A more secure and convenient alternative to passwords.

Everyone knows the frustrations of creating, using, managing, and forgetting passwords. But what if there was a way that once you signed in to your device, all subsequent sign-ins happened securely and automatically without your needing to remember a thing?
In the coming years, you’re likely to hear more and more about passkeys.
Not passwords. Not passphrases. Passkeys.
You might already be using them without realizing it.
Become a Patron of Ask Leo! and go ad-free!

Passkeys
Passkeys use cryptography instead of passwords to authenticate your identity and allow you to access an account. Passkeys are more convenient and more secure than traditional passwords. There’s nothing to remember and nothing for a hacker to steal.
Pass what now?
Let’s differentiate between these three authentication methods: passwords, passphrases, and passkeys.
As the name implies, passwords are an authentication method where, in addition to your user ID, you prove you are you by entering a “word” — a collection of characters you previously defined as the password — to your account. “Password” is a very bad password because it’s short, simple, and easy to guess, but “jy9zdQbNsWQmuyciC2xw” is a pretty good one because it’s long, random, and basically unguessable.
Passphrases are passwords made up of multiple words. “I Love Lucy” is a bad passphrase because it’s a famous phrase all on its own. Until it was used as a popular example of a passphrase, “Correct Horse Battery Staple” was a good passphrase because it’s lengthy and the words are unrelated. “John Snow You know nothing” is a decent passphrase because it’s an erroneous1 mix-up of an easy-to-remember phrase.
Passkeys are something else entirely. They use what’s called public key cryptography. They might be the safest and easiest to use but the most difficult to explain, so bear with me.
Important
This is a high-level conceptual overview. It’s not meant to be accurate at a detailed level. Actual passkey implementation details are difficult to get. I believe the concepts here are accurate enough to understand the basics of how the technology works. If I later discover inaccuracies in my assumptions, I’ll update the article, of course.
Key pairs
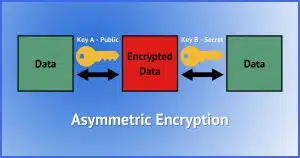
Public-key cryptography is the workhorse of most online encryption. It’s what’s used, for example, to secure https connections, the “SSL/TLS” connections configured in your email program, and much, much more.
The concept is simple.
Two large numbers, A and B, are created using a special mathematical formula. Among many other things, they have the following relationship to one another.
- You cannot calculate one from the other.
- Anything encrypted using one can only be decrypted using the other.
That last point is very important. If you encrypt some data using the number A as the encryption key, then only B can be used to decrypt it. Similarly, anything encrypted using B as the encryption key can only be decrypted by A. A cannot decrypt A, and B cannot decrypt B. Only B can decrypt something encrypted using A, and only A can be used to decrypt something encrypted using B.
Think of it as two locks on the same box.

If you lock the box using key A, it can only be opened using key B.
If you lock the box using key B, it can only be opened using key A.
It’s digital and mathematical magic, as far as I’m concerned. Beautiful magic at that, if you’re into that sort of thing.
Public and private
I did mention this is typically called public key cryptography. Here’s why.
Public key encryption or authentication refers to the use of both keys in these magical key pairs. One of the two is referred to as the “public key”, and the other is the “secret” or “private” key.
If I keep A secret and make B public, then two really interesting things are possible.
- Anyone can encrypt something using the public key B that only I can decrypt using my private key A.
- If I encrypt something using my secret key A, anyone can confirm that only I could have encrypted it if they’re able to decrypt it using the public key B.
Indeed, I have a publicly available public key that anyone can use to encrypt a message to me. Given that only I have the corresponding private key, only I can decrypt it.
Public key authentication
Public key encryption can enable authentication that doesn’t use passwords (something that’s been used on Linux systems for decades).
- Create a key pair: a public key and a private key.
- You keep your private key safe and secure, and you don’t share it with anyone.
- You give the public key to the owner of the server you want to connect to.
- Now you try to sign in to the server.
The server says, in effect,2 “I’m thinking of a number. I’ll encrypt this number using your public key and give you the encrypted result. Now tell me what number I’m thinking of.”
Since you are in possession of the corresponding private key (which you kept safe and secure), the tool you’re using to sign in can decrypt the data the server sent you. It can then respond to the server, “No problem, the number is…” and provide whatever the number is.
