Whole-disk encryption is an important aspect of security for many people. If you encrypt a disk properly, and your computer falls into the wrong hands, those hands won’t be able to access your data.
While the average computer user may or may not need to use whole-disk encryption (it depends on the type of data they store, as well as their own level of concern), it’s an important tool for business, government, and particularly for portable computers, such as laptops and tablets.
I’ll review a couple of my recommended approaches to encrypting a disk completely.
Become a Patron of Ask Leo! and go ad-free!
Encrypt a disk using BitLocker
If you’re running a Professional edition of Windows or better1, and your disk is formatted using NTFS (most Windows hard disks are these days), Windows can encrypt your disk using BitLocker.
Much like encrypting folders, the technique is very simple. Right-click on the drive in File Explorer and click on Turn on BitLocker.
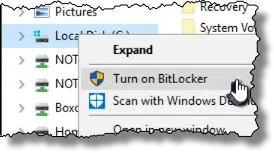
You’ll be asked exactly how you want to unlock the encrypted drive when you want to use it. You can choose to either type in a password (actually a passphrase), or set up a USB drive to act as a secure key that, when inserted, causes the drive to be unlocked.
We’re more familiar with passwords, and since they are less easily lost or broken than a physical USB drive, I prefer them.
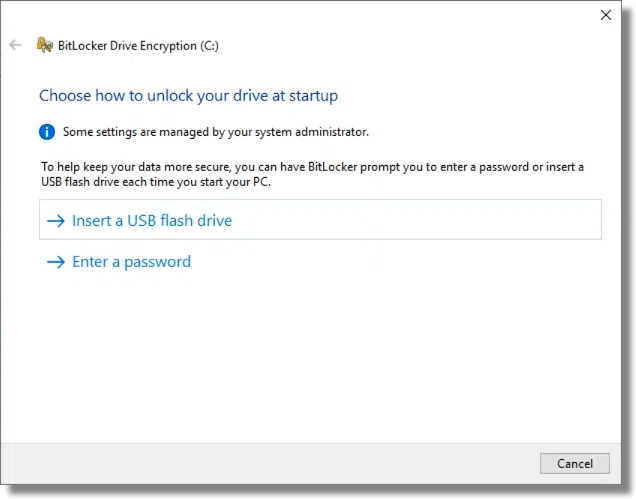
Click on Enter a password. Enter an appropriately secure password, re-enter it, and click Next.
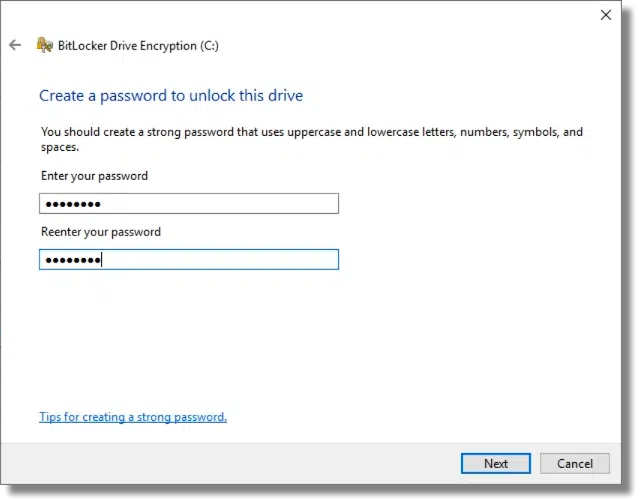
This step is critical. You must save a copy of the recovery key somewhere. Should you ever forget your password (or lose that USB key, if that’s what you selected at the start), having a recovery key is the only way you’ll regain access to your encrypted data. Exactly how you save it is less important than that you save it somewhere, so that some days, months, or even years from now, you’ll have it should you need it.
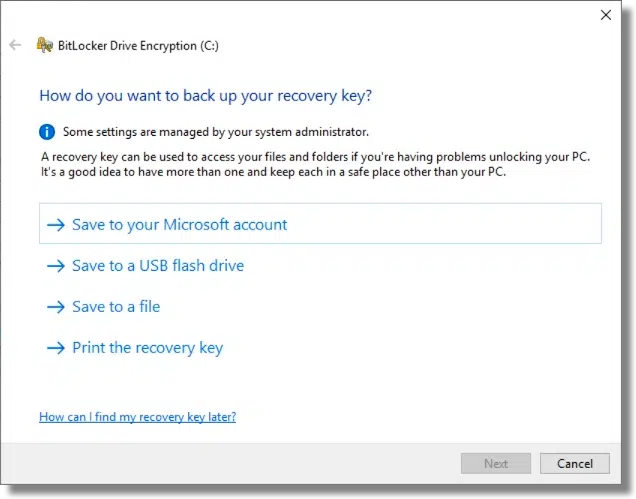
I elected to save to a file.
