bestof
Ask Leo! Articles that are part of The Best of Ask Leo! email subscription available at http://bestofaskleo.com.
The Email Tracking Myth: Why You’ll Never Reliably Know If Your Message Was Read
We often want confirmation that an email has been opened, delivered, or read. In the age of spam, it’s not possible with any accuracy.
Why Programs Might Use All the Memory in Your Computer
Programs typically don’t use all available memory unless they need it or they have a problem.
What Are Tracking Cookies, and Should They Concern Me?
Cookies are placed on your machine by websites — often more websites than you realize. We’ll review cookies and how third parties can use them.
Why Does My Home Network Only Work with One Computer at a Time?
If there is a conflict with your IP address, it could result in only one of the machines on your network connecting at a time.
Does My Computer Need a Memory Upgrade?
A memory upgrade can be an easy, inexpensive way to improve system performance, but how do you know if an upgrade is called for?
Could the Microsoft Servers Be Infected?
It’s tempting to blame the mail service for account hacks and vulnerabilities, but in fact that’s rarely the case. Much more likely is that hackers gained access to individual accounts through more traditional means.
Are Automatic Updates a Good Thing?
Unless you’re willing to pay a lot of attention on a very regular basis, automatic updates are an important part of keeping your machine safe.
How Do I Secure a Hard Drive Before Sending It in for Repair?
When sending your computer out for repair, you’re handing over everything on it, including your data. Options to secure a hard drive are limited.
How Should I Wipe My Hard Drive in Windows Before Giving It Away?
Erasing your hard drive before you give it away is important. Exactly how thorough an erase you need depends on your data and level of paranoia.
Why Do I Get a Black Screen on My Computer After a While?
A black screen is most commonly caused by a screen saver, but there are other possibilities.
How Do I Connect My Desktop to Open Wi-Fi Nearby?
Wi-Fi hotspots make for a convenient connection. To connect, you need proximity, a little hardware, and most important, permission.
Why Shouldn’t I Use the “Report Spam” or “Junk” Button?
The “Report Spam” and “Junk” buttons serve an important function in the war against spam. However, used improperly they can do more harm than good.
Finding the Owner of an IP Address
While you can’t find the specific owner of an IP address, there are a few tools to see what IP-related information you can get.
My External HDD Shows Not Formatted — But It Has All My Data!
Occasionally, when moving a drive to another machine it’ll show up as unformatted. I’ll look at some possible causes and actions to take.
How Do I Remove Malware that Blocks Downloads?
Some malware goes to great lengths to prevent you from downloading, running, or applying a fix. I’ll tell you what steps to take.
Do I Need a Firewall for My Home Network?
A firewall is a critical component of keeping your machine safe on the internet. There are two basic types, but which is right for you?
BoxCryptor: Secure Your Data in the Cloud
Many online cloud storage providers encrypt your data — which means they can decrypt it themselves. BoxCryptor is a great solution to ensure that your online data remains private, regardless of how it’s stored.
Why Don’t Anti-malware Tools Work Better?
It’s possible to get malware, even with anti-malware tools installed. Why the heck is that true?
So Just Why Are Manhole Covers Round?
Manhole covers? Really? Interviewing for technical positions can be tricky, but it can also be fun, if you know what interviewers are looking for.
Why Can’t We Use https for Everything?
HTTPS provides validation and encryption, two important pieces of security. Using it for everything is possible but costly, and issues would remain.
How Do I Become a Computer Programmer?
Being a computer programmer can be a fun and rewarding profession. Here’s my take on what it takes to get there; some aspects are obvious, and others are not.
What’s the Difference Between a MAC Address and an IP Address?
A MAC address and your IP address are both key components to networking, but they serve different purposes, and are visible in very different ways.
Is MAC Address Filtering a Viable Wireless Security Option?
MAC address filtering is a technique that theoretically prevents unauthorized computers from accessing your network. I’ll explain why the theory fails.
What Is Peer-to-Peer File Sharing, and Is It Legit?
Peer-to-peer file-sharing programs have a bad reputation because of the content they’re often used to download. But the technology is quite legal and useful for legitimate purposes.
Should I Get a Dual-Core or a Quad-core Processor?
Processors are generally available with what are called “multiple cores”. We’ll look at what that means, and how you might select which is right for you.
What’s the difference between i3, i5, and i7 processors?
Intel’s Core i3, i5, and i7 processors present a headache-inducing combination of characteristics. I’ll look at what matters and then dig a little deeper.
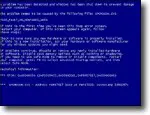
Why Does My Computer Blue Screen?
There are many reasons your computer could get the “blue screen of death”. I’ll review some things you can look into to help determine the cause.
How Does Flushing a DNS Cache Help Resolve Some Issues, and While You’re at It, What’s DNS?
DNS transforms domain names into IP addresses. A DNS cache remembers DNS information… but sometimes it needs to forget.
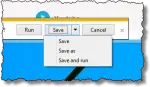
What’s the Difference Between “Save” and “Run” When Downloading?
You can Run a download or you can Save it, or you can even Save and Run it. I’ll review what Run and Save each really mean.
Why Is an Email Address Sometimes in Angle Brackets?
Computers use email addresses to route email. Angle brackets are used when a more human-readable name is also included.