Because you had the matching private key, only you could have decrypted the information, and only you could have responded with the correct number.
You must be you. And it all happened behind the scenes without you doing a thing.
I’ve been using this type of authentication to connect to my Linux servers for nearly two decades.
Passkeys and public key authentication
Passkeys are public/private key pairs that are automatically generated for you. The public key is kept on the service that supports passkeys — like Google, for instance — and the private key is stored securely on your computer.
When you sign in, the service responds with a challenge that is encrypted using your public key. Because your computer has your private key, it can correctly decrypt that challenge, proving that you are who you say you are.
Access granted.
And all of that is completely transparent to you, other than perhaps needing to unlock your computer’s securely stored repository of private keys. We’ll talk about that below.
Passkeys are unique to each device
Note that in its basic form, the passkey keypair is different for each machine you use. So, for example, I might have:
- A keypair for my Google account accessed from my desktop.
- A keypair for my Google account accessed from my laptop.
- A keypair for my Google account accessed from my phone.
- A keypair for my PayPal account accessed from my desktop.
- A keypair for my PayPal account accessed from my laptop.
- And so on.
Once again, all of this is managed behind the scenes for you; there’s nothing you need to keep track of yourself. The service keeps track of all the public keys associated with your account, and each device holds the private keys for the accounts that have been set up on that device.3
Passkey setup
How passkeys are set up depends on when and where you’re doing it. Let’s look at two possibilities: creating a new account from scratch and adding passkeys to an existing account on a new device.
Passkeys and a new account
If you’re creating an account from scratch using only passkeys for authentication, the setup process will create the key pair used for that service. The service will keep a copy of the public key, and the private key is securely stored only on your machine. You’re signed in on that machine automatically as needed.
The process will also have you set up additional information so you can sign in to the account without a passkey. Usually, this is something like an email address or mobile number at which you could receive a confirmation code. This is used to sign you in on additional devices on which you’ve not yet set up a passkey.
Signing into a new (or replacement) device
Whether or not you’re already using passkeys with an existing account, you can add a passkey when signing into a new or replacement device for accounts that support it.
First you sign in some other way: using a password, or, for passwordless accounts, using a code sent to an email address or mobile number; or conforming to a prompt on a different device where you’re already signed in.
Once you’ve signed in (again, using something other than a passkey, since you haven’t set one up yet), many services now offer to set up a passkey if they notice that there’s no passkey for the device on which you’re signing in. You can typically also visit the account security settings to set one up.
The passkey setup process creates a keypair to use for that service and stores the private key on your machine. You’re signed in from that machine automatically as needed thereafter.
Using passkeys
When you visit a site for which you have set up a passkey, you sign in by:
- Unlocking your phone or Windows with your PIN, face, fingerprint, or other mechanism you’ve set up.
Even if your phone or computer is already unlocked, your attempt to use a passkey should require the unlock process to confirm you are who you say you are. This prevents someone from grabbing your unlocked phone and using the passkeys on it.
That’s it.
Without a passkey, you can still sign in some other way, but the techniques are more cumbersome.
- Receive an email with a code to enter or a link to click.
- Receive a text message with a code to enter or a link to click.
- Receive a notification on another device on which you’re already signed in to the same account.
- Enter a password, if your account still has a password.
That last one is important because one of the goals of passkeys is to phase out passwords completely.
Passkeys and two-factor authentication
Passkeys are often confused with two-factor authentication. They’re similar but separate things.
Conceptually, passkeys replace passwords. What that means is that if your account has two-factor enabled, then the first time you sign in to a new device:
- You’ll sign in “some other way” (since it’s a new device, there’s no passkey in place).
- That “some other way” may include needing to respond to a 2FA process.
- Once signed in, you can then set up a passkey, if you like, to securely streamline future sign-ins on that device.
The confusion is that the “some other way” techniques are similar to two-factor authentication mechanisms.