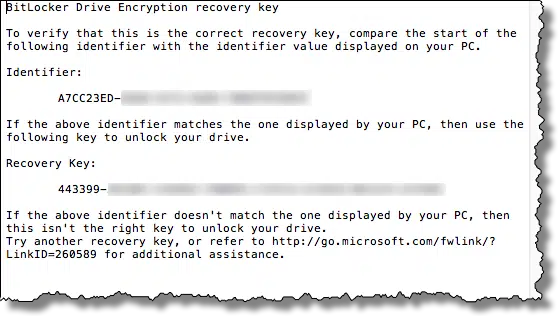
Note: this is sensitive data. Be sure to keep your recovery key in a secure location. Anyone who has access to it can decrypt your drive.
BitLocker then gives you the option to immediately encrypt only the existing files on your system, or all of the files and currently free space.
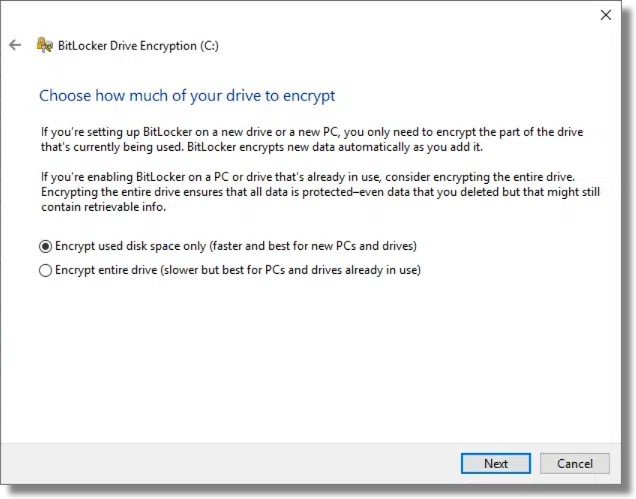
The issue here is that when you delete a file in Windows, the data for that file is not actually removed from the hard disk. It’s marked as free space, and doesn’t actually go away until sometime later, if and when new data is written on top of it. That implies that if you’ve used your machine for any length of time, the free space may actually have fragments of sensitive data. If you’re unsure, select “Encrypt entire drive”. Regardless of which you choose, data written to the drive from here on out will be encrypted.
If you’re running Windows 10, BitLocker asks yet another question: the “mode” to be used.
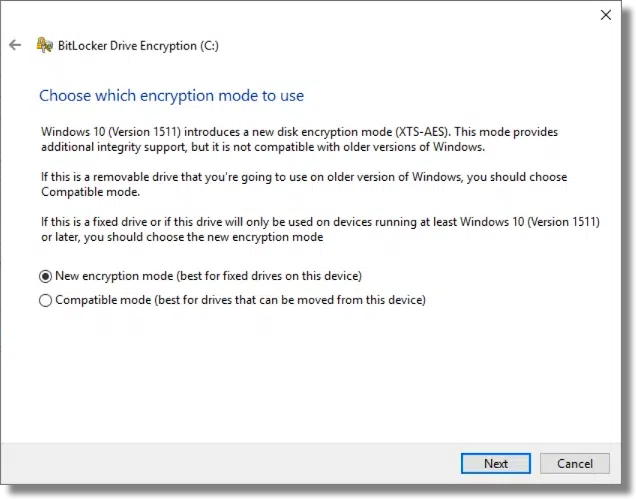
This is basically an improved encryption algorithm. If you’re encrypting your internal hard drive, I recommend selecting this new mode. If, as the prompt indicates, this is a drive that might regularly be taken to other machines, use the older, compatible mode.
Finally, it’s time to encrypt the drive.
