The Best of Ask Leo!
Articles selected (and updated) and sent to The Best of Ask Leo! email subscription available at http://bestofaskleo.com.
Are Deleted Emails Really Deleted?
Deleted an email and think it’s gone forever? I’ll explain what “delete” really means in webmail and desktop programs, why trash folders and database files can leave messages recoverable, how backups and even court orders can bring them back, and the inconvenient fact that the other person may still have a copy.
Dealing With Video Starts and Stops While Watching: Three Common Causes and Three Possible Solutions
There are common causes, and sometimes simple solutions, for a video that starts and stops as you watch it.
Don’t Call Yourself Stupid
Feeling “stupid” about computers? STOP IT. I’ll discuss why that label holds you back, how attitude changes what you can accomplish, and better words to use when you need help.
How Do I Decrypt Files Encrypted by Ransomware?
Prevention and preparation are the best solutions to ransomware.
The For-Pay Email Providers I Recommend
People often use free email providers only to lose everything when a problem occurs. So what should you look for in a paid email provider?
Is Private Browsing Really Private?
Private browsing sounds safer than it really is. I’ll explain what Incognito mode actually hides, what it absolutely doesn’t, and when it’s still worth using. If you think private mode keeps your online activity secret, you’ll want to see where the real limits are.
Is it Safe to Put Two-Factor Codes in My Password Vault?
Storing 2FA codes in your password vault might slightly reduce security, but the risk is minimal compared to the convenience.
How Can I Tell If a Web Address Is Safe?
URLs are simple in concept, but can be constructed in ways that might fool you. I’ll look at some examples and discuss what’s important.
Does the Recycle Bin Take Up Space, and Where Is It?
The Recycle Bin is your friend. I’ll show you where it lives and how to control the space it uses.
What’s a QR Code, and Can You Trust Them?
QR codes are a nifty way to encode web addresses and other text in a way that’s easy for your smartphone to decode, but they are not without risk.
Are You Afraid of Tracking Cookies
Cookies are placed on your machine by websites — often more websites than you realize. We’ll review cookies and how third parties use them.
What Happens When Applications Die?
Apps don’t last forever, and when one you rely on disappears, it can take your data with it. I’ll show you how to protect yourself so you stay in control.
Should I Use RAID for Backup?
RAID might sound like a clever backup shortcut, but it’s not. In fact, relying on it could make things worse. Learn what RAID does, how it helps (and doesn’t), and why it still won’t save your data when disaster, malware, or mistakes strike.
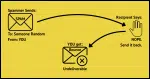
“From” Spoofing: How Spammers Send Email That Looks Like It Came From You
Ever get an email from yourself that you didn’t send? You’ve likely been spoofed. I’ll show how spammers fake your address without touching your account at all, why it happens, and what (little) you can do about it.
Why Don’t Anti-Malware Tools Work Better?
Ever wonder why your antivirus program didn’t catch that virus? It’s not broken. Security is a race, and the bad guys are usually ahead. Learn why security tools can’t stop everything, what that means for you, and the most important step you can take to stay safe.
Why Do System Cleanup Utilities Report So Many Errors on a Supposedly Clean System?
Some system cleaners cry wolf, showing scary error counts to pressure you into buying. Others disagree on what counts as “dirty.” I’ll unpack the scare tactics, the lack of standards, and the risks of using these utilities, plus safer ways to keep your PC running smoothly.
Replying to Spammers to Tell Them to Stop
Tempted to hit “reply” and tell spammers to knock it off? Don’t. Here’s why replying makes things worse, and what you can do to keep spam under control.
What Are the Internet’s Rules About Free Speech?
When people find their posts or comments removed or altered from websites they visit, sometimes they claim that their right to free speech has been violated. That’s rarely the case.
Why Am I Being Labeled a Spammer?
Possibly being labeled a spammer is another reason not to forward political and other emails. Do it enough, and your normal email may not get delivered.
What’s the Difference Between an Email Account, an Email Address, an Email Program, and an Email Service?
What’s the difference between your email service, account, address, and program? I’ll break it down so you’ll know what each term means, why it matters, and how not to get tripped up next time you want to change your email or ask a question.
Can I Tell If Email I Sent Has Been Read by the Recipient?
People want to know if someone’s opened their email. I’ll explain why features and tools claiming to do that can’t work most of the time. I’ll share the only way to know for certain your message was read.
Why Is My Machine Slowing Down?
Is your once-speedy computer crawling? From hidden malware to too many background apps, there are plenty of reasons your PC might feel sluggish. I’ll walk you through the most common causes and what you can do to get things running smoothly again.
How Do I Get an Email Address for Life?
