Longer.

For a long time, the common thinking was that the best, most practical passwords consisted of a random combination of upper and lower-case letters, numbers, and a special character or two. If so composed, password length needed to be only eight characters.
Randomness remains important, but as it turns out, size matters more. Much more.

Password length
Longer is better. Traditional eight-character passwords are now easily compromised. A password should be 12 characters at a minimum — ideally 16 or more. Using a multi-word passphrase makes even longer passwords possible and easy to remember.
Large-scale account hacks
When you hear about large numbers of accounts being stolen by a hack at some service provider, you’re naturally concerned the hacker might now have access to your account names and passwords. If the service stored your actual passwords, that could indeed be the case. (If a service is storing your actual passwords,1 they don’t understand security or have made some horrifically bad decisions.)
In fact, most services store an encrypted (technically, a “hashed”) form of your password. For example, if my password were “password” (and that’s a very poor password, of course), then a service might store “5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8” as the hash value that corresponds to that password.2
What that means is that hackers do not get a list of usernames and passwords. They get a list of usernames and password hashes.
And what’s great about hashes is that you can calculate a hash from a password, but you cannot calculate the password from the hash.
As a result, one would think that by being hashed it’d be pretty unhackable, right?
Sadly, not so much.
Help keep it going by becoming a Patron.
Dictionary attacks
The most common type of password attack is simply a high-speed guessing game. This doesn’t work on an actual log-in page; they’re slow and deny further access after too many failed attempts. But this technique works wonderfully if the hacker has the entire database of account and password hashes sitting on his computer.
These attacks start with an exhaustive list of possible words and known passwords (including names, profanities, acronyms, as well as lists of passwords discovered in previous breaches) and perhaps a few rules to try interesting and common ways that people obfuscate words. They calculate the hash of each guess, and if it matches what was found in the database of account information they stole, they’ve figured out the password for that account.
It’s easy for hackers to make an amazing number of guesses in a short amount of time.
That’s why you’re not using a short password or common obfuscations, right?
That’s why a password created from a totally random combination of characters is best. It forces hackers to move on to a true brute force attack of every possible combination to gain access.
Brute force attacks
Computers are fast. In fact, the computer on your desk is so fast that its ability to do simple operations is measured in terms of billions of operations per second.
Creating a password hash is not a simple operation, on purpose. However, it’s still something that can be done very quickly on most machines today. Spread the work over a number of machines — perhaps a botnet — and the amount of processing power that can be thrown at password-cracking is amazing.
The net impact is, it’s now feasible to calculate the encrypted hash values for all possible eight-character passwords comprised of upper and lowercase alphabetic characters and digits.
Sixty-two possible characters (26 lowercase, 26 uppercase, 10 digits) in each of the eight positions gives us 221,919,451,578,090,3 or over 221 trillion combinations.4
It doesn’t matter what your password is; if it’s eight characters and constructed using upper and lowercase letters and numbers, the hackers now have it — even if it was well hashed by the service they stole it from.
Why 12 is better and 16 better still
As we’ve seen, eight-character passwords give you over 221 trillion combinations, which can be guessed in an offline brute-force attack in hours.
Twelve characters gives you over three sextillion (3,279,156,381,453,603,096,810). The offline brute-force guessing time in this case would be measured in centuries.
Sixteen takes the calculation off the chart.
That’s why 16 is better than 12, and both are better than eight.
What about special characters?
I left out special characters.
Let’s say the system you’re using allows you to use any of 10 different “special characters” in addition to A-Z, a-z, and 0-9. Now, instead of 62 characters, we have 72 possibilities per position.
That takes us to 700 trillion possibilities for an eight character password.
Compared to sticking with the original 62 letters and numbers, adding only a single “normal” character makes a nine-character password significantly more secure.
That takes us to over 13 quadrillion possibilities.
Yes, adding and using special characters makes your password better, but significantly better yet is to add one more character.
Or two. Or six.
Long passwords are good, passphrases are better
The difference is really a semantic one, but in general:
- A password is a random string of characters.
- A passphrase is a longer string of words.
Why passphrase? Because they’re easier to remember, so it’s easier to make long ones — and as we saw, password length is the single easiest way to increase the security of a password.
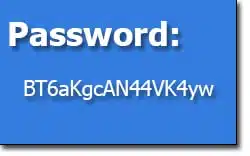
“BT6aKgcAN44VK4yw” is a very nice, secure 16-character password that’s difficult to remember. In fact, about the only way to use this is with password manager software that remembers it for you.

The biggest problem with passphrases? Many services that use passwords don’t allow spaces or such lengthy passwords.
Shouldn’t services fix this and do better?
Absolutely, they should. And many do.
As I’ve stated above, passwords shouldn’t be kept in plain text anywhere by the service at all, yet some do.
There are techniques that make brute-force attacks significantly harder, yet many use techniques that are easier than the example above.
There are services that do a great job of keeping your information secure. There are also services that don’t. The problem is, you really can’t be certain which is which.
To be safe, you have to act like they’re all at risk.
The bottom line
The bottom line for staying safe is simply this:
- Don’t trust that the service you’re using is handling passwords properly. While many do, it’s become painfully clear that many do not, and you won’t know which kind you’re dealing with until it’s too late.
- Use longer passwords: 12 characters minimum and 16 if at all possible.
- Use even longer passphrases where they’re supported or where information is particularly sensitive.
- Use a different password for each different site login you have. That way, a password compromised on one service won’t give hackers access to everything else.
Even the best eight-character passwords should no longer be considered secure. Twelve is “good enough for now”, but consider moving to 16 for the long run.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
Footnotes & References
1: If they can respond to an “I forgot my password” request with your actual, current password, then they have stored your password. This is bad. Best practice is to reset it to something new, either via a reset link or by emailing a new password to you exactly once, after which the service no longer has it.
2: For the curious, I’m using an un-salted sha256 as the hashing function here. That’s technically better than the commonly-used md5 or sha1.
3: OK, OK. Technically, the number is actually 221,919,451,578,090 + 3,579,345,993,194 + 57,731,386,986 + 931,151,402 + 15,018,570 + 242,234 + 3,844 + 62. Then we also add in the possibilities of seven-character passwords, six, five, four, and so on. I’m not doing the math. It’s around 225 trillion.
4: Many of the numbers and attack estimates here come from or are based on GRC.com’s excellent Password Haystack page. Included there are links to an excellent Security Now! podcast segment discussing password length and how length really does matter.