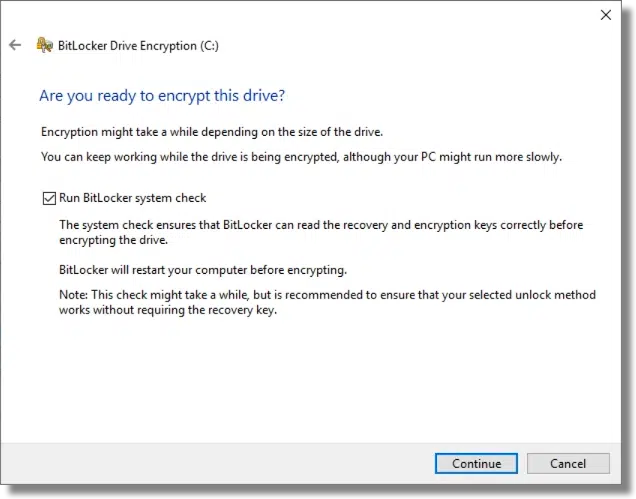
A reboot is required to begin the process, and you’ll need to specify the encryption password to begin.
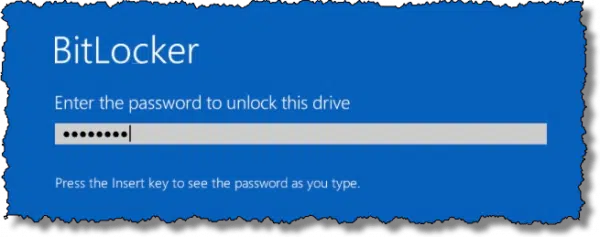
This is the same message you’ll see any time you reboot your machine.
Exactly how long the encryption process takes depends on many factors, including the size of your disk, the speed of your machine, and whatever else you might be doing while the encryption proceeds. You can continue to use your computer while the disk is being encrypted.
The good news: BitLocker is strong, secure encryption built in to Windows Pro editions or better. Once encrypted, other than specifying the password to unlock the drive at boot time, it’s completely transparent.
The bad news: BitLocker is Windows only, and not available for Windows Home editions, or for drives formatted using anything other than NTFS. While it can be used to encrypt disks to be shared with others, only using machines running a compatible edition of Windows (Pro or better, supporting the same encryption mode) can decrypt the drives. Using BitLocker assumes you trust Microsoft, particularly if you use the option to store a backup of your recovery key in your Microsoft account.
Encrypt a disk using VeraCrypt
VeraCrypt2 is a third party tool that supports, among several other things, whole-disk encryption.
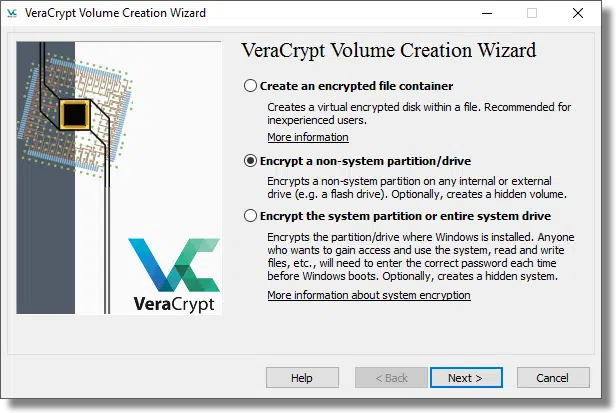
I’m not going to cover this option in detail, as the VeraCrypt documentation is quite good.
The good news: in many regards, VeraCrypt works almost exactly like BitLocker, in that once you specify the appropriate passphrase to gain access to an encrypted disk, its operation is transparent. VeraCrypt is free. Volumes encrypted using VeraCrypt should be inherently portable to any system, including non-Windows systems on which VeraCrypt has been installed. VeraCrypt works with all editions of Windows.
The bad news: If you lose or forget your passphrase, your data cannot be recovered. There is no back door. VeraCrypt is third-party, open source software, which may raise trust issues for some.
Encrypt almost an entire disk using VeraCrypt
Another approach is very similar to the approach I outline in How Do I Encrypt a Folder? Rather than using whole-disk encryption, create a VeraCrypt container that is as large as possible on the disk you’re wanting to encrypt.
So, for example, let’s say the disk you want to use is 100 gigabytes in size, and is empty. You would use VeraCrypt to create a container as large as possible – approaching 100GB3. That container would appear on the drive as a single, large file. When you mount it using VeraCrypt, another drive letter appears on your system. Files you read and write on that drive are transparently encrypted in the VeraCrypt volume. When it is dismounted, the drive letter goes away, and your encrypted data cannot be accessed.
