You can use BitLocker safely, but it does require taking appropriate precautions.

BitLocker is Microsoft’s full-disk encryption technology. It’s available in Windows Pro, Enterprise, or Ultimate editions from Vista onwards.
I typically recommend avoiding it, for one simple reason: it’s too easy to encrypt yourself into a corner and lose access to your encrypted data.
I’ll review the steps you need to take to use BitLocker safely.
Become a Patron of Ask Leo! and go ad-free!

Using BitLocker safely
To encrypt your drive with BitLocker safely, right-click the drive in Windows File Explorer and click on Turn on BitLocker. Save the recovery key as part of the setup process. Do not skip this step, or you may lose access to your data. Then back up your data as well.
Encrypting your drive with BitLocker
The process of encrypting your drive with BitLocker is fairly straightforward. Right-click the drive in Windows File Explorer and click on Turn on BitLocker.
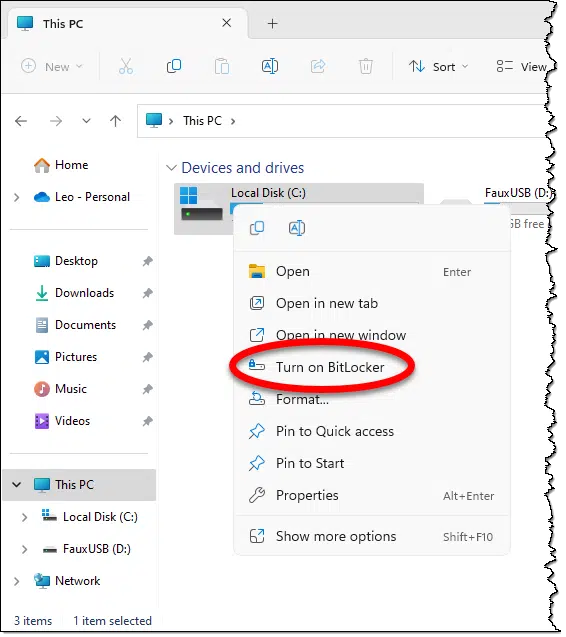
BitLocker will first check to ensure that your system supports BitLocker, and having done so, will proceed to encrypt your drive.
The next step is the most important.
Save the recovery key
As part of the setup process, you will be given the option of backing up the recovery key for your encrypted drive.
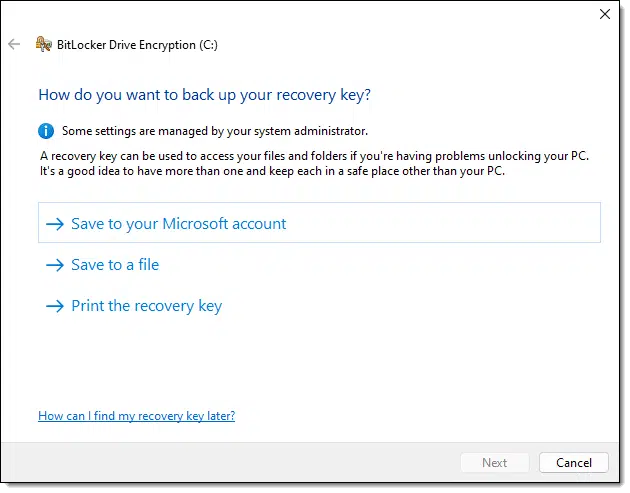
Do not skip this step.
Skipping this step is what I refer to as “encrypting yourself into a corner”. If you lose this recovery key (or you don’t save it in the first place), you can lose everything on the drive.
Losing access to your encrypted drive
There are several ways you can lose access to all the data on your encrypted drive. The two most common are by losing your sign-in account or when system failure strikes.
Losing your sign-in account
Normally we think about simple things — like forgetting the log-in password — that result in losing access to an account.
However, one of the things we see in Windows from time to time is the “corrupt profile”. For various reasons, information associated with your account can become so damaged that you can’t sign in. The typical solution is to create a new account with a new profile to regain access to the machine.
The problem is, your new account is not the account that set up the encryption, and it doesn’t have access to the encrypted data.
Losing your sign-in account for any reason could be enough to lose access to your encrypted data.
System failures
On one hand, you might expect to lose data when a system fails. However, BitLocker encryption also invalidates one of the techniques to recover data from a hard drive salvaged from a damaged computer: connecting it to another computer.
Decryption is tied to the sign-in account that encrypted the data. That sign-in account simply doesn’t exist anywhere but on the machine that performed the encryption in the first place. Even if you re-create an account with the same ID and password, it’s a different account, and you still won’t be able to access the data on the encrypted drive — unless you have the recovery key.