Why passkeys are secure
Passkeys protect you from the most common ways that passwords are compromised. (That’s why eventually, passwords will become a thing of the past.)
| Compromise | Impact using passkeys | Impact using passwords |
| Data breach | No impact. The public key is useless anywhere but at the legitimate service. | Low impact unless the breached service has poor security. |
| Phishing | No impact. Passkeys cannot be phished. | High impact when you hand over your password to a hacker. |
| Malware/keylogger | No impact. There’s nothing secure to type or log. | High impact, as merely typing your password can cause it to be captured. |
| Lost device | Low impact. Passkeys are protected by your device-unlock process and can be revoked remotely. | Moderate impact, depending on how you store your passwords. |
| Re-use | No impact. Passkeys are unique to each device and each account. | High impact. Using the same password for multiple accounts is a common way accounts get compromised. |
| Brute force attack | No impact. While technically brute-force is possible, the amount of time required is so ludicrously long (centuries) that it’s impractical. | Moderate impact. Poor password choice can often be easily brute-forced, as can poor storage techniques on the part of an online service. |
Where passkeys are stored
It’s your possession of the corresponding private key that allows you to confirm you are you.
That’s a sensitive piece of information, not unlike a password. It’s stored securely in one of several ways.- In your operating system’s secure credential storage. This isn’t your browser saving a password; this is the operating system using its own highly secure repository. This is the default. When you need to use a passkey, your operating system requests your PIN, face, fingerprint, or whatever other technique might be available. In Windows, it’s Windows Hello; on your mobile device, it’s typically whichever device-unlock process you’ve chosen.
- In your password manager. Many password managers offer to act as your passkey repository. This allows you to set up a passkey for an account once, and then, via the password manager, use that same passkey on multiple devices without having to set up a new one in each place. When you attempt to use a passkey, your password vault will then confirm you are authorized with either your master password, a separate PIN, or the operating-system-provided methods used above.
- On a hardware security key. Some (though not all) hardware security keys, like YubiKey, can be used to store a limited number of passkeys. Like using a password vault, this allows you to have a single passkey for an account that you carry with you and use as needed by providing the security key at authentication time.
In all cases, the private key is stored securely. While we can never say never, it’s extremely unlikely that a passkey’s private key would ever be compromised — much more unlikely than security associated with other authentication techniques.
Do this
Get ready for passkeys. It’ll take a lot of time (think years) for more and more services to add passkey support, but this does seem to be the direction authentication is headed. I enable it whenever it’s offered.
The good news is that the transition may be largely transparent. You’ll just start using passwords less often as passkeys are set up behind the scenes.
I try to demystify technology every week. Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: The correct spelling in this context is “Jon”, I’m told.
2: Totally making this up, but it gets the concept across.
3: Password managers are getting into the game as well and may act as the secure repository for your private keys, allowing them to be automatically synchronized across your devices if you so desire.




Leo:
This one had me doubting my ability to comprehend new concepts; however, I now believe this is actually a round-about description of 2FA. If so, I have to say, for anybody interested in security, I’ve used 2FA since you first described it, and I think it’s great. Thanks.
It’s similar to 2FA, but it is NOT 2FA. It’s closer to having a unique extremely secure password for every combination of site and machine, managed not by you, but by the site and machine.
But will you have control to NOT leave a passkey on a device. For instance, say I want to access my Google account on a public machine at the Library because it has the information I need to research or book list I want to look at or whatnot. I certainly do NOT want to leave a passkey on that device that someone can leverage to get back into my account. (I make sure to clean the cache and history on public PC browsers before surrendering the machine for just this reason as cookies and other login mechanisms can get saved.)
I would expect so.
“John Snow You know nothing” is probably a terrible password as many Game of Throne viewers may not know it’s Jon and not John. If I were to use a guessable phrase, I’d add some punctuation, numbers, and switch up the puncuation.
“j0hn&sn0w&Y0u&Kn0w&N0thing”
Even “correct)horse)battery)staple” is probably OK.
My own take is, NEVER use words tgat can be found in a dictionary, if you can possibly helo it. (There IS such a thing as a “dictionary attack.”)
Try:
“Dzhahn&Snoe&Yoo&Noe&Nuhtheeng!5263”
I have other recommendations, but that’s all I’ll say for now. 🙂
A dictionary attack won’t work on a string of words unless it’s a well known phrase. The entire phrase “Correct Horse Battery Staple” would have to be included word for word in the dictionary, or have an algorithm that tries out combinations of words for it to be cracked. If such an algorithm were implemented, it would still take centuries to crack. And if your password is leaked in a hack, changing one character would make it a completely different password. In that case, I wouldn’t simply add a special character at the end as once cracked, a hacker could try adding on different special characters. That’s extremely unlikely, but I’d ass something in the middle just to be sure.