The good news: VeraCrypt container volumes can be copied to other hard disks, or even other operating systems, and can be accessed as long as VeraCrypt is installed and you know the passphrase.
The bad news: This approach does not work for system drives (the drive containing Windows and from which you boot your system).
My recommendation
Once again, what’s most appropriate for you will depend on your situation. Some general guidelines include:
- To encrypt your system drive, I recommend using the system-provided encryption if you can. That means using BitLocker in Windows.
- If you can’t use BitLocker for whatever reason (perhaps you have Windows Home Edition), then use VeraCrypt if you want to encrypt your system drive.
- For any other drive – particularly those you might consider sharing with other machines – consider the “almost whole disk” approach I’ve outlined, using VeraCrypt containers instead of whole-disk encryption. It’s technically less complex and somewhat less fragile. It’s also somewhat more flexible, allowing you to copy the container to other drives or machines, should you be so inclined.
Regardless of which approach you decide to take, make absolutely certain that you have your recovery key or passphrase backed up somehow. Without them, your data will be lost.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!


What caused you to change your mind about BitLocker?
https://askleo.com/avoid-bitlocker/
Short version: they’ve taken steps to really, REALLY, REALLY encourage you to save the recovery key. And note that I’m most comfortable recommending it for full-disk, specifically system disk, encryption, where portability and interoperability aren’t an issue. I need to go back and update that article.
BitLocker has always prompted for a recovery key to be created and I don’t think the process has changed much, if at all, since the Vista days (but I could be mistaken about that).
Will these options work for a thumb drive?
Yes, but it’s probably not as easy simply installing the program and using it. You would be able to use Veracrypt on a thumb drive but you would need to have administrator privileges to install Veracrypt on the computer you will access it from.
These instructions from Microsoft explain how to encrypt a USB flash drive using Bitlocker. But I believe you’ll need admin privileges to enable Bitlocker on a computer, and you can only use Bitlocker on computers with the Professional edition or higher.
https://technet.microsoft.com/en-us/magazine/ff404223.aspx
I personally find using an encrypted .zip file the most practical and simple method on a flash drive. See the section on “7-Zip and Zip files in general”
https://askleo.com/how_do_i_encrypt_a_file/
That is what I do now, only using WinZip. The problem is, it allows you to see the file names without knowing the password and I need to avoid that.
To encrypt the file names, first zip the file(s) unencrypted, then zip the zipped file, but encrypt it this time. An extra step, but you get encrypted file names, because when they look, all they’ll see is the inner zip file. That’s what I do with Boxcryptor.
I use PKZIP, and it has an option to encrypt the filenames, too, but the downside is that the other zip programs probably won’t be able to decrypt it. I’m not sure if this feature uses digital signatures.
Would file encryption work to thwart Ransomware? How about encryption on a Mac or Linux?
No. If you use file encryption, that would only mean that your encrypted files would be encrypted a second time by the ransomware.
“Would file encryption work to thwart Ransomware?” – No. Not at all.
Actually it’s not quite that black and white. Or, as my most common answer goes, “it depends”.
MOST ransomware encrypts only certain file types, typically based on the extension of the file name. So it might encrypt “.docx” files, along with a lengthy list of other commonly valuable file types. (One of the variables in ransomware is, indeed, the length of that list – the number of different types of files that it’ll attempt to encrypt.)
IF your encryption technique involves renaming the file – for example renaming “important.docx” to “important.docx.axx”, and “.axx” is not on the of file types encrypted by the particular ransomware variant encountered, then the file will not be impacted by that ransomware. And yes, this implies that simply renaming a file to a non-targetted extension would also cause that ransomware to bypass it.
As you can tell, whole disk encryption, as discussed in this article, doesn’t change file names, so Ray’s and Mark’s answers stand: whole disk encryption has no effect on ransomware. HOWEVER other recently discussed encryption techniques – specifically TrueCrypt/VeraCrypt vaults, individual file encryption and so on – do stand a reasonable chance of bypassing most (though not all) ransomware threats.
It’s worth noting that “.zip” files are likely to be targeted simply because they’re ubiquitous – thus using .zip for some kind of ransomware protection is not particularly useful.
In fact, I’ll go one step further: relying on your own encryption is not a way to plan for, mitigate, or otherwise “protect yourself from” ransomware. Do all the things you do to protect yourself from all malware – including those all important backups. The topic remains interesting, though, for those folks who have been impacted by ransomware – some of the files on their machine may have dodged a bullet depending on the encryption they may have used, and the specific attack targets of the specific ransomware encountered.
