With preparation.

The short answer is that you can’t. Not directly. I’ll explain why in a moment.
Cryptomator is a free program built to encrypt files before they’re uploaded to cloud storage. To access those files, you must have both Cryptomator and your passphrase. Even with the information, if you want to recover just a single encrypted file, things get challenging.
I’ll address how to protect yourself from scenarios like this. One approach relies on something I’ve been suggesting you do for a long time.
Become a Patron of Ask Leo! and go ad-free!

Recovering Cryptomator encrypted files
Recovering files from an encrypted Cryptomator vault is essentially impossible because the encryption completely obscures file names and paths. The best strategy to protect your sensitive information is regularly backing up the unencrypted contents of the vault for easy access in emergencies and storing those backups securely.
Cryptomator on disk
Once the correct passphrase is provided, Cryptomator creates an unencrypted window onto your encrypted files. For example, here’s what is shown in my mounted (unencrypted) Cryptomator drive.
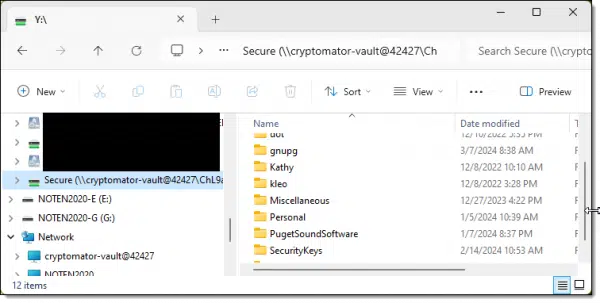
And here’s what it looks like on the hard disk when it’s encrypted.
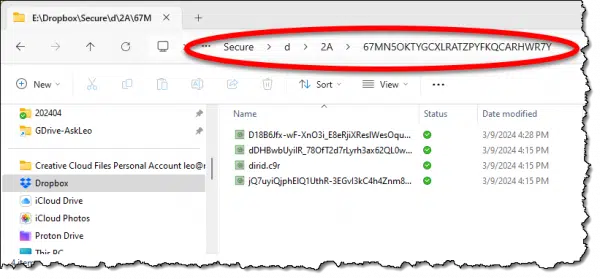
There are no file names. There’s no hint as to how things are organized. Even if we could see that, it’s all useless unless you have the decryption key.
So the short answer is that no, you can’t directly recover individual files from the hard disk if they’ve been encrypted using Cryptomator — mostly because we can’t tell where they are.
Be prepared
My fallback solution for just about any tech problem is a recent backup. This scenario is no different; there are just a couple of twists.
If you just back up a hard disk with encrypted files, you’ll be backing up files in their encrypted state. That’s fine, and certainly better than no backup at all. However, it assumes that you always have your decryption tool and passphrase at the ready if you need to access them. The recovery scenario would look like:
- Restore the Cryptomator-encrypted folder somewhere (its original location or somewhere else).
- Fire up Cryptomator.
- Configure it to access the restored files.
- Supply the password and access the unencrypted files.
That certainly protects you from things like hard disk failures, stolen laptops, and so on.
I prefer a different approach before a restore is ever needed.
- Mount the Cryptomator folder so that the unencrypted files are accessible.
- Back up the files in their unencrypted state (i.e., back up the contents of the mounted drive.)
- Securely store that backup.
This way, if you need a single file, you can go to your backup of the unencrypted files and extract it without needing Cryptomator at all. Your backup may be more cumbersome than using Cryptomator, but at least your files will be there.
Since you’re using Cryptomator for a reason — to encrypt sensitive files — it’s important to store the backup of those unencrypted files securely. That could mean storing the backup in a physically secure location or encrypting the backup using different technology.1
Grasping at straws
I’ll preface this by saying I don’t know why you’re asking this, so these approaches may or may not get you the results you’re looking for. If you don’t have a backup of the unencrypted files, here are some next steps you could try.
Restore a backup of the encrypted files and mount it. If you have a backup of the files as stored on disk, you can restore that (to any machine with Cryptomator, and in any location), and then mount it using Cryptomator. All your files should then be visible.
Copy the entire folder of encrypted files elsewhere and try to mount it. This assumes you may have an issue with the machine on which you normally access the files. The entire tree can be copied elsewhere and mounted using Cryptomator. All your files should once again be visible.
Restore an online backup and mount it. You may notice from the images above that my Cryptomator files are stored in Dropbox. Dropbox has a recycle bin, so if my Cryptomator files become damaged for some reason, I may be able to restore files from a particular date. OneDrive and other cloud storage services have similar features.
Visit another machine on which you have the files. Again, since I’m using Dropbox, my Cryptomator files are available on all other machines connected to that same Dropbox account2. If the problem is with your machine and not the files themselves, it might be as simple as walking to another machine to get the files you need.
Don’t lose access
When you set a passphrase on a Cryptomator vault, you have the option to create a recovery key.
Do so. Then save that recovery key in a secure place. I’m partial to putting it into my password manager, but whatever works for you and is secure is fine.
This protects you against forgetting your passphrase. If you forget it and you do not have a recovery key, you will lose access to your encrypted data.
Do this
Cryptomator is awesome, and I love it. I use it heavily and daily. But it does come with some caveats, the most important being that if something goes wrong, you won’t be able to recover the encrypted files without both Cryptomator and your passphrase.
As usual, the best defense is a comprehensive backup. In this case, I strongly recommend a backup of the unencrypted files stored securely.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: I recommend different technology to protect yourself from issues with Cryptomator itself, including losing your unlock password. I create a single password-protected ZIP file of the files I store using Cryptomator and then store that file securely.
2: Cryptomator’s primary purpose is to efficiently store securely encrypted files in cloud storage services.





