You can store sensitive data in the cloud safely.
I regularly hear concerns about using cloud storage, the biggest being that online files are at higher risk of compromise should your account or the storage provider get hacked. There are also concerns that your storage provider could be required to hand over your files to law enforcement agencies under certain circumstances.
Those are all valid concerns.
Cryptomator is a free encryption solution that addresses them.
Become a Patron of Ask Leo! and go ad-free!

Cryptomator
You can store files safely in the cloud if you encrypt them before uploading. Cryptomator makes the encryption transparent by allowing you to designate a folder within your cloud service that is automatically and transparently encrypted before uploading and decrypted when used on your device.
Don’t the providers encrypt?
Many online cloud storage providers encrypt your data. The problem is that since they encrypted it, they can decrypt it.
And while the folks at major online storage providers are professionals with no interest in snooping around in your data, there have been rare instances of the so-called “rogue employee” poking around. The service providers can also turn your unencrypted data over to the authorities should that ever be required.
In addition, should someone hack your account, the data would be available to them unencrypted, just as it’s available to you.
Provider-supplied encryption is nice, but it doesn’t protect us as well as we’d like.
The solution is simple: encrypt the data yourself. If you encrypt your data before it’s uploaded to an online storage provider, you, and only you, control access to it.
The Cryptomator model
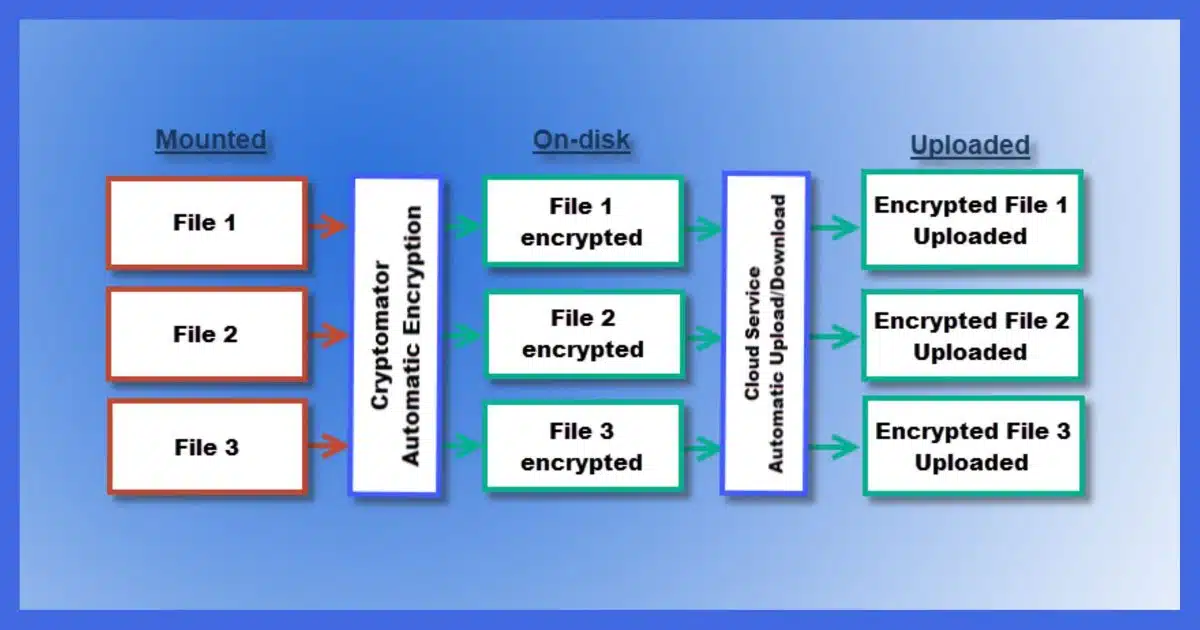
Cryptomator encrypts file-by-file, which is perfect for cloud storage providers like Dropbox, OneDrive, and others that upload and download individual files as they change.
You select a folder to be encrypted by Cryptomator and assign it a passphrase to encrypt the contents.
When you “mount” this folder using Cryptomator — providing the passphrase to do so — another drive letter appears, which I’ll call L:. Anything written to drive L: is encrypted and written to the folder you specified. Anything read from that drive causes the corresponding encrypted file in the source folder to be read and decrypted on the fly. There’s little noticeable impact on performance, since accessing the disk, not performing the encryption, is the slowest part of the operation.
