Yes, but it’s kinda useless.

You’re correct . . . it could put a big dent in laptop burglaries if MAC addresses were truly traceable. It would at least increase the odds of stolen equipment being recovered.
But they’re not traceable . . . at least not in any way that could help.
Let’s look at why.

MAC Addresses
MAC addresses are unique identifiers for each network interface on your device. While they do identify the device, when used in networking they travel only as far as the next device, like your router. That limits the usefulness of MAC addresses for any kind of device location or tracing.
MAC addresses are unique — sort of
A Media Access Control (or MAC1) address is a unique 48-bit number2 assigned to every network interface. If your computer has multiple network interfaces — say both a wired ethernet port and a wireless network adapter — each interface will have its own MAC address.
In theory, it’s unique. In theory, every network card or network interface should have its own unique MAC address, different from every other network card or interface on the planet.
There are three problems:
- Occasionally, manufacturers don’t ensure they’re unique, so multiple network interfaces can have the same MAC address.
- In many network interfaces, the MAC address can be set in software — meaning whatever the original MAC address, it can be changed.
- Some operating systems now randomize the MAC address.
So the uniqueness on which we might want to rely is not 100% reliable.
But that isn’t really the biggest problem.
Help keep it going by becoming a Patron.
MAC addresses travel only so far
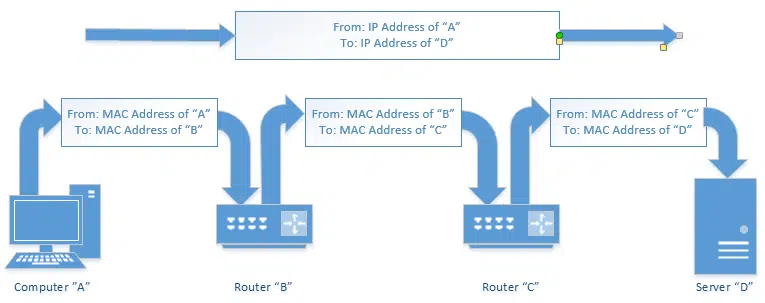
The MAC address is used by the network to identify which piece of hardware a packet of information is to be sent to. While the IP addresses involved indicate the original source3 and ultimate destination, a MAC address is used only on connections from one piece of networking equipment to the next.
That means when information leaves your computer, it has your computer’s network adapter’s MAC address. But when it arrives at your router, that MAC address is removed. When your router sends the information further upstream to your ISP’s router, it contains the MAC address of your router. When it moves from the ISP’s router to another router on the internet, it contains the MAC address of the ISP’s router.
And so on.
When it comes to data traveling over the network, your MAC address never makes it further than the first piece of networking equipment between you and the internet.
MAC addresses gone wild
MAC addresses, however, have been used for other things.
For example, since MAC addresses are theoretically unique, a MAC address could be used as a unique identifier for tracking the actions being taken by or on a specific computer. (I’m not aware of specific situations where this is done — I suspect other unique identifiers are easier to use — but it also wouldn’t surprise me if a MAC address were used in this way somewhere.)
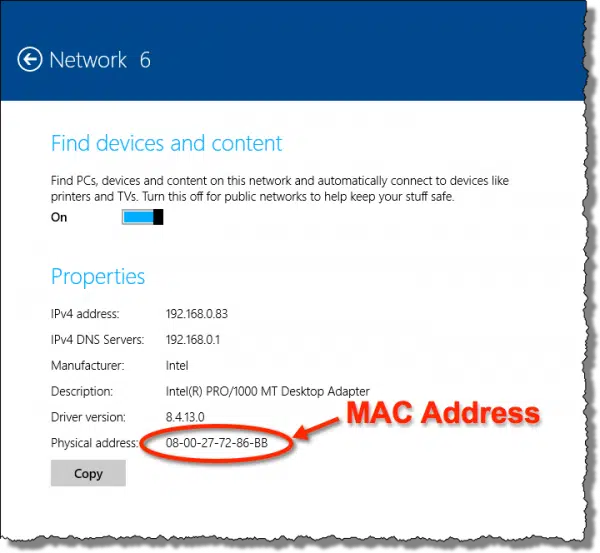
The MAC addresses of the network adapters on your computer are easily readable by software, and could be used for just about anything . . . except tracking your stolen laptop via its network connection.
Sorry.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
Footnotes & References
1: Completely unrelated to Apple –except that like all computers, your Mac’s network adapter has a MAC address. But it’s unrelated to it being a Mac from Apple.
2: Meaning it can have a value between 0 and 281,474,976,710,655.
3: The original source at that time. IP addresses are typically dynamic and often change.