Using BitLocker safely
All that being said, BitLocker is pretty cool encryption technology, and people often want to use it. It’s not uncommon or even unreasonable for organizations to insist it be used to keep data secure.
There are two key elements to using BitLocker safely.
Back up
Backing up seems like a cure for just about anything, and this is yet another case.
An image backup of the encrypted drive will back up everything.1 But even if you just back up the data on your encrypted drive religiously — to the point where losing that drive completely and without warning would be an inconvenience, not a disaster — then you’re safe.
You could lose access to your encrypted data for any reason and simply restore it from backup. The catch, of course, is since your data is sensitive enough to be encrypted, you’ll want to take steps to ensure your backups are also secure. That may mean encrypting them separately or keeping them in a secure location.
Keep that recovery key
The recovery key created when you set up BitLocker is like a magic key that will recover access to the data from another log-in account or another machine. The catch is you need to have it — which means creating it in the first place and being able to find it when you need it. Since it is a magic key to your data, it needs to be kept safe and secure.
If you didn’t create the key when you enabled BitLocker (or BitLocker was enabled to begin with2), right-click on the drive, click on Manage Bitlocker, and click on Back up your recovery key.
Back up the key, back up the data, and you can use BitLocker safely.
However…
How data gets lost
There are two things I can tell you from my experience running Ask Leo!:
- Too many people don’t back up appropriately.
- Too many people misplace important files.
The reason BitLocker scares me is that when you put those two things together, a lot of people lose access to important data on their BitLocker-encrypted drives.
Alternatives
While they’re not built-in like Bitlocker, alternative technologies like VeraCrypt and Cryptomator are less complex and more portable with no loss in data security.
Consider VeraCrypt: you encrypt it with a passphrase. That’s the only thing you need to remember, and you can choose any technique to do so. A VeraCrypt volume is completely portable and can be moved from machine to machine — even machines using different operating systems (including Mac and Linux). All you need is that passphrase.
The same is true for Cryptomator. In fact, I rely on Cryptomator to do both: I regularly copy encrypted data between several PCs and Macs and use it on both platforms.
Do this
Regardless of what technology you use, use it safely. That means saving or remembering the encryption key and backing up the data.
If you use BitLocker, make certain to create the recovery key and save it in a safe place.
Be sure to subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: Though it’s important to understand whether an image backup of an encrypted drive will back up the data in encrypted or unencrypted form. I recommend the latter whenever possible.
2: I have been seeing new machines come with BitLocker enabled on the system drive. It’s worth checking. If you see “Manage BitLocker instead of “Turn on BitLocker”, then BitLocker has already been enabled for that drive. Back up the key right away.




You can unlock and access data on a BitLocker encrypted drive by attaching it directly to another computer (example: SATA) or via an external USB adapter/enclosure; and providing “either” the correct password or choosing “I Forgot the password” and enter the recovery key. The encryption method is not tied to a particular user account. The loss of both the Password AND Recovery key will cause the data to become inaccessible. Microsoft will usually maintain a copy of the recovery key (but do not depend on it being available) if the encryption of the drive were performed while logged in to a Microsoft account as opposed to a Local account.
The encrypting file system (EFS) requires the export/import of the security certificate. You WILL lose access to data without the proper certificate. This method is more complex to administer and probably should be avoided outside of a corporate domain environment.
QUESTION
with bitlocker, if you back up the image, can you recover that image to an unencrypted drive, in even t of disaster, so that you can then re-encrypt the recovered image?
I currently encrypt full drive with truecrypt, and do backups of images of the c: drive (I back up to truecrypted external drives), and if I need to recover, I can copy one of the backed up images to a clean drive, and then run recovery (I use Paragon Hard Disk Manager 2015), and I then have a working image on a new drive.
I have NOT tried this with bitlocker, but would like to know if it works
thansk
What’s important here is that you backup the UNencrypted data. That can be restored wherever you want.
If you backup the encrypted partition then you may not be able to restore it anywhere other than on the same machine. I’m not 100% on this, but it scares me enough that I would not do it.
I have three machines running Windows 7 Ultimate SP1 that are too old to have a TPM (Trusted Platform Module) chip in them so BitLocker doesn’t work on any of them. I use TrueCrypt instead to do whole-drive encryption. Since TrueCrypt uses pre-boot authentication in order to start the computer, a thief would be stealing a really fancy paper weight with no way to start the machine without entering the 25+ character passphrase. Anybody who tries to view the data on the drive by plugging it into another computer would see nothing as everything is encrypted.
While TrueCrypt is no longer supported by the developers, I feel confident using it, at least until an actual vulnerability is discovered.
A TPM is NOT required to use BitLocker but you need to change a Group Policy setting to allow it to work without a TPM.