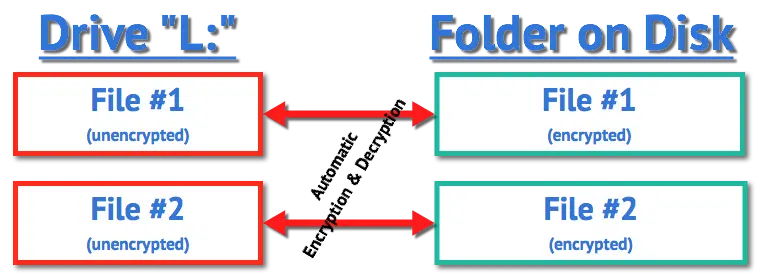
The files in the original folder on disk are always encrypted. It’s only when the folder is mounted using Cryptomator that the files are visible in their decrypted form in the virtual drive.
An example of Cryptomator in use
Let’s say I use OneDrive.1 On my machine, there’s a folder:
C:\Users\leon\OneDrive
It contains all the files and folders that are part of my OneDrive cloud storage. I have many files and folders that automatically synchronize with the OneDrive servers, as well as on all other machines on which I have OneDrive installed.
One sub-folder within my OneDrive folder is:
C:\Users\leon\OneDrive\EncryptedFiles
I don’t place any files in this folder directly. It starts out empty.
Next, I install Cryptomator and configure it to mount “C:\Users\leon\OneDrive\EncryptedFiles” as drive L:. I set up the passphrase required to mount it again in the future.
Drive L: appears on my machine.
I create a Word document on drive L:
L:\MyPrivateInformation.docx
As soon as I save that document to drive L:, new files and folders appear within the EncryptedFiles folder:
C:\Users\leon\OneDrive\EncryptedFiles\d\2G\BQCY3SUZEVRU3MRAGLO6C62JGGGYZJ\5Y5RR6LM5SKSFZ6FIKULKNNBVQ3Y6DDTNGAKKX3VI2N72ZWM6KUOIGWL2AWCGB2TMY======
The file that was saved to L: is automatically encrypted and placed in the folder I named EncryptedFiles. This extremely obscure filename (along with others) is Cryptomator’s encrypted version of my document. This is the only representation of the file that is physically written to disk.
Next, OneDrive notices a new file has appeared on disk within the OneDrive folder. It uploads this encrypted file and distributes it to all my machines running OneDrive. Note that only the encrypted version of the file has been uploaded.
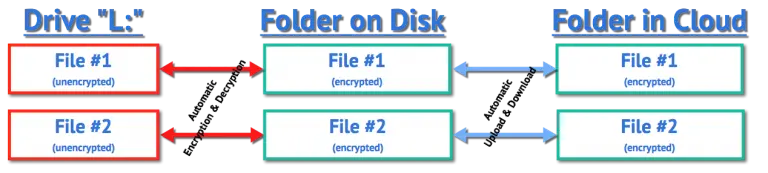
I can continue to work on the file on L: to my heart’s content. It’s just a file, and I can manipulate it like any other. As changes are saved to disk, the corresponding encrypted version of the file is updated appropriately.
Once I dismount the EncryptedFiles folder, its corresponding drive, drive L:, disappears. The unencrypted versions of the files are no longer accessible. All that remains are the encrypted versions stored in the EncryptedFiles folder within the OneDrive folder, both online and on my hard drive.
It’s for more than Windows
Cryptomator is available for:
- Windows
- Mac
- Linux
And there are also apps available for:
- Android
- iOS
That means you can continue to share your documents across all the platforms and devices supported by your online storage provider, but now you can easily encrypt the data you share.
The hidden cost of doing your own encryption
I have to mention one caveat: there’s one good reason not to encrypt your data yourself, and that’s web access.
Unencrypted files are accessible via your service provider’s web interface. Dropbox, as one example, allows you to log in to your account from any machine and access the files stored in your account via the web.
If you encrypt the data yourself, only encrypted data is available to you via a web interface. If you ever want to access your unencrypted data on a device that doesn’t have the encryption software installed and configured, you can’t.
What about Boxcryptor?
In the past, I used Boxcryptor to perform the same task as Cryptomator.
Boxcryptor was sold to Dropbox, and its future is now unclear. You can no longer create new accounts.
Do this
Cryptomator is free2 and open source, with no limitations on use. My bottom line is that Cryptomator is a convenient solution for making sure the data you place in cloud storage services remains secure and accessible only by you.
I recommend it.