What you can do is install a tool like dyndns or no-ip on your system. What they do is resolve the wan ip address of the system the software is installed on into a hostname. You can then log into your account and see the IP address last used when the software was running. This can aid law enforcement with the combination of the ISP used by the thief, to track him down. You can even run a tracert on the hostname and get a general idea where they are located by the routers the ping packets hop through.
All this is one of the many things software like Leo is talking about and law enforcement use to track down stolen computers. Chances are though, if it was a professional thief, they would have whipped the drives, software and all, making it virtually impossible.
A hostname will definitely log an IP Address the machine used to connect from so you at least get something if the machine was connected before being wiped.
hiii….
i want to know that whether the websites i visit through my laptop be traced by the company i work for, if they dont know my MAC id.
12-Jun-2010
Hello, yea it’s very simple actually , if your company host a network , the network administrator do have access to proxy,firewall and most network logs, they can find most of the web info a particular ip was accessing, if your company uses DHCP for ip allocation that might make it harder to pin you since the lifetime of an ip is dynamic, on the other point as a digital forensic analyst i can easilly pin you on whatever corner you can think of,if i acquire your laptop and you had accessed some “suspicious sites” then you are done, thats it for you, even if you try to wipe you history or format your harddisk.
I’m studying for a middleware exam atm, reading about home gateways.
When talking about device discovery and management (DHCP) my lecture notes say “This data will be accessible to the RMS” (ISP’s Remote Management System)
Does this not mean that the ISP’s sytem can see what devices are connected to my network and therefore trace a stolen laptop if it’s connected via one of their clients networks??
Thanks
When you have a local network, it usualy mean that you have a router connected to the internet, and any other devices are connected to the router.
An ISP can ONLY see the router itself. There is no way that it can know what, and how many, devices are connected to that router.
This is not always true. If the ISP manages the router as well (which is very common in a lot of markets where the ISP provides the modem which includes the router function), they can definitely see all the devices with their MAC-addresses. To prevent this add a router of your own to the network.
Another way for ISP’s (or other internet access providers) to do get access to your device’s MAC address is by providing free WiFi spots or guest networks.
If you are paranoid about your MAC address begin logged or tracked, having an additional firewall and providing your own WiFi device is wise.
I thought they could be traced. I opened 47 hushmail email accts for my students one morning at Starbucks. When we went to log into them, hushmail said they had blocked my computer (not closed the accts) in case of fraud or spam and to contact them. I did (but they never responded). I went home and tried again. That’s 3 different IP addresses that hushmail knew it was my computer. I thought they’d IDed my mac address. If not, what was it.
If you accessed the internet through a router, the MAC address of your computer would only be visible to the router
http://ask-leo.com/whats_the_difference_between_a_mac_address_and_an_ip_address.html
It possible that this blocking was accomplished through something as simple as a cookie. Try clearing your Saved Cookies and see if that helps.
This article on clearing the browser cache will show the steps needed to do that, just press Delete Cookies where it says Delete Temporary Internet Files (or Clear Cache depending on which browser you use). You might also Delete the Temporary Internet Files anyway, just in case.
http://ask-leo.com/whats_a_browser_cache_how_do_i_clear_it_and_why_would_i_want_to.html
R
That will be based on a cookie, placed on your computer at the time of registration, by the website. Not on your MAC address. The same way that Facebook remembers you’re already logged into that site via your computer.
One thing that I believe is an exception to the rule is when one connects to the internet using an ISP’s “Hotspot” or Wifi Network (like Xfinity, Optimum Wifi) on the road or some of those “free” connections like the ones in McDonald’s, Starbucks, etc. Some of these hotspots require you to have an account and log-in first, while others are free to roam on or give you a time-limited trial. I experimented with the “free” ones (no log-in credentials needed) and realized after going to the same spot several days that my MAC address was totally traceable because obviously the ISP controls their switches and routers (I cleaned all cookies, etc so I know it was MAC-related tracing). If you actually look at the first URL once you start browsing, you will see your MAC address as identifier at the end of the URL, as a way of remembering you the next time you are on their network. Also, the “fine print” disclaimers on these connections (which no one bothers to read) explain that your MAC address is being logged. If you think about it, in theory, if a laptop was stolen and you knew your mac address and someone tried to log on one of these hotspots, the ISP should be able to identify such connection, however I’m assuming that only law-enforcement would be able to obtain such records and as Leo kindly pointed out, equipment manufacturers can’t ensure that a MAC is unique…just food for thought…cheers
The MAC address is used between two devices. It’s value is static. It’s effectively a local address.
The IP address is used across the internet. It’s a global address. It’s value is usualy attibuted to your device for some time and may change periodicaly.