Below are a couple of links from Microsoft outlining how to recover a Bitlocker Encrypted Drive if the machine (but not drives) fails.
For the second link, search “can I access”. It’s about halfway down the page
Basically, you just need to have your recovery key.
http://windows.microsoft.com/en-us/windows-vista/regain-access-to-a-computer-locked-by-bitlocker-drive-encryption#
https://technet.microsoft.com/en-us/library/Hh831507.aspx
Is it safe to bitlocker on computer. what if I lost the key and not able to access my user account either.
is it possible to open the encrypted file on other device also. whether my onedrive, googledrive and other online cloud folders will also get encrypted with this bitlocker.
if everything will be encrypted whether I will be able to open those folder on my handheld gadget also. or I need to put bitlocker everywhere on all gadget.
Bitlocker will only encrypt the files on your computer. Any file uploaded from your computer to the cloud will be unencrypted. If you want to encrypt your files in the cloud, you can use a program like Cryptomator.
I have a general question about bitlocker. We use to use another encryption software for out laptops, and with that software, you could take the hard drive out of the laptop, and put it into another laptop of the exact same type and boot the machine. I have also noticed that you can do this with bitlocker (although, last time we tried to do this, it did not work).
Isn’t being able to do this type of thing rendering drive encryption useless? if you can steal someone’s hard drive (not the entire computer, just the hard drive), or grab an image of it and boot it in an identical pc, make drive encryption useless?
No. You’d still need the password in order to be able to boot Windows and access those files.
I bought a new computer when my old and dear XP died. It came with Win 8.1 which was ok after I played around with it. Then the DREADED update to Win 10. Ok. no problem -except there is NO Bitlocker on my computer anywhere, any shape or form. I dunno why. I’ve been up. down, back and forth, all through the nooks and crannies searching the whole damned computer and there is no Bitlocker anywhere. I can’t find anywhere I can download it. Micro$soft doesn’t have a download, it’s supposed to be preinstalled, I guess. If there’s a download for Bitlocker, tell me where.
Drat and durn . I can exist without it as I have a secure system (I hope) and have my OS and system stuff in a seperate physical drive aside from my apps.
Not every Windows 10 version supports Bitlocker. From: https://support.microsoft.com/en-us/help/4028713/windows-10-turn-on-device-encryption “It isn’t available on Windows 10 Home edition.”
Over the past week I’ve dealt with “it’s too easy encrypt yourself into a corner and lose access to your encrypted data.” I’ve been researching this and found that other people are having this same problem.
My laptop was having boot-up problems and every proposed solution lead me to a screen that asked for a Bitlocker recovery key. I’d never heard of Bitlocker before. More than a week later I decided to just go back to the factory settings. NOPE! Can’t even do that without the Bitlocker recovery key.
Now the laptop is at Best Buy undergoing a clean install for $100.
I have noted that some new laptops (including my own) are coming with Bitlocker enabled by default. While that’s generally a good thing, it should really REALLY be made obvious, and saving a key should be part of the initial setup process. Sadly it is not.
Leo, I’m in trouble. I recently turned on my laptop to see the BitLocker screen. I knew nothing about what The Bit was. But I was able to get the recovery key by logging into MS. When I couldn’t get anywhere with the key of a thousand digits, I called Dell. After almost two hours of their tech trying to help me and me inserting all those numbers in time and time again, the tech came to the conclusion that Windows 10 kept crashing and that pc would have to be reset. I said I would have to get data backed up by Geek Squad on an external hard drive I had. However, Geek weren’t allowed to do it. But recommended place where I could have it done with hard drive being placed in a third party pc and then backed up.
Needless to say, this old babe here almost went to heaven when told that my hard drive was locked by The Bit and could not be unlocked.
Now Dell who keeps in touch with me, cuz they know I’m old called me right after getting this bad news. So, they ready for a reset. I can’t bear it. Is there anyway out that you can suggest? If so, please help me. TIA
Unfortunately no. This is the purpose of whole-disk encryption: to keep people out if they don’t have the encryption key. Unfortunately, as you’ve seen, some people who should have access can’t.
One lesson to take away from this: start backing up. If you lose anything simply because you can’t access the hard drive, then you weren’t backing up.
I have been using Bitlocker for a long time now. The most important thing to remember about using it is to backup the recovery keys. Currently I have the keys backed up to my Microsoft account, a flash drive, and printed copies kept in a safe.
In over ten years of using Bitlocker, I’ve not had any issues caused by Bitlocker. I use Macrium Reflect to backup my computers and Reflect works with Bitlocker enabled. Remember to check the box for Add Bitlocker Support under Advanced Options when creating Macrium rescue media.
