Articles in Category: Security
Why Do People Think a Phone is More Secure than Email?
Even though digital communications are generally safer than their old analog counterparts, many people still mistrust them.
Can My School Tell I’m Using Tor?
Your school (or whoever provides your internet connection) can see what you’re connecting to. Do they? There’s no way to know.
What Happened to TrueCrypt and What Do I Use Instead?
The TrueCrypt project was suddenly and without warning shut down. I’ll look at a little of the history and what you should use instead.
Which Files Were Affected by a Hack or Malware?
After a hack or malware infection, you’ll want to know you’ve cleaned up the resulting mess. The news is not good.
Can My Mobile Provider Track What I Do Online?
Your mobile provider is indeed your ISP when you use their data services, and that means they can see a lot of your activity.
How Can I Recover My Current Account Password
Trying to recover the existing password for an online account is usually an exercise in frustration. There’s one possible straw to grasp at.
Is an Up-to-Date Browser Secure on an Out-of-Date OS?
An up-to-date web browser is important, but it’s not the whole picture, by far.
How Can I Tell If a Download is Safe?
Checking whether a download is safe before you download it is nearly impossible. Your best defense is your own skepticism, plus anti-malware tools to scan what you choose to download.
The State of Passwords in 2019
Password are here to stay, at least for a while longer. Until they die, here’s quick review of how to make sure yours are as secure as possible.
How Do I Get Rid of Ask.com?
You should be able to remove any toolbars or browser settings that have been added to your computer.
Password Checkup: A Recommended Chrome Browser Extension
Password Checkup is a browser extension that tells you if the password you’re using has been discovered by hackers.
How Do I Get Rid Of “overseer.exe”?
Overseer.exe can be left behind after an uninstall of Avast Free Anti-virus. Deleting it is a two-step process.
How Do I Keep My Kids Safe from Internet Garbage?
There’s a lot of garbage on the internet, and it’s difficult to prevent your children from seeing it. There are tools to help and steps to take.
Use BitLocker to Bypass Potential Self-Encrypting Drive Vulnerabilities
Headlines to the contrary, it’s BitLocker to the rescue to protect yourself from some vulnerabilities discovered in drives providing hardware-based encryption.
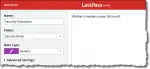
How Can I Use a Password Manager for My Security Questions?
Password vaults are good at keeping track of passwords, but not answers to security questions. There is a technique you can use to help.
Don’t Lose Your Phone: Here’s What Can Happen (and How to Prepare)
Given how much we’ve come to rely on them, are you prepared to lose your mobile device?
BoxCryptor: Secure Your Data in the Cloud
Many online cloud storage providers encrypt your data — which means they can decrypt it themselves. BoxCryptor is a great solution to ensure that your online data remains private, regardless of how it’s stored.
How Can I Send a Document to Someone Securely?
Email is a fairly insecure media. There are many things that can go wrong when email gets delivered, and protecting yourself can be difficult.
What Can a Website I Visit Tell About Me?
Websites can collect a fair amount of information about you. Let’s look at what every website sees.
Can My ISP See What I’m Doing If I Use a Virtual Machine (VM)?
A VM doesn’t get you any additional privacy from your ISP… although it might be a convenience as part of a more complete solution.
VeraCrypt: Free Open Source Industrial Strength Encryption
VeraCrypt provides a solution for encrypting sensitive data — everything from portable, mountable volumes to entire hard disks.
How to Tell if Your Email, Computer, or Facebook Has Been Hacked
Unless a password’s been changed, it’s difficult for a typical user to tell if their computer or account has been hacked.
Download Your Facebook and Google Data
It’s a worthwhile exercise to download the data made available by Google and Facebook, if only to realize exactly what information is being kept.
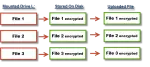
How Should I Encrypt the Data on My Laptop?
Protecting data on your computer is key. I’ll look at three common encryption methods.
How Did I Get Advertising About the Contents of an Email?
Sophisticated targeted ads can sometimes seem creepy. Here I explore how a few techniques work, and one I can’t explain at all.
What Is “Privilege Escalation” on a CPU?
