How they work to ensure others have access if and when needed.

Unfortunately, your question reflects a common misunderstanding about passkeys. They’re probably not quite what you think they are.
Let’s clear that up and then discuss how they factor into disaster planning overall.
Become a Patron of Ask Leo! and go ad-free!

Passkeys offer easier and more secure authentication than passwords. Each device has a unique passkey, requiring device-specific authentication like a PIN or biometrics. If a device is lost, the passkey can be canceled. In emergencies, access can be granted through other methods, like recovery emails or phone numbers, making it convenient for trusted individuals like family members to access your accounts.
What’s a passkey again?
Imagine typing a quick PIN or using your fingerprint to sign in to the accounts you use most often rather than messing about with passwords. That’s a passkey — or, more accurately, those are authentication methods you can use with a passkey.
A passkey is a secure token saved to your device after you sign in with an online service supporting them. This token takes the place of your password when you need to sign in again later. To use the saved token you instead authenticate with the device holding it, typically by using a PIN or biometrics.
Passkeys are offered by some online services — for instance, Google, PayPal, Microsoft, and others. I expect more and more services to offer passkeys as the industry and users become more familiar with them. Once you’ve set it up on a device, it then uses the passkey to sign you in to the online service securely, quickly, and painlessly.
Passkeys are per-device
Let’s say you elect to use a passkey for your Google1 account. Let’s further say that you use three computers to access your Google account — a laptop, a desktop, and your mobile phone.
By default (I’ll discuss alternatives in a moment), the passkeys set up on each device are unique. They are specific to that device and that device only. Put another way, the passkey for your laptop will not work on your desktop or phone.
You have to set up each one separately the first time you sign in to the account on each device.
But if you need a passkey to sign in, and you haven’t set up a passkey on the device yet, how do you sign in?
Passkeys are never the only way in
The first time you sign in to a new machine, you need to authenticate some other way. There will always be another way. It’s that other way that allows you to then set up a passkey on that device.
So, you get a new machine, and you want to sign in to your Google account. Since there’s no passkey on that device to authenticate you yet, Google will use some other mechanism. It may:
- Send an alert or pop-up message to another device already signed into that account if there is one.
- Text a code to the mobile phone number associated with the account if you’ve set one up.
- Send an email with a code to the recovery email address associated with the account if you’ve set one up.
- Ask you for your second factor if enabled.
- It may even ask for your password if your account still has one.
Any of those things will confirm that you are who you say you are. If you’ve requested or OK’ed it, Google will then create a passkey for that specific device, and you won’t need to do any of those things on that device again.
Passkeys are a convenience
All those other steps used to authenticate you for the first time are often cumbersome and/or time-consuming. You need to remember and type a password, grab a different device, wait for a code or link to be texted or emailed, and so on.
Using a passkey to authenticate, you simply:
- Authenticate with your phone or Windows PIN, your fingerprint, your face, or whatever you have configured for that device.
That’s it. Once that’s done, you use that passkey to sign in transparently.
All those other methods still work. They’re just less convenient.
The promise of passwordlessness
You’ll note that all of those methods amount to a “second factor”. With one exception, they all require you to have access to something else. You’d need to be able to get to that different already signed-in device, the phone number to which a code would be texted, or the email account to which a code or link might be sent.
All of these are something a hacker would have no access to.
That leaves the password.2
Which you no longer need.
If you can use those other methods once on each device to set up a passkey, you never need to use a password. You never need to remember a password.
In fact, the service may not even store a password, meaning there’s nothing for a hacker to gain access to in a breach.
Passkeys without passwords are more secure. There’s nothing to lose, nothing to be stolen, and nothing to be discovered in a breach.
“Stealing” passkeys
Technically, passkeys can be stolen, but it doesn’t matter. There are two scenarios.
- If the passkey itself is somehow extracted from your system’s credential storage and copied somewhere else, it’s useless because the passkey can only be used on that device and no other. Without having actually stolen the device, the hacker can do nothing with your passkey.
- If your device is stolen the only way a passkey itself might be “stolen” is if the thief is somehow able to bypass whatever it is you use to sign in to the device.3 In practice, thieves are more likely to just turn around and sell the device without even turning it on.
Disaster planning
Finally, we can address disaster planning. What happens if you set up passkeys and the day comes when you’re unable to access your accounts and it’s time for some trusted friend, representative, or heir — your son, in your question — to do so?
In this scenario, passkeys are basically irrelevant.
What matters to your son is that one or more of the ways you used to set up a passkey to begin with is something they have access to. That means:
- They have access to another device already signed into that account if there is one.
- They have access to the mobile phone number associated with the account if you’ve set one up.
- They have access to the recovery email address associated with the account if you’ve set one up.
- They have access to your second factor if enabled.
- They know your password if your account still has one.
Typically, one of those will be enough to gain access, but the more your son or representative can access, the easier it will be for them to sign in as you.