There are many (MANY) more words than there are letters, so a dictionary attack — which by definition would mean all possible combinations of all possible words — is pragmatically not feasible. Hackers have more effective approaches to getting lower hanging fruit.
“If you’re adding passkeys to an existing account, first you sign in to the account normally, proving you are you in the usual way, like a password. ” Wouldn’t this defeat the purpose of passkeys if it’s possible to sign in using a password? I assume they require on a second factor such as a text message or email to be able to add a passkey for a new device.
It’s pragmatism. Remember, most systems use passwords today, so I actually don’t even know of a passkey-only situation. WHEN we get there, though, then it’ll be a “confirm on other device” or by email or sms or something similar.
What happens when you get a new machine (laptop)? How are the private keys loaded on to the new system? (The old system was damaged and can’t be booted.) Do you use the “old” system and log in with the “old” password system?
Leo, you wrote: “Indeed, I have a publicly available public key that anyone can use to encrypt a message to me.”
[The words, “public key” in the above text, are a hypertext link to Leo’s public key.]
Jeez, Leo! How long is that Public Key! And, for God’s sake… WHY?!? Yeek!
[N.B.: It’s utterly useless to anyone — myself, for instance — who doesn’t have some version of PGP installed.]
It’s to demonstrate that it’s perfectly safe to have it publically available.
PGP and/or GPG. And normal usage is not to copy it from a web page, but rather get it from a keyserver, which is all part of learning how to use GPG/PGP. (Which is also why this type of encryption, while extremely powerful, isn’t something the average person is really set up to actually use).
As Mark said, it’s a) an example of a public key, and b) an example that public keys can be public, and c) available should someone knowledgeable ever feel the need to use it.
I just counted. Leo’s passkey is 7,309 characters long. … Counted it twice to be sure.
Just kidding. I merely copied and pasted it into Word, and got the character count instantaneously.
I think it’s long enough to be considered virtually unhackable using today’s technology.
If you’re referring to my public key, that’s not a passkey. It’s a GPG/PGP key. Same concept, but different implementation and different usages.
‘[The words, “public key” in the above text, are a hypertext link to Leo’s public key.]’
Not on my computer, I wonder why not.
And yet, they are linked. (Make sure you’re looking at the right text: “Indeed, I have a publicly available public key that anyone …”)
It goes here: https://askleo.com/whats-your-public-key/
How does this technique relate to the use of password “helpers”, such as 1Password?
1Password specifically is adding passkey support. What that means is that rather than each device having its own key for each service, each service will have a single key stored in 1Password and thus it’ll “just work” when you set up 1Password on another device.
Not all password managers are doing this, and thus they’ll not be involved in passkeys.
Hello! Yes, passkeys have been around for many years for computer professionals working with servers, etc. The encryption protocols have been pretty great… up to the recent entry of quantum computing. Quantum computers work with totally different processing principles (algorithms) and from what I’ve read in the literature, can “hack” a standard passkey in nanoseconds. So, these passkeys will be great for keeping your data and communications private and safe from your average hacker, but in the future as more governments and other institutions buy into quantum computing, and it begins to become more mainstream, a much more secure approach will have to be thought up to be “quantum proof”.
It’ll be a long, long time before quantum computing has an impact on the average consumer’s day-to-day security.
I know Passkeys are still early on in development so my question may be premature. I was just wondering where say on a Windows PC would the private keys be stored? Would it be somewhere in a folder under /appdata or somewhere else on the PC? Could the keys be viewed or are they “locked” & not viewable? How does an account server with a public key know where the private key is stored? If they leave it up to the PC, what resident app knows where to go to get the private key to pass to the server? Is it the browser that gets the private key & passes the results to the server? I’d like to know answers to most of these questions before I would become comfortable with passkeys.
Since Leo has been using them for a long time for his Linux server logins, I assume he would know most if not all the answers to the above questions.
On the Linux side they’re not passkeys, but they’re like passkeys in the internal (public key pair) implementation. I keep my private keys in secure locations on my machine that, indeed, are just a file and folder situation.