I also recommend you subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




Hi Leo,
In some of the online articles comparing Boxcryptor vs Cryptomator, there is a phase that suggests that making changes to a single file in Cryptomator would change the entire storage vault. Your article mentions that Cryptomator encrypts file-by-file, which the paragraph below seems to contradict, or I simply misunderstand it.
Would you be able to enlighten me how file-by-file encryption cause changes to the entire vault? My main concern is how changing a single file (e.g. working on a word doc) may potentially result in me corrupting/ruining/losing other files in the vault. Thank you.
“When it comes to Cryptomator, encrypted data goes to storage vaults before it goes directly to the software. If you want to use this storage, Cryptomator will take note of a certain pathway and use it to check files. A change in a single file will also lead to changes in the entire storage vault, so keep that in mind when editing content in Cryptomator.
Files encrypted with a Boxcryptor are subsequently stored in key vaults. That way, these files are encrypted one after the other so if a single file changes in any way, then users can easily change the content without ruining other files.”
I think it’s a conflicting use of the term “vault” (which really has no definition for our purposes). If you take a look at the folder in which Cryptomator stores its encrypted files you’ll see a lot of nonsensical files. My belief (and to be clear, it’s just a guess) is that your file (say a .docx for example) might be contained in one or more of these files. Thus changing the .docx “logical” file could change multiple physical files, and quite possibly the information in the folder path to the file as well (if you have folders within your Cryptomator setup, as I do). So changing one logical file could cause multiple physical files to appear to have changed, quite possibly including something at the top of the folder tree.
I can confirm that changing ONE file does NOT cause EVERYTHING to be altered. That would defeat Cryptomator’s purpose.
I can also confirm that editing directly a file (the .docx in my example) does not corrupt other things. I do it all the time. The only time I could conceive of an issue might be if multiple edits were happening on “nearby” files across multiple machines.
Nonetheless, as with all things, I back up the unencrypted contents of my Cryptomator vault anyway. Because you never know.
I’ve had a serious go at installing Cryptomator but it keeps on sticking (after I’ve installed it) at
– I enter “reveal drive”
– it replies “H: is unavailable. If the location is on this PC, make sure the device or drive is connected ….. etc
The ‘help’ section is rather complicated and suggests making changes I’m not comfortable with. As Boxcryptor is closing down, is there any other encryption app that is more user-friendly than Cryptomator? I don’t want to go back to hiding pendrives of my key files in the loft …
Make sure you have “Files on Demand” turned OFF in OneDrive, to start.
I should add that I’m using Windows 10, and trying to link Cryptomator to OneDrive. There are suggestions that I should link my vault to a directory not a letter – though I don’t see how to do this in OneDrive – and generally it all gets very techy very fast.
I’m beginning to see why seniors find computing difficult …
Create a Cryptomator folder inside your OneDrive folder and place everything you want encrypted into the Cryptomator virtual drive. They will be encrypted on OneDrive. The same works for Dropbox, Google Drive, pCloud and more.
Sorry to be a Muppet, Leo, but how would I do that?
Can’t find any such command box on OneDrive.
Mark – I’ve made a Cryptomator folder in my OneDrive. But when I try to run Cryptomator it gives the “H: is unavailable…” message. There is therefore no option to put anything into the Cryptomator folder as Cryptomator can’t find it. I’ve tried the custom route but that fails, too.
Clearly I’m doing something wrong but computers sulk so effectively …
Thanks for your patience, gentlemen. I’m at my wits’ end (not a long journey, I grant you).
It’s an option in OneDrive settings. Right click on the icon in the notification area of the taskbar, click the gear, click Settings, scroll down and click Advanced settings. You’ll find it there. Once you turn it off give OneDrive a chance to download anything that hadn’t been.
Thanks Leo, after a reinstall of Cryptomator, and making the changes you suggest, all seems to be tickety-boo. Problem may have also included a “hidden.^^^” file that appeared from nowhere, and also that I set my initial vault to be in \OneDrive instead of \OneDrive\Cryptomator, but I’m now a happy bunny.
Thanks for your patience and knowledgeable assistance.
Andrew
I’m glad I switched from Dropbox to OneDrive. Dropbox was irresponsible for dropping support for BoxCryptor in an attempt to drive BoxCryptor users to Dropbox.
To be clear, it’s not clear who drove the decision. Could have been the BoxCryptor team making that call, but it certainly could have been DropBox making a criteria for the deal.
Either way, communication to customers has been handled very poorly.
