Stacking the deck in favor of your security.

I don’t think I can say it’s advisable, but it’s certainly understandable. Moving is no small task.
And you’re most certainly not alone.
Let’s review what it takes to be as safe as possible while continuing to use LastPass.
Become a Patron of Ask Leo! and go ad-free!

Using LastPass Safely
Ensure that LastPass’s “Password iterations” setting is 600,000 or more, change your master password, and add two-factor authentication to LastPass.
Regardless of which password manager you use in the future, change passwords to important (and even not-so-important) accounts and consider adding two-factor authentication to those as well. Be particularly wary of phishing attempts, which may use information from the breach to create convincing but fake emails.
“Minimal exposure to external threats” is misleading
We need to debunk this line of thought. We are all at risk. No matter how much you use or think you don’t use the internet and online services, the risks posed apply to everyone.
I discuss this in more detail in Why You — Yes, You — Are a Target of Hackers. I simply run into too many people who believe for a variety of reasons that they are not valuable enough for an attacker to care about. That’s flat out wrong.
The problem is, thinking that way often leads to lax security. And that’s asking for problems.
So, please, take security seriously. You’re at risk, just as we all are.
LastPass password iterations
There is an obscure setting in LastPass called “password iterations” that controls the quality of the encryption used by the tool. You’ll find it in the advanced settings in your LastPass account online.
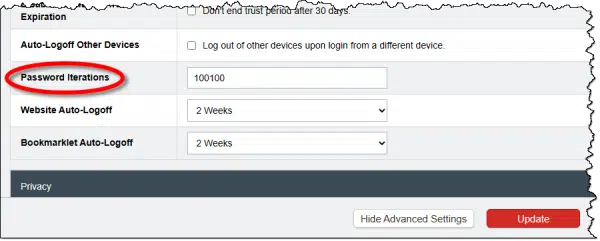
Ensure that this setting is 600,000 or larger.
While LastPass did change the default some years ago, older accounts were created using a lower number and were never instructed to update. The result is the encryption used may be somewhat more vulnerable to some forms of attack. Updating that setting resolves this issue.
LastPass has instructions here: Change your password iterations for LastPass.
Change your master password
Particularly if your password iterations were less than 600,000, it’s time to change your master password.
It’s unclear if changing your master password alone is enough to force your entire database to be re-encrypted,1 but apparently changing the password iterations will.
So do both. Select a new, secure, master password, and change it. Then, even if you were at 600,000 iterations, change it to 600,001 to force re-encryption. Make sure to also use this opportunity to create or update any account recovery options associated with your account.
LastPass has instructions here: Change your master password.
Change passwords for “important” accounts
While we’ve increased our security moving forward, none of what we’ve done so far addresses the damage done by the breach.
That’s because the damage has already been done. Vaults containing your passwords are “in the wild”, and hackers could be trying to decrypt them as we speak. There’s no clear indication of how likely it is that they’ll be successful. Assuming LastPass has done encryption properly, and assuming your original master password was sufficiently secure, then access to your account information is highly unlikely.
But not impossible.
Thus, I recommend you change passwords to any “important” account that you had stored in LastPass at the time of the breach. This would include banking, accounts containing sensitive information, and of course the email account(s) you use for password recovery on any of your accounts. Naturally, make sure you choose appropriately secure passwords.
This is the painful part, because it really does mean visiting all those accounts and performing manual password changes. But it’s the only way to address the direct risk associated with the breach.
And this applies whether you continue to use LastPass or not.
Add two-factor authentication
Add two-factor authentication to any of your accounts that support it. This’ll protect your account even if you don’t change the password. (But you should change the passwords anyway.)
That includes adding two-factor to not only LastPass itself, but to those important — and perhaps even not-quite-as-important — accounts as well.
As always, when you set up two-factor authentication, make absolutely certain to create and save account recovery information along the way. This will be critical to regaining access to your account should you ever lose or have a problem with your second factor. Recovery is easy in these situations, but only if you’ve saved that recovery information.
Watch account activity
This is always nebulous, but watch your various accounts for unexpected or suspicious activity.
This could mean that the account has been compromised in some fashion. Again, ensure you’ve secured the account appropriately, including that all-important password change.
Watch for phishing
This is perhaps the most important action you need to take resulting from the LastPass breach, and it applies whether you stick with LastPass or not.
The problem is that some information included in the breach was not properly secured — specifically the URLS of the services you use, and potentially even your usernames with those services. That means that hackers can use that information to create highly targeted and convincing phishing emails in an attempt to get you to hand over the piece they didn’t get: your password.
You should always be skeptical and keep an eye out for phishing attempts. The LastPass breach just made it that much more important.
Do this
Obviously, my bottom-line recommendation remains to switch to a different password manager that hasn’t lost our trust.
But I also understand that can be an annoying and painful process.
The steps above — many of which apply whether you stay or switch — should help decrease the risk of continuing to use LastPass moving forward.
While you’re thinking about security, why not subscribe to Confident Computing? Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: While I can’t confirm this about LastPass’s implementation, it’s common for the master password to be used only to encrypt a long random number, which is the true encryption key for your vault. This allows you to change the master password without having to re-encrypt the entire vault.