As Leo pointed out, the MAC addresses of the interfaces on your device can be accessed by software. And to paraphrase leo regarding malware, once some MAC address reading software is on your device it can do almost anything with it. (Some proprietary software used MAC addresses for license control – which played havoc when people installed a new interface.) So, there may be an opportunity for some clever soul to develop a security app that will periodically read the MAC address of your interface(s), plus any current location identifying info (that might include network & ISP data), and register it all with a server somewhere. If you installed that app, it would provide a way to track, somewhat, a stolen device, as long as it was still running. And for the overly security minded – you do know what all those background apps on your computer are doing, don’t you?
Sir if we can’t find stolen laptop by mac address .. then what type of information should be used to find a stolen laptop .. or there is no way to find a laptop…?
There are apps you can install on your computer like PreyProject https://preyproject.com/ which can help recover a lost computer or device. Obviously, they are not perfect and are probably not difficult to circumvent, but it might work in the case of your device being stolen by a non-sophisticated thief. Has anyone here had an experience with PreyProject?
Well it only works if the thief doesn’t wipe the pc,but if it has been wiped ?
As I said above, if the thief is sophisticated, there’d be no way to track it.
A MAC address has no relation to an IMEI number.
It cannot. Repeat IT CANNOT. That feature only applies to certain routers in certain network layouts. It does NOT work outside of some very specific situations.
My bt home hub 5 lets me see what devices are connected to it. Once i log in to it, in the section ‘settings’, ‘bt access control’ there is a drop down list of devices (which can have their access limited at certain times). on my list there are all our household devices but also 17 (!) other devices which are described as ‘uknown : xxxxx’ where the numbers in xxxxx are the same as the mac address.
can anyone explain what these ‘devices’ are and how come they have access to my home hub (and presumably therefore to my network login password and other devices o the system?). Also, any advice on how to delete themwould be great thanks asthere are more of them than the maximum number of ‘rules’ I can set for limiting access.
I assumed they were left over from the times my isp has accessed my router to help sort variousproblems …but I guess they coukd be from anywhere (including hackers?)
any information and advice very welcome …thanks
As long as your wireless network is protected by WPA/PSK and NOT WEP, the mac addresses that you are seeing shouldn’t be of any concern. It is theoretically possible that if you have a relatively large family with friends that there may be 17 unique devices listed that have had access at one time or another in the recent past to your home’s internal network. However it is highly unlikely that these have anything to do with any equipment that your ISP may have used at any time in the past. You can do a lookup of a mac address to find out the Hardware Vendor and then use that information to help you determine which devices each mac address might represent. If your wireless network is open, the devices could be anything around your home within a reasonably short distance. But, if you live in an apartment in New York City for example, that could be a LOT of folks!
Hi Leo first of all I must say this is a tremendously interesting forum that you have here and I have a question. I pay $30 per month fee to a company to access market information. That information is accessed by login.Recently the owner of the company contacted me to say that I would have to pay $150 per month for no reason other than I worked in the industry and therefore he wanted to charge me a commercial rate. I cancelled that account and reapplied so I could get the same rate as everybody else, using a friends name and Credit Card. Unfortunately probably through IP tracking he established that the new account which I opened was in fact mine I assume that this was done through IP tracking so I have arranged with my carrier to get a new IP address. Because I have cable connection to my PC I can’t get a new IP address unless I get a new router so I have ordered the new router which should give me a new IP address . My question is … once I have the new IP address is there any way for this thief 2 determine if it is me logging into the system and can he in fact find out my MAC address to identify me. What can you recommend I do to stop him knowing my new account is not me ….im being held to ransom by this grubby businessman. Please help me.
THere are various ways he could track that you’re coming from the same machine. Check out “evercookies” as just one example – Supercookies and Evercookies: Resistance is Futile.
I think you have two choices: stop trying to hide who you are and pay the additional fee, or stop using that service completely.
if sim card is not inserted in mobile phone but internet acessing in that mobile through router, so then is it possible to track that phone .
If the SIM card is removed, your phone would be untraceable unless you have a security program like PreyProject installed.
preyproject.com
A phone could be located through the cell phone company, but if the SIM card is removed, the phone couldn’t be traced via the MAC address. You’d need some kind of tracking software like preyproject.com installed to find it via WiFi.
Then how can police trace the device if any stolen device connect to the Internet? Suppose if a man get lost his smart phone or laptop.He complain regarding this issue to police with full purchase document than how corps can find that stolen device with location if theft connect with Internet?
Unfortunately, they can’t. They would be able to trace a smart phone via the cell network if they continue to use it with the same SIM card, but that’s a long shot. There are utilities like Prey Project to help locate lost or stolen devices, but again if the thief uninstalls that, it wouldn’t be traceable.
