Technically, yes, but in most cases, no.

Yes, it’s true.
But before you focus on it too much, there are two things to keep in mind:
- First, it’s not easy for the average consumer to do.
- Second, there are easier alternatives to monitoring than your router.
Let me explain what I mean and what you can do to protect yourself — if, indeed, you can protect yourself at all.
Become a Patron of Ask Leo! and go ad-free!

Monitoring at the router
- Your ISP has the technology to see all traffic on your connection.
- Monitoring traffic at home is conceptually easy but technically difficult.
- Encryption is your best defense against monitoring.
- Physical access allows for easier monitoring.
- The police have access, but generally only with appropriate cause and documentation.
Your ISP can see everything you do
Your ISP’s equipment is at one end of your connection, and your home router is at the other. We’re talking about the data flowing between the two.
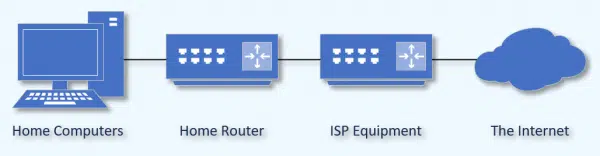
Whoever controls or has access to the equipment at either end of that connection can monitor it.
I’ve written about this before specifically talking about your ISP. They have the equipment to monitor the data flowing over their connection and their equipment.
But just like your ISP at the far end of your connection, anyone with access to your router at home can also monitor your internet traffic.
It’s just not particularly easy.
Monitoring traffic at home
ISPs have equipment that makes monitoring internet traffic fairly easy. They usually don’t do it, because you and I just aren’t that interesting. Only when law enforcement arrives with a warrant might they start to pay closer attention.
Most home or small business routers don’t have full monitoring functionality. That’s not what they’re built for. Some might be able to expose what websites and internet services have been visited, but not the data exchanged as part of those visits.
However, with some cheap equipment, free software, and access to the connections going into your router, direct monitoring is possible.
It’s pretty simple physically. Someone inserts a hub into the connection between, say, the router and your computer. They connect another computer to that same hub and run free, open-source packet-sniffing software to monitor all the traffic between your computer and the router.
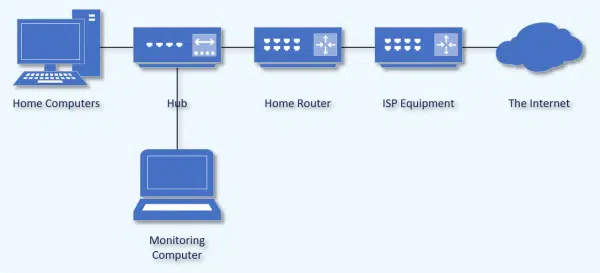
It’s not difficult to connect; the hard part is analyzing the data. Packet-sniffing software is designed for folks very familiar with networking.
If your dad is a computer geek or network engineer, this may be no problem for him. On the other hand, if his expertise is elsewhere, this may be pragmatically impossible.
But Dad has easier alternatives that I’ll speak to in a moment.
Protecting yourself from sniffing
Everything I’ve described so far should be very, very familiar. It’s exactly the same type of sniffing that can be done at an open Wi-Fi hotspot.
As a result, all the steps you take to protect yourself in an open Wi-Fi hotspot apply here.
- Turn on your computer’s firewall.
- If you use a desktop email program, make sure its connections are encrypted via SSL or TLS.
- If you use web-based email, make sure that it’s via https and only https.
- Make sure any sensitive website you visit uses https and only https.
- Consider using a VPN.
A VPN will protect you more or less completely. Anyone monitoring will know you’re using a VPN, but that’s all; they won’t be able to see what sites you visit, connections you make, or data you exchange.
Without a VPN, it’ll still be possible to see what sites you visit and servers you connect to.
Without https or SSL, all data going back and forth is visible to anyone watching.
Physical access trumps everything
If someone has physical access to your PC, they can do whatever they like when you’re not looking. That’s often much easier than playing around with your home network to set up some kind of monitoring.
All they need to do is install spyware. It might even go by the name “parental monitoring software”.
To be clear, while it’s aimed at parents monitoring their children’s internet usage, you don’t need to be a parent to use it, and you don’t need to be a child to be monitored. There are assorted packages readily available for this type of monitoring, and they’re easy to use.
About the police…
In your dinner conversation, you said, “Police can monitor everything that you do on the web and can track you.”
Taken at face value, that sounds a little paranoid, and I want to address that.
Literally, it’s true. They can.
Perhaps in some countries and jurisdictions, they do.
But in most of the world, they don’t. In most countries, the police can’t just “monitor everything you do” on a whim. They must get a court order or warrant first. Only then can they compel the ISP or other services to provide the monitoring data.
The police have more important things to do with their very limited resources than monitor us. As I’ve said many times, we’re just not that interesting.
Well, we’re not that interesting to the authorities.
How interesting you are to your dad might be another matter.
Do this
For the most part, I don’t think this is something most people need to worry about. However if you do, then:
- Scour your machine for monitoring software.
- Consider using a VPN.
Consider subscribing to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