I have performed maintenance on hard drives, such as running Chkdsk, on Bitlocker-encrypted drives without issue. There are times when either Windows or Macrium will ask to suspend Bitlocker protection, which then will be re-enabled after a restart of the computer.
And I also am using Cryptomator for files stored on OneDrive. I keep unencrypted copies of those files on separate external hard drives just in case.
I’m in the same camp as Mark H. Using Bitlocker for full-drive encryption on laptop and external drive (starts on bootup); Macrium (paid version) for backups to an external drive and Cryptomator for encrypting my cloud content.
Feel good that if machine and ext drive were ever stolen, they wouldn’t get one step into either without the 9 digit PIN I use.
Back in my XP days, I used TrueCrypt. It was okay at the time. A few years ago I decided to look into VeraCrypt for use on my Windows 10 Pro. I don’t know why but I decided not to use VeraCrypt. Instead, I opted to use Bitlocker but I did not want to encrypt my whole drive. Before turning on Bitlocker, I partitioned one of my HD’s. I only use Bitlocker on that new partition (Drive “X”). That is where I save all my sensitive data. I also save that data on a Thumbdrive… just in case. I also created two batch files on my un-encrypted drive. One file un-locks Drive “X” (after manually typing a password), and the other batch file to re-lock Drive “X”.
Looks like Bitlocker is useless against any decent adversary and certainly useless against law enforcement if they have your system (laptop, desktop or TPM chip) and not just your drive. https://www.theregister.com/2024/02/07/breaking_bitlocker_pi_pico
Most computers (& probably all laptops), nowadays, have the TPM integrated on the CPU chip which doesn’t allow that hack.
To be clear, as that article mentions:
So it’s only a subset of Bitlocker installations, and a subset of theft/compromise situations.
I also expect it’ll be something soon fixed.
Hi there,
I have purchased a new laptop (lenovo ideapad 5) with windows 11 Home on it. After unboxing the laptop, I first created a local account and never connected to the Internet; I am still configuring the thing and figuring out a couple of issues. With rescuezilla I want to make a disk image (first out of the box, and then another with all the updates on it and possibly some partitioning of the SSD). For that I need a bootable USB flash drive with rescuezilla on it. That flash drive requires me to change the Secure Boot policy – standard you can only boot via internal media. If you change the boor menu, then the configuration data on the configuration platform differs from what is stored in the TPM; next time you start the laptop, it will ask for the Bitlocker recovery key. Oh, but I created a local account and on the tab Privacy & security> Device encryption it says Device encryption is on, but it also says ” Sign in with your Microsoft account to finish encrypting this device.” Looking with a Command Prompt, using ‘manage-bde -status’ I see Protection Off and Percentage encrypted at 100%. The result of this status with the used space on the SSD encrypted and the protection off, is that I have no Bitlocker recovery key. No problem if I do not need it, but if I do then I am in trouble. What to do? Is there a way out, or do I have to give in to Microsoft and have them poke their noses in all of my data?
Thanks
So I read that you now longer have objections to Bitlocker, but I do not know whether Bitlocker and Rescuezilla (or any other software that uses a USB drive) can live together. Maybe I did not fully understand the entire complexity, but your article does make me wonder if Bitlocker allows for booting from a bootable USB drive? That seems to be required if you want to use Rescuezilla. In the mean while, I consider decrypting the SSD; hoping to get F12 working at start up so I get into the boot menu; making an image of the disk, after which I might have to concede to MS – I need the Windows updates – and in the end have Bitlocker active on my laptop, while not knowing how to make a disk image in the future.
“Do not skip this step.
Skipping this step is what I refer to as “encrypting yourself into a corner”. If you lose this recovery key (or you don’t save it in the first place), you can lose everything on the drive.”
The graphic mentions three options:
I do all three and recommend people do all three.
Option #3 – I print it as a PDF. I do similarly with all programs recovery options that allow more than one method. It’s like Leo’s often stated “If it’s only in one place, it’s not backed up.“
So I read that you now longer have objections to Bitlocker, but I do not know whether Bitlocker and Rescuezilla (or any other software that uses a USB drive) can live together. Maybe I did not fully understand the entire complexity, but your article does make me wonder if Bitlocker allows for booting from a bootable USB drive? That seems to be required if you want to use Rescuezilla. In the mean while, I consider decrypting the SSD; hoping to get F12 working at start up so I get into the boot menu; making an image of the disk, after which I might have to concede to MS – I need the Windows updates – and in the end have Bitlocker active on my laptop, while not knowing how to make a disk image in the future.
Booting from an external drive has nothing to do with Bitlocker as it opens a Windows completely separate from the installed Windows. What blocks booting from an external drive is Secure Boot. Secure Boot has to be disabled to boot from an external drive.