privacy
Is Private Browsing Really Private?
Private browsing sounds safer than it really is. I’ll explain what Incognito mode actually hides, what it absolutely doesn’t, and when it’s still worth using. If you think private mode keeps your online activity secret, you’ll want to see where the real limits are.
An Unexpected Way Videos Can Expose Your Location
Something many people do every day may expose their location in ways they aren’t aware of.
Can the Owner of an Open WiFi Hotspot See What Files I’m Downloading?
Internet cafe owners can monitor the activity on open WiFi hotspots. Whether or not they take the time to do it is another story!
How Does a VPN Protect Me?
A VPN can keep your online activity private, especially on open Wi-Fi, but it’s not magic. I’ll show you what a VPN hides and what it doesn’t, so you can decide if it belongs in your security toolkit.
How Do I Remove Myself From a Computer?
Leaving a job and worried about what’s on your work computer? From browser history to email accounts, traces of you remain. Learn what you can (and can’t) erase, and the smartest way to protect your privacy before you walk out the door.
How End-to-End Encryption Protects Your Messages and Where It Fails
You would think that for such an important concept as end-to-end encryption there’s be some agreement on exactly what it means. Sadly, not so. There’s the correct definition, and then there’s the marketing definition. One protects you, the other not so much.
Why I Keep Saying You’re Just Not That Interesting
Many people are concerned that they are specifically targeted by hackers, advertisers, and others. Nope.
Are You Giving Away Your Privacy?
We rail against intrusions into our private affairs and private information and then post our private information publicly. Where’s the logic in that?
Yes, You Should Give Google Your Mobile Number
Google uses your mobile number for verification if you lose access to your account. Some people don’t want to provide it. They should.
Can You Make an Email Without a Phone Number?
There are legitimate reasons for not wanting to give your phone number to an email service. Let’s look at alternatives.
If I Leave a Service Like LastPass, Does My Data Remain Online?
When you leave a service, or if your information is stolen from that service, there may be steps you need to take.
They Set Up My Computer and Now My Ex Is Spying on Me. What Can I Do?
Trust is tricky when it comes to computers. When you add relationships to the mix, things quickly get complicated.
Why Does My Facebook Post Show as “Unavailable” to Some People?
Sharing posts you find on Facebook often results in an “unavailable” message. That’s Facebook respecting privacy settings.
“Right to Be Forgotten”: Misguided and Misleading
“The right to be forgotten” is a misleading and ineffectual technique to prevent people from finding information on the internet. Bottom line: it can’t work.
Can My Boss See My Mail and Instant Messages?
When using your company’s machine and/or network, it’s safe to assume that your boss or IT department can see your emails, instant messages, and everything else.
Protecting Your Privacy: Points of Vulnerability
Tracing the privacy and security of the path from your fingertips through the services you use to your information’s final destination.
How Do I Delete My Facebook Account Permanently?
Deleting your Facebook account requires some preparation, including understanding exactly what you’ll lose.
How Does Facebook Track Me Even If I Don’t Have an Account?
Facebook can use standard web protocols to get an idea of what you’re doing online, even if you don’t have an account.
How Should I Wipe My Hard Drive in Windows Before Giving It Away?
Erasing your hard drive before you give it away is important. Exactly how thorough an erase you need depends on your data and level of paranoia.
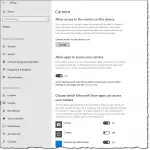
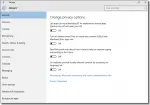
Setting up Windows 10 for Privacy
Windows 10 privacy seems to be somewhat of an oxymoron, at least based on reputation. I’ll review the choices you can make at setup to retain some control.
Facebook Privacy Settings 2021
You can and should be aware of and control your Facebook privacy settings.
The Biggest Risk to Your Privacy Revealed
We worry a lot about privacy, but our concerns are often misplaced. Fortunately, the biggest risk to our personal privacy is right under our nose.
You’re Just Not That Interesting (Except When You Are)
Worried about privacy? I believe we over-imagine the risks and at the same time are our own worst enemies.
Can My Workplace See What Else I Do When I Work from Home?
Working from home can be convenient, or even a necessity. Does it open up your other online activity to scrutiny by your company?
If I Do These Things, Will I Be Anonymous?
Anonymity on the internet is really, really hard. Some of the practices we might use to stay anonymous could still be leaking identifiable, traceable information.
Are My Skype Calls Recorded?
Skype calls recorded by Skype? Possible, but until recently, highly unlikely. However, there’s a much scarier scenario that no technology can prevent.
How to Keep Information on a Shared Computer Private
When using a shared computer, it’s too easy for others to see your data or history. If you must use a shared computer, you need to protect yourself.
Supercookies and Evercookies and No Cookies at All: Resistance Is Futile
So-called “supercookies” and “evercookies” track the websites you visit even if you regularly disable or flush normal cookies.
Should I Upgrade to Windows 10?
The most common question related to Windows 10 seems to be “Should I upgrade?” I’ll cover my recommendations.
Adjusting Windows 10 Privacy Settings
We’ll look at how to review and adjust privacy settings in several areas of Win10.
Is “Windows 10 Privacy” an Oxymoron?
Windows 10 has been criticised for encroaching on users privacy. Is it an issue? Is Microsoft being evil? Or is it something else?
Why Is Chrome Automatically Filling in Forms?
Web browsers like Google Chrome try to be helpful by recognizing commonly used forms and fields and remembering previously entered information for you. It’s no conspiracy, but it can seem spooky.
About that Facebook test…
Facebook did some testing. It’s made some people upset. What’s important to realize is that testing is ubiquitous on the web and happens in many different ways.
Do privacy apps really keep me private?
Privacy on the internet means different things to different people. I discuss three different privacy applications out there, explain what exactly each does, and offer some of my own thoughts.
Why Do I Always Have to Sign Out Other Sessions in Gmail?
Isolating other sessions in Gmail can become pretty complex. We’ll walk through a number of scenarios.
Does deleting things really delete things?
Deleting items on your computer usually doesn’t wipe them clean. That’s an extra step.
Does visiting a search-engine cached page prevent the original site from noting my visit?
Even a cached version of a website could send information about you back to the original server. The thing is that we just don’t (and can’t) know.
Can Search Engines Track My Searches?
Search engines have numerous (and quite amazing) ways to gather information on people and the way they search. It’s nothing to worry about unless you have some critical need for privacy.
How Do I Remove Only My Personal Information from a Computer?
Unfortunately, there is no practical way to determine what is and what isn’t personal information. Securing a computer to give away is an all-or-nothing proposition.
Can my boyfriend/girlfriend/spouse tell that I’ve hacked into their account?
Once you’ve hacked into someone else’s account you’ve not only done something morally wrong – you’re at risk of being found out.