“In fact, I’ll go one step further: relying on your own encryption is not a way to plan for, mitigate, or otherwise “protect yourself from” ransomware.” – Absolutely. While encrypted files may or may not be re-encrypted – and that could depend on whether or not the files were accessed while encryption was occurring – encryption should certainly not be considered to be a defence mechanism.
Another problem with relying on an extension change to protect you against ransomware is fine today, but who knows if tomorrow, a version of ransomware encrypts everything, then you’re out of luck. As Leo suggests, keep a few generations of backups and you can always recover.
RE. Encryption on Mac and Linux:
Yes, VeraCrypt has MAc and Linux versions.
I still have excellent results using the last version of TrueCrypt for full disk and boot sector encryption. It worked when I upgraded to Win10 and then when I switched back to Win7. Of course it had to be removed to change the O/S.
So my computer is vulnerable if someone steals my computer when the RAM is still active but that is a ridiculous, unlikely. I am not really too paranoid and just want basic protection but the last version of TrueCrypt is so moron proof to install and protect the entire system without any noticeable overhead. Just too lazy to look at the other options.
TrueCrypt has potential vulnerabilities to hacking. VeraCrypt is the continuation of the TrueCrypt project. In other words, it’s TrueCrypt with vulnerabilities being patched as they show up..
The thing I particularly love about Leo is that every question I might have thought of is answered by him in advance. But something went wrong this time. There is no indication of what it really means to encrypt a disk, presumably an external or internal hard drive. Can you continue to use it or are you constantly entering a password every time you try to access a file on that disk.? The basic question of how you use the disk after encryption is completely ignored. Well, one omission in a sea of brilliant discussions is not much of a blemish.
I still use Truecrypt (Leo’s pointer years ago) and I love it. If only every program could be presented with such clarity and executed with such precision. It is still doing yeoman work on Windows 10. I know that I can use encrypted drives as though they were just normal, once I enter the password at the beginning of a session. Is this true of all the encryption programs?
When you encrypt a disk you enter a password once, to boot. Then as long as the system is running the disk is accessed normally.
You might want to switch to Veracrypt. It is the continuation of the Truecrypt project and is receiving security updates and bug fixes. Truecrypt is no longer supported is is more vulnearble to exploits.
Hello Leo,
I have some questions and potentiality some problems regarding backups and encryption. I am hoping you or one of your other followers might be able to clear my concerns up. I have found some discussions on these issues on your website but they don’t seem to address my concerns completely.
First, I am running Windows 10 Home edition, upgraded from Windows 8.1. My computer is an HP Envy 700-214, Intel Core i5-4440, 3.1 GHz CPU, with 120 GB RAM and a 1.8 TB hard drive. All this behind a Linksys WRT 1900 ACS router. I have set the router up according to the suggestions from Michael Horowitz’s Router Security Website, so I feel my system is secure from an internet standpoint.
I have been using Acronis True Image and am currently running the 2016 version. I back up incrementally every day to a Seagate Backup Plus, 2 TB USB drive. I have 2 of these and alternately backup to one and put the other in a safe deposit box and then switch at the beginning of every month. So I have 1 offsite and one as an active backup. I am particular about my backups because I keep all if my financial data, (bank accounts, brokerage data, portfolios etc.) on my computer. As I see it my main vulnerability is the data. If someone were to break in and steal my equipment they could of course see my entire financial life. Thus enter encryption. I have investigated various encryption alternatives and concluded that since TrueCrypt no longer seems viable, VeraCrypt would meet my needs. I would like to include my sensitive files in a separate encrypted container and leave the rest of the drive unencrypted. Thus I would end up with both encrypted and unencrypted files for Acronis to write to my backup drives.
I tried to use Acronis Cloud but the backup operation kept crashing and instead of resuming where it crashed, it continually started over. I burned up my data allocation from my ISP in 2 days. My ISP has a rule that if I exceed my allocation they charge me a higher data rate, and if I exceed my allocation for 2 consecutive months they suspend my account for 6 months for overuse. My current plan allows for a bandwidth of 300.00 GB per month which I think should be sufficient for my needs. But based on my experience so far a cloud based backup solution doesn’t seem practical.