5: Particularly if you’re a Game of Thrones fan. And yes, I know that John Snow is actually Jon Snow. That’s another level of handy yet easy-to-remember obfuscation.





I don’t mind any recommendations on passwords…what I detest is these sites FORCING you to conform to their password rules…those of us who aren’t overly concerned about getting hacked and have been around awhile often prefer an old password we came up with years ago that may be 4 or 6 characters in length…it’s very aggravating to have sites NOT ALLOW YOU to use it
14-Jun-2011
To those who want to hang on to their favourite passwords add symbols on ends or middle
Actually, any password less than 14 characters is easily hackable. 14 characters is the old NTLM limit and there are many pre-hashed disctionary files out there. Personally I use 16 characters – at least 2 upper case, at least 2 lower case, at lease 2 numbers, at lease 2 special characters. A product such as L0ftCrack cannot crack those even when it is the only password in the Windows system and running continuously on a multi-core server !
You wrote:-
> most services will store an encrypted
> (technically, a “hashed”) form of your
> password
“encrypted” sounds more “technical” than “hashed” to me – but what sort of encryption is it, that turns an 8-character password into a 64-character one ?
And is it 64 even for a 12-character one ?
14-Jun-2011
Wouldn’t just 12 alpha characters all lower or all upper work? Since the person hacking doesn’t know that there aren’t numbers or special characters, the possibility of having them would make them still have to check.
14-Jun-2011
12 is the probably less than the bare minimum now. 12 with uppercase, lowercase, numbers and special characters might be OK, but not for long. I wouldn’t trust 12 characters all alpha. I see 20 characters all alpha long enough and at the same time easier to type than 12 characters with uppercase, numbers, and special characters, especially on a phone. TheQuickBrownForksJumpedOverTheLazySpoon is 40 characters and obfuscated enough to foil any brute force or Rainbow Table attack.
I use 14-18 character passwords.
@Robin Clay (and Leo’s response#
Hackers don’t have to check for all 4 groups of characters #upper, lower, numbers, specials)…if they’re approach to hacking is to ONLY use lower case letters during their crack attempts, then a password of “123” is far more secure to that particular hack attempt than a password of “lowercasepass”. Hopefully that perspective discourages you from only using one of the four available groups. IMHO.
…in response to my previous post…
I notice that sometimes during the preview of a post, certain symbols don’t appear correctly, like paranthesis and apostrophes. Nevertheless, in the past I’d click the POST button after previewing and they’d post just fine. My last post however still has some “pound” signs instead of “paranthesis”….just FLI (for Leo’s information) 😛
Wow. Thanx. I’ve made a couple of wrong assumptions. Now, even before finishing this news letter, I’m going to go and change the password on my Vet Health page. Again, Thanx.
Many websites lock you out after 3 attempts, so how can a brute force attack work under those conditions?
17-Jun-2011
Regarding Leo’s reply – If the password cracking is performed offline how does the cracker know the crack was successful and that they have decoded the password and not some other gibberish? I guess I don’t really understand how password cracking works. Isn’t it necessary to actually try the ‘solution’ against the relevant site? Thanks
My password is [15] letters long and i’ took my password from the Holy bible
Unless you changed some things a Bible verse can be easy to crack. So many people use Bible verses that hackers sometimes include the Bible and Shakespeare as their hacking dictionaries.
@Dan Klein
In the article, Leo’s suggesting that many of these types of attacks (if not all) are done “offline”. The hacker get his hands on the data and then goes to work with it in a private (or controlled) setting.
That being said, I can assure you that there are ways for hackers to work online too. Before we purchased a robust firewall for our business network, as the IT Manager I witnessed at least one or two attempts per month on our network. In about 2 or 3 minutes time, the hacker was able to produce thousands of attempts at username/password combos. I’m guessing this is less preferred because one thousand attempts a minute is a lot to you and me, but compared to the numbers Leo explains in the article, it would take lifetimes to crack even a moderately secure password. Like you suggest Dan, they should be getting locked out because I do if I fail 5 times. However, on less secure site (like ours was before a good firewall was implemented) they have methods that allow them to go “underneath” the interface that checks their attempts.
I had a good relatively long (can’t say exactly how long for security reasons) all letter password that I began to feel maybe should be upgraded so I added a friend’s old phone number and some punctuation. Very easy to remember and looooooooonnnnnngggggggg. For the guy who uses the Bible Password. Could be crackable. Add a phone number or something easy to remember.
Isn’t it always the simple things that get overlooked and yet can be the root of so many problems if not properly implemented? Very thought-provoking – yet easy to comprehend article, Leo. Many thanks for these pearls (that are hopefully not before swine and we will all act accordingly). Keep up the good work.. 🙂
Here is an article that suggests simple three word phrases may be powerful passwords – the words are separated by spaces.
http://www.baekdal.com/tips/password-security-usability
17-Jun-2011
Quote: “•Use a different password for each different site login you have. That way a password compromised on one service won’t give hackers access to everything else.”
I think that is completely unreasonable. A different pw for “every site”? In my case, that’s almost a 100 different pw’s. Not very practical
@Robertprice
Pwd for every site is very possible & practical. And simple 🙂 Not just sites even. You can create Unique pass for every account. That’s what I do. and this is how I do it!!
CREATE YOUR OWN ALGORITHM (consider my algorithm 3 years ago)
Step (1)
Take the last 3 characters of the site name in reverse order & Capitalize them. Do not add the extension. By extension I mean something like .gh, .com,.africa, .us, .net, .org, .whatever)
Something like this:
The last 3 characters of:
a) http://www.askleo.com = leo The reverse order is oel. Capitalize to get OEL
b) http://www.WebExtremist.com = ist The reverse order is tsi. Capitalize to get TSI
c) http://www.gmail.com = ail The reverse order is lia. Capitalize to get LIA
d) http://www.hotmail.com = ail The reverse order is lia. Capitalize to get LIA
Step (2)
Take the first 3 characters of the site name.
The first 3 characters of:
a) http://www.askleo.com = ask
b) http://www.webextremist.com = web
c) http://www.gmail.com = gma
d) http://www.hotmail.com = hot
Point (3)
Concatenate Point (1) and Point (2) in the order of numbering.