Windows has a “Credential Manager” (You can just search for and run it) that is already in place to store credentials securely. My assumption is that PassKeys will use this. It’s unclear where exactly the information is store. Knowing Windows that answer is probably not simple.
I know I’m answering old questions, but better late than never!
Passkeys can be stored in a number of different locations. I can’t really give a file path for most of these, as the locations are variable or don’t really have a file path at all (or in the case of Windows Credential Manager, I simply don’t know where it is ). But I can give you named locations.
Also Passkey private keys aren’t supposed to be viewable. It’s in the spec that they’re hidden and well-protected, and that the user can’t view them, though if someone were determined enough, they CAN be extracted with varying amounts of effort depending on where they are stored.
If your machine does not have a TPM or it is disabled, Windows will have a digital vault called the Credential Manager that it keeps the private keys in. I’m not sure where the files for this vault are located. If they were found, it’s possible to extract the keys, provided you could find or reconstruct the encryption key for the Credential Manager. Such a thing is possible to do — the key is derived from the Windows login password and a few other pieces of information, which a) the Windows password is stored as an MD4 hash which has been cracked, and b) the other pieces of required information can be found in the registry. It is possible to start with no password, and break your way into the Credential Manager, and then you would have the private key. This assumes Bitlocker is not being used, but that’s a whole complication that I won’t get into right now.
If the TPM is present and enabled, then the private keys will not even be stored on the hard drive, but instead they will be stored on the TPM. The TPM is a microchip on the motherboard which is built to make sure that any key which is not supposed to leave the chip, can’t be extracted from it. Even if you had a machine hooked up to the actual pins of the chip to wiretap it, and you convinced the TPM to unseal itself, the Passkeys on the TPM are kept and used “in-house,” i.e. Windows give the TPM the challenge number, the TPM uses the private key to decrypt it and sign it, and then gives the result back to Windows. Keys which are stored and used “in-house” are never transmitted outside the chip, and are thus impossible to extract, and instead must be reconstructed from heat map and electromagnetic measurements which are so complex and expensive to perform and analyze that it is not feasible for anyone but nation states or perhaps dedicated college research teams to do it.
On phones, it will always be stored in its respective security chip — Secure Enclave for Apple devices, TITAN M2 for Pixel devices, S3FV9RR for Samsung devices, and so on. Same thing applies, it is incredibly difficult to obtain a private key stored in these security chips, and furthermore, you need the device passcode, password, or PIN in order to get the chips to unseal themselves in the first place.
If you choose to use a hardware Security Key to store the passkey, it will be stored there, and the same shtick applies as with the TPM and the other security chips — only nation states and a small handful of people in well-off colleges and universities have the resources and education to do it. Furthermore, they need the Security Key’s PIN.
If you choose to store it in your Password Manager, then the private key will be stored wherever the respective Password Manager stores its vault. The encryption keys derived from the Master Password are needed to decrypt the vault and extract the private key in this case. Unlike with Windows Credential Manager, the cryptography used to both hash the master password, and derive the keys from it, are secure and sound. You will need to have the Master Password to decrypt the vault.
If you store the passkey in your browser’s built-in password manager, all bets are off. They are stored inside your browser profile, and unless the browser allows you to set up a Primary Password or Master Password, and you actually enable it, the encryption keys can be retrieved from wherever the browser stores them, and used to decrypt the browser’s password storage. Only way it’s secure without a Master Password or Primary Password is if you enable Windows authentication to use stored passwords, in which case it will store the encryption key in either the Credential Manager or the TPM, whichever is available.
Now, unlike the private key, a record and identifier of an existing Passkey IS viewable and discoverable by applications and by Windows. The challenge is passed from the website to the browser, to the password manager if present, to the operating system, to the security key or the security chip, until eventually one of them says, “Hey wait a second, I have a passkey for this website!” at which point it will ask you for authentication, then use the passkey to decrypt and sign the challenge, and send it back up the chain, to the OS, to the browser, and then to the website.
Some parts of this chain require you to manually tell it to pass it along, even if there is no passkey present. For example, some browsers will allow you to send the challenge to your phone via bluetooth, by scanning a QR Code — you will need to choose whether to use the passkey on your phone, or whether to move it on down the chain to use a passkey on your operating system or security key.