At which point they can set up a passkey of their own.
Portable passkeys
I mentioned above that by default, passkeys are unique to each device, and thus you need to set up a new passkey for each device you passkey-enable.
Enter password vaults. As it turns out, several password vaults can also be passkey vaults. I happen to use 1Password, which can do so.
- You go through the steps mentioned above to authenticate yourself some other way.
- The service sets up a passkey.
- Your password vault offers to save it for you instead of saving it to the device.
Then, as you use your vault on other machines, you already have a passkey ready to go. Rather than being unique to each machine, it’s simply unique to your password vault. Your ability to open your vault becomes the method you enable access to your passkeys.
This might feel like a security issue, but it’s no different than storing your passwords in your password vault. If you’re comfortable doing that — as I most certainly am — then this adds no additional risk while being more convenient. It even enables greater security for systems that elect to stop using passwords altogether.
Canceling passkeys
Let’s say you lose your machine and you’re concerned that someone might gain access to it even though you have PIN/face/fingerprint/whatever authentication set up on it.
The service with which you’re using passkeys will likely have a way for you to cancel or invalidate the passkey for that specific machine.
For example, with Google, visiting https://myaccount.google.com/signinoptions/passkeys will list the devices with currently authorized passkeys.
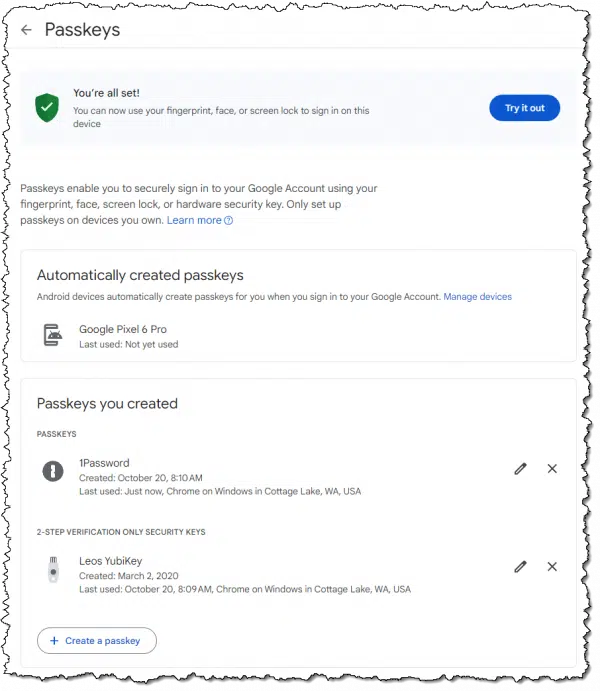
In my case, it lists 1Password, which I use for passkeys. If you don’t use a password vault, you’ll find a list of all devices on which you’ve signed in to that Google account using a passkey.
You can delete individual entries at will. For example, if my 1Password was compromised,4 I could instantly invalidate the passkey it contains.
Do this
Use passkeys when offered. Seriously. Once you get passed their unfamiliarity, I think you’ll find that they’re easier and more secure than the password management we’ve all been struggling with over the years.
And with a few simple things you’ll need to provide anyway, those who might need emergency access to your accounts won’t be inconvenienced at all.
Podcast audio
Footnotes & References
1: I’m using Google as my example throughout this article, but the concepts apply to all services implementing passkeys.
2: I suspect that a well-designed system would not rely on only a password to authenticate when setting up a passkey. But that’s up to each service, and I’m sure not all will be well-designed.
3: If they’re able to actually sign in to your PC you actually have bigger problems, since everything on the machine is presumably accessible to them. Depending on how they broke in, it’s possible that your passkeys would still be secure, as they still require proper device authentication to be used.
4: Incredibly unlikely, but it’s a good example.






Leo: Great article as usual; you covered most areas on Passkeys! However, what is NOT being covered, is the actual use. What I mean here is that we are limited by the accounts and services we connect to as to what we can use. NOT GOOD, BAD!!!! they try and push 2FA, or MFA; which is better than nothing (but not much better) as it’s still being sent by cell or email via open-air accounts. And we are NOT controlling the 6-digit codes on our machines. Furthermore, if they have a tracker or logger on their machine and don’t know it; well, they just gave any password, key value, or code that they type to them for free!! ONLY PASSKEYS controlled and managed on our personal machines are safe! As these codes never leave your machine! As long as I’m on my soapbox, let’s cover Authenticators most people use the remote Authenticator by the service, Not good!; better option is use Yubico PassKeys and use their Authenticator, which stays on your machine and they are your codes from inside your Yubico device Passkey. Bonus you can copy and paste your codes from your key and trackers or loggers can’t get them! Cause you didn’t type them! Well, I could keep going, but I have said enough! This should generate food for thought and keys! Bottom line, we need to keep pushing for business and services to start using PassKeys.! Thanks and take care, have a great holiday! Rod
Leo – Could the person who asked the question might be referring to a hardware authentication device (like a yubikey) instead of a passkey?
