve been backing it up regularly. Example: How Do I Back Up LastPass?
My low-income self has attempted to rely on government-supported Lifeline phones that merely require a minimum of one telephone call per month to keep your account active. HOWEVER, the private firm providing my first Lifeline phone purportedly went out of business and the FCC number portability regulation either had not been established or was poorly enforced by the FCC, because I repeated and alternative efforts to transfer that phone number to my new Lifeline carrier failed. Since then, said new Lifeline carrier failed to replace my malfunctioning phone in July (2022) as it claimed that it would, I was thus unable to make a phone call within that 30-day period, I still do not have a replacement phone, and I fear I might not be able to rely on the FCC again to enforce my phone number’s portability once I get around to get the phone replaced. It has now been over four months without a phone, one return receipt requested snail mail to Assurance Wireless (my most recent Lifeline carrier), and both snail mail and email to both Senators for my State (Illinois) and my U.S. House Rep. (Mike Quigley) alerting them to the FCC number portability issue. That I never trusted these Lifeline phones and enforcement of telephone number portability under FCC regulations at least kept me from relying on 2FA, so I can still (albeit less securely) get into my online accounts (until I can’t, which hasn’t happened yet (knock on wood)). WE NEED TO BE ABLE TO HAVE OUR PHONE NUMBERS RECOGNIZED SIMILARLY TO OUR SOCIAL SECURITY NUMBERS, SO THAT LOSING A PHONE OR ITS ACCOUNT WITH A CARRIER WILL NOT CAUSE LOSS OF YOUR PHONE-NUMBER IDENTITY IF YOU WANT TO DEPEND UPON (KEEP) IT.
Can you afford to buy a yubikey or two? You can find it here
https://www.yubico.com/us/store/
You can use this as a the second factor when you login.
With 2FA its safe to use a simple password you wont forget. My wife and I use rhe same Yubikeys on our Google accounts so other family members can use the same keys as the aecond factor very convenient and recommended by US Department of Defence.
Leo or Mark?
What do you think about the suggested yubikey?
I have one. It’s the most secure alternative, but it’s also the most inconvenient if you rely on it alone. While most of us with smartphones tend to carry them with us at all times, the YubiKey is something else we need to remember to have as well. Highly recommended for those situations requiring significant extra security (corporate, government, health, etc. scenarios) but probably overkill for personal use.
Yubikey is great but I don’t use it for the reasons Leo mentions in his comment. It’s one more thing to have to carry around and overkill for my needs.
One of my Yubikeys works with NFC and I use it with my Android phone. I just have to hold it to the back of my phone to provide authentication. That Yubikey is kept on my key ring with my car key and house key.
I don’t do much on my phone, but having that capability can be useful at times.
Leo,
How do you deal with what you might call a Catch-22 situation. Gmail will not allow security changes without verification through the mobile phone, so if a number is changed or a phone is lost, it is impossible to update the new information without going through the same phone which is already lost.
Also you mentioned that Verification is though the number and not the phone. This doesn’t seem to be the case, as my 2 Step Verification pops up on the named phone rather than a direct SMS message to my number.
When you setup and maintain account recovery information you can typically include more than one alternative — a SMS number, an email address, and so on — so you can choose which one to use if the default one no longer applies.
If you use the encrypted mail service Protonmail, in addition to a recovery email address and phone number, be sure to also set up both a data recovery phrase and file immediately! And put them somewhere safe.
I lost all prior mail (fortunately nothing important) when I was reset my password with them via the recovery email BUT… I didn’t have the other data recovery information so all previous email messages disappeared. Poof!
They call what I did (using recovery email and/or phone number) “Account recovery” but to do “Data recovery” you need either (1) a recovery phrase or (2) a recovery file.
A particularly arrogant client insisted on using Protonmail but had not set up the “Data recovery” items. Her previous “IT guy” got her on Protonmail. She “knew” everything and she would not listen to me about this.
Naturally she lost track of the password and… therefore ALL of her mail history.
There was no way that I was responsible for this but I fired the client at that point for that and many other reasons.
I still like secret phrases the best, as I put them into LastPass and can be easily auto-entered. 2-factors take longer, and if it is used my Authy app, then I can’t even copy and paste since the Authy app is on my phone.
You can run authy on your desktop, and use copy paste. I do it all the time.
Hi Leo, I dont get where you set up this account recovery information to retrieve. Is it on a memory stick?
Regards Ray
Read the article again. It tells exactly what to do. The recovery information isn’t something you store. It’s an email account you associate with your account for recovery. Maintaining it means keeping those recovery email current and making sure you can access them. The exception to this is outlook.com which allows you to create a Recovery Code which you can store anywhere you consider safe. I keep mine encrypted in OneDrive and copies in my computer backups.
This Recovery Code is useful even if you don’t use your outlook.com account for email management. Supported versions of Windows require a Microsoft account to get access to certain features such as OneDSrive.
I dont know my password for my main account for gaming
Use the “I forgot my password” option for whatever gaming account this might be.