I started using Cryptomator about a year ago and I use OneDrive. Just as a heads up, when I was setting up my Cryptomator vault I moved rather than copying existing files into the vault. I received multiple warnings via Windows Security pop-ups and messages from Microsoft about a possible ransomware attack.
I considered it a test of the security features, but after I had everything set up, I accessed my OneDrive online to make sure that no copies of the files I had moved were recoverable. Once I had done that, I keep copies of my vault contents unencrypted on an external hard drive, just in case something goes wrong. That is in addition to doing regular backups.
Also, for those deciding to give Cryptomator a try, make sure to make a copy of the recovery key and keep it in a safe location. Just like a good password manager, if one forgets the password to their Cryptomator vault there is no support to get back into it. The recovery key can be used to get back into it.
Just a quick tip for new Cryptomators users:
1. NEVER copy or save files directly into the Cryptomator folder in your cloud service – always work within the vault you created.
2. The Cryptomator folder in your cloud service will only reveal a handful of files, a few which start with the word “masterkey” and the others starting with the word “vault.” There should be one folder with a single letter (like “d”). This is where all your encrypted content sits. Again, don’t save anything directly into it – always use your vault to access your stuff.
I speak from experience that if you have a problem, the CR forum has a lot of users willing to help and they provide great support even for a free app.
I have been using Cryptomator for some time with pCloud. I am happy with it but there is one thing that puzzles me: At some point developers introduced an option to save password for the vault. To my simple mind it seems to encourage people to take a step that makes it less secure.
I have an Open Document (LibreOffice Writer) file I use to keep track of my monthly bills. I tried using Cryptomator to encrypt it for storage on OneDrive (changing the desktop icon I use to open it in LibreOffice accordingly, since its location changed). When I had the ‘vault’ mounted with Cryptomator, all worked as expected, but after a re-boot, I’d often forget to re-mount the vault in Cryptomator, making it less than convenient for me. If there was an option to auto-mount the vault in Cryptomator on system startup, I’d be using it today. If anyone can tell me how to set this up, I’d appreciate it,
Ernie
First, set Cryptomator to launch automatically with Windows. It’s a Cryptomator setting.
Then, next time you mount your vault, check the settings for that vault. Remember password, and auto-mount should be available options.
Before attempting to use Cryptmator, I am curious what happens if my computer that Cryptomator is installed on crashes, what is the recovery process to setup on a new computer. Having never used an encryption software, I’m sure it’s a fairly easy process but want to be sure before attempting. Thank you!
Assuming the encrypted data is being replicated to other computers (as in Dropbox) you would simply install CryptoMator on the other machine, and open the vault.
Good morning Leo,
I am wondering if I could use the mklink /j to redirect the Windows Folders (Desktop, Documents, Downloads, Music, Pictures and Videos) to the OneDrive Folder being encrypted (to use your example C:\Users\leon\OneDrive\EncryptedFiles — of course I would create my own OneDrive folder) before going to my Unlimited Sync.com Cloud Storage?
I really enjoy your YouTube videos and am thrilled I stumbled across this article.
Thanks for any time and help you can offer.
John Levesque
I would be shocked if it worked, and would expect it to be fragile if it appeared to. The mounted Cryptomator drive doesn’t have all the characteristics of a “real” hard drive, and Windows treats those folders so specially in so many nuanced ways that I suspect it’d just be a mess. (Remember also, Windows will run and expect those folders to be present before you even have a chance to mount them.)
If it’s an issue, I’d keep sensitive files out of the Windows standard folders, and set up your own elsewhere.
Thanks Leo,
Yes you are correct it didn’t work. What I ended up doing was just creating Folders of the same same in my Crytomator folder. I then removed the Quick Access pins from all the System folders in the Windows Explorer and add Quick Access pins to my newly created folders inside the crypto folder.
I noticed an issue that I will just ignore pertaining to screen shots. When I tried relocating the target it seemed to be recreating the Camera Roll and Screenshots folder, over and over again, so I just removed them.
I am about to try this new arrangement which I actually installed to my PCloud which has an empty 16TB of storage being used, except for a few files that only amount to less than 1GB currently.
I am now going to install TickTick using my newly created Quick Access Folders and see what happens as far as speed (especially since I purchased the migration of my PCloud to Switzerland).
Thanks again for your time and help. Love your program.
John Levesque
I should have mentioned that I am in Florida and switched from US PCloud to EU because I am looking forward to a day I can trust our government again.