Thus,
a) OEL and ask = OEL&ask
b) TSI and web = TSI&web
c) LIA and gma = LIA&gma
d) LIA and hot = LIA&hot
Point (4)
Count the length of the characters in the site name. Prefix the length with the character “@”. And put in braces. Add result to Point (3) above
Thus,
a) Length of http://www.askleo.com = 14 Characters. When in bracket (14) When Prefix with @ gives (@14)
b) Length of http://www.webextremist.com = 20 Characters. When in bracket (20) When Prefix with @ gives (@20)
c) Length of http://www.gmail.com = 13 Characters. When in Bracket (13) When Prefix with @ gives (@13)
d) length of http://www.hotmail.com = 15 Characters. When in bracket (15) When Prefix with @ gives (@15)
Weldone! Your final password is therefore
a) = OEL&ask(@14) (When you want to login to askleo.com)
b) = TSI&web(@20) (When you want to login to webextremist.com)
c) = LIA&gma(@13) (When you want to login to gmail.com)
d) = LIA&hot(@15) (When you want to login to hotmail.com)
Though not strong algorithm, this should give u fair idea. You can generate your own which will guarantee you 500+ unique pass. The good news here
is, you don’t have to remember even a single password. You only remember them when you visit the site
My current Algo gives me 21 length character pass. Very complex to computer but simple for human mind to remember
Felt happy reading your comments regarding the algorithm based password. I totally agree and that’s exactly what I do too : )
One thing however that I realized is that my passwords used to be to only 8-10 characters. I should now increase the string length to 12 or more characters.
Cheers!
@robertprice
That’s where password managers such as LasPass, Bit Warden, and KeePass come in. You have to remember only one password and the program remembers the rest for you. Warning keep several backups of your password file.
I’m not saying it’s necessary to have a different password for every login as that is still much discussed point, I’m just saying how it can be done. I, for example, have one weak password for forum log-ins where I don’t care if it gets hacked. For important things like my emails and my banks, they all have a similar but unique password ie. the same password but with a unique identifier for each account.
For RobertPrice:
Dude! That’s what programs like Roboform or (my personal favorite) KeePass Password Safe are for! Sheesh!
For Leo:
Twelve is good — but I understand that 16 should be the minimum, due to rainbow tables.
I’m a little surprised that you didn’t mention rainbow tables in your article.
Rainbow tables essentially are databases in which hackers have computed the all hashes for brute-force attacks on all passwords up to a given length in advance. They make the breaking of passwords both much easier, and much faster. The book “Perfect Passwords: Selection, Protection, Authentication” by Mark Burnett ($18.96)” recommends a 16-character minimum length password for this reason, but then, it was written in 2005 — so I would expect by now that the standard rainbow tables have been rather expanded by now!!! I would very seriously recommend a twenty-character password by now.
Really, folks: There is NO such thing as “a password too long” — unless it’s so long that it’s rejected by the system you’re feeding it to.
17-Jun-2011
Do you know that Google started to “fiddle” with Quantum computers? And do you know that a Quantum computer could (theoretically) decipher any passwords that a user like me could create (12-16 or 20 letters, numbers or symbols) in a “few minutes!” You read that correctly…. in a few minuscule minutes, a quantum computer will decipher your “tough” passwords.
As regular computer users, we’re not there yet but large corporations (and countries alike), are spending billions to create those little nifty toys! The purpose, ask Google: Data gathering, and less obviously, to be able to “control” anyone and anything on this planet.
Yope! That’s where we are heading…
EDIT: I noticed that most comments were written 8-9 years ago. Then, the word “quantum computer” was not even in our vocabulary, or it was a science-fiction thing, that could be 100 years down the road. Not so fast! They are here, now, and Google has already started to work with them… again, only to “control” the data… Did I say “only the data”? And who’s behind that data? A human of course!
Good article Leo.
It Is worth noting that, in some unix environments (eg AIX) you can set a long password but the system will only evaluate the first eight characters (the rest are ignored).
17-Jun-2011
so do password crackers waste their time trying 4 character passwords?…if not, it seems a shorter password may be more secure…it’s all really about what their algorithms do, isn’t it?
Hey Leo, great article!
I totally agree with two main points that Leo has made:
1. The password has to be long — the longer, the better. Personally, I use at least a minimum of 16 characters, but in most cases, I use more, even 22 or 24 characters. Every online site is different in what they allow. For example, the last that I knew, Hotmail only allows a 16-character maximum, but other websites allow longer, which in that case, I will always generate passcodes that to the maximal length a website will allow. I suggest contacting the website or reading their help section to find out what the maximal passcode they will allow.
Also, like Leo suggested, I would make all passcodes as a random combination of majuscule and miniscule letters as well as numbers. I admit that I tend to shy away from special characters, as some websites do not seem to understand special characters. There are so many special characters too, even way more than what is on an ordinary qwerty keyboard. And, if we start to discuss non-standard and non-Latin letters, then there are even more. Seemingly, many servers and websites do not understand those characters either.
For the benefit of persons reading this article, I would like to mention two great passcode generators that I like to use:
Chaos Generator by SafeSoft:
http://safechaos.com/cg.htm
PassGEN by Abhishek:
http://myfreewares.weebly.com/passgen.html
Both of these softwares are similar in appearance and how they work. And, they are both easy to use. They can generate passwords of any length and as many at one time as you would like. I normally like to produce a list of over a thousand passcodes at a time, then save them to a notepad and pick out ones that I want to use. Also, I will mention that I use Zone Alarm firewall, and neither of these two softwares have ever suddenly out-of-the-blue “phoned home”, otherwise, ZA would have alerted me.
I have developed my own manual password management system, as I am not willing to use password managers that are supposedly freeware. I am not willing to wake up one day to find software on my computer that was once freeware to now be a paid version, thereby leaving me locked out of my passcodes. I use a program called Mince, in order to manually archive and save my passcodes onto notepads. It can be found at:
http://bluefive.pair.com/mince.htm
I admit that my methods of online security are somewhat intensive and laborious, but me and my computers are worth that effort I put into online security.
Also, I recommend changing your account passcodes at least monthly or quarterly too. As far as robertprice’s comments about having too many different passcodes as being unreasonable. Perhaps you are on too many websites in the first place. Good online security and living a virtual life are nearly incompatible. And, this brings me to the second point that I agree with Leo on…
2. Use a different passcode for each online account you have. Why is that? For example, websites such as Plenty of Fish are easily hacked into. Once a hacker is into someone’s account, they can easily find your email address in your account information section. And, if your email passcode is the same as your PoF account passcode, then wal-lah: the hacker also has your email passcode too.