If there’s a password manager extension installed, choosing “use a different device” in the browser may make your password manager pop up regardless, and you’ll have to unlock the vault and either blacklist the site from the password manager handling passkeys for it or tell the password manager to pass it off just this once, where it will then be passed off to the operating system.
Once it’s at your operating system, you’ll be prompted whether to authenticate and send the challenge to the security chip or Credential Manager, or whether to use your Security Key.
When passkeys are created, wherever you choose to store it, that thing will make the keypair. The website will send a challenge, the tpm or security key or password manager or whatever will make a keypair, and then it will sign the challenge and send it along with the public key to the server. The server will receive the public key, use it to verify the signature on the challenge it originally sent you, and then store the public key for itself. From then on, when you login, the challenge will be sent encrypted and signed by the public key, and the private key will be used to decrypt, verify, and sign the challenge and send it back.
A website with a public key does NOT know where the private key is stored. It will send any device a challenge regardless of whether a passkey is present or not. The website will await either the signed challenge, at which point it will verify the signature using the public key, or a response from the device cancelling the authentication request, at which point the website server will present an error. At that point, you can choose to try again, or you can choose another authentication method, if you have one set up.
I have been confused about how this all works forever.
When you say, “The server says, in effect, “I’m thinking of a number. I’ll encrypt this number using your public key and give you the encrypted result. Now tell me what number I’m thinking of.” I don’t understand how this can possibly work. If the message sent to me is encrypted by the Public key, I don’t see how anything besides the Public key can decrypt it. I assume I only know the Private key, not the Public key. Help!!
Up earlier in the article I talked about this. Public and private keys are PAIRS with the following property:
– something encrypted by the public key can only be decrypted by the private key
– something encrypted by the private key can only be decrypted by the public key
It is, indeed, mathematical magic.
Leo,
Way too technical. Just tell me how it interfaces with me (Google for example) and how I use it. It’s great to know an outline of how they work technically but I still am not comfortable HOW to use it. And I AM USING IT for Google already but it seems to have “variants” and I’m not comfortable with USING IT yet….
I haven’t jumped on the passkey bandwagon just yet, but I will switch to using them as they become available. I already use a passkey (I think) with my Microsoft account and I will set up passkey authentication with google/gmail when the Microsoft Mail client works with them. Until then, I may sign into my google services using a passkey, but my Mail app will still use a traditional password. I have a fingerprint scanner on all my computers for easy login/authentication using Windows Hello in Windows. I’m eagerly awaiting reliable support for them in Fedora and Manjaro (the GNU/Linux distributions I use on my PCs). I suspect bio-metrics presents the best/safest option for authentication to access the local key store. Regarding quantum computing, it may be a while before we must concern ourselves with it, but that technology may offer an even more secure way to authenticate – quantum entangled pairs, where one half of the pair resides on my device, and the other resides in my account data on a server with which I have set up an account. I do not know anything about quantum entanglement, but the technology sounds like something worth investigating.
This has been a stream of consciousness from
Ernie
The gentleman above said it well, way above my comprehension.I have a Google Titan physical key, is that the same thing?
No. That’s a two-factor authentication key. Passkeys are NOT physical keys.
Is this the same as PGP (pretty good privacy) which has been around for years.
Is it exactly the same? I don’t know. Is it the same concept? I believe so.
Hi, Leo.
Given the clear superiority of passkeys, would you explain why you think it will be years before they become commonplace?
Thank you.
Because it’s additional work — not insignificant — for every website and service that wants to start using them. (Work where a return on the investment isn’t clear, to boot.)
Consider we’ve been trying to get two-factor adopted across the web for years, and we’re still not there.
I’m not poo-pooing the passkey system, but there is always the other side of the story. First, never say that a system is hack-proof because you’ll be proven wrong. It’s only a matter of time. Passkeys transfer the burden of security from the service provider (the big company) to the user. If the user is compromised then it’s the user’s fault (so far) and the service provider can’t be sued for a breach. So, what’s protecting the use of your private passkey on your device? A four-digit pin into your device? Certainly you can layer a biometric login on top of the passkey, but that has its own issues. With passkeys you have to depend on your browser or OS to implement the passkey handshaking and security. So, are we talking about a Microsoft Windows “security” implementation? What about the browser? Whose browser will you trust? Which browsers will be sidelined as unacceptable by a service provider? In other words, passkeys may not be the security nirvana we’re looking for. It’s all TBD.
