Featured
Articles featured in the weekly Confident Computing newsletter from Ask Leo!.
How Should I Format My Thumbdrive?
Looking to format a USB thumb drive but confused about FAT32, exFAT, and NTFS? I’ll break down each file system’s strengths and limitations and help you choose the best format based on compatibility needs, file sizes, and which devices you’ll use it with.
What Do I Do If I’m Being Harassed, Bullied, or Stalked Online?
Online harassment can happen to anyone, but what can you actually do about it? I’ll break down whether it’s illegal, how to identify who’s behind it, ways to make it stop, and the critical mistakes to avoid so you can protect yourself and your loved ones.
How Microsoft Extortion Can Lead to Data Loss
OneDrive’s “backup” can quietly move your Desktop and Documents into the cloud, fill your free 5GB of storage, and start pushing you to “free up space.” Here’s the scary part: the wrong click can delete files everywhere.
How Do I Get Rid of Copilot Everywhere?
Copilot popping up everywhere? I’ll show you how much of it you can disable or hide.
Has My Computer Been Hacked?
It’s easy to jump to the conclusion your computer has been hacked, but it’s usually not the case. Regardless, preventing a hack is easier than recovering from one.
The Recycle Bin You Might Not Know About (Perhaps Holding Data You Thought You’d Lost)
Think the Recycle Bin on your PC is the last stop for deleted files? Not always. I’ll show you a second, often-overlooked Recycle Bin hiding in your cloud storage. It might rescue files you thought were gone for good.
Why Am I Seeing So Many CAPTCHAs?
Tired of being asked if you’re human? I’ll explain what site owners like me are dealing with behind the scenes and why you’ll probably be clicking “I’m not a robot” a lot more often.
So, Leo, Where Ya Been?
Did ya miss me? Did ya notice? I’ll explain what was happening behind the scenes.
Can I Trust Cloud Backups?
Backing up data using an online backup service can be an important part of an overall strategy, but it’s important to understand its limitations.
Help! Someone Is Inside My Computer, Controlling It!
When things behave unexpectedly, many people assume their computer has been compromised by remote hackers. Most of those people are wrong.
Four Risks With Free Wi-Fi
Freely accessible Wi-Fi is almost everywhere, and most systems are set up to use it safely. There are a few things to pay attention to in order to stay safe.
7 Ways to Increase Internet Speed in Windows
Internet speed: we all want it. Here’s how to improve yours.
Three Reasons You Can’t Get Your Account Back
I hear from people who have lost their accounts permanently way too often. Here’s how to avoid being one of them.
My Two New PCs
I swapped out two old computers for a pair of tiny but mighty mini-PCs, and I’m impressed. If you’ve ever wondered whether one of these small machines could replace your bulky desktop, this peek behind my setup might surprise you.
What Happens If I Don’t Update to Windows 11?
Thinking of skipping or delaying Windows 11? You can keep using Windows 10 safely, but changes are inevitable. From security updates to app support, here’s what happens if you stay put. Learn how long you can expect things to keep working before problems appear.
How What I Do Is Threatened by AI
AI is rewriting the rules of the web, and sites like Ask Leo! are feeling the squeeze of fewer clicks, more bots, and uncertain futures. What does that mean for the content you rely on? I’ll look at the challenge, the irony, the fear, and what you can do to help.
How Often Should I Reset My PC?
Is your PC slowing down, acting odd, or just feeling old? A full reset might be the fix, but how often should you do it? I’ll share when it makes sense, when it doesn’t, and how to decide if your computer needs a fresh start.
Can My Computer or Signed-In Account Be Hacked from the Internet?
Worried that staying signed in leaves you open to hackers? I’ll explain why your router, firewall, and smart habits protect you, what the real risks to your accounts are, and the simple steps you can take to stay safe online.
I Opened Something I Shouldn’t Have — Now What?
Accidentally run or opened something suspicious? We’ve all done it. I’ll walk you through the options from scans to resets, and consider what to learn from the experience.
Public or Private? Picking and Changing the Windows Network Setting
Not sure if your Windows network should be public or private, or even what that means? I’ll show you what each means, when to use them, and the simple steps to switch.
Should I Update to Windows 11? (October 2025 update)
Windows 10 support ends October 14, 2025. Should you move to Windows 11? I’ll walk you through the pros, cons, and options: upgrade now, wait for new hardware, or even stick with Windows 10 safely. The choice is yours, but it’s time to decide.
How to Keep Using Windows 10 Safely after Support Ends
Worried about Windows 10 after support ends? Don’t be. I’ll show you the simple steps — good habits and reliable security software — that will allow you keep using your Windows 10 computer safely.
On Trusting and Not Trusting Microsoft
Worried Microsoft is peeking at your files in OneDrive? The truth is more complicated and perhaps surprising. I’ll look at what scanning really means, why avoiding OneDrive may not be enough, and how trust in Microsoft’s products comes down to risk, reality, and choice.
Can Your Video Chat Be Intercepted and Recorded?
Your video chats are usually private and encrypted, but nothing is foolproof. The real risk isn’t hackers; it’s the person on the other end, who can record everything. Learn why interception is rare, where the real danger lies, and the one rule to follow if you’re unsure.
Should I Just Use AI for Searching?
AI or search engine? Both promise answers, but in very different ways. From accuracy and freshness to bias and even energy use, each has trade-offs you need to know. Before you pick one over the other, find out why the smartest choice might be both.
