Articles in Category: Security
How Should I Encrypt the Data on My Laptop?
Protecting data on your computer is key. I’ll look at three common encryption methods.
How Do Websites Store Passwords Securely?
Effective website security is difficult, and often an afterthought. Not all sites or services store passwords securely.
How Did I Get Advertising About the Contents of an Email?
Sophisticated targeted ads can sometimes seem creepy. Here I explore how a few techniques work, and one I can’t explain at all.
What Is “Privilege Escalation” on a CPU?
Privilege is a fundamental concept in modern operating system design. We’ll explore what privilege means as used by the CPU when software runs.
What Do I Need to Do About Spectre and Meltdown?
Spectre and Meltdown sound scary. Here’s what you need to do, which is hopefully what you’re doing anyway, along with an attempt at an analogy.
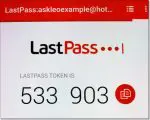
How Do I Back Up LastPass?
It’s important to back up LastPass, because unexpected things happen. What you do with that backup, however, is critical.
Enable Two-Factor Authentication in LastPass
Your LastPass password vault is full of exceptionally important data. Add additional security with two-factor authentication.
Why Do Password-strength Meters Give Different Results?
Password-strength meters don’t always agree. My take is to avoid them completely.
What the Equifax Breach Means to You
One of the largest data breaches in history has left many wondering what to do next.
Why Don’t Anti-malware Tools Work Better?
It’s possible to get malware, even with anti-malware tools installed. Why the heck is that true?
How Can I Tell If a Website Is Safe?
It’s important, yet sometimes hard to tell, if a website is safe. You can stack the odds in your favor. I’ll show you simple tools and smart habits to help spot shady sites before they cause trouble, even if there’s no way to always be 100% sure.
Does a Lapsed Anti-malware Tool Leave an Open Door for Malware?
Letting your anti-malware subscription lapse is never a good idea. I’ll look at why that is, and available alternatives.
How Do I Know If My Computer Has Been Compromised?
You can’t rely on yourself as a malware detector. Learn how to be a malware avoider.
I’ve Been Told My Computer Has a Virus, But My Anti-Malware Program Doesn’t Remove It. What Do I Do?
Making sure your anti-virus program and its definition database are up-to-date is the best way to make sure it can recognize and remove viruses.
What’s the Difference Between a “Trojan Horse”, a “Worm”, and a “Virus”?
There are many different terms that relate to software with malicious intent. Ultimately, however, there’s only one you really need to know, and several things you need to do.
Google Remembers More than You Realize
Wherein we consider how much information we “give away” in our daily lives online.
Why Microsoft’s Response to the Windows Defender Zero Day was Spot-On
Microsoft’s response to the recent Windows Defender zero-day vulnerability was an example of how the system is supposed to work.
Are There Hidden Files that Save Every Keystroke I’ve Ever Typed?
There’s a lot of misinformation, and even paranoia, relating to keystroke logging and privacy. Much of it, however, is based on small kernels of truth.
Sometimes the Threat Is in the Hardware
We spend a lot of time on software-related issues, but malicious activities and privacy violations can happen via hardware as well.
How Do I Encrypt a Hard Drive Using VeraCrypt?
VeraCrypt makes is easy to encrypt whole drives, making it safer to travel with your data. Here’s how to safely encrypt and then access your data.
How Do I Protect Myself from My ISP?
If you’re using an internet connection from a source you don’t trust, there are a few alternatives.
Offline Anti-Malware Tools
Sometimes, the best way to remove malware is to reboot your system and run a completely separate tool. I’ll list some of the most popular.
Windows Defender Offline in Windows 10
When malware prevents your anti-malware tools from working, the built-in Windows Defender Offline is your first line of defense.
Using BitLocker Without a TPM
Should you want to use BitLocker on a machine or virtual machine that doesn’t support TPM, there’s a single hoop to jump through.
What if My Security Software Vendor Gets Hacked?
It’s important to consciously choose which software and online services to trust – whether they are directly related to security or not.
Should I Accept My Security Software’s Recommendation of What to Remove?
Should you trust your security software to make the right recommendations? Typically, yes, as long as you’re using reputable software.
How Do I Encrypt a Disk?
For many, it’s important to be able to encrypt a disk entirely. Particularly if a portable machine contains sensitive data, whole-disk encryption is key.
How Do I Encrypt a Folder?
