encryption
What Is a Passkey?
Passkeys are a new form of signing in that promise to be easier and more secure. I’ll walk you through some of the high level concepts and how they work, and how they keep you safer than passwords.
How End-to-End Encryption Protects Your Messages and Where It Fails
You would think that for such an important concept as end-to-end encryption there’s be some agreement on exactly what it means. Sadly, not so. There’s the correct definition, and then there’s the marketing definition. One protects you, the other not so much.
Can My School See My Email and Other Messages?
Numerous people and programs can track your internet activities. But are you really that interesting?
Can Someone Install Something on My Computer When It’s Not Logged In?
If your computer is not physically secure, someone could install something even if you’re not logged in.
Can My ISP Monitor My Internet Connection?
Your ISP controls your internet connection, and it’s easy for them to monitor the data you send and receive. The question is, why would anyone monitor your internet?
Password Update Without Re-encrypting: How?
If your password is used to encrypt your hard disk, how can you change your password and still be able to decrypt your disk?
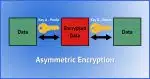
What Is Public Key Cryptography?
Public key encryption is the workhorse of security online. I’ll review just what it is and how it’s used at a high level.
What Encryption Software Do You Recommend?
There are many different tools for encryption. The right one depends on what you’re attempting to accomplish.
Cryptomator: Encryption for Your Cloud Storage
Cryptomator is a powerful tool to protect the data you store in the cloud.
How to Back Up Encrypted Data
Encrypting your data is important for security, but it also adds risk that’s easy to overlook when backing up.
How Tech Mistakes in Media Harm Us All
Please don’t base your understanding of technology on what you see in TV and movies.
Protecting Your Privacy: Points of Vulnerability
Tracing the privacy and security of the path from your fingertips through the services you use to your information’s final destination.
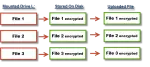
How Do I Back Up an Encrypted Container?
Backing up is critical, but exactly how you back up your encrypted container data depends on how secure your backups are.
How Secure Is Email?
Email is ubiquitous and convenient, yet surprisingly, not particularly secure. I’ll look at why that is and when you should worry.
How Do I Secure a Hard Drive Before Sending It in for Repair?
When sending your computer out for repair, you’re handing over everything on it, including your data. Options to secure a hard drive are limited.
Can Someone See Encrypted Email?
Encrypted email cannot be sniffed, but chances are you aren’t using encrypted email. I’ll explain what I mean and what you might want to do.
How Does Bitcoin Mining Work?
What does it mean to mine something that doesn’t physically exist? And why might it use so much electricity?
How Do I Protect My Laptop Data from Theft?
Laptops are portable, convenient, and easily lost. If lost, all your data could easily be available to the finder. Encryption is the answer.
Are You Ready for Your Computer to be Stolen?
You might lose your hardware and any un-backed-up data on it, and possibly give a thief access to it all! I’ll cover a few of the basics. A stolen computer or lost computer can open the doors to all sorts of havoc if you’re not prepared.
Are HTTPS Connections Really Safe?
HTTPS is an important part of keeping your data safe, but it’s only a part. It’s important to understand what it does and doesn’t mean.
Does Whole-disk Encryption Impact Computer Performance?
Whole-disk encryption has only minimal impact on the performance of modern computers and hard drives. I’ll review why that’s the case and outline something more important: your ability to access the data when something goes wrong.
How to Keep Information on a Shared Computer Private
When using a shared computer, it’s too easy for others to see your data or history. If you must use a shared computer, you need to protect yourself.
What Happened to TrueCrypt and What Do I Use Instead?
The TrueCrypt project was suddenly and without warning shut down. I’ll look at a little of the history and what you should use instead.
How Do I Password-protect a Flash Drive?
There are several approaches to password-protecting a flash drive, one of which might be designed for exactly the task at hand.
BoxCryptor: Secure Your Data in the Cloud
Many online cloud storage providers encrypt your data — which means they can decrypt it themselves. BoxCryptor is a great solution to ensure that your online data remains private, regardless of how it’s stored.
Encryption, Padlocks, and Backdoors
Government agencies are increasingly pushing for a “back door” to encryption. I’ll look at what that means, and why it’s such horrible idea.
Why SSL?
I recently switched Ask Leo! to SSL, partly as a statement and partly for fun. I’ll explain a little of what goes on behind the scenes.
What makes a site secure?
A secure website means the site owner has jumped through the technical hoops necessary to qualify for https. Safety is another thing all together.
If we login to a site securely will our other activities be secure?
Once you are out of https pages you are out of encryption. But there is one good way to secure all your online activities.
What Information Does a Laptop Leak on a Wireless Network?
There is very little about your computer that can be transmitted over a WiFi connection… provided you know how to keep yourself safe on the internet.
How does website or VPN encryption work?
Using a bunch of mathematical magic, a key pair is generated. But that’s just where the fun starts.
TrueCrypt – Free Open Source Industrial Strength Encryption
TrueCrypt provides a solution for encrypting sensitive data – everything from portable, mountable volumes to entire hard disks.