Be sure to also check out the Best Articles page!

|
Are Deleted Emails Really Deleted?Deleted an email and think it’s gone forever? I'll explain what “delete” really means in webmail and desktop programs, why trash folders and database files can leave messages recoverable, how backups and even court orders can bring them back, and the inconvenient fact that the other person may still have a copy.2026-03-02 - #17447 |

|
Before You Click: 3 Quick Checks for a Suspicious WebsiteFound a website you’ve never heard of and not sure you should click? I'll show you three fast clues -- domain dates, server location, and site history -- that can help you judge whether a site feels trustworthy or sketchy before you commit.2026-02-28 - #189667 |

|
How Does Cloud Storage Work?Cloud storage sounds mysterious, but it’s really just your files living on someone else’s online computer. Let's look at how synchronization moves your changes between devices, why it can feel like backup, and the big catch: deletes spread everywhere too.2026-02-27 - #75658 |
|
Why Am I Being Asked for Additional Verification on Sign-in?Traveling and suddenly locked out of Outlook.com? I'll explain why Microsoft asks for extra sign-in proof, what “something unusual” really means, and how to set up backup email, phone, or authenticator options before you leave so you can get your code and your account back when it matters most.2026-02-26 - #92840 |

|
What Do I Do If I’m Being Harassed, Bullied, or Stalked Online?Online harassment can happen to anyone, but what can you actually do about it? I'll break down whether it's illegal, how to identify who's behind it, ways to make it stop, and the critical mistakes to avoid so you can protect yourself and your loved ones.2026-02-25 - #15569 |
|
Dealing With Video Starts and Stops While Watching: Three Common Causes and Three Possible SolutionsThere are common causes, and sometimes simple solutions, for a video that starts and stops as you watch it.2026-02-23 - #2981 |

|
The Nirvana FallacyI'll explain the Nirvana Fallacy -- rejecting helpful tools because they aren’t perfect -- and show how that thinking can make you less safe.2026-02-21 - #179344 |

|
Is It Safe to Look, Just Look, at Spam?Curious about what’s hiding in your spam folder, but worried a single click could infect your computer? I'll explain the simple rules that keep you protected and how to view raw message source safely.2026-02-20 - #6335 |
|
In Search of a Complete Photo Management AppStruggling to organize photos? Me too. I'll explore the features of my ideal photo management app.2026-02-19 - #189407 |

|
How Microsoft Extortion Can Lead to Data LossOneDrive’s “backup” can quietly move your Desktop and Documents into the cloud, fill your free 5GB of storage, and start pushing you to “free up space.” Here’s the scary part: the wrong click can delete files everywhere.2026-02-18 - #182312 |

|
Don’t Call Yourself StupidFeeling “stupid” about computers? STOP IT. I'll discuss why that label holds you back, how attitude changes what you can accomplish, and better words to use when you need help.2026-02-16 - #13521 |

|
How Long Does Email Delivery Take?Email is typically very fast, but sometimes it can take hours or even days. I'll explain why delays might happen, what spam filters and busy servers really do, and how long mail servers keep trying before they give up.2026-02-14 - #3501 |

|
Three Ways Spammers Can Tell If You’ve Opened One of Their EmailsI'll share three simple ways spammers know you’ve read their email, and how you can avoid more spam in the future.2026-02-13 - #189165 |

|
Lessons from a FallAn injury turned everyday tech into a lifeline and exposed a few surprises. From what worked to what failed, I'll share my experience so you can be a little better prepared when life throws you an inevitable curveball.2026-02-12 - #188836 |
|
How Do I Get Rid of Copilot Everywhere?Copilot popping up everywhere? I'll show you how much of it you can disable or hide.2026-02-11 - #177830 |
Ask Leo! Analysis via Claude CodeI asked Claude Code to analyze the last 20+ years of Ask Leo! content.2026-02-10 - #189664 |

|
How Do I Decrypt Files Encrypted by Ransomware?Prevention and preparation are the best solutions to ransomware.2026-02-09 - #20068 |

|
Can You Recommend a Cordless Keyboard and Mouse?Tired of keyboards that fail too soon or slow you down? I’ll share what I think matters when choosing a keyboard and mouse, what I do, and why “wireless” may not be your friend.2026-02-07 - #189040 |
|
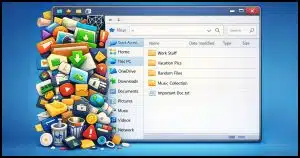
Managing Windows File Explorer’s Navigation PaneFile Explorer’s messy left side driving you crazy? I'll show you how to clean up the navigation pane, remove clutter, and pin only the folders you actually use.2026-02-06 - #188995 |

|
How Do I Get a Program to Auto-start When I Sign In to Windows?Want a program to start automatically every time you sign in to Windows? There’s a simple, built-in way to do it.2026-02-05 - #8111 |

|
Has My Computer Been Hacked?It's easy to jump to the conclusion your computer has been hacked, but it's usually not the case. Regardless, preventing a hack is easier than recovering from one.2026-02-04 - #4807 |

|
The For-Pay Email Providers I RecommendPeople often use free email providers only to lose everything when a problem occurs. So what should you look for in a paid email provider?2026-02-02 - #2824 |

|
Unexpected Authenticator Alerts: Annoying, Scary, or Harmless?Random authenticator requests can be unsettling. Are you being hacked, or is something else going on? I'll discuss why these alerts might happen, what they really mean, and what to do.2026-01-31 - #188936 |