Hi, so can my parents see what I have been searching even if i click on Ctrl+H to remove all search history?
can they see who i have been direct messages to via Instagram? Or who’s profile i have checked on Instagram? And under what username/account I am signed in as while i’m browsing through instgram on my labtop?
can my router see what I have submitted (this letter) into this website?
please respond ASAP
thankyou
Possibly, yes. There’s no way to know for certain, but it is possible.
Can my dad see if i went on an app? like for eg discord, since im not using it on the chrome but im using the app of it, would that show up for him when checking the internet?
Unlikely. Possible (read the article) but very unlikely.
even if its on a laptop right?
and even if he can see that i went on the laptop app , discord, through the router or internet, could he see what servers i went on?
Again UNLIKELY. Technically possible, but very unlikely.
Thank you for the information. I have had serous privacy issues and i now know it’s definitely spy wear. I’m not even able to receive my email and every time I try to delete my cookies or update my privacy it takes me to Verizon Media like I have a child lock of some kind. I am a adult I assure you. I am beyond aggravated.
I have had a scammer on me for 3 years. He blocks all my reports. Feel free to access my blocked people on FB, Twitter and I G. I have tried every Avenue to get rid of him. Please get rid of him. Thanks
We don’t have the means to do that.
My immediate family (me, wife, adult son) share my home WiFi network (pass phrase protected). The nearest neighbor is 1/4 mile away so out of WiFi range. My VPN is automatically engaged when I boot my computer so is always on. However, my wife and son’s devices aren’t protected with VPN. Not a big worry since virtually 100% of their traffic is via https (they both use web gmail.)
My dad has webwatcher and He can see a live view of my screen even with wifi on and he tracks my keystrokes how do I turn it off
I’d treat it as malware, which it is.
How Do I Remove Malware
I’m a. It confused… I use a VPN(proton) and I use Yandex if that’s helpful…. Anyway I use a friends wifi down the hall from me and thought I would be relatively anonymous to her and others but yesterday she says oh you visited sites that were considered to be dangerous and proceeded to name said websites! I believe It was sent to her as a notification that she was reading at the time. Also she had made mention to me once or twice things which I found to be odd and made me think a bit. Such as “don’t look up anything weird on my phone” while I was using it for a few minutes while I was with her. Please let me know what is going on. Also if she is being sent request about the sites I visit wtf is going on to begin with? How is it that is able to be a notification if I’m using a VPN to begin with? That means the Internet provider is able to see and is monitoring my traffic as well as sometimes reporting to her about said traffic!?! How is that possible and who else has access to this information?? Thanks for any help you can provide it is much appreciated.
If you’re using a VPN, she shouldn’t be able to see anything. Make sure that app is actually using the VPN, and make sure DNS Leak Protection is turned on.
Would it be possible for a wifi owner in charge of a router to see what you are specifically doing on apps on your phone? (Please note, my network gives a warning that encrypted DNS traffic is blocked).
Possible? Yes. Likely? No way to know for sure, but I’ve never actually heard of a case of it happening. It depends on the tech abilities of the owner.