This is especially problematic nowadays as there is how a great deal of spam and phish is being sent out via normal email. Spammers and phishers like to use “established email accounts” nowadays for their well-developed contact list. Unsuspecting victims (the email recipients) imagine that they got an email from someone they know and trust, only to find out cold, hard reality once they mistakenly click a link or open an email attachment imagining that they received the email from someone they trusted.
If an email account had been legitimate for years but suddenly is hijacked, then those spammers are harder to be detected by ordinary spam filters in the email industry. Email account hijacking nowadays is a dime a dozen. And sadly, many people are too irresponsible to let the people on their contact list to know their account was hijacked in order to ignore any emails from that account.
So, I totally reaffirm Leo’s idea of keeping different passcodes for different accounts. Even if you have online throwaway accounts, if they are linked in any way to some other account of yours that you value, then that is a potential security breach.
I personally use Lavabit email accounts, as in the past two years that I have had my email with them, I have never once received a spam or phishing email. Seemingly, they have a bullet-proof email account system. I have not found a better email carrier on the internet yet. However, I still change my passcodes monthly or quarterly, depending on how I use the account.
Also, I highly suggest keeping a good antivirus, firewall and several anti-spyware engines on your computer too. Getting a trojan or keylogger in your computer can be very devastating to your computer and personal security too. I always say that old-fashioned viruses were only meant to wreck your computer. But nowadays, adware and spyware are meant to wreck your life!
I feel it is a matter of self-respect and personal responsibility to keep my computers clean and fit for duty. Many people do not, so you cannot rely on your online virtual friends to not infect your computer with theirs. I feel that sharing computers nowadays is like someone who is sharing their toothbrush and underware with someone else. As far as I am concerned, computers are not toys whatsoever. As Americans, it is our second amendment right and responsibility to protect ourselves. Often times, using my brain and some common sense are my best line of defense, especially in the cyber world!
“I still change my passcodes monthly or quarterly”
Changing a already long/secure password is a waste of time unless one does it as a precaution if a site was breached. but just changing it for the sake of changing it is pretty much pointless as it does not really give one a real boost in security and just puts unnecessary work on yourself.
and if your that worried about getting a virus and the like, especially if one has a spare computer, I suggest putting Linux on it as just using that reduces ones risks of getting hit with viruses and the like quite a bit since that stuff tends to largely target Windows based computers since it’s about 88% of the market share where as Linux is only about 2% tops. even if one wants to stay on Windows… all one really has to do is keep their Windows OS and general programs like their web browser up to date (don’t use too many extensions and be careful on what extension you use and try not to have Flash or Java installed in your browser) and be careful on what one allows to install on their computer and your chances of being infected are slim. I am not a fan of loading ones computer down with multiple scanners for random junk as you should not even need it if your careful on what you do online as the basic anti-virus Microsoft gives you with Windows 10 should be ‘good enough’. I would even avoid smart phones for doing anything important online since many don’t even get proper security patches in a timely manner, if at all.
I realize I am replying to a post nearly 9 years ago now but I figured I would make a post for those who stumble into this article.
Ik see KeePass Password Safe recommended. How can I be sure this is a safe program and not someone who tries to hack all my passwords?
I don’t recall if it was a link to this article or some other place. But that article said that phrases with spaces make cracking even more difficult.
For example:
my name is bob
with spaces, is even harder to crack than inserting symbols between the words. Opinion?
29-Jun-2011
Many sites don’t allow spaces in passwords or phrases, but in most cases is a valid character and it looks just like a space.
Well, that didn’t work. It edited my comment. I tried to say that the key combination of the alt key and the number 255 creates a character that looks like a space but is not considered to be a space.
I see people are bringing up whether one can use spaces in between each word they use but a simple work around to that is to use something on the keyboard instead. so for example, instead of… ‘my password is super secure’, change it to ‘my_password_is_super_secure’ or ‘my-password-is-super-secure’ or ‘my.password.is.super.secure’ etc. this way you never even attempt to use the space bar and don’t have to worry about whether a site accepts it or not as your brain will just get into the habit of using a random key on the keyboard to fill in where the space bar would normally be used between the phrase you want to it.
That’s also useful because many sites require a “special character” which is usually anything except a letter or a number and that takes care of that. Don’t forget to use a unique password on every site, for example, ‘my_password_is_super_secure_facebook’ ‘my_password_is_super_secure_gmail’.
Good advice. My own passwords are over 22 letters long [ calculate that time to crack hee hee ] and I always use the complete phrase of something I NEVER forget. That favorite opening line from your favorite book EG ‘itwasthebestoftimesandtheworstoftimes’
Just an example. Notice no spaces and no funny characters – not needed because a cracker is using an engine that must go through upper AND lower case as well as numbers 1 to 0 AND funny characters like = or *. The above example is 37 letters long !!! No way hose is a cracker going to stumble on that password this side of eternity.
Looks as though my obsession with long and crazy passwords has already paid off. My “standard” password is 15 characters long and is a little modified for each site; it contains lower and upper case letters, numbers, and special characters. Also I have that nifty little code generator avavilable for free that works on both eBay and PayPal. How do they go about getting around that step as hackers? But my pride and joy password is 25 characters with 16 special characters. No, wait, for Word documents, I use a 33 character password with 24 special characters. Yes, I am crazy.
Thank you. I thought my 8 letters with numbers was safe – I’ll be changing most of my passwords now.
Always having a complicated password for every different online account is almost impossible. Just in email I have several accounts that I use regularly and then you add in all the other accounts: online-banking, credit cards, social media, etc… and then to have different passwords for all of them is a pain, but necessary. However one of the first things I look for when setting up an account is if they offer 2FA (two-factor authentication) where I can telesign into my account. This gives me the confidence that my account won’t get hacked and my personal information isn’t vulnerable. Personally I think if you are just relying on your passwords (complicated or not) to protect your info you will pay the price sooner or later.