My problem is that based on what I read on the Acronis website, as well as other websites, Acronis True Image as well as some other backup software, seem to have or have had, problems with backing up and restoring encrypted data. I have contacted Acronis and their response is less than I would have hoped. They merely refer me to their support site. I like Acronis and the software seems easy to use and has the features I need. Is this a legitimate concern with respect to Acronis and other common backup routines? Or is there a better alternative for a backup solution? Your thoughts please.
Regards,
Leon
“I have set the router up according to the suggestions from Michael Horowitz’s Router Security Website.” – Some of the advice on that website is not particularly good – especially in relation to MAC filtering and SSID hiding (which makes a router less secure, not more secure). Leo has an article on MAC filtering here:
https://askleo.com/is_mac_address_filtering_a_viable_wireless_security_option/
Backing up/restoring encrypted data is pretty straightforward. That said, encryption does increase complexity – and the more complex something is, the more likely it is to go wrong.
Given the risks associated with encryption – namely, that messing up can make data completely irrecoverable – I always encourage people to think about whether it’s really the best option (especially when it comes to desktop systems that remain in the home). I’ve known far more people who’ve lost their data because it was encrypted than people who’ve been stung because their data was unencrypted. Consider too that the average burglar will have no interest in your data and will simply want to wipe your computer and sell it on the street corner or Craigslist as quickly as possible.
As with most things, it’s a matter of weighing up the pros and cons.
I personally use DropBox paid as my cloud solution. OneDrive or Google Drive or whatever you prefer would work similarly. I keep all of my personal files and folders inside the DropBox folder. I use the free version of Boxcryptor Classic for my encrypted files. I prefer that to Veracrypt because of the bandwidth issue. Boxcryptor encrypts each file separately and only the changed files are uploaded and downloaded, whereas with Veracrypt, the whole container has to be uploaded. If your encrypted files consume just a little space, this might not be a big issue. One disadvantage with the free Boxcryptor is that the file names are not encrypted. I get around this by zipping the files I want to hide the names of within my Boxcryptor volume.
And regarding Ray’s comment about the potential danger of data loss due to encryption errors, having a few backups would mitigate this, and another advantage of Boxcryptor is that since individual files are encrypted, a glitch in the encryption process or file damage would only damage one file and not the whole Veracrypt volume. But I wouldn’t consider that a major issue if I’m sufficiently backed up.
“And regarding Ray’s comment about the potential danger of data loss due to encryption errors, having a few backups would mitigate this.” – I was actually referring to the fact that encryption can be a dangerous tool – especially in the hands of somebody who doesn’t completely understanding what they’re doing. Should somebody forget password/phrase – which is something we’ve all done at one time or another – and they’ll lose access to their data. Permanently. And this is something that happens very, very frequently – as anybody who works in the data recovery industry will tell you (“Help! Can you get my data back?” “Nope”).
I’m not suggesting that people shouldn’t encrypt their data, simply that they should think about whether it’s really the best option. And in the case of a desktop PC that’s sitting in the home of the average home user, the risks associated with encryption may well be greater than the risks associated with non-encryption.
“I use the free version of Boxcryptor Classic for my encrypted files.” – And this is why that’s important (if the data is sensitive, anyway):
https://www.troyhunt.com/the-dropbox-hack-is-real/
To Leon Williamson: You have one problem, and options for the other issues. Your problem is your ISP limiting your bandwidth. I was in that mode while using Hughesnet a few years back, then I switched to a local startup company that solved that problem and more. I no longer need to worry about using up my monthly allocation, so I use DropBox as one of my off site backups. Works great.
About the other issues … I have not used Acronis. I am using Macrium Reflect. I subscribe to their more robust version, but even the free version does very well. It does not care about whether the files or folders are encrypted, it just back up the whole system as you prefer. For encrypted files and folders I still use TrueCrypt which is as reliable as always. I may migrate over to VeraCrypt.
So, given your bandwidth problem, try to find another ISP if that is an option. If not, back up locally using Macrium. You will not regret that transition from Acronis. Play with the free version to get your experience. The only thing it lacks is that, as far as I remember, it will not make incremental backups, whereas the paid version does.
My thanks to all who took the time to comment on my problem. Your responses were very helpful.
Thank You
I attempted to turn on bitlocker and received the following error, What am I missing?
This device can’t use a Trusted Platform Module. Your administrator must set the “allow bitlocker without a compatible TPM” option in the “require additional authentication at startup” policy for OS volumes.
How do I set this up, I looked in the BIOS and there is no reference to TPM.