It’s not uncommon to want to encrypt a folder and all it contains. There are several techniques to encrypt a folder, each with pros and cons.
How Do I Encrypt a File?
Since most encryption tools are designed to encrypt collections of files, the best approach to encrypt a file isn’t always obvious. I’ll look at a couple of alternatives.
Do I Need this Add-on Recommended by this Software Installation?
Many installers include offers of additional software packages. If you don’t pay attention, you could end up with software you don’t need or want.
Possible LastPass Phishing Vulnerability
News broke over the weekend regarding a potential phishing vulnerability that could lead you to give a hacker your Lastpass master password.
Is My ISP Calling Me to Clear Up My Problems with Windows?
In a brazen scam attempt, you may get a phone call from someone claiming to be your ISP or other service provider to “help” you with your Windows problems. Don’t fall for it.
How do I change my LastPass master password?
It’s not something we do often, but occasionally it’s important to be able to change your LastPass master password.
Removing a Redirect Virus
A redirect virus can fool your browser into going to malicious web sites without your knowledge. I’ll outline my experience detecting and removing one.
How Do I Give Someone a Laptop Without Including Access to My Accounts?
It’s not easy to give someone a laptop without giving them access to your personal accounts. Depending on intent and trust, there are steps you can take.
How Do I Remove a Website from My Computer?
How to remove a website from a computer is a common question, yet it actually doesn’t make sense – websites aren’t on your computer. I’ll look at what is.
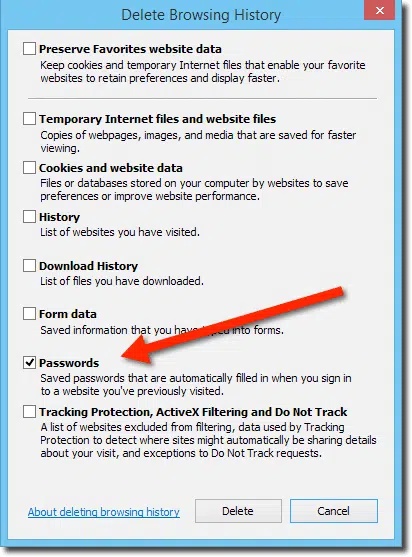
How Do I Disable Remembered Passwords in My Browser?
Web browsers aren’t necessarily the most secure approach to saving your login passwords. I’ll show you how to disable the feature and clear out any previously remembered passwords in IE, Firefox and Chrome.
Do privacy apps really keep me private?
Privacy on the internet means different things to different people. I discuss three different privacy applications out there, explain what exactly each does, and offer some of my own thoughts.
Is anti-virus dead?
Anti-malware tools have never been 100% solutions – but, despite what we hear on the news, they are far from dead!
Can spyware see what you did before the spyware was installed?
When a hacker gets ahold of your computer they can do anything. Keeping them off is the best plan.
Is there software that allows someone to track my emails and texts?
The bad guys can do anything they want to your computer if they can gain access.
If we login to a site securely will our other activities be secure?
Once you are out of https pages you are out of encryption. But there is one good way to secure all your online activities.
Is It Safe to Stay Logged in to My Password Vault?
Remember, the goal is to keep malware off your computer, not to try and manage it once it’s watching you. But there is another security hazard you may not be thinking about.
Why would scanning a disk be quick, but just a file on it be slow?
If that large file is a backup image, then maybe your anti-malware tool knows what I know… that there’s no point in scanning it.
How do I safely switch from one security tool to another?
If you follow a few security measures it’s perfectly safe to uninstall an old anti-malware program and then install your new choice.
Can I Delete What My Anti-malware Program Puts in Quarantine?
Quarantine gives you the option to “rescue” files you might want. Of course there is one way to make sure you always have an extra copy of everything…
Why is my machine so slow after a recovery from malware?
Not only is malware written with bad intent, but it is often written badly. It can leave a mark on your computer’s performance even after it’s been removed.
Would deleting Facebook help clear up a malware infection?
Deleting Facebook won’t help, so I’ll look at more general approaches to removing Potentially Unwanted Programs that are, effectively, malware.
Is My ISP’s Router Safe to Use?
There are a number of compelling reasons to use the router your ISP provides for you. Ongoing support is one. And switching to another router won’t necessarily do anything to guard your data.
Is It Safe to Let Websites Remember Me?
Safety in your internet browsing depends on how secure you really need to be! So let’s take a look at what remembering a login really means.