If some one stoles your laptop and have a active google account on it, try searching thru web history & saved accounts & passwords in to that account & you may even find even his name or at least accounts that he uses to login on sites & you may ask the site admin to try to track the ip that the tief it’s ussing. Note that it may also be a normal person that bought the laptop fron the tief.
However, on some builds of Linux distributions, you can find a Geolocator Application within the Fern Wifi Cracker Application, which claims to be a Mac Geolocatory Tracker. Why would this utility even be created if it is impossible to track a MAC address from two separate networks?
Without knowing how it works, I can’t say. What I do know is how far MAC addresses travel in the protocol, and it’s not far enough to be useful.
I am using an Android phone and using Internet directly from sim card ( no wifi)
Is there any android application installed on my phone can have access to my device’s Mac address ?
Programs can access your MAC address, although as the article states, they can’t use it to trace you.
someone is using my mac address on my apple mac air book
how do I change my mac address is it possible? If I reset my computer to factory default will that change the mac address. It is someone I know who lives rather close to me who is manually connecting my computer via an apple airport tower and some how remotely connecting my computer, I find my bluetooth setting turned on sometimes, I have tried everything I have firevalult on encryption on. Im about to buy another computer.
It shouldm’t be possible for someone to use your MAC address without actually using your computer – it’s assigned TO THE COMPUTER. So I’d have to know why you think someone is using it.
Can the MAC Address be traced by a purchase. Like do retailers keep records of who purchased the device with that specific Mac address? I know that the first 6 characters are linked to a manufacturer, but can the entire MAC Address be traced to the original buyer, maybe if they bought tge item by credit card or other payment method?
Retailers wouldn’t generally have access to a MAC address unless they opened the box and turned on the machine. It’s not impossible, but extremely unlikely. But even if they did have your MAC address, they couldn’t do anything with it. If you’re worried, don’t buy a computer whose box has been opened.
Possible, I suppose, but highly unlikely. And also something that might vary from one retailer to another.
if you have an idea were your laptop is just use airodump-ng aka you live in a small town drive around with it running watch for your mac. No one that steals a laptop is going to change the wireless card aka the mac addy. and a website can record the mac addy btw. so this art is rubbish. google can prolly tell you right were it is 🙂
It’s like looking for a needle in a haystack. My bicycle was stolen last week, and I think it would be a waste of time driving around looking for it even though it would be much easier than driving around stopping at every house looking for a MAC address.
We cannot help. A MAC ID will also not help find it. (Though it may help confirm that a laptop once found is the one you’re looking for.)
Ok, so if I understand you correctly, MAC for tracking is a non issue.
What if the device broadcasts or searches for a firmware update?
Is this not MAC specific and directed only back to the requestor device?
Nope. First, there’s no standard for this type of broadcast/search. Second, the device would be looking for updates based on its model number, not it’s mac address.
Check the “OSI layer” on Google. That’s the way it works in deep. When you talk to Google you talk to the to the server going thrue each layer ip , tcp, MAC, physical machine,…. We can say that each ip is Attached to a MAC address
Please excuse my ignorance in the matter.
@ Leo Thank you for your prompt reply.
I do not know what information is leaked/lost in the event of a wireless network attack, including IPs, the mac addresses(hence my query) and passwords and private information, and what the person doing it is after.
I/My PC was connected through a wireless extender NETGEAR WN3000rpv3, to a d-link router D-Link DIR-605L which was connected to the ISPs modem/router, a Beetel one.
I reside in South Asia.
All my e-mails were being uploaded. The browser kept saying uploading in the bottom task bar everytime I used certain sites, including my private hotmail. Private information was being stolen.
Pressing the reset button on the router did not restore administrator control. After the ten second reset time, and the initial setup, remote administration is obviously off by default, but the panel could be accessed wirelessly from any pc through the wireless/antennas.
Through this reset setup as well the router acted weirdly/abnormally. It would go offline for minutes, something like two minutes, even though connected to it through a LAN cable, during this procedure.
10 seconds was the reset time, blinking LED and about 3 seconds before the setup screen to appear etc.
Somebody had set up the wireless router for us.
I had no idea that people would/could crack passwords with a click of a mouse button, for example. I then learned about other devious inventions.
My machine/PC was connected to that home wireless network through an extender.
Other family members PCs and devices are connected to the wireless setup/network.
Somebody had set up the wireless router for us.
@ Mark Jacobs Thank you for your prompt reply. That helps greatly.
Thank you for your article, the diagrammatic representation above from computer A to Router to Server D helps clear up/elucidate the information in the article.
I’m closing comments on this article because the questions being asked are answered in the article.
I don’t know how to say this any more clearly: Read The Article. If you still have a question after carefully reading the article, you can use the “Ask A Question” page (its linked from the menu at the top of every page).