Like already mentioned, a password manager is how you can use unique/randomly generated passwords for each website as all you got to do is remember the master password to the password managers database it creates and it gives you instant access to all of the passwords you randomly generated for your random websites. and to state the obvious… make backup copies of the password managers database and store them in a secure location. so this way if your primary device/computer happened to instantly fail, you will still be able to restore that password database on another device. because losing that would be a huge pain in the neck.
also, for sites that have questions in case you forget your password you should treat those as secondary passwords. because for example even if you had a really secure main password for your username/password login info, but if you got easy to answer security questions to reset the password, it would be a potentially easy way for someone to get around you super secure password. so just generate long/random passwords even for those security questions. so say one is ‘What’s the name of your first pet?’ don’t answer it honestly and just use a password manager to generate a long password for the answer to that. which will prevent any shady person from bypassing your secure setup.
In the above article you have said and I quote “62 possible characters (26 lower case, 26 upper case, 10 digits), in each of the eight positions gives us 221,919,451,578,0902, or over 221 trillion, combinations.3” Looking at mathematically, if you have more characters, the resulting number will be still larger and more difficult to hack or conversely you can get away with shorter password. Please let me know how through Email I can send my details of the solution for finding out from expert like you if it is feasible or not.
Thanks.
That’s Jon Snow, but I’m sure you did that to obfuscate the password even more 🙂
There is one way to test if the website is handling passwords well. Submit a lost password request. If they send you your password, as Leo mentioned in the first footnote, you know they’re handling it wrong. However, if they send you a password reset link, you still can’t be 100% sure they are doing it right, but at least you can determine the really bad ones.
Some remarks:
1. Dictionary attacks are the reason why general-purpose hash functions are not very good for hashing passwords. Instead of SHA-256, you might want to use something really slow, like bcrypt.
2. If a service doesn’t accept spaces, there’s a trivial fix: instead of spaces, use some other characters, like hyphens. This might even be slightly better because the space key has a distinctive sound, so someone listening to you typing your password could, theoretically, take note of that.
3. I’m surprised you didn’t mention password managers at all. They are pretty much the only way to have a unique password for every website.
4. An excellent tool for generating secure yet memorable passphrases is Diceware (http://diceware.com). Basically, you have a word list of 7,776 short words, and you pick each word by rolling five dice. This way, your passphrase is truly random, so its strength is easier to determine than if you choose a slightly obfuscated, but still sensible phrase from a book or a movie or whatever.
Leo has a lot of articles on LastPass – a great password manager. Here’s one: https://askleo.com/lastpass_securely_keep_track_of_multiple_passwords_on_multiple_devices/
2. Or just leave out the spaces entirely. That’s what I do.
3. Leo did mention password managers:
““BT6aKgcAN44VK4yw” is a very nice, 16 character long and secure password that’s difficult to remember. In fact the only way to use this is with a password manager of some sort that remembers it for you.”
I would like to use passwords of the type Mark Jacobs depicts. Trouble is, I don’t trust Password Managers!
I use LastPass and feel safe using it. I have a long random string of letters and numbers that I’ve memorized as its password.
https://askleo.com/are_password_managers_safe/
https://askleo.com/is-lastpass-still-secure/
If you don’t trust a password manager storing your passwords on the internet, then you can use a password manager like KeePass which stores the passwords only on your machine and not on the internet.
http://keepass.info/index.html
Password managers are fine. just use one that only stores stuff locally as I tend not to trust ones that upload ones database online as it seems like a potential security risk.
I trust LastPass encryption to keep my passwords safe on the Internet.
Done correctly (as LastPass does) it’s not any additional risk.
@Mark Jacobs (Team Leo)…
Thanks for the info. I use Password Safe (pwsafe dot org) which is ‘Designed by renowned security technologist Bruce Schneier’ as it says on their website for storing my passwords as I have used that for around the last 13-15 years and never had a problem with it and it only stores the password database locally on ones hard drive and I just make multiple backup copies of the database to ensure I don’t lose it. it works on Windows/Linux and I think there is even one for Android to (although I am not a fan of smart phones holding sensitive info as they just seem higher risk in general vs a desktop/laptop computer). although I have been using Linux (desktop/laptop) exclusively since last year to date and the database I created on Windows works fine on the Linux version of Password Safe.
I would say my master password to Password Safe is good but probably not great which is another reason I would rather avoid storing it online in case it were to ever fall into the wrong hands I don’t have to worry about it potentially being cracked. but I guess if one wanted to store the database online they could maybe use some other software that can encrypt the database file with a really long/randomly generated password. so if the database file did fall into the wrong hands they would have to get around the encrypted file first before they could even attempt to crack the password managers database file. but I probably ain’t going to take the chance, especially not until I improve the master password on Password Safe’s database. but I guess if one is even more paranoid they could do it one addition time, so one would have to decrypt one file, then another in order to get access to the general password managers database file and then they would have to crack that before getting access to your login/password info. because with that setup it seems unlikely one would be able to get through all three of them when the first two will have a different a 64 character password on it.
@Leo Notenboom
Unless I am missing something, I don’t see how ones risk would not increase, at least a little, given if your password database is stored online and the place gets hacked, one could potentially get a hold of ones password database file where as if it’s only on ones computer then it makes it impossible to leak short of ones computer being compromised. basically one has control over their own computer where as with ones database being uploaded online we have no idea what’s being done with. so there surely must be at least some increased risk, right?
Of course, there’s a tiny risk of having your password vault stored on the Internet. That risk is decreased by a factor of about 100 (typeable ASCII characters) for every character added to your password. LastPass doesn’t store a hash of your making it impossible to use rainbow tables to crack the vault. I’m not suggesting you switch from Password Safe as, from everything I’ve read, it’s a great program. I’m mentioning this for anyone else who is making a decision as to which password manager to use. I have 5 computers, 2 tablets and a phone and LastPass keeps my passwords synchronized on all of them.
In LastPass’s case the database is well encrypted, and LastPass does not have the master password. So if they were hacked (which they have never been), all the attacker would get is an encrypted blob of random data. No practical risk to me if that blob happens to be mine. (Yes, technically, there’s a slight increased risk, but it’s insignificant, IMO.)
@Mark Jacobs (Team Leo) / Leo Notenboom…
I get the gist of what your saying in that the increased risk (of storing ones password database online), while technically there, is low enough not to concern you two (since you have confidence in LastPass security practices) and LastPass gives the average user a solid increase in convenience for only a small, if not negligible, risk of storing ones password database online.
Password Safe just takes the conservative approach and assumes the user will take precautions not to lose that password database file. but since many people slack off on backing up data in general I can see how something like LastPass would be the overall safer choice for these kinds of people since it backs up ones password database online, so if there computer dies out of no where, they can just restore everything from the LastPass online backup once they get a replacement computer.
thanks for your time.
