Articles in Category: Encryption
How Do I Know If My Hard Disk Is BitLocker-Encrypted?
Your hard disk could be BitLocker encrypted without your knowledge.
Protecting Your Data: Why I Avoid Most Pre-Installed Security and Encryption Software
External hard drives often come with security and backup software. I’m not convinced it should be used.
BitLocker vs. Cryptomator: Why I Use Both (and When You Should, Too)
Use different tools for different purposes.
Cryptomator vs VeraCrypt: Which Do You Want?
Cryptomator and VeraCrypt are both excellent encryption tools. We’ll look at how to choose the right one for your situation.
Why Encryption Backdoors Are a Horrific Idea
A phrase we’ve heard more and more often in recent years is encryption backdoor. The concept is simple: government agencies want to be able to monitor otherwise encrypted communications. The concept is flawed.
How Do I Recover Encrypted Files From Cryptomator?
Recovering individual files from a Cryptomator encrypted vault can be tricky. I’ll discuss why and how to protect your access to those files.
How Can I Password Protect My Documents?
There are several options to keeping information private on your computer.
Why Won’t My VeraCrypt Volume Back Up?
When using VeraCrypt containers, the default setting may interfere with backing up your container. Here’s how to fix that.
Password Update Without Re-encrypting: How?
If your password is used to encrypt your hard disk, how can you change your password and still be able to decrypt your disk?
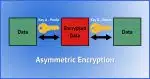
What Is Public Key Cryptography?
Public key encryption is the workhorse of security online. I’ll review just what it is and how it’s used at a high level.
What Encryption Software Do You Recommend?
There are many different tools for encryption. The right one depends on what you’re attempting to accomplish.
How to Back Up Encrypted Data
Encrypting your data is important for security, but it also adds risk that’s easy to overlook when backing up.
How Should I Password-Protect an External Hard Drive?
You want more than a password; you want encryption. Encrypting an external drive can be done with the right software.
Find Your Lost Bitlocker Recovery Key in Your Microsoft Account
BitLocker might be turned on without your knowledge. That’s fine, but make sure you have the recovery keys stored somewhere should you ever need them.
How Can an Https Website Still Not Be Secure?
Surprisingly, it’s possible for aspects of an https site to still not be secure, if the site is improperly designed. And it’s extremely difficult to tell.
Does Whole-disk Encryption Impact Computer Performance?
Whole-disk encryption has only minimal impact on the performance of modern computers and hard drives. I’ll review why that’s the case and outline something more important: your ability to access the data when something goes wrong.
What Happened to TrueCrypt and What Do I Use Instead?
The TrueCrypt project was suddenly and without warning shut down. I’ll look at a little of the history and what you should use instead.
Use BitLocker to Bypass Potential Self-Encrypting Drive Vulnerabilities
Headlines to the contrary, it’s BitLocker to the rescue to protect yourself from some vulnerabilities discovered in drives providing hardware-based encryption.
VeraCrypt: Free Open Source Industrial Strength Encryption
VeraCrypt provides a solution for encrypting sensitive data — everything from portable, mountable volumes to entire hard disks.
How Should I Encrypt the Data on My Laptop?
Protecting data on your computer is key. I’ll look at three common encryption methods.
How Do I Encrypt a Hard Drive Using VeraCrypt?
VeraCrypt makes is easy to encrypt whole drives, making it safer to travel with your data. Here’s how to safely encrypt and then access your data.
Using BitLocker Without a TPM
Should you want to use BitLocker on a machine or virtual machine that doesn’t support TPM, there’s a single hoop to jump through.
How Do I Encrypt a Disk?
For many, it’s important to be able to encrypt a disk entirely. Particularly if a portable machine contains sensitive data, whole-disk encryption is key.
How Do I Encrypt a Folder?
It’s not uncommon to want to encrypt a folder and all it contains. There are several techniques to encrypt a folder, each with pros and cons.
How Do I Encrypt a File?
Since most encryption tools are designed to encrypt collections of files, the best approach to encrypt a file isn’t always obvious. I’ll look at a couple of alternatives.