Tired of changing your email every time a service shuts down or your ISP changes? Learn the smartest way to secure an email address that’s truly yours for life, and why relying on free or “lifetime” promises could leave you stranded.
How Does a VPN Protect Me?
A VPN can keep your online activity private, especially on open Wi-Fi, but it’s not magic. I’ll show you what a VPN hides and what it doesn’t, so you can decide if it belongs in your security toolkit.
How Do I Remove Myself From a Computer?
Leaving a job and worried about what’s on your work computer? From browser history to email accounts, traces of you remain. Learn what you can (and can’t) erase, and the smartest way to protect your privacy before you walk out the door.
Why Am I Getting Bounces for Email I Didn’t Send?
Spammers want to send email that looks like it’s coming from someone who can be trusted. They want it to look like it’s coming from you — and you may end up getting the bounce notifications.
What Security Software Do You Recommend? (2025 Q3 update)
My updated guide cuts through the hype with four no-nonsense steps to keep your PC safe. Learn what works, what to avoid, and how to stay secure without overspending or overcomplicating.
Can’t I Just Copy Everything to Back Up?
Just copying your entire drive is not a safe backup, Learn why a real backup program is safer, faster, and more reliable when disaster strikes.
Are There Hidden Files that Save Every Keystroke I’ve Ever Typed?
Worried your computer is secretly saving everything you type? It’s not. While there are hidden files and places keystrokes can live temporarily, there’s no master file of your entire typing history (unless malware is involved). Learn what’s real, what’s myth, and how to truly erase your data.
Is Copyright Still an Issue If Something’s Not Available Anywhere?
Just because something’s old or unavailable doesn’t mean you can make copies of it. I’ll explain why copyright still matters, how technology complicates things, and what you need to know before making that backup or download. It’s simpler and more important than you might think, even if you don’t like the answer.
What Should I Do About the Latest Breach?
Yet. Another. Breach. Don’t panic, I’ll walk you through what you really need to do next. From checking if you’ve been exposed to strengthening your account security, it’s all here in simple terms.
Could Someone Reopen My Closed Email Account?
Closing or abandoning an email account can have unexpected and perhaps unwanted side effects. I’ll explain what those are and what options you have.
CHKDSK: What Is It and How Do I Run It?
CHKDSK, short for Check Disk, is a utility that checks the integrity of the files and file structure of your hard disk. I’ll walk you through it.
The Event Viewer, Explained
Many Windows components log messages and use Event Viewer to display them. Sadly, the messages are often cryptic and inconsistent, and the result is a mess that scammers take advantage of.
Extend Your Wi-Fi: Simple Fixes for Better Home Coverage
It can be difficult to get wireless network coverage throughout your home.
What Backup Program Should I Use?
Backing up your computer’s data is critical. The best program is whatever you’ll actually use.
Why Can’t I Talk to a Real Person?
There are many reasons you’re more likely to be directed to online and self-help resources than be able to talk to a real person.
Open-Shell: Regain Your Start Menu
The single biggest complaint about Windows 11 is the Start menu. Don’t like it? There’s an app for that.
How Do I Get My Windows Computers to Network With Each Other?
Home networking can be very difficult. I have a few tricks that work well for me.
Why Doesn’t My New, Empty Hard Drive Show All the Advertised Space?
Terms used to measure disk space can be ambiguous. A megabyte may mean one thing to you and another to your computer.
How Can It Be Safe to Give My Information to Anyone?
If we listen to the news, we might never leave the house, much less go online. I’ll review why that kind of thinking is opportunity lost as well as how to stay safe.
What Happens at Windows 10 End of Support?
The end of support for Windows 10 means Microsoft will no longer issue security updates. Here’s how to continue using it safely.
Are Free Email Services Worth It?
Free email services and accounts are convenient and ubiquitous. They can be used safely if and only if you take responsibility for that safety.
What’s a Screenshot, and How Do I Take One?
A screenshot — an image of your computer screen saved as a picture — can eliminate a lot of frustration.
How the Internet Is Breaking Journalism
As we use the internet, we need to be more vigilant than ever to separate truth from falsehood and recognize what’s important over what’s popular.
Would You Give Your Wallet to a Stranger?
Many people seem more than willing to give a complete stranger access their computer. It’s safer to give them your wallet.
Should I Back Up If My Machine Is Infected?
If you believe your machine is infected, first protect and preserve your data.
How Does Blocking Pictures in an Email Protect My Privacy?
Email programs commonly block remote images. I’ll look at why, and how spammers and others use remote images for good and evil.
The Most Important Attitude
There is one approach to life — one setting in your psyche — that affects your experience with technology much more than any lack of skill or knowledge.
Why Doesn’t Blocking Email Senders Work?
Most email programs can block email from a specific address. Unfortunately, that’s completely ineffective when it comes to spam.