I am running windows 10 Pro on an HP Pavilion DV6 machine with a 1TB hard drive.
That’d be right here: https://askleo.com/using-bitlocker-without-a-tpm/
Mark Jacobs:
I am running Windows 7 Home Premium on a Dell Studio 1535 and I have a Seagate 4TB external drive as my auto backup.
I would like to install a encryption program but after reading all the advise above I am a lot confused. Is there a recommended program
for my system? I’m retired and have a fairly good knowledge in the PC world.
Could you help me out?
Thank you in advance for your assistance.
Jerry Barbur
For an external hard drive, I’d use Veracrypt as recommended in this article.
I would like to share my experience. I am also on a metered ISP connection.
On my main computer I do a local image backup to an external drive using Macrium Reflect paid version. I have shared data on a network drive, RAID 1 setup.
My critical documents and data are sync with the network drive, a USB drive on my main computer and a second computer. All data files on the main computer and the external drive are cloud stored using Backblaze. I did have to monitor the initial backup to Backblaze to avoid going over my data cap. After the initial upload it only updates modified files, so it was no problem after the initial upload.
So I end up with a cloud storage with Backblaze and 3 local copies of my data plus one image backup. I guess I am paranoid, but I only once lost a small amount of data (about 2 dozen critical files) from a hard drive failure. That’s spread over a 15 year period. I still have emails from 1990.
I agree with Leo. Backup, backup, and backup again.
I have now enabled Bitlocker on my Backup USB drive and use it as another point of protection from Ransom Ware,
Prior to running a backup i run the following batch file
————————————————————————————————————————————
Cls
mountvol A:\ \\?\Volume{b7e4e1a8-c0ef-4a75-aa72-6af81395d4cf}\
manage-bde -unlock a: -recoverypassword 123456-123456-123456-123456-123456-123456-123456-123456
Exit
————————————————————————————————————————————
The above mounts the backup Volume and unlocks the Bitlocked drive and at the end of the backup process i run the following batch.
————————————————————————————————————————————
Cls
manage-bde -lock -forcedismount A:
mountvol A:\ /d
Exit
————————————————————————————————————————————
The above relocks the drive and dismounts the volume making it invisible in Windows.
Whilst still not perfect it goes along way to protecting unattended backups, Ransomware would need to find and mount volumes and also brute force the Drive encryption possible but unlikely , i also do some other tricks with permissions on the batch files which make them unreadable to all but the backup software and lock the permissions on the backup drive whilst backups are running .
I don’t believe encrypting your files will give much protection against ransomware. Ransomware can also encrypt encrypted files.
Not really correct Mark. It can’t encrypt the files if the drive is encrypted, because it cannot access the files without first breaking the encryption lock.
If it uses whole disk encryption or a large encrypted volume then it won’t be able to encrypt it. If the files are encrypted individually, then they can be re-encrypted.
And if whole-drive encryption is used the the drive may appear unencrypted when mounted and in use, so its contents could still be encrypted. Whole drive encryption really only protects when the drive isn’t mounted, or the computer is off.
Correct Mark and Leo, the whole drive is encrypted so until you enter the unlock code there is no access period. Really taking the drive offline maybe a little redundant now, but this idea is a work in progress and was the first method i was using to get some protection for unattended backups.
So now the main vector of attack is when the drive is actually in the process of being backed up , then it is vulnerable, to mitigate this i am playing around with scripting permissions changes at the start and finish of the backup which seems promising. (denying all users and administrators access whilst backup in progress and only allowing a special “backup account” Read / Write).
At the start of a backup
-The drive is brought online
-The Bitlocked drive is unlocked
-The new permissions are applied
-Backup commences
At the end of the backup
-Permissions are set to normal
-Drive is locked
-Drive is taken offline
My PC has just one internal hard disk. This hard-disk has three primary partitions that host Windows10home, Ubuntu20.04LTS & Fedora34 Operating Systems. I have installed Veracrypt software in the operating system Windows10home. Would you care to let me know what exactly is the technically informed manner to use the Veracrypt software in Windows10home Operating system to encrypt only the 1TB partition on which Windows10home OS’s files are installed? Further, can I install Veracrypt software in the two linux operating systems (I hear Veracrypt is a multiplatform software and comes for linux as well) and encrypt their partitions? Finally, if I encrypt the partitions, will I be asked for the Veracrypt passphrase after I select the operating system from the grub bootloader? Else how will I choose the OS?