Great advice as always ……..really appreciated. My latest way of dealing with passwords is – as you suggest – to create a pass-phrase. To further secure this, I have been creating a long phrase but spelling the main words phonetically – my own version so to speak. To finish off I put numerals. As commented, I have hit the problem of being forced not to have spaces and being limited to number of characters but can easily get around this.
There’s another extremely important element to all of this, and that’s your ability to remember the password without writing it down!!
Too often I hear of people who tell me they have “impressive” 18 character long passwords, then I ask them how they remember them, and they say they don’t, they simply write they down and stick them to the back of their monitors!
I think that if you need to write down a password then it’s lost most of it’s benefits. It takes a fraction of a second for someone to come across this piece of paper and take a photo with a smartphone, then months later they could use the passwords and you would have no idea who was doing it.
For me the above tips are very useful, for most people a password of 10-12 characters long which is a mixture of all possible characters but also very memorable is the best solution. Additionally, as others have said, have a 4 digit part of your password and then for different sites change that.
E.g.
jOHn_2001_$AVE – for Apple
jOHn_4001_$AVE – for Microsoft
jOHn_7001_$AVE – for Google
I use a 6 digit name, 2 digit number, 3 special characters, a 6 digit name and a 2 digit number for a total of 19. Easy to remember. For other PWs I use the 4 digit of one of my aunt’s address mixed into the PW.
I use the postal addresses of my childhood school friends. So I can, for example, write down “Bradley Hughes” as my aid memoir – or even have a picture of that individual to help me remember – so the password for something may actually be “16 Acacia Avenue” (including spaces) but I have a thumbnail of Bradley Hughes referenced elsewhere to help me remember.
Oh – and by the way Bradley Hughes and 16 Acacia Avenue are fictitious – (just in case ‘the feds’ or the dark side are watching)
p
To really secure their user’s passwords/passphrases, companies should also salt their hashes — that is, they add a bit of random data to the hash. This way, the hash CAN’T match the passphrase, unless the salt is removed first! Unfortunately, not all companies salt their hashes, and you have NO way of knowing which ones do or don’t.
I also want to reiterate my recommendation for the book “Perfect Passwords,” which I mentioned in an earlier reply. Even though it is over thirteen years old, its author is so knowledgeable, and so forward-thinking, that the book easily remains relevant even to this day!
The “Perfect Passphrase” is HARD. It has eight (8) parts:
1. lowercase letters.
2. UPPERCASE LETTERS.
3. Numbers (1,2,3, etc).
4. Punctuation (.,”;:? etc).
5. Symbols (&%#@$ etc).
6. Spaces (” “).
7. Respelling (“reaspehleeng”) — NEVER use a word that can be found in a dictionary!
8. Length — at LEAST 16 characters long, and the longer, the better.
Hope this helps! 🙂
Leo, you wrote:
“If they can respond to an “I forgot my password” request with your i>actual, current password,
then they have stored your password.”
It has just occurred to me that there is a way, at least, to test this! When you first sign up for a service, DON’T enter you real password (yet). Enter a test passphrase (your chosen passphrase, minus a few characters at the end, will do for this purpose) and then “forget” it — that is, click the “I Forgot My Password!” link, and see what you get back. If you get back “test,” abandon that site immediately, and dob’t ever look back!
On the other hand, if what you get back is, “Click here to enter a new oassword
Never mind that last repky, I belatedly see that someone else made the same suggestion.
[ Hey, Leo, how about adding “Edit/Delete Post” links so we can correct our mustakes?! ]
I would if I could, but I’m afraid the software that I use doesn’t support it, except for logged in accounts, and even then possibly only for administrators.
Lei, you wrote:
“I would if I could, but I’m afraid the software that I use doesn’t support it, except for logged in accounts, and even then possibly only for administrators.”
Time to bite the bullet then, Leo, and install new & better software!
The problem is software doesn’t always do everything you’d like it to do and you have to choose the features that are most important.
These articles give advice on how to recover a Facebook account:
How Do I Recover My Facebook Log-in Password? and/or
How Do I Recover My Hacked Facebook Account
Unfortunately, if you no longer have access to the recovery email account or phone number, your account may be lost forever. It’s important to always keep these up to date on your account.
A One Step Way to Lose Your Account Forever
Leo,
I use LastPass to store and generate passwords. One thing I’ve noticed is that some web sites are still limiting which characters and how many characters can be used to generate a password. I set LastPass to generate passwords of 24 characters of all types as a default. Often when creating a new log in for a site I will get a message that my password is a) too long, with message showing the max password length, usually 8, b) can only use alpha-numeric combination with no special characters or c) can only use alpha-numeric characters with a specified list of special characters. In those cases I just max out the characters and follow their rules.
What bothers me about this is that some of these sites are government sites such as the Social Security Administration and some Defense Department sites (I’m retired military). Seems to me that in 2020, web site owners would be less restrictive on what a password should be. Minimum and maximum values of say, 10 to 30 characters of all types, should be standard practice.
At least Social Security requires two-factor authentication.
Any rules that require certain characters be included or excluded, or specify a minimum length reduce the universe of possible passwords. Hackers can easily determine these rules by looking them up on the original site. This can greatly reduce the number of passwords that must be tried to find the “hits”.
Totally agree. The issue, I think, is that so many of these agencies are running legacy systems on top of incredibly old systems (mainframes?) that would take years and million$ to replace.
Would adding a letter from a different alphabet, like the German ö instead of a regular o, help slow down hackers from getting your password?
If the password is short (and the service you’re using allows it — many will not) then maybe. But length is MUCH more important.