Hi Leo, to be honest, I assumed my Cryptomator files were backed-up unencrypted, since they’re accessible when I fire up my computer and run Macrium. But I just checked my image backup and they’re not. Guess there’s something else I need to do before I run my backups. So how do I ‘mount’ my Cryptomator vault to make sure it’s backed up unencrypted? Thanks!
Well, it’s kinda covered in the article, but while you have Cryptomator mounted for normal use, back up the unencrypted version.
Example: your cryptomator vault is at c:\users\{you}\Dropbox\Secure. When you mount it, it appears as drive F:. Backup the contents of Drive F:.
My Cryptomator folder is a subfolder of my OneDrive directory and shows as Z:\ in Windows Explorer. But in Macrium the Z-drive doesn’t show, not for an image backup, not for a files & folder backup. I can see Cryptomator’s OneDrive subfolder in Macrium for the files & folder backup, but those are the encrypted files/folders. What am I missing? Thanks!
A system image backup backs up cryptomator files in their encrypted form. If you are running Cryptomator and the Cryptomator virtual drive, the z: drive in your case, is mounted, you can manually copy the unencrypted files from the z: drive. I’d encrypt the backup as well, but depending on how physically secure your computer is, you may or may not want to encrypt it locally on your backup drive. I encrypt that backup. It protects me against my backup drive being stolen.
OK, thanks. Guess I misunderstood. To me Leo made it sound as if you can backup Cryptomator files unencrypted as part of a Macrium backup, but seems like that’s not the case. I’ll stick with backing up the encrypted CM files.
FYI: I found a thread on the CM forum that explains it and from which the following is taken (Backing Up Unencrypted Vaults – May ’23).
If in setting up my CM vault I let it ‘Automatically pick a suitable location’ OR ‘Use assigned drive letter’ as Mount Point it will appear in Windows Explorer as a virtual drive and therefore cannot be seen by Macrium. This is why in my case Marcium doesn’t detect my Z-drive.
However, if I were to set it up with ‘Use chosen directory’ as Mount Point, Macrium can ‘see’ and therefore map to that folder and back it up unencrypted. The drawback of this approach is that you will NOT see a drive appear in Windows Explorer like you would if you created it as a virtual drive.
In other words, it depends on how you set up a CM vault whether Macrium let’s you back it up encrypted or unencrypted. I haven’t tried this myself yet, but thought I’d share here anyway.
I’m confused.
I use Cryptomator to encrypt stuff I have in OneDrive.
I can backup the unencrypted contents of the vault, but the unencrypted contents aren’t being uploaded to OneDrive.
If recovering files from an encrypted Cryptomator vault is impossible then why would there be a reason for me to use OneDrive as part of my computer backup system?
I have a Microsoft Windows 11 Pro Dell XPS 17 9720 computer.
Thanks for the assistance.
My mistake, I wasn’t clear with my question. I meant what would be the point of backing up Cryptomator drives with Macrium Reflect 8 to an external hard drive if recovering files from an encrypted Cryptomator vault is impossible.
You can restore the entire cryptomator encrypted vault (the folder containing all the encrypted data), anywhere you like, and then mount it to extract whatever content you want from it. You do need to restore the entire vault, but if you can to that you can recover anything within.