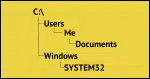
What Is the “Normal” File Hierarchy in Windows?
Ever wonder where Windows puts all your stuff? From drives to folders to files, the “normal” Windows hierarchy has a logic, though it’s often hidden by shortcuts and misbehaving programs. Here’s a look at how it works and how to keep your files organized.
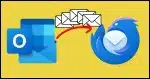
How to Transfer Your Email From a PST to Thunderbird for Free
Switching from Outlook (classic) to Thunderbird? You don’t need to buy tools. With a little time and a free email account, you can move your messages yourself. I’ll walk you through the steps to transfer your email safely and reliably.
How to Save or Recover Your BitLocker Recovery Key
BitLocker could be running on your PC without your knowledge. Without the recovery key, you risk losing everything. I’ll show you three ways to check, find, and save your key.
Is It OK to Reuse Passwords on “Unimportant” Sites?
Reusing passwords on sites you don’t care about might feel harmless, but it still can open the door to bigger problems. I’ll look at why even “unimportant” accounts matter more than you think, the risks of cutting corners, and simple ways to stay safe.
Faking Reality: How AI Images Are Being Used to Scam You
Scammers take advantage of AI’s ability to create fake photos that look very real. From phony images of your car to completely made-up situations, it’s easier than ever to be fooled. Learn how they’re made, why they’re dangerous, and what you need to do to protect yourself.
Changes for Ask Leo!
Changes are coming to Ask Leo!, including the removal of outside ads. I’ll explain why this (very) scary step is necessary, how search engines and AI are changing the game, what it means for the future of the site, and how you can help.
A Hacker’s Four Favorite Ways to Get You
A security professional shared the top four most successful hacks that compromise business accounts. I’ll walk through them and show how they all apply to you and me as well.
How to Block the Windows 11 Upgrade and Stay on Windows 10
Want to stick with Windows 10 and avoid the surprise of waking up to Windows 11? You have options. I’ll show you a simple, free tool that puts you back in control of system updates, keeping Windows 11 at bay until you decide otherwise.
Should You Sign Up for Extended Security Updates (ESU) for Windows 10?
I’ll review the security protection for Windows 10 beyond its official end-of-support date: what it means, pros and cons, and what we know about how to get it — perhaps even for free.
Two-Factor Authentication: It’s Not as Complicated as You Think
There are some persistent myths about two-factor authentication that stop people from adopting it. I’ll clear them up so you can use this simple yet powerful security feature with confidence.
Where Are My OneDrive Files?
What OneDrive does with your files can be both frustrating and confusing. I’ll walk through two important issues: what’s really on your computer (or not) and the impact of using OneDrive’s horrid backup “feature”.
My OneDrive-free Experiment
I wanted to see if I could live without OneDrive and avoid the risk that OneDrive would make changes I didn’t request. Turns out, it’s not that hard. I’ll walk you through what I did and how I did it.
Why I Don’t Expect a Windows 10 Apocalypse
Don’t believe the FUD; your PC won’t suddenly collapse into chaos when Windows 10 support ends. With updated security tools, smart habits, and backups, you can keep using Windows 10 safely long after Microsoft stops updating it—without fear, hype, or panic.
What Is a Passkey?
Passkeys are a new form of signing in that promise to be easier and more secure. I’ll walk you through some of the high level concepts and how they work, and how they keep you safer than passwords.
How End-to-End Encryption Protects Your Messages and Where It Fails
You would think that for such an important concept as end-to-end encryption there’s be some agreement on exactly what it means. Sadly, not so. There’s the correct definition, and then there’s the marketing definition. One protects you, the other not so much.
Should You Leave Your Backup Drive Plugged In? The Real Risk
Some people are afraid to leave their external backup drive connected. They’re trading a small risk for a much, much larger one.
Start11: Another Start Menu Replacement
Want your old Start menu? We can do that. Want to tweak the taskbar in useful ways, including its position? Start11 can do that too.
Avoiding Scams: Why Hackers Can’t Recover Your Gmail for You
You’ll often find testimonials and offers of amazing account recovery success. It’s a trap.
Yet Another Way to Install Windows 11 With a Local Account
The latest workaround allowing you to set up Windows 11 without a Microsoft account.
8 Ways AI Can Help You Every Day
Discover how AI can actually make your life easier. From summarizing long articles to rewriting tricky text, answering vague questions, or even helping you write better emails — these eight real-world examples show how tools like ChatGPT, CoPilot, and Perplexity can save time and boost confidence every day.
Don’t Trust the Cloud. You Need to Back Up Your Email and Online Data
It’s your data, so it’s your responsibility to back up the information you keep online.
If You Don’t Have a TPM, You Might Still Have a TPM
Many machines reported as not having a TPM have one that’s simply not enabled.
No, Windows 11 Is Not Forcing You to Buy a New Machine
Your old machine won’t suddenly become useless. I’ll explain why Microsoft’s hardware rules aren’t a conspiracy, and what real options you have, from keeping Windows 10 to exploring Linux, without wasting good hardware.
Why Email Forwarding is Broken and What to Do Instead
Learn to pull your email together rather than push it.
Microsoft Killed WordPad. Here’s How to Revive It.
WordPad is being removed from Windows 11. We can get it back.