It disables one, not all.

That’s a comment I received from a reader relating to the pernicious tech support scam, where scammers call you, say they’ve detected problems originating from your computer, and offer to fix it for you — perhaps even for free — if you just give them access to your computer.
Disabling remote access in Windows does not disable this kind of remote access. It does nothing to prevent remote access scams.
I’ll review the setting in Windows and compare it to the remote access more commonly used by scammers.
And, of course, I’ll review what you need to do to stay safe. There’s a good chance it’s something you’re doing already.
Become a Patron of Ask Leo! and go ad-free!

Disabling remote access
Turning off remote access in Windows doesn’t stop scammers because that’s not the tool they use. They trick you into using tools that ignore those settings. The real fix? Don’t give access to anyone you don’t know. Be skeptical. Only use remote access tools with people you absolutely trust.
Windows Remote Desktop
As outlined in “What’s the Difference Between Remote Desktop and Remote Assistance?“, Windows Home editions don’t support being accessed remotely by Remote Desktop, so this section doesn’t apply to computers running Home edition.
In other editions of Windows, search for “remote access” or “remote desktop settings” and click on the latter when it appears.
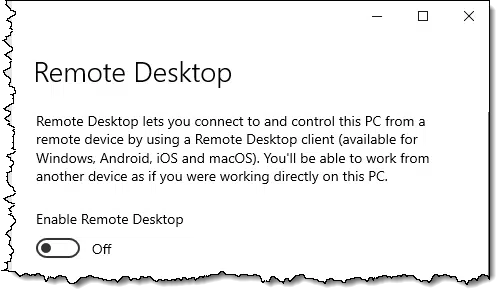
Remote Desktop allows someone to remotely use your computer as if they were sitting in front of it.
It works most seamlessly on local area networks, so if you have multiple machines behind a single router, it can be a very useful tool for that as well.
If it’s not something you know you need, leave it off.
Either way — on or off — it’s unrelated to the scams we hear about. Scammers rarely use Remote Desktop.
Windows Remote Assistance
Remote Assistance is similar to Remote Desktop because it allows someone else to access and control your computer. However, you must initiate each remote assistance session, and you can watch and interact with whatever the other person is doing.
To find it, search for “Remote Assistance” and click on “Allow Remote Assistance invitations to be sent from this computer”.
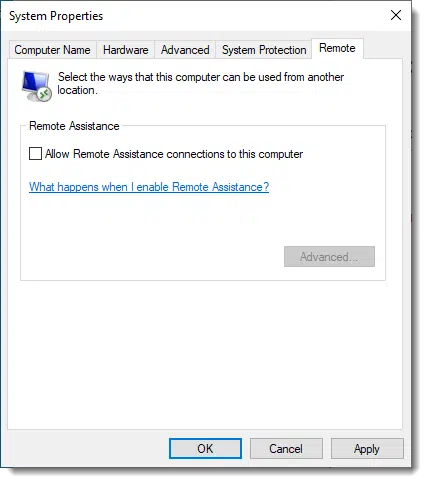
I recommend you leave this option off unless you’re about to use the remote assistance feature, and then turn it off again when you’re done.
Or leave it on. Once again, this is rarely a tool used by scammers.
Remote Access using other tools
There are a myriad of other tools to access computers remotely. I happen to be partial to Google’s Chrome Remote Desktop, but tools like TeamViewer, LogMeIn, GoToMeeting, Zoom, and others are all valid and useful tools to access someone’s computer remotely.
Scammers try to convince you to install or otherwise use these tools. To be extra clear, the tools themselves are not scams or malicious. Like most tools, though, they can be used for good or evil.
The bad news is that none are affected by the Remote Desktop or Remote Assistance settings I just described. They’ll work regardless of those settings.
The good news is that these tools don’t start themselves; like Remote Assistance, you have to take steps to let someone into your machine.
And this is exactly what scammers try to get you to do.
Do this
The solution is simple. Most tech support scams will be very insistent that you need to take action — action that will allow them access to your computer.
Don’t. That’s it. Don’t.
Be skeptical1. Don’t trust people you don’t know, especially people who call you out of the blue.
Use remote access as you see fit — it’s an incredibly handy tool — but only use it with people you know and trust. You’re giving them complete and total access to your computer. That’s not something to give to just anyone.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Footnotes & References
1: Since you’ve been reading Ask Leo! regularly, you probably already are. But for everyone else…

Also be very careful when searching for support, especially for a free service such as Hotmail, Facebook or Gmail. Free services generally don’t offer phone support. If it’s a paid service better to go directly to the company’s website, for example, {company_name}.com. Scammers have a lot of fake websites offering fake phone numbers or links.
The Risk of Searching for a Support Phone Number
what about “remote apps and desk top connections” in the control panel?
when i click on that it says “there are currently no connections available
on this computer”. wouldn`t that at least let me know if someone has
gotten remote access somehow? i`m still on win 7 ult.
Hi GlenLW
In short no. The control panel really only shows the Microsoft apps connection to your computer but as indicated in the article there are many ways to connect which would not be covered in the Control panel setting. e.g. VNC
So how exactly do the scammers get access to your computer? From what I understand, they first have you open the Event Viewer where there are a bunch of “scary” warnings & errors. Then do they have you go to some type of Go To Meeting link where they can remotely access your computer & do the damage?
Exactly … after convincing you they can help, they share a link with you that opens remote access using one of the commonly available tools.
OK, I read the article — twice, three times. But what do you do when you are comprised? How do you get them out? How do you stop them from sabotaging you down the line?
When you are compromised, you must assume the worst. Even though this article talks about scammers claiming to be from Microsoft, it applies to any similar scam: I Got a Call from Microsoft and Allowed Them Access to My Computer. What Do I Do Now? – the section “Recovering from the scam” has next steps.
It happened to me… once your computer is compromised, the only choice is to get another computer or pay a professional to clean out the infected computer.
You Do Not Need To Get A New Computer!
Please read: My Machine’s Full of Malware; Should I Get a New Computer?
Here is what I did when a friend’s machine was compromised (& no they did not have a current back-up of their computer).
1) Removed the hard drive from the laptop and installed in an external hard drive enclosure.
2) Connected the usb drive to another machine that had anti-malware installed (made sure that PC was not connected to a network or the internet). If there is something very nasty & aggressive, you don’t want it escaping into your network or phoning home.
3) Ran scans on the external drive to see if there was any “obvious” malware on the drive.
selectively copied data files off the hard drive to another drive.
4) Wiped the suspect hard drive, reinstalled in the computer and did a clean reinstall of windows. My normal preference would be to start with installing a new drive rather than the old drive – just in case there is a rootkit installed that escaped being wiped.
5) Copied recovered data files back to the PC.
I have been trying to reach pcmatic for some time. I hopes you can help by forwarding this message/My phone number is {removed}. Pcmatic does not run properly on my computer. The last 2 weekly scans on Tuesdays have started and stopped at exactly the same time; the start numbers and end numbers are identical. When I click on the shield icon on my task bar nothing happens. When i right click I get 2 options: remove the icon from the task bar or a second opportunity to click on the icon.
I need to have them respond by telephone because I think the computer will block any direct response.
Never publish your phone number, email address or other personal information on a public forum. It opens you up to spam, marketing calls and scams.
There must be other ways to access remotely….It’s happening to me and I have not let anyone in remotely for sure. I also live alone. When I am under the event viewer, device manager looking at a remote desktop device called the redirector BUS, it has a computer named: WIN-IPO0RLK1C4T as shown below: Copied/Pasted from the event viewer:
Microsoft-Windows-Kernel-PnP/Configuration
Computer WIN-IPO0RLK1C4T
– Security
[ UserID] S-1-5-18
I am not sure what to even do with the information I have, let alone how to keep them out. I’ve done a lot of research on so much since this all started. Pretty sure it is an ex husband soliciting the help of a very smart hacker-nephew of his, but again no proof. I just have mental fun with it. Anyway, no one seems to know anything about this so I thought I’d try to pique your interest. Please advise, thank you.
I seem to be morphing into some computer geek against my will!!!!! HELP~~~ lol. Thanks again.
I’m not sure how you’re interpreting this as remote access?