Articles in Category: Security
Removing a Redirect Virus
A redirect virus can fool your browser into going to malicious web sites without your knowledge. I’ll outline my experience detecting and removing one.
How Do I Give Someone a Laptop Without Including Access to My Accounts?
It’s not easy to give someone a laptop without giving them access to your personal accounts. Depending on intent and trust, there are steps you can take.
How Do I Remove a Website from My Computer?
How to remove a website from a computer is a common question, yet it actually doesn’t make sense – websites aren’t on your computer. I’ll look at what is.
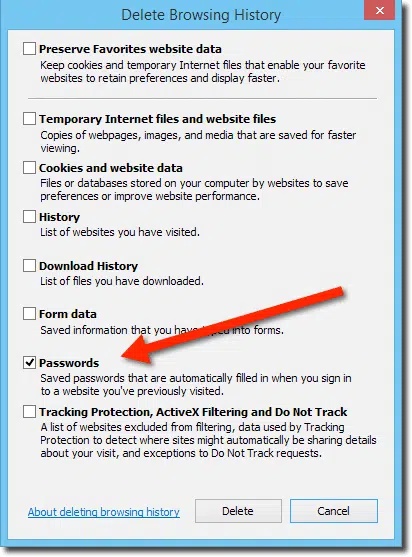
How Do I Disable Remembered Passwords in My Browser?
Web browsers aren’t necessarily the most secure approach to saving your login passwords. I’ll show you how to disable the feature and clear out any previously remembered passwords in IE, Firefox and Chrome.
Do privacy apps really keep me private?
Privacy on the internet means different things to different people. I discuss three different privacy applications out there, explain what exactly each does, and offer some of my own thoughts.
Is anti-virus dead?
Anti-malware tools have never been 100% solutions – but, despite what we hear on the news, they are far from dead!
Can spyware see what you did before the spyware was installed?
When a hacker gets ahold of your computer they can do anything. Keeping them off is the best plan.
Is there software that allows someone to track my emails and texts?
The bad guys can do anything they want to your computer if they can gain access.
If we login to a site securely will our other activities be secure?
Once you are out of https pages you are out of encryption. But there is one good way to secure all your online activities.
Is It Safe to Stay Logged in to My Password Vault?
Remember, the goal is to keep malware off your computer, not to try and manage it once it’s watching you. But there is another security hazard you may not be thinking about.
Why would scanning a disk be quick, but just a file on it be slow?
If that large file is a backup image, then maybe your anti-malware tool knows what I know… that there’s no point in scanning it.
How do I safely switch from one security tool to another?
If you follow a few security measures it’s perfectly safe to uninstall an old anti-malware program and then install your new choice.
Can I Delete What My Anti-malware Program Puts in Quarantine?
Quarantine gives you the option to “rescue” files you might want. Of course there is one way to make sure you always have an extra copy of everything…
Why is my machine so slow after a recovery from malware?
Not only is malware written with bad intent, but it is often written badly. It can leave a mark on your computer’s performance even after it’s been removed.
Would deleting Facebook help clear up a malware infection?
Deleting Facebook won’t help, so I’ll look at more general approaches to removing Potentially Unwanted Programs that are, effectively, malware.
Is My ISP’s Router Safe to Use?
There are a number of compelling reasons to use the router your ISP provides for you. Ongoing support is one. And switching to another router won’t necessarily do anything to guard your data.
Is It Safe to Let Websites Remember Me?
Safety in your internet browsing depends on how secure you really need to be! So let’s take a look at what remembering a login really means.
Can Malware Authors Hijack My Anti-malware Software?
Once a hacker has control of your machine they can do anything they want. So yes, they will try to disable your anti-malware… and more!
Should I take the security protection offered after the most recent security breach?
Hackers are very good at sending emails that look like they come from legitimate companies. So, how do you tell the truth from a lie?
Does deleting things really delete things?
Deleting items on your computer usually doesn’t wipe them clean. That’s an extra step.
Should I Cover My Webcam When Not in Use?
Sure, you can cover your webcam with tape. But that won’t solve the real problem… you’ve got malware on your computer!
Can I trust this site or utility?
There are a number of steps you can take to help determine if an unfamiliar utility is safe.
Can I get malware from a picture?
Typically there’s no need to be terrified of clicking on images… as long as you know what to look for and how to manage your protection.
Is the internet just full of scams?
Many advertisements of computer products include promises that they can’t keep, or know that they won’t keep. By making things seem much worse than they actually are they attempt to entice – or even scare – you into purchase tools you simply don’t need.
How Do I Erase Traces of a File I Moved to an External Disk?
Moving a file almost always leaves traces behind. So deleting any file securely is only the first step.
Why does this malware keep coming back?
There are tools out there that can remove malware completely so that it does not come back. But it’s worth taking a look at your own internet habits.
Why haven’t you mentioned CryptoPrevent?
Preventing one type of malware is not going to help you in the long run. And if it does help in the short run… then you may have a bigger problem!
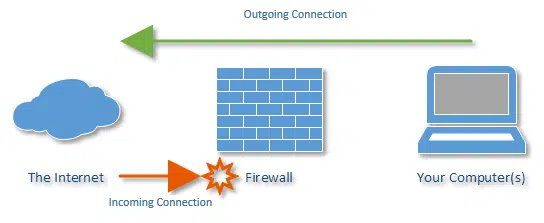
If My Anti-virus is Working Properly, Do I Still Need a Firewall?
There is no such thing as perfect anti-virus software, so it’s wise to have another line of defense when online.
Do I Need to Worry About the Latest Security Breach?
That’s a composite of several questions that I’ve received relating to a recent theft of something like two million user accounts and passwords. I’ll address this specific incident, but I also want to discuss some things to consider with any large scale account theft.
Why does this ad imply I have a criminal record?
It can be pretty frightening when a search result delivers back to you the term you were searching for as an ad… particularly if you were searching for your name. But it might not be any more sinister than that.
Do I Need to Deactivate My Old Anti-virus Before Installing the New One?
It’s best to uninstall old anti-virus software before installing a new one, assuming you make sure to stay safe during the transition.
Should My Anti-virus Scans Include My External Drives?
Malware can certainly insert itself on external drives. The question is how high is the risk?
Is Shockwave Player safe?
The security of Shockwave, like many programs, depends on how you use it, and if you keep it up to date.
How safe is iCloud?
When you put your privacy in the hands of online companies it’s going to boil down to: How much do you trust them?
What Information Does a Laptop Leak on a Wireless Network?
There is very little about your computer that can be transmitted over a WiFi connection… provided you know how to keep yourself safe on the internet.
How does a site identify me when I am using a VPN?
There are lots of modules and widgets available online that help websites appear to identify who you are. Your VPN isn’t involved at all.
Does a VPN give me complete security?
A VPN service can offer a certain amount of security, but it ‘s dangerous to think it’s doing things for which it is not designed.
Is it safe to let my daughter purchase online using my email address?
Sharing an email address may seem like a good idea, as long as you’ve considered all the ramifications.
How does website or VPN encryption work?
Using a bunch of mathematical magic, a key pair is generated. But that’s just where the fun starts.
Why Are Sites Making It Difficult for Password Managers?
Long passwords are your top-line of defense in internet security. Don’t let any trends steer you in the other direction.
Can My Computer Be Hacked if I’m Offline at an Internet Café?
Internet café hackers can get at you in a number of different ways, but how much do you really need to worry?
Do I Need to Stop Using Microsoft Security Essentials?
Recently statements were made by a Microsoft spokesperson that some interpreted as implying that Microsoft was giving up on Microsoft Security Essentials. I went to the source and asked for clarification.
Will my internet activities of years ago come back to haunt me?
We just don’t know how long information will stay public on the internet, so it’s best to assume that it will be forever.
Can an ISP Remotely Access My Computer without My Knowledge?
Knowing who you are dealing with is the key to safe remote access. It’s not the technology that’s a problem. It’s the person on the other end of the remote access!
Why didn’t my firewall stop this malware?
Firewalls and security software are important tools to keep your computer safe. Unfortunately, there’s no such thing as perfect protection from the variety of threats on the internet.
Can a flash drive that has a Linux install on it become infected?
Depending on the format of the drive, how the malware finds you, and how you access Windows, you may or may not have a problem! Does that sound vague enough for you?
Can I Be Sure My Machine Is Malware Free?
Believe it or not… you can’t prove that you don’t have malware. But when your computer slows down, it doesn’t necessarily mean malware.
How Long Does Google Keep My Account Information?
Once you delete your account, your information will be gone… but there may be backups. Ultimately, anything online or shared is completely out of your hands.
Will Someone Hacking My Router Show up on My Computer?
Router hacking is rare, but it can happen. I’ll discuss what it is.
Can a hacker get away with only my address book?
If you’ve been hacked… you’ve been hacked. That means the hacker had access to everything on your computer or in (and linked to) your email account. In either case, you need to review your security.