People can look up ‘Diceware’ which appears to be a good way to generate pass phrases that are secure and then to make it even more secure with minimal effort one could add in a word not on that list or add in a small amount of random symbols on the keyboard. it appears six words is the recommended minimum, although I figure why not go a bit longer (say seven words, if not eight words(eight should be plenty for the foreseeable future for the more paranoid types)), or add in small tweaks, to help future proof your master password which will access your password manager program as then you can just use the password managers random password generation to do the rest for websites you log into.
so instead of say, “Word1.Word2.Word3.Word4.Word5.Word6” one could do something like, “Word1.Word2.Word3@@Word4.Word5.Word6” and variations of this type of stuff. or even do a little tweak like add in another small word etc not on the list in addition to the six words the Diceware comes up with which I imagine should give one a solid boost to security for minimal effort.
when it comes to websites that use security questions for resetting a lost password… NEVER answer those honestly. so for example… ‘What’s the model of your first car?’. instead of answering honestly, you use a password manager to generate a long/random password instead (which you can store in the notes section of your password manager in relation to that specific website in case you ever need it) as then this will further harden the security of your account because without doing this it becomes to easy for someone to reset/bypass your secure password on the account.
additionally… one can get a bit more security by using different login name for different websites you use. but this is not that important, especially for the average person, so I would not worry about this. the main thing is, use a different password for each website you use.
but obviously make sure ones computer is secure (as in no viruses or malware etc) before doing all of this stuff.
one last thing, which is slightly off topic (and optional but beneficial) but still security related… for those who prefer to more thoroughly secure their Gmail account one can use a YubiKey (for a person using a standard computer with a USB port you can just buy two of the cheapest keys which are 40 dollars tops for two of them) as with those on ones Gmail email account even if someone gets a hold of your username/password, like through Phishing, they still can’t gain access to your account. it’s the most secure form of 2FA (two-factor authentication) available as it’s not been bypassed yet (and it’s been around for quite a few years now) where as a typical smart phone 2FA is not fool proof, but better than nothing. YubiKey gives one peace of mind especially given if ones Gmail email account became compromised some shady person could potentially use that to reset passwords to other accounts you might have tied to that email address and could wreak havoc on ones internet life.
regarding the YubiKey… the reason you want two of these is to help ensure you don’t get locked out of your Gmail account as you use one of them and store the other in a secure location in case your primary YubiKey gets lost or stolen as if you lose your primary key you can simply use the other to login and remove the lost key from the account and then you can simply order another YubiKey and register that to your Gmail account and you now have two YubiKey’s setup once again with one stored in a secure location while you use the other for general usage.
A reply to myself… I mentioned ‘Diceware’ which is good but I suspect something would be a bit easier then using the Diceware only and still likely pretty secure is use what they call ‘padding’. like for example… !0—_My.Password.Here_—0! ; a total of 28 characters in this example (and uses at least one capital letter, lower case letter, and one number, and one symbol).
because I read it’s a good idea to to use at least one capital letter, one lower case letter, a number, and at least one symbol as it forces someone to scan through all possible password combinations that way pretty much which should make it harder to crack vs if someone is using all lower case words. plus, that method (with the padding) I think would be easier to remember than a rather long password or passphrase paired with ones own padding will likely be easier to remember than using say 6-8 totally random words etc. also, one could even misspell a word on purpose to further mix it up if they want to like for example… instead of ‘password’ one could use ‘ppassword’ (or ‘passwordd’ / ‘passsword’)
this just gives people more options/choices on how to make a password. but I would probably suggest not to make the padding stuff too short and try to use maybe a few words in there etc. but like people always say with password in general… length seems to be the biggest factor for increasing password strength and I would definitely include the at least one lower and upper case letter, one number, one symbol in there to.
Another reply to myself… using that Diceware stuff I noticed on one site it shows a chart on how to make those really long/random passwords using real dice using pretty much all possible keys on the keyboard, which is very secure.
like to speed things up a little one needs three dice and for each roll of those three dice (read from left to right as they fall in front of you on the table) it gives you one character out of the 94 possible characters on a keyboard (assuming we do not count the ‘spacebar’). so for a 20 character password for example one would have to roll all three dice, twenty times (possibly a bit more if you end up on the blank sections since if you do it says to roll all three dice again).
basically go to the section that says, “How do I use dice to create random character strings?” to create your own passwords using real dice at this link… theworld.com/~reinhold/dicewarefaq.html ; using that, you basically reach 131.1bits of entropy at 20 characters long which is pretty much uncrackable for the foreseeable future as even going to a lesser length is still very strong when your using 94 characters in the keyboard. even at 16 characters long using 94 possible characters in the keyboard it comes out to 104.9bits of entropy.
for example… here is a 20 character password I rolled using real dice with that method I listed above… q+’?NJaly8hzNjbUTS)Z
I tend to prefer at least one upper case, lower case, number, symbol in there just to help ensure if someone is trying to brute force the password it pretty much makes them try all possible combinations basically. but when rolling say a 20 character password, as I was playing around with it using real dice, it seems to pretty much do that in general (with at least one upper/lower case letter, a number, and a symbol) even though it’s possible that won’t happen occasionally since the stuff is random after all.
but this info I posted in this particular post is for those who want more of the full-on security of randomness using dice (and are not satisfied with random password generation of password managers (which I would assume are secure enough from what the experts say)) as I would probably just opt for the usual Diceware words instead since it will be easier to type etc.
for measure… to get similar level of entropy of a 20 character password using 94 characters on keyboard to a Diceware passphrase one would have to have a 10 word Diceware passphrase which comes out to about 129.2bits of entropy. so the 10 word passphrase would only be a bit weaker than a 20 character password using 94 characters on the keyboard which is 131.1bits of entropy.
because while other people might post their own methods, which may or may not be secure enough, with this Diceware stuff I posted in my handful of posts in here, your guaranteed a minimum level of entropy as you don’t have to hope your own method is secure, but you got the assurance that it IS secure as it does not matter if a attacker knows your using Diceware, they still can’t get around it since the math around this stuff is sound.
p.s. I can calculate the entropy of this Diceware etc stuff by using the calculator on Linux Mint with it’s ‘advanced mode’ and then manually type in for example… log2(777610) *press enter* NOTE: when you type the ‘2’ after the word log you need to hold the ALT key first before pressing 2 and before pressing the ’10’ after the 7776 section you need to hold the CTRL key. but anyways… with that particular example it’s basically giving you the entropy of a 10 word Diceware passphrase (which comes out to 129.2481 which rounded off is 129.2bits of entropy). to do the same with the 20 characters of random stuff using 94 characters on the keyboard you would do this instead… log2(9420) *press enter* NOTE: when typing ‘2’ you need to hold ALT on the keyboard and for the ’20’ you need to hold CTRL. if you want to use the spacebar as part of your password you would adjust that 94 to 95 but it barely has any effect on entropy as we are talking minimal difference of 131.4bits vs 131.1bits for a 20 character password. so one barely loses anything by removing the spacebar from the equation to where it’s a non-issue as you can choose whatever you want.
or another way to put it in simple terms… one can say a 10 word Diceware passphrase is similar in security to a 20 character password using the 94 characters on the keyboard (basically everything besides the spacebar).
or another thing I could say is this… when it comes to Diceware word length that site recommends a minimum of six words and six words is 77.5bits of entropy. to get that with the random 94 characters on the keyboard one would need at least a 12 character long password which comes out to 78.7bits of entropy, which is a little stronger than the six word Diceware passphrase.