Privilege is a fundamental concept in modern operating system design. We’ll explore what privilege means as used by the CPU when software runs.
What Do I Need to Do About Spectre and Meltdown?
Spectre and Meltdown sound scary. Here’s what you need to do, which is hopefully what you’re doing anyway, along with an attempt at an analogy.
How Do I Back Up LastPass?
It’s important to back up LastPass, because unexpected things happen. What you do with that backup, however, is critical.
Enable Two-Factor Authentication in LastPass
Your LastPass password vault is full of exceptionally important data. Add additional security with two-factor authentication.
Why Do Password-strength Meters Give Different Results?
Password-strength meters don’t always agree. My take is to avoid them completely.
What the Equifax Breach Means to You
One of the largest data breaches in history has left many wondering what to do next.
Does a Lapsed Anti-malware Tool Leave an Open Door for Malware?
Letting your anti-malware subscription lapse is never a good idea. I’ll look at why that is, and available alternatives.
How Do I Know If My Computer Has Been Compromised?
You can’t rely on yourself as a malware detector. Learn how to be a malware avoider.
I’ve Been Told My Computer Has a Virus, But My Anti-Malware Program Doesn’t Remove It. What Do I Do?
Making sure your anti-virus program and its definition database are up-to-date is the best way to make sure it can recognize and remove viruses.
What’s the Difference Between a “Trojan Horse”, a “Worm”, and a “Virus”?
There are many different terms that relate to software with malicious intent. Ultimately, however, there’s only one you really need to know, and several things you need to do.
Google Remembers More than You Realize
Wherein we consider how much information we “give away” in our daily lives online.
Why Microsoft’s Response to the Windows Defender Zero Day was Spot-On
Microsoft’s response to the recent Windows Defender zero-day vulnerability was an example of how the system is supposed to work.
Sometimes the Threat Is in the Hardware
We spend a lot of time on software-related issues, but malicious activities and privacy violations can happen via hardware as well.
How Do I Encrypt a Hard Drive Using VeraCrypt?
VeraCrypt makes is easy to encrypt whole drives, making it safer to travel with your data. Here’s how to safely encrypt and then access your data.
How Do I Protect Myself from My ISP?
If you’re using an internet connection from a source you don’t trust, there are a few alternatives.
Offline Anti-Malware Tools
Sometimes, the best way to remove malware is to reboot your system and run a completely separate tool. I’ll list some of the most popular.
Windows Defender Offline in Windows 10
When malware prevents your anti-malware tools from working, the built-in Windows Defender Offline is your first line of defense.
Using BitLocker Without a TPM
Should you want to use BitLocker on a machine or virtual machine that doesn’t support TPM, there’s a single hoop to jump through.
What if My Security Software Vendor Gets Hacked?
It’s important to consciously choose which software and online services to trust – whether they are directly related to security or not.
Should I Accept My Security Software’s Recommendation of What to Remove?
Should you trust your security software to make the right recommendations? Typically, yes, as long as you’re using reputable software.
Do I Need this Add-on Recommended by this Software Installation?
Many installers include offers of additional software packages. If you don’t pay attention, you could end up with software you don’t need or want.
Possible LastPass Phishing Vulnerability
News broke over the weekend regarding a potential phishing vulnerability that could lead you to give a hacker your Lastpass master password.
Is My ISP Calling Me to Clear Up My Problems with Windows?
In a brazen scam attempt, you may get a phone call from someone claiming to be your ISP or other service provider to “help” you with your Windows problems. Don’t fall for it.
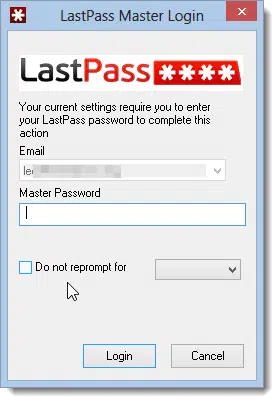
How do I change my LastPass master password?
It’s not something we do often, but occasionally it’s important to be able to change your LastPass master password.
Removing a Redirect Virus
A redirect virus can fool your browser into going to malicious web sites without your knowledge. I’ll outline my experience detecting and removing one.