We’ve long, long said that if your machine is compromised all bets are off. That’s just as true before passkeys as after. My take is they don’t really alter the equation.
Leo, I would like to know if my Private Passkey is on my machine and the drive fails or I get a new machine. What can I do? Am I locked out of all my sites?
Certainly not. It’s exactly like setting up on a new machine, described above. (Passkey Setup #3)
Victor: The amusing story is that your private keys are stored and backed up on the service provider’s servers or the servers of a password manager service (if you use that)! So, you’ll need another access scheme to retrieve your key when you lose or damage your device.
Done properly your private keys are NOT stored on the service provider’s service. By default they’re on only your machine.
If you CHOOSE to use a password manager to manage this, then use, passkeys would be stored there, and would be available once you (re)install your password manager on a new/replacement machine.
Isn’t it sad that great sites like ask Leo are all about avoiding hackers. The internet could be a great information highway for everybody to enjoy. I love repairing computers and working new operating systems. It is always fun to have a computer that will not boot. New challenge today!
Honestly, a world without spammers would excite me even more.
hello there. actually i have to find the exact working on passkeys and try to implement on a local server for its applications , they need to implement passkey on their applications on server with employees phone as private key holder . could you please guide to implement the same or steps to move forward. expecting a positive response from you. thank you
That’s well beyond what I do here. I’d start you here: https://fidoalliance.org/passkeys/
You said that setting up a new account would be authenticated perhaps by sending an email with a link. So, if the public key was disclosed in combination with your email address why couldn’t a hacker then set up a new key on his machine, using your email to authenticate it?
It is not “disclosed”. Each key lives on one and only one machine. And of course if the hacker already has access to your email, you have larger problems.
In the context of Passkeys, the server typically provides a challenge to the user (or client) that must be signed using the user’s private key. Here’s a brief overview of the process:
Challenge Generation: The server generates a unique, random challenge (a nonce) and sends it to the client (user).
Signing the Challenge: The client uses their private key to sign the challenge. This ensures that the client possesses the private key without revealing it.
Response to the Server: The client sends the signed challenge back to the server.
Verification: The server verifies the signed challenge using the public key associated with the user’s account. If the signature is valid, it confirms that the user has successfully authenticated.
I enjoy your explanation of passkeys, thank you.
I do have a question…
Once Passkeys are setup, do Passkeys then replace two-step authentication codes?
I travel on vacation and find it difficult to obtain two-step authentication codes on my mobile phone depending on which Country I am visiting in.
Thank you
No. They replace passwords.
Some companies don’t seem to understand the concept of passkeys or maybe I don’t. I have a passkey set up with my Amazon account, which already had 2FA enabled. When logging in to my account, I can either use my password or passkey (both stored in my Bitwarden vault).
It doesn’t matter which I use, Amazon still asks for the authenticator code before logging me in. Other accounts that I have passkeys for and that also have 2FA enabled if using user name/password don’t ask for the second factor when using the passkey.
Did Amazon implement passkeys incorrectly or am I missing something?
Think of passkeys as only a replacement for passwords, and nothing more.
Without 2FA: you provide your passkey (aka password) and you sign in.
With 2FA: you provide your passkey (aka password), and then you provide your 2FA code. IN MOST cases this happens only the first time you sign in to a web site on a specific computer and browser (or if you clear cookies). SOME services require 2FA constantly.
So, with two factor: When I check into a system and they send a code to my phone (text or the Duo app) of my phone is missing or I just dropped it and now it’s broke, or I don’t OWN a mobile phone, then I’m just totally screwed, right? And the same with passkeys?
No no no.
IF you lose your device, you’ll have set up recovery processes when you set up 2FA. You’ll have used a different login approach (say, an email or SMS you need to respond to) to sign in without a passkey, just the same as setting up a passkey to begin with.
And not much more difficult than recovering from a forgetten password.
Why can’t they brute-force the passkey? How is it different than brute-forcing the password?
Theoretically, they can be bruteforce cracked, but the odds of a crack nearly zero. If you were to try one trillion combinations every second, it would take far longer than the age of the universe—to exhaust the full search space.