|
How Do I Route My Email Through Gmail?Google quietly removed the Gmail feature that let you pull all your email into one inbox. If you relied on Gmail as your central hub, it’s time to rethink your setup. Here’s what no longer works and the options that still do.2026-01-30 - #4415 |

|
The Top Five Small Business Security RisksRunning a small business, especially from home, puts your data at risk in ways you might not expect. I'll discuss what I see as the five biggest security threats facing small teams.2026-01-29 - #188874 |

|
The Recycle Bin You Might Not Know About (Perhaps Holding Data You Thought You’d Lost)Think the Recycle Bin on your PC is the last stop for deleted files? Not always. I'll show you a second, often-overlooked Recycle Bin hiding in your cloud storage. It might rescue files you thought were gone for good.2026-01-28 - #188843 |

|
Is Private Browsing Really Private?Private browsing sounds safer than it really is. I'll explain what Incognito mode actually hides, what it absolutely doesn’t, and when it’s still worth using. If you think private mode keeps your online activity secret, you’ll want to see where the real limits are.2026-01-26 - #27929 |

|
Why Didn’t Microsoft Fix My Pet Peeve?Ever wonder why Microsoft never fixes that one thing that drives you crazy? It’s not personal. I'll break down why some annoyances stay put, how Windows chooses what to fix, and why even simple changes can be surprisingly risky.2026-01-24 - #3345 |

|
How You Can Avoid Social Media AlgorithmsSocial media often shows you what it wants you to see, not what you asked for. I'll explain how those algorithms work and the steps you can take to see more of what matters to you.2026-01-23 - #138044 |

|
How Does My Computer Know Where I Am?Ever wonder how your computer or phone “knows” where you are, and why it sometimes gets it wrong? I'll break down the clues your devices use, why location mistakes happen, and what you can do when websites think you’re somewhere else entirely.2026-01-22 - #187540 |

|
Why Am I Seeing So Many CAPTCHAs?Tired of being asked if you're human? I'll explain what site owners like me are dealing with behind the scenes and why you’ll probably be clicking “I’m not a robot” a lot more often.2026-01-21 - #187517 |

|
Is it Safe to Put Two-Factor Codes in My Password Vault?Storing 2FA codes in your password vault might slightly reduce security, but the risk is minimal compared to the convenience.2026-01-19 - #168687 |

|
Find Your Microsoft Account Recovery EmailYour Microsoft account recovery email address is an important part of making sure you never lose access to your account.2026-01-15 - #169010 |

|
An Unexpected Way Videos Can Expose Your LocationSomething many people do every day may expose their location in ways they aren't aware of.2026-01-14 - #167448 |

|
So, Leo, Where Ya Been?Did ya miss me? Did ya notice? I'll explain what was happening behind the scenes.2026-01-14 - #188504 |

|
How Can I Tell If a Web Address Is Safe?URLs are simple in concept, but can be constructed in ways that might fool you. I'll look at some examples and discuss what's important.2026-01-12 - #4399 |

|
Don’t Be Scammed When Recovering an AccountDon't let your panic open the door to scammers.2026-01-10 - #173764 |

|
How Do Spam Filters Work?Spam filters can be sophisticated or simple. I'll look at some of the characteristics of email that spam filters check.2026-01-09 - #18972 |

|
Six Signs of a Phishing AttackA friend received a fairly convincing phishing attempt. I'll cover the signs that showed it was spam.2026-01-08 - #136589 |

|
Can I Trust Cloud Backups?Backing up data using an online backup service can be an important part of an overall strategy, but it's important to understand its limitations.2026-01-07 - #20208 |

|
Does the Recycle Bin Take Up Space, and Where Is It?The Recycle Bin is your friend. I'll show you where it lives and how to control the space it uses.2026-01-05 - #173788 |

|
Can I Delete Temporary Files in Windows?Temp files can pile up. Why is that, and do you need to worry about them?2026-01-02 - #173949 |

|
How Do I Find My Downloads on My PC?Downloading a file from the internet is easy, but controlling where downloads go takes a little more understanding.2026-01-01 - #2775 |

|
Help! Someone Is Inside My Computer, Controlling It!When things behave unexpectedly, many people assume their computer has been compromised by remote hackers. Most of those people are wrong.2025-12-31 - #142596 |

|
What’s a QR Code, and Can You Trust Them?QR codes are a nifty way to encode web addresses and other text in a way that's easy for your smartphone to decode, but they are not without risk.2025-12-29 - #143703 |

|
Privacy and Searching for Phone Numbers OnlineYou have an email address and you want the associated phone number. It's unlikely you'll find it, but there are a few things to try.2025-12-27 - #166374 |

|
How Do I Tell If an Email Address Is Fake?It's hard to determine whether an email address is fake.2025-12-26 - #164415 |

|
How to Deal with SpamSpam is inevitable; just don't ask for more.2025-12-25 - #161851 |

|
Four Risks With Free Wi-FiFreely accessible Wi-Fi is almost everywhere, and most systems are set up to use it safely. There are a few things to pay attention to in order to stay safe.2025-12-24 - #158026 |

|
Backups Are GREAT SecurityDon't overlook backing up as part of your computer security. When the worst happens, it's your backup that will save you.2025-12-22 - #147489 |