You suggested using a pass-phrase and mentioned that many sites don’t allow spaces in passwords. Is there any reason not to simply leaveoutthespacesinalongpassphrase?
Nope, that’s fine.
Add the extended ascii characters (degree, copyright, registered) which cannot be typed directly from the keyboard and double the possibilities.
OR the unicode-table (foreign characters, electronic symbols, smileys, etc) and add another 65,000 possible combinations.
I’ll let you do the math.
I have tried these with a few site passwords and some worked, but I wasn’t bored enough to do extensive testing.
…And STILL continue to recommend:
“Perfect Passwords: Selection, Protection, Authentication”
by: Mark Burnett
(As of Mon., 21-Sep-2020):
Kindle, $15.31
Paperback, $11.65
Purchase At:
https://amzn.com/1597490415
This book is already 15 years old, yet it is still the best source of information on passwords that I have ever seen.
Mr. Burnett ‘s book pretty much anticipates everything that Leo has just said in this article, confirming that, while length trumps everything, complexity helps, too.
(And the book even contains a few amusing anecdotes, to boot… like the one about his five-year-old son’s password!)boot
Get the book — you won’t regret it. 🙂
I have a way of making fairly complex passwords and easily remembering them – I randomly combine old (UK) car registration numbers (OK I have had 36 cars over the years!) add my name then year of birth – so e.g Abc123Xy05abcFred61
esy to remember just write down TR6 + Honda FRV – only you will know those reg nos.
I also have used how secure is my password site
copying that into https://howsecureismypassword.net gives a crack time of 9Quadrillion years
now I don’t know how accurate that is but it surely must be pretty secure!
a) 36 CARS! 🙂
b) I’m not sure I could remember 36 registration numbers. Sounds like a great approach if you can, though.
I am using the macrium free back-up you have previously recommended. Is this still a good option? I do a full back up each week and an incremental back-up every day. Two questions this too much and if it is how many do I retain and for how long? OK can’t count its three questions!
Passwords are I was going to say important but I think critical is far more accurate. I now use 16 random upper and lower case letters plus, at least, 4 other identifying letters and a symbol. The last 5 are just gouges to help me remember what the password is for. Have I rolled over into the realm of lost my mind or is this, at least partially, safe?
You’re all good across the board.
Macrium is still a recommendation and your strategy seems sound. I do monthly full with daily incrementals, but weekly for the full is fine.
Your passwords sound fine. 12’s the minimum I recommend these days, with 16 preferred. I happen to use 20.
Macrium Reflect Free doesn’t do incremental backups. It does differential backups which are a little different and take up more space
The following articles (below) from 2012/2013 were a big revelation to me concerning how password crackers go about their nefarious task, and scared me enough to prompt me to come up with a better, more consistent and easier to use password/password management strategy than the sporadic password creation efforts I had tried developing up to that point.
I gave up trying to consistently come up with a password for each online/offline account/login that is attempted to follow the common recommendations of the time (and still) – you know: “. . . easy to remember but hard for anyone else to guess . . .” and that use “. . . at least eight characters, use at least one upper-case, one lower-case and one symbol character . . .”.
I had/have dozens of passwords for various online (and offline logins). I quickly concluded that trying to have a unique strong password that I can remember for say, more than two or three accounts, is simply unrealistic and nuts because of my limited memory capability (i.e. the human factors/condition).
I eventually opted to use password manager, Password Safe for various reasons, one key reason being that it has the option of using a hardware key (e.g. Yubikey) as a second-factor authentication (2FA) in addition to requiring a master password to open the password vault.
Password cracking articles:
https://arstechnica.com/information-technology/2013/05/how-crackers-make-minced-meat-out-of-your-passwords/
https://arstechnica.com/information-technology/2012/08/passwords-under-assault/
https://arstechnica.com/information-technology/2012/12/25-gpu-cluster-cracks-every-standard-windows-password-in-6-hours/
Some changes to my previous post of February 25, 2020:
I’ve noticed that some websites are starting to get with the program. This morning I had to change the password at my bank and reading their requirements for a password, they have made it easier to come up with a decent password. In particular, the number of characters allowed was raised to 32 and restrictions on special characters were eased. Looked as if the bank had just implemented a new system.I use Bitwarden so maxing out the passwords is not an issue.
The U.S. Government is also tightening up and most government sites now are moving to two factor authentication. Social Security has been for some years, but the Department of Defense and IRS now require it as well.
When creating passwords for a new login or when changing an existing password, check what, if any, requirements are for passwords and then max them out.
Back in the old TRS-80 days (1977’ish), I created a demo program for my local Radio Shack store. The program simulated a slot machine. The program also had extra options accessible to the store employees (and me) by entering a password. Since the TRS-80 could recognize individual characters as they were typed on the keyboard, I set it up so that after the first 2 character were typed, it ignored accepting succeeding characters until after 5 seconds had elapsed. The characters would still appear on the screen as “X” though. Maybe the password was REQUEST. I’d type RE (pause for 5 seconds as if I was looking for the next key) then type QUEST. I noticed a customer shoulder surfing me and he tried the same password and said it didn’t work. Jokingly I said, “Did you press the keys too hard”? I showed him by pressing RE, and then paused for 5 seconds by saying, “See how lightly I’m pressing the keys”? and then finished by typing QUEST. He tried it again, but he still failed. If REQUEST was typed entirely within 5 second, the TRS-80 thought only RE was typed but it would still display “XXXXXXX” on the screen.
I later heard that customer bought a TRS-80 a few weeks later. I was told he said if the TRS-80 prevented him from accessing something he was not entitled to access, it would surely prevent his wife and kids from accessing things they shouldn’t.
Said Mark Jacobs in July 2015: “I use LastPass and feel safe using it.”
And April 2020: “I trust LastPass encryption to keep my passwords safe on the Internet.”
Said Leo (also April 2020): “Done correctly (as LastPass does)…”
And: “So if they [LastPass] were hacked (which they have never been)…”
Oh, how times have changed!