Unclear. The wording is mixed.
So far, I have passkeys for my Google and Microsoft Accounts, but nowhere else that I’m aware of. I’m hoping more services start to offer passkey access because I agree with Leo, they’re even more secure than passwords with 2FA. At this point, I have 2FA set up on all my Internet accounts. When I went through all the accounts I had stored on LastPass after the breach, I eliminated any that did not offer that option (2FA) because if they don’t care enough about my security to offer it, I don’t trust them enough to let them keep my stuff.
I decided to stay with LastPass after the breach because I figure that if I have 2FA set up on all my Internet accounts, the security of my passwords is a secondary concern (they’re useless without my second factor). Leo, If I’m wrong about this, please respond telling me how and why.
If truth be told, I have my LastPass vault set up so I know where to find all my Internet accounts (and I have Firefox ‘trained’ to set a web address as the top pick with the first letter I enter in the address field – the character “a” gets Amazon, “f” gets Facebook, etc.), and I don’t want to go through all that organizational process again with another provider for what I currently consider to be a minimal upgrade in security if any at all. Don’t get me wrong, I do care about security, but I’m not fanatically paranoid about it.
I’m careful about the personal information I put out on the Internet – I use generalizations without specific names, ages, etc. I avoid clicking links or check that the URL matches the label before clicking, and I treat everything on/that comes from the Internet with a very healthy dose of skepticism. Finally, I have the six credit bureau accounts I know of frozen to thwart identity thieves, so for the most part, I’m fairly well protected from most miscreants who are likely to try to do me in.
I hope I didn’t wander too far off-topic here. I know this item is about passkeys, but they’re about Internet account security, and I believe there’s much more to Internet security than account access, so I added a few things I do to be as safe as I reasonably can when I’m on the Internet to help others consider things that may help them be safer out there too.
Ernie (Oldster)
Hi Leo and thank you for the article.
I imagine my concerns re passkeys are due to lack of understanding/knowledge and I am hoping you can explain further please.
My concern with passkeys is if someone stole my device, and gained access into it by way of a brute force attack, they would then have access to all my accounts that use a passkey, e.g. if they cracked my computer PIN. I understand that fingerprint and face identification are more secure, but I have also heard of examples where fingerprint or face identification may sometimes be unreliable and allow a thief access – is that possible?
I currently use 1Password, and if someone currently stole my device, and gained access to it by a brute force attack, they would then have the impossible task of breaking a 32 character pass-phrase I use for 1Password. Thus I think I am reasonably secure presently.
However, if I was to use 1Password as a repository for my passkeys, would I still by using my strong 32 character pass-phrase to gain access to the 1Password vault containing all my passkeys? Or, would a passkey be immediately available to anyone who has signed into by device, perhaps by a brute force attack, and now has access to all the passkeys in 1Password? This is my main concern.
Hoping you can help.
Thanking you.
Phil.
I hadn’t thought of that but it’s a good argument for using a tool like 1Password to save passkeys.
Without 1Password: Person needs access to the machine, and the PIN/fingerprint/face of the owner.
With 1Password: Person needs access to the machine, the PIN/fingerprint/face of the owner, and the 1Password master password.
On the last post. Bitwarden can and does save passkeys now. So yes, the thief would need three things:
1. Your device
2. Access to that device by way of a PIN fingerprint, and/or whatever you use (I use the combination of Bitlocker + fingerprint to get into Windows)
3. Access to Bitwarden (needs a 9 digit PIN)
I’ll add a 4th door – for certain accounts they’d also need my Yubikey and Yubikey PIN
Feels secure enough for me.
Thanks for this article.
I have started to apply Passkeys to some of my Google accounts.
I can not see how to obtain a passkey for a Microsoft consumer or free accounts.
“Passwordless” is offered, but this appears to be a choice between using Microsoft Authenticator, Windows Hello, physical security keys (like Yubico), or SMS codes. I presume that there is some form of a passkey behind the scenes for Microsoft Authenticator.
Not all services offer them yet, and I suspect larger services (like Microsoft) are in the process of rolling them out so they may not be available to all accounts. Yet.
Hi Leo,
We have always gotten a sim card and purchased a data package when we have traveled in Europe. It is problematic because I can’t use MFA or 2FA. Will the use of passkeys work around this issue? Thanks from a long-time reader.
All I can say is “maybe”. It depends on how persnickety the specific online service chooses to be.
I live between Europe and the US. I have a T-Mobile account in the US that allows me to send and receive SMS texts for free and gives me 6 GB 5G internet per month. I also have a local SIM card for unlimited calls in the EU.
Check if your mobile provider has anything like that. If not as long as you have a GSM SIM card, sending SMS texts are only a few cents.