security
In Search of Perfect Security
Perfect security is a myth. What’s important is to pay attention to the trade-offs you make.
Are You Giving Away Your Privacy?
We rail against intrusions into our private affairs and private information and then post our private information publicly. Where’s the logic in that?
Can Someone Install Something on My Computer When It’s Not Logged In?
If your computer is not physically secure, someone could install something even if you’re not logged in.
Why Do I See Lots of Failed Login Attempts on My Account?
I’ll show you how to look at your Outlook.com recent activity and review why it might be full of failed login attempts.
Can My ISP Monitor My Internet Connection?
Your ISP controls your internet connection, and it’s easy for them to monitor the data you send and receive. The question is, why would anyone monitor your internet?
Should I Buy a New Computer to Fix Malware?
Buying a new machine is a common knee-jerk reaction to a bad malware infestation. And it’s wrong. Not just a little wrong — it’s completely unnecessary.
How Long Should a Password Be?
For years, the standard practice has been to assume that eight-character passwords made up of sufficiently random characters was enough. Not any more. Not even close.
8 Steps to Securing Your Router
Your router is your first line of defense against malicious attacks from the internet. Is yours secure?
Preparing Your Technology for Travel Abroad
Travel is exciting, but be sure to plan ahead for your technology to avoid things going wrong.
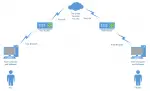
Protecting Your Privacy: Points of Vulnerability
Tracing the privacy and security of the path from your fingertips through the services you use to your information’s final destination.
Why Your “Unimportant” Accounts Matter
Regardless of your initial thoughts, every account is important, and we are all targets.
Security: It’s a Spectrum, Not a State
Many people want to be secure, not realizing there’s no such thing.
Online Shopping: Just How Safe Is It?
Online shopping is ubiquitous, and yet some avoid it completely. Why are some people afraid to shop online when it’s arguably safer than offline?
How Do I Remove Myself from a Machine?
Although there’s no way to remove all traces of yourself from a machine, there certainly are ways to remove as much as you can.
If I Do These Things, Will I Be Anonymous?
Anonymity on the internet is really, really hard. Some of the practices we might use to stay anonymous could still be leaking identifiable, traceable information.
Tip of the Day: Change Your Router’s Password
If I could tell you only one thing about securing your home network, this is at the top of my list.
Is an Up-to-Date Browser Secure on an Out-of-Date OS?
An up-to-date web browser is important, but it’s not the whole picture, by far.
Tip #4: Stay Safe!
Five Tips to get the most out of your technology. Tip #4: Stay Safe – I discuss the most important security software you have.
Do privacy apps really keep me private?
Privacy on the internet means different things to different people. I discuss three different privacy applications out there, explain what exactly each does, and offer some of my own thoughts.
Is Running Windows XP in a Virtual Machine as Risky as Running XP Natively?
In and of itself, running XP as a virtual machine doesn’t make it any less vulnerable. You can add security by restricting what you do inside a virtual machine to the bare minimum required.
How can I get my lost Hotmail emails back?
The answer isn’t going to be too hopeful, though I do have a few small straws you can grasp at.
2013’s Ten Most Popular Posts
As 2013 draws to a close, I review which articles on Ask Leo! were the most popular and briefly discuss what trends that I feel they reveal.