Also, I have the Lifetime 16TB with Lifetime Crypto but I enjoy the idea of being in control of my encryption. I purchased enough Lifetime Storage and eventually got PCloud to consolidate it all into one 16TB drive with another 4TB leftover for my wife under her ID.
Love your show Leo.
Thanks,
John
“I am looking forward to a day I can trust our government again.” It’s legal according to American law to spy on the EU. It’s illegal for the US to spy on domestic servers, although as Ed Snowden pointed out they do it all te time. The only way to protect your data is via encryption, and of course, backing up.
(This isn’t legal advice. It’s just an observation)
So, Cryptomator will upload your encrypted files to cloud provider (i.e. OneDrive) but it does not upload the unencrypted files to OneDrive? So, if Cryptomator shuts down my OneDrive backup is useless? Would this be true with my daily incremental backup with Macrium Reflect to my external hard drive as well?
I’m confused by your wording, so I can’t answer for certain. I will say this:
Maybe a little more clarification:
If you are asking will the Cryptomator still be backed up when Cryptomator isn’t running? then yes. First of all, Cryptomator doesn’t upload files. Your synchronization program does that. Cryptomator just encrypts and decrypts.
Everything in the Cryptomator folder remains whether Cryptomator is running or not. What Cryptomator does is decrypt those files and place them in a virtual drive that goes away when Cryptomator is exited. When running, Cryptomator lets yoy add, edit, and change the unencrypted on the virtual drive and saves the encrypypted version of the files in the Cryptomator folder. There’s even a warning when you run Cryptomator not to place any files into the Cryptomator folder. If you place any files there, they won’t be encrypted.
What is the best way to backup the UNencrypted Cryptomator files? My primary and secondary backup software (AOMEI Paid and EaseUS Todo paid versions) do not show it as a source (probably because it’s listed as a network drive under My PC in File Explorer?). I do not have this issue with mounted Veracrypt volumes.
Thank you!
If you do a backup while logged in to Cryptomator, you can back up the virtual drive created by Cryptomator.
You can even copy and paste the files without running a backup program.
I just stumbled across this topic and comment about copy & paste as backing up my unencrypted files while the vault is open in Windows. My question is would that leaves a trail on the Windows system, e.g. clipboard, etc. ? What would be the best practice to safe guard my files and my privacy?
The only thing left in the clipboard after using copy/paste to copy a file is the full path to the file — NOT the file’s actual data. So only the path could be exposed. If that’s an issue, then either put something else in the clipboard right away, or don’t use copy/paste as your backup method.
If you have a Clipboard manager and want to hide the paths, you’ll need to clear the Clipboard manager.
The Cryptomator folder in your cloud service will only reveal a handful of files, a few which start with the word “masterkey” and the others starting with the word “vault.” This is a quote from Sam Hunt above. My question is . . . if the master key to encryption is stored in the Cryptomator folder that is in my cloud service (the unencrypted one), doesn’t this give DropBox the ability to have access to my Cryptomator master key to decrypt anything that is stored in my virtual vault? If the “masterkey” file is indeed the master key to Cryptomator’s encryption/decryption process, it would seem that this key would NOT be stored in the cloud. It would be stored on my local drive or an external drive.
As I understand it the masterkey is encrypted using your password. So:
Password encrypts master key. Master key encrypts data.
This allows you to change your password without having to reencrypt all of your data. It also insulates the master key from poor choices, as it’s a truly random, and very large number.
A question about ‘data migration’ after installing CM. I created the vault in my OneDrive folder as Leo explains above, where it now sits next to most of Windows’ main user folders (Docs, Pics, Downloads, etc.) that I moved there when I signed up for OneDrive. I want my Documents subfolders and files encrypted by CM. Do I move the whole Documents folder to the vault to accomplish that? And if so, does that change the paths of folders and files in any way?
I would not move the documents folder. That will probably confuse many things. I would create folders of your own design in the mounted cryptomator vault, and copy your documents into those folders.
Ok, thanks, that’s helpful. Figured as much 🙂
I did get a warning from OneDrive of a possible ransomware attack, after I copied a bunch of my folders to the newly created CM vault. Very thoughtful of Microsoft! 🙂
My next challenge is figuring out how to change the way I make backups with GoodSync and Macrium Reflect, so that I can still access the encrypted files if I ever want to pull files/folders from my file and folder backups! Never a dull moment! 😉
As long as you backup and restore the entire CM folder tree, you can restore it anywhere, and you should be able to access its contents.
The main drawback of that is that you can’t pull individual files or folders from the backup that are stored in a CM vault, as the names are encrypted too. So you have no idea which one you’re looking for. Also, CM won’t let you load the vault directly from the external backup drive. So you end up having to copy the whole vault to your hard drive before you can load and unlock it in CM. Then OneDrive starts sending you warning messages again about a possible ransomware attack. And after you have retrieved that one file you need and remove the vault and delete the files OneDrive then warns you that a suspicious large amount of files has been deleted.
Ah, the joys of digital file management! 😉
You should be able to mount the vault wherever it is, and extract the files that way. (Filename obfuscation is part of its security.)
I am currently using Boxcryptor and onedrive (unfortunately I signed up for 3 more years a month before they announced going to Dropbox). I’m now looking at moving to Cryptomator even though I have another 2 years on my license. In Boxcryptor I used the personal vault feature in onedrive to keep my most sensitive files so I could have 2FA before accessing them and kept other files outside the personal vault (also encrypted). How do I set up a folder within the personal vault and outside the personal vault using Cryptomator?
Thanks, Mitch
Ignore my comment on January 29th, I figured it out, just needed to unlock my onedrive personal vault on my laptop and then create a vault in cryptomator and locate that vault on my PC and point the vault to that location. I’m now ready to cut the cord with Boxcryptor.
If I understand correctly, the Cryptomator philosophy is different compared to Boxcryptor.
With BC, my GDrive was mounted and I had access to my entire (unencrypted) GDrive under the drive letter X: (Boxcryptor mount). Then I could right-click to decide which files or directories I wanted to encrypt (and possibly also do file name encryption). These were then no longer readable in the unencrypted GDrive, but only in my X-Drive.
This allowed me to work comfortably in a mixed mode, where unencrypted and encrypted files could be stored side by side and I could decide on a case-by-case basis.
That would have to change with Cryptomator, right? I need a vault (a directory, so to speak) where everything that is to be encrypted must be stored. No more mixed mode that allows both (encrypted AND unencrypted) to be stored side by side in the same directory.
Have I summarized this correctly?
After reading your articles on Cryptomator and Veracrypt, I decided to install them on my test computer.
I went to download Cryptomator and saw this:
—
This installer includes the third-party driver WinFsp. You can also download the MSI installer without dependencies.
—
I read about WinFsp (https://winfsp.dev/doc/) and could see no reason to install it. So I decided to use the MSI Installer.
On the MSI install page, I read this:
—
We recommend installing WinFsp. FUSE is optional but offers better integration into Windows.
—
Now I’m all confused. What does WinFsp do in the Cryptomator world?
Thanks very much,
John
“File System Proxy”. From their website: “WinFsp enables developers to write their own file systems (i.e. “Windows drives”) as user mode programs and without any knowledge of Windows kernel programming. It is similar to FUSE (Filesystem in Userspace) for Linux and other UNIX-like computers.”
I’d really like to see a comparison of Cryptomator with VeraCrypt. They’re both open-source and VC has some interesting deniability features that most folks won’t need, but are there any audit or analysis reports available for review?
The main difference for the average user is that Veracyrpt stores all the files in one container file, where Cryptomator encrypts each file individually. That gives Cryptomator 2 advantages over Veracrypt. If you make even a tiney change to a file in Veracrypt, it forces the entire Veracrypt file to be uploades to the cloud server and downloaded to every device synced to that account. Another disadvantage of Veracrypt is that the container is a fixed size and can waste a lot of diak space. I use both Veracrypt and Cryptomator. Veracrypt is especially good for systen drive encryption for computers that don’t support Bitlocker.
They both have similarly strong encryption strength.
As for technical specs and analysis reports, you’ll have to check their websites or other tech websites to see if any reports are available.
This article is about the now-defunct BoxCryptor, but the concepts, particularly the comparison to VeraCrypt, apply https://askleo.com/boxcryptor_secure_your_data_in_the_cloud/
As I see it, one advantage of CM over VC is the availability of mobile apps. However, a $20 price tag on the android app along with a ton of negative comments does not encourage downloading to see if those comments are specious.
Cryptomator has a 3.8 out of 5 stars rating and a high number of 5 star ratings. I don’t use it because I do all my serious work on my computers, but if I needed to encrypt and decrypt on my phone, I’d consider it.
I just used it on my phone to access something earlier today. Worked great.
Maybe I’ll spring for a subscription