After many years of using LastPass, the second security breach shattered our trust in their operation. Following Leo’s advice, we bit the bullet and changed. We exported our vault files from LastPass into a CSV file. Then, we installed BitWarden and imported our exported Vault files into it. I was surprised by how seamless this operation was! Now that we’ve been using BitWarden for several months, I prefer it over LastPass. It is easier to get it to auto-fill the password data, and its interface feels more straightforward than that of LastPass. My BitWarden premium membership fee is about the same as I was paying for LastPass. In addition, BitWarden’s customer assistance has been much better than we experienced with LastPass. BitWarden customer service has been very responsive to our questions.
+1 for Bitwarden for all the reasons cited by Rene. Although I cannot fathom anyone being so lazy as to willfully elect to keep using a breached password tool vs spending maybe 30 minutes changing the important passwords and making the switch.
I continue to use LastPass since I had a very long Master Password (28 characters) even before the breach but changed it afterwards just to be safer. I did change the passwords for my important accounts even though they were all more than 16 characters to begin with. I’ve not encountered any problems with my accounts including phishing emails so far (knock on wood).
I can tell you that when I changed my Master Password, LastPass popped up a message informing me that it would re-encrypt my vault based on the new Master Password. So evidently changing the Master Password or the iterations number causes a re-encryption. I had changed the iterations to 600,000 before the breach & that caused a re-encryption. I’ll follow Leo’s suggestion & up that number higher.
Like Ron (above), I’ve elected to remain with LastPass (for now). I honestly believe in the ‘Three strikes and you’re out’ theory. LastPass has two strikes against them now.
I’ve increased my vault’s iteration count to at least 600,000 as recommended by LastPass and I took the time to go through all my accounts (one at a time). For those accounts I use or need to keep (for any reason) I changed the password to a new one with at least sixteen characters and enabled 2FA where it’s supported. When I encountered a site that does not support 2FA, I contacted the webmaster to ask why. For those sites whose answers were either not forthcoming or sounded like so much Blah-blah-blah, I requested that my account and all related information be closed/deleted. All but two complied. For those two, I ‘updated’ my account information with false data (I took the time to create a ‘temporary’ gmail account and then deleted it after I finished going through my vault). For the accounts I don’t use/need, I requested it be closed/deleted. All but one (NewEgg, but that is an entirely different story) have complied. After I received confirmation that an account has been closed/deleted, I then removed it from my vault (I moved the accounts to be closed/deleted to an ‘action needed’ folder to keep track of them). This process took about a week, working on the project in my spare time. I have no estimate for the amount of time I invested, but it was significant.
At this time, I am pleased to say that I actively use all my online accounts, and that they are all as secure as I can make them on my end, and that my password update project is completed. The effort, persistence, progress tracking, and patience required was more than significant. It was nearly overwhelming, but I got through it by working on one account at a time, step-by-step, with no planned completion time/date. I used a sticky note (the app that comes with Windows) to note the last updated account when I stopped work on the project to do other things so I’d know where to resume later. Even though the project involved a lot of effort, it was all well worth it in the end, and even if I have to switch password managers at some point the experience I gained completing my password update project will make the transition orderly, at the very least. I may post a step by step guide on my blog someday.
Ernie
Unlike Rene I find on Windows 10 Bitwarden fails to automatically fill the user name and password fields about half the time while Lastpass does it almost always.
Leo,
Thanks so very much for making your explanations and answers crystal clear. Short paragraphs. Short sentences. One or two syllable words. A minimum of geekeze. A major shortcoming of geeks is that they often — usually? — have difficulty communicating. (Read both the Challenger accident report and some of the online critiques of Mr. Borisjoly as he and his fellow engineers at TRW tried to convince management the night before the launch of the Challenger why it should not launch in cold weather. They failed to convince. Result: seven dead.) I may not always agree with you but I know exactly why you recommend what you do. Yours is a skill that must be consciously developed over time.
Thanks for your kind words. I’ll share them with my editor as well, since they’re partially responsible as well.
Thank you for this post, as well as the comments on BitWarden. I am old time LastPasser, paying only $12 / month for one more year. I had my wife try 1Password, but she didn’t like it. She knows how to use LastPass. But I was disappointed with the breach communication, was disappointed with a recent user-interface change, and disappointed I couldn’t even figure out the iteration that was listed here. I’ll have my wife try BitWarden so we can consider switching when my membership runs out in November
I change my Lastpass master p/w often, 14-20 digits because that results in a new encryption. Also increase the interations a little bit which also re-crypts. But mostly I have an active Yubikey. After entering name, p/w, a box appears and I must enter the code I created earlier. That prompts the Yubikey which I insert into a USB port, and since my code was correct, the key is active, so I press the button and my vault opens.
Foolproof? Of course not…! But I’m confident, until something better comes along.
My understanding is that simply changing your master password does NOT re-encrypt your database. (Though if you get a message that it is, then I’m wrong. Would love to hear if so.) The master password is used to encrