Yes, it’s still true: a VM doesn’t get you any additional privacy from your ISP.
I do need to clarify exactly what “everything you do” means. I’ll also revisit what you need to do to avoid ISP monitoring. Hint: a VM isn’t the solution, but might be a convenient part.
Virtual Machines
To refresh: a virtual machine, commonly referred to as a “VM”, is software you run on one machine in which you create a simulated environment of another.
The best way to conceptualize that is with a picture. Here’s a snapshot of my Mac Pro’s desktop.
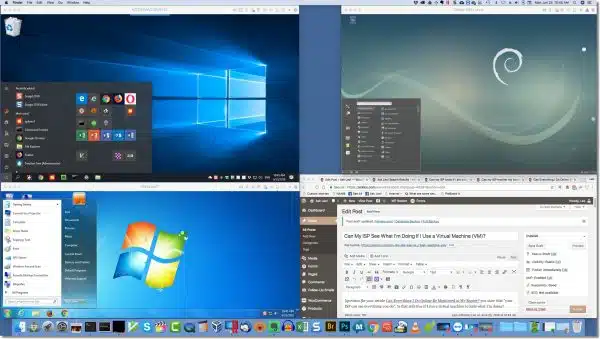
You’ll see that in addition to the Mac “Dock” (an equivalent to the Windows taskbar) across the bottom, and Chrome — the browser in which I’m writing this article — there are three additional windows, each running what looks like a completely different operating system:
- In the upper left is Windows 10
- In the lower left is Windows 7
- In the upper right is Debian Linux
Each of these systems believes it’s running on dedicated hardware, but in fact is running in a software simulation of a PC. As you can see, it’s possible to run several such simulations simultaneously with different operating systems in each.1
What your ISP doesn’t see
Your ISP only sees the connections your computer makes to the internet. That means it has no concept of what software is making those connections, outside of anything those connections imply.
So when my browser makes a connection to askleo.com, my ISP can see it, regardless of whether I do it in the native browser — Chrome, in the example above — or in a browser within one of the virtual machines. My ISP just sees there’s a connection being made to askleo.com by some machine at my IP address.
This is very similar to what happens if you have more than one physical computer: your ISP cannot generally tell which is making the connection. The rule of thumb is that virtual machines behave just as if you had multiple, different, real computers.
What your ISP might see
Help keep it going by becoming a Patron.
I said your ISP has no idea what software you’re running outside of what the connections you make imply. For example:
- If you connect to askleo.com, your ISP can tell you’re probably running a web browser.
- If your connection is unencrypted, and your browser includes information that says “Hi! I’m Google Chrome” as part of the conversation, your ISP might see that.
- In fact, any information in an unencrypted connection could be seen by your ISP and used to infer what software you’re running to create that connection, and what that connection is used for.
More interestingly, though, it’s the services we connect to that expose some of what you’re doing.
- If you connect to a file-sharing service, your ISP can infer you’re running file-sharing software. However, if the connection is encrypted (as most are), your ISP can’t see what files are being shared.2
- If you connect to a VPN (virtual private network) service, your ISP can see that you’ve done so, but cannot see beyond that.
- If you connect to a TOR (The Onion Router) anonymization server, your ISP can see that you’ve done so, but cannot see beyond that.
But it doesn’t matter where those connections originate on your machine: from the programs you run directly, or from programs run within a VM; to the ISP, they all just look like connections and data transferring to and from your internet connection.
The best hiding you can hope for
If you don’t trust your ISP, things get difficult.
Honestly, the best privacy solution is to use a VPN. As long as it’s correctly configured, your ISP will still see that you are using a VPN, but they are not able to see what sites or services you are connecting to, or what data you’re exchanging with those sites.
The next level would be to run a dedicated TOR browsing session. It’s slower, and it’s easy to leak information if you’re not careful, but it can be done. (TOR focuses more on end-to-end privacy and traceability than a VPN, whose primary job is to protect your connection to the internet from eavesdropping.)
Finally, one approach that might be convenient, if you’re so inclined, is to set up a virtual machine that uses one of these technologies. That’s nothing more than a convenience, though, and doesn’t increase your privacy. All it does is make it easier to run a virtual machine that’s pre-configured with your favorite VPN or TOR — exactly as if it were a different always-ready physical machine at your location.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!


When I started reading that article, I wondered if, maybe, the person asking the question confused VM (Virtual Machine) with VPN (Virtual Private Networking). Then you eventually discussed how a VPN works, so even if the person asked the wrong question you covered it anyway.
It’s quite possible, and indeed, that was part of my approach to the answer.
“Honestly, the best privacy solution is to use a VPN. As long as it’s correctly configured,”
Unfortunately some Dial up VPN connections leak DNS requests by default, so people may believe they are correctly setup but in fact are still leaking information to their ISP.
While this is a risk, this is not true of all VPNs. Because this is a known issue many VPNs carefully handle DNS requests as well. (And I’m not sure what you mean by “dial up” VPN. All VPNs are services to which you need to connect to use.)
My Bad Rasdial vs OpenVPN client 🙂
HI Leo what about Proxy servers like the one in Opera web browser? can they still see threw it like normal browsing. i seen you covered VPN and VM but said nothing about proxys?
A proxy is in a sense a more limited form of VPN. The proxy provider can see everything that goes through the proxy just as if they were your ISP.
I’ve always looked as a VPN basically as an encrypted proxy.
That’s off the mark, in my opinion. Proxies can be (and often are) encrypted as well. I think of Proxies as browser-based web-pages only, whereas VPNs should handle all internet traffic.
how do I know that my VPN (I use Kapersky) is correctly configured?
There’s no way to know for sure but in addition to the question of DNS leaking, it’s necessary to be able to trust your VPN. This article discuses Kaspersky Internet Security but it applies equally to any of Kaspersky’s products. Your VPN has access to all of your unencrypted internet traffic and all of the sites you visit. The integrity of your VPN provider is extremely important.
https://askleo.com/safe-kaspersky-internet-security/
Impossible for me to say. I’d check with the VPN’s support options.
Regarding the various versions of Windows you’ve tested in VMs, I would imagine that Windows 98, XP and Vista are so old and no longer updated that you would simply disable the ethernet connection in the VM, and those are then in effect in a closed sand box. Otherwise, same as the PC.
True. Unfortunately, though, that typically means disabling the network connection which dramatically reduces their ability to access even other machines locally.
I do believe that I have heard that there are utility programs that can help you determine if you configured VPN is leaking info?? Do you know about any of these utility programs and how they are used. I would like to lean more about this. Thanks
I don’t, but if you google “vpn leak test” you’ll likely get some good results.
In addition to DNS leaks there are problems with WebRTC leaking information, whilst this is apparently a browser problem it is a concern.
This is a list of 16 VPN providers who are known to leak according to a report done by Tech Pro Reasearch
“Of the 74 VPNs analyzed in the report, 16 were leaking data. DNS leaks, WebRTC and IP leaks, and Chrome extension leaks were the most common, the report found.”
“VPNs leak for a variety of reasons,” the report stated. “DNS server issues and WebRTC API conflicts can cause your true location to shine through. The problem is that these often strike when you least expect it.”
Hoxx VPN (free & paid version)
Hola (free version)
VPN.ht (paid version)
SecureVPN (paid version)
DotVPN (free version)
Speedify (free version)
Betternet (free version)
Ivacy (free version)
Touch VPN (paid version)
Zenmate (free version)
Ace VPN (paid version)
AzireVPN (paid version)
BTGuard (paid version)
Ra4w VPN (paid version)
VPN Gate (free version)