By definition passkeys are long. Compared to passwords, they’re HUGE. As Mark points out, it would take more time than is practical to actually brute force one.
Excellent article! Even today, it’s amazing how often servers store valuable data, like passwords (or SSNs), in clear text files! PassKeys block this leak. There remain issues with man-in-the-middle attacks at the individual target level. For example, if I can spoof your SIM and you receive your TXT 2FA, then I can use MITM or DNS attacks to encourage you to reset your password, which I can intercept. At Bell Labs, I was one of the early inventors of 2FA https://patents.google.com/patent/US5708422A/en – reset channels are a potential security hole. Encrypted email and encrypted messaging apps are your friend.
Leo:
I’m a little confused (My wife says that about me often :-)). If you’re asked to provide authentication in order to use your private key each time [Windows Hello or Password Manager Master Password (mine’s 30 characters long), biometrics, etc.], it seems to be just as much of a hassle as using passwords. Once authenticated by the service’s server, do they still send a challenge for each login or do they skip that process on subsequent logins?
My PIN / face / fingerprint are way easier and faster for me than typing in a password.
Once authenticated you should stay authenticated for the current session. How long that lasts depends on whether or not there’s a “remember me” that you’ve checked when signing in.
Good afternoon, Leo.
I am old school, but I want to be new school and I learn by example. Could you please give an example step by step? We are missionaries outside of the USA.
Thank you
If you are referring to setting up a passkey, it’s generally a matter of clicking yes when a website offers a passkey or “Fast Login”, “One-Tap Login”, “Instant Sign-In”, “Passwordless Login”, or “Biometric Authentication” etc. Just agree when offered, answer any questions and you’ll have a passkey for that site on your device. You can still log in the old way as each device gets its own passkey and you can choose to set up a passkey for each one when offered.
It varies DRAMATICALLY based on the service you’re using. I’ll see about doing one using Google, but that won’t necessarily apply to other services.
Hi, great article but I don’t quite follow your example with the 2 locks on a single box. If I lock the box with key A, how does using key B unlock the box?
Mathematical magic. It takes very complex math to make that happen. The two lock example won’t work with physical locks.
How much trouble would I have with this technique if I were to reinstall windows?
Not a problem at all. You’d setup new passkeys, just as you did when you setup passkeys on Windows before.
Leo,
“What is a Passkey” is a good introductory article that gives enough technical information to demonstrate improving effort and technique to sign in security. Our responsibility is to do additional research to have a better understanding of this technology. Also, there were some good replies to the article by multiple levels of understanding.
if someone hacked into your computer via remote desktop would they be able to open protected sites from that computer?
Yes, with Remote Desktop Protocol (RDP), you are able to take full control of the computer you are accessing. When connected via RDP, the remote user can interact with the system as if they were physically present at the machine.
Not sure how but I use passkeys with my Google account with my pixel phone, Macbook Air and iPad but I do and it works great. FYI I sign in to all those devices with finger print or face.
I die, and how does my husband get in to my Google account from these devices? He obviously knows my Google password and device passwords. TIA!
See this article, it also applies to “what if she doesn’t have access to my phone.”
https://askleo.com/what-if-theres-a-passkey-on-my-lost-phone/
Leo, Great YouTube clip. Learned a lot.
What happens if a hard drive fails and needs to be replaced. The data is backed up but the OS my be installed. What happens to those stored passkeys. Thanks.
There are still ways to get into the accounts.
What if there’s a Passkey on my Lost Phone
A full image restore would restore the passkeys.
A reinstall would have you then create new passkeys, just as when you first set up passkeys for each account.
Thanks for great information here and in the Lost my Phone article. But it seems that passkeys are not yet a solution for anything other than the inconvenience associated with strong passwords. Having a passkey will remove the annoyance of using a strong password, but as long as a leaked password can be used to log in to a site, a passkey will not solve the security problem. Best you can do for now is to have strong passwords and 2FA.
Its preparation for a passwordless future.
I know it’s bad practice but I do not use any type of security to unlock my phone. From your article I gather that this prevents me from using passkeys. Is that true? I’ve seen them offered on occasion but never took advantage because I didn’t understand them. Now that I do, I might give them a try. I suppose I’ll have to select a method to unlock my phone. Great article. Thanks