How Do I Route My Email through Gmail?
Gmail can be used to handle email for almost any email address. I’ll show you how to route your email through Gmail, and why it’s worth considering.
How Do I Create a New Machine Image?
When you get a new machine, creating a new machine image backup as soon as you can is a convenient way to reinstall should you ever need to.
What Kind of Computer Should I Get?
A new computer is a major purchase and knowing what kind to get isn’t easy. I’ll review some of the important things to think about when deciding, starting with the type of device you’ll want.
Internet Explorer crashes, how do I fix it?
IExplore.exe, aka Internet Explorer or ‘IE’, can crash, but it’s not always its fault. We’ll look at some of the things that can cause IExplore.exe to crash, and steps you can take.
How Do I Make an Outlook PST File Smaller?
The the Outlook PST file or Personal STorage file can easily grow to an extreme size. Here’s a 4-step plan to managing that size and getting it back under control.
How to Monitor Network Activity and Speed up Your Machine’s Connection
Process Monitor is a powerful tool and it can be used to track down exactly what program on your machine is responsible for internet activity.
Why won’t some files defrag?
When you defrag files the pieces of the file are physically arranged for quicker access. But you can’t defrag some files. At least, not easily.
How Do I Boot from CD/DVD?
Most computers with a CD or DVD drive can boot from that drive, but it frequently takes a small configuration change in the computer’s BIOS.
How can I find out what program keeps popping up in my taskbar and disappearing before I can click on it?
It’s not uncommon to see programs quickly come and go. There are a few ways to try and capture what they are; some technical, and some innovative.
Why Would a Website’s Automatic Sign-in Suddenly Stop Working?
A website’s automatic sign-in may suddenly stop working when cookies are deleted from your machine.
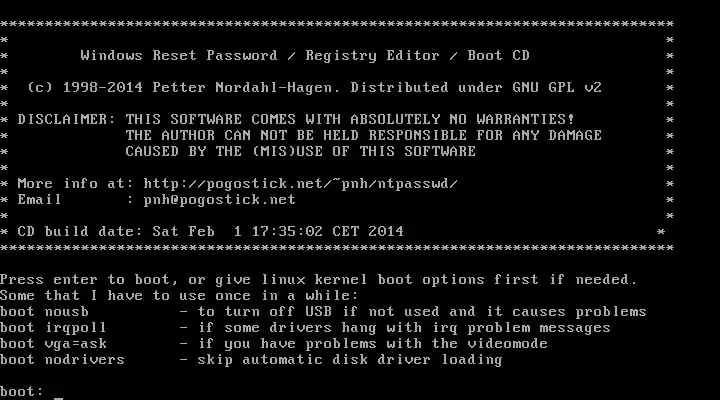
I’ve Lost the Password to My Windows Administrator Account. How Do I Get it Back?
It turns out that resetting your Windows account password is frighteningly easy as long as you have physical access to the machine.
I Don’t Have Installation Media for Windows. What If I Need It?
At some point, you’re going to need your Windows installation CD/DVD. If you don’t have it, you could be severely out of luck. I’ll review alternatives.
How Do I Deal with One Email Account on Two Machines?
There are various options to access one email account from multiple computers, and there are pros and cons to each.
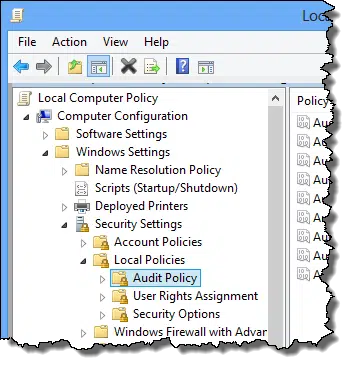
How can I track what programs come and go on my machine?
Windows is constantly starting and stopping programs as part of its normal operations. You can see exactly what programs are being run using a Windows technique called process auditing.
My webmaster left. What do I do?
If your webmaster leaves unexpectedly, you can have a lot of trouble getting access to your own website. I’ll review some of the things that you need to do to prepare – just in case.
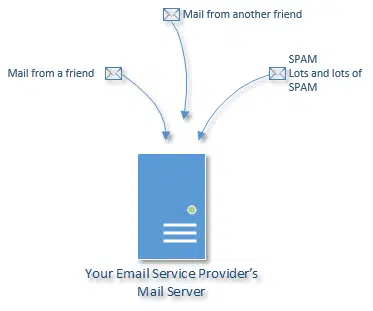
Why do some people get 60 copies of messages I forward?
We’ll try to isolate the reason your forwards are getting multiplied, and then look at the only way to really stop the problem once and for all!
Where is my Outlook “PST” file located?
Outlook’s PST or Personal STore is a single file that holds your email, contacts, and more. You can use Outlook itself to find the location of the file.
Is There Software that Will Transform Poor Quality Images and Videos?
You can’t add data to an image to make it better, but there are some tricks that can make it visually more appealing.
Are Silent Background Updates a Good Thing?
In my opinion, background updates are awesome. I love that Chrome is always up to date without my ever even having to think about it. Let’s look at why.
What’s the difference between an ad and your recommendation?
Advertisements, just like in newspapers or magazines, are nothing more than rented space on a page and should never be confused with recommendations.