multi-factor authentication
Two-Factor Authentication: It’s Not as Complicated as You Think
There are some persistent myths about two-factor authentication that stop people from adopting it. I’ll clear them up so you can use this simple yet powerful security feature with confidence.
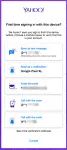
I Lost My Two-Factor Authentication (2FA) Device. How Do I Sign In?
Fear of second-factor loss prevents some people from using two-factor authentication. There’s no need to fear that scenario.
Why ANY Two-Factor Is Better than No Two-Factor
Headlines are proclaiming that two-factor authentication has been hacked. That in no way means you shouldn’t use it. Your account is still much safer with two-factor enabled.
A Lost-Second-Factor Tale of Woe and How to Avoid Your Own
A tech journalist lost his phone and encountered issues recovering a two-factor-protected account. We can all learn from his experience.
I Lost My Phone With My Second Factor for Authentication. How Do I Recover?
My phoned died, and with it, all the two-factor authentication methods I’d used it for. Here’s how I recovered.
Is Passwordless Authentication Safe?
Passwordless authentication removes the need for a password and replaces it with something else. But can that be secure?
The Easy-to-Avoid Two-Factor Loss Risk
Two-factor authentication is an important tool to keep accounts secure, but prepare for losing the second factor so you don’t lose your account.
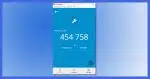
How Two-Factor Authentication Works
Two-factor authentication is a great way to keep your accounts secure from hackers — even those who manage to get your password.
What If I Lose My Second Factor?
When you lose your second factor, there are two things to be concerned about: getting into your own account — for which you should be prepared — and someone else having access to your second factor — which isn’t as scary as it sounds.
What Should I Do When My Information Is Involved in a Breach?
If your account is ever part of a breach, secure it to avoid further risk.
Five Steps to Better Security Working from Home
Security threats for people working from home are increasing. I’ll review steps you need to take to keep yourself, your company, and your job safe.
Setting Up Two-Factor Authentication — Ask Leo! Live
Two-factor authentication is perhaps the most important, if not most recommended, additional security steps you can take for your online accounts. I walk through two-factor using a Microsoft account.
Don’t Lose Your Phone: Here’s What Can Happen (and How to Prepare)
Given how much we’ve come to rely on them, are you prepared to lose your mobile device?