Articles in Category: Security
What’s the Best Two-Factor App?
Two-factor authentication is one of the most important things you can do to secure your accounts. Here are the 2FA apps I can recommend.
More Passkey Questions
Passkeys seem like magic, and confusing magic at that. I’ll address a set of questions I received recently.
What to Do About Kaspersky Antivirus
Any software company with ties outside the U.S. comes under scrutiny. Should you be worried?
Changing Your Password After a Hack May Not Be Enough
Changing your password is a common response to account hacks. Unfortunately, it isn’t enough.
What If There’s a Passkey on My Lost Phone?
Losing a device with a passkey isn’t a disaster at all. I’ll describe why that is.
One-Time Code Contradiction: When to Share and When to Beware
You’re told not to share your two-factor or other authentication code. And then you’re asked for it.
Can Someone Install Something on My Computer When It’s Not Logged In?
If your computer is not physically secure, someone could install something even if you’re not logged in.
Surprising Reasons to Use a VPN at Home: More Than Just Privacy
Although a VPN service is probably not necessary at home, there are a few scenarios where you may want to consider it.
What to Do With an Unexpected Two-factor Code
Getting an unexpected authorization code on your phone or via email can be concerning. Let’s see when it’s a sign of a problem and what to do about it.
I Got a Call from Microsoft and Allowed Them Access to My Computer. What Do I Do Now?
A very common scam has people supposedly from Microsoft, your ISP, or other authorities calling to help you with computer problems. Don’t fall for it.
How Do I Recover Encrypted Files From Cryptomator?
Recovering individual files from a Cryptomator encrypted vault can be tricky. I’ll discuss why and how to protect your access to those files.
Beware the Middleman: How Your 2FA Could Be Compromised
Some forms of two factor authentication have vulnerabilities. Here’s how to avoid it.
Facebook Marketplace Scams: 3 Warning Signs You Shouldn’t Ignore
Facebook Marketplace scams are on the rise. Here are three red flags that should tell you something’s not right.
What Is Credential Stuffing?
Credential stuffing: less complicated than the fancy words imply and easy to prevent.
Don’t Be Ashamed or Smug
If you’re embarrassed at having fallen for a scam, it’s tempting to want hide and not tell anyone. But it’s important to learn from the experience and share it. There’s no need to feel shame.
How Can I Tell If a Web Address Is Safe?
URLs are simple in concept, yet can be constructed in ways that might fool you. I’ll look at some examples and discuss what’s important.
6 Steps to Dealing With Phone Spam
Phone spam, be it voice or text, is as annoying as it is persistent. Here’s what (little) you can do.
How Can Passkeys Possibly Be Safe?
Passkeys may feel confusing now, but they’re a doorway to a more secure, less frustrating, passwordless future.
How Can I Recover an Outlook Password Without Resetting It?
Microsoft doesn’t know your Outlook.com password. Honest. That makes recovering it without changing it challenging.
Isn’t Putting Two Factor Codes in My Password Vault Less Secure?
Storing 2FA codes in 1Password alongside passwords might slightly reduce security, but the risk is minimal, especially compared to the convenience.
How to Protect Yourself From a Two-Factor Hack
Two-factor authentication isn’t perfect, but it’s much better than not using it at all. Here are the various risks and what you can do to protect yourself.
When You Change Your Phone Number, Change Your Phone Number
The ability to keep your old phone number when getting a new phone can avoid several headaches. If you get a new number, there are steps you must take.
What Is a Pig-Butchering Scam?
Pig-butchering is a nasty term for a particularly painful type of scam. Here’s how to protect yourself.
Could Malware Record My Chats and Video Calls?
If you’re curious what might happen if a hacker was in control of your computer, the question really is “What can’t they do?”
Dealing With the Demise of Authy Desktop
Authy’s desktop version is going away (darn it!). Here’s how I will replace it.
Are the Bad Guys Winning?
Media hype makes it seem like the bad guys are winning. They’re always in the lead – but don’t believe the hype.
Can My ISP Monitor My Internet Connection?
Your ISP controls your internet connection, and it’s easy for them to monitor the data you send and receive. The question is, why would anyone monitor your internet?
Another Way to Protect Yourself From 2FA Loss
A little bit of preparation when you set it up can make losing your Google Authenticator 2FA device a minor inconvenience.
The Surprising Ways Your Videos Can Expose Your Location
Something many people do every day may expose their location in ways they don’t know.
I Lost My Two-Factor Authentication (2FA) Device. How Do I Sign In?
Fear of second-factor loss prevents some people from using two-factor authentication. There’s no need to fear that scenario.
I Gave AI My Search History and Here’s What It Told Me
I was listening to a podcast recently in which one of the hosts described giving ChatGPT the history of the questions he had asked it and then asking it to build a profile on him based on that. It was interesting, of course, but it got me to thinking… why not use internet searches as … Read more
What If Password Autofill Won’t Work?
Password vaults are sometimes unable to auto-fill fields. There are several ways to work around this.
If They Got Into My Account Once, Could a Hacker Get In Again?
Once your account has been hacked, there are many things you need to consider to prevent it from being hacked again.
How to Securely Wipe the Windows System Drive
Reformatting the system drive takes a little more effort than other drives. Here are three ways to get it done.
How to Find a Phone Number With an Email Address
You have an email address and you want the associated phone number. It’s unlikely you’ll find it, but there are a few straws to grasp at.
Yes, You Should Give Google Your Mobile Number
Google uses your mobile number for verification if you lose access to your account. Some people don’t want to provide it. They should.
How Do I Change My Password for Google Mail?
There are times when a new password is what you need. Here’s how to change it.
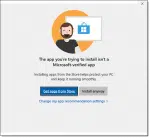
How Do I Fix “The App You’re Trying to Install Isn’t a Microsoft-Verified App”?
“The app you’re trying to install isn’t a Microsoft-verified app” message is the result of a simple setting you can change.
How to Use Just a Single Password for Everything
It’s very tempting to use only a single password everywhere. That’s dangerous, and there are better alternatives.
How Can I Password Protect My Documents?
There are several options to keeping information private on your computer.
How Do I Prevent a Service From Logging Me in Automatically?
Preventing someone else from accessing your account is as easy as signing out before you leave.
Passkeys and Disaster Planning
Passkeys are new, convenient, and secure. I’ll review how they affect your disaster planning. (Not very much.)
How Do I Tell If an Attachment Is a Virus?
You can’t prove a file isn’t malicious, but you can certainly stack the deck in your favor.
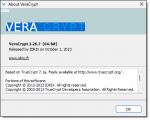
Why Won’t My VeraCrypt Volume Back Up?
When using VeraCrypt containers, the default setting may interfere with backing up your container. Here’s how to fix that.
Can I Password Protect a Folder?
Keeping data secure is important. Being able to password-protect a folder seems an obvious approach. Unfortunately, it’s not that simple.
My Computer Is Infected With Malware. Should I Just Throw It Out?
Malware is just software. It doesn’t destroy your computer’s hardware in any way. Some work will get you back up and running without needing to destroy anything.
How Should I Keep Recovery Codes Secure?
Recovery codes protect you against account loss. The issue? Where to store them safely.
Password Update Without Re-encrypting: How?
If your password is used to encrypt your hard disk, how can you change your password and still be able to decrypt your disk?
Preparing for the Ultimate Disaster
If you’re not around to unlock all the digital data you take such care to secure, who will be able to access it, and how?
Should I Disconnect My Backup Drive When I’m Not Backing Up?
Some people disconnect their backup drive when not backing up because they fear ransomware. I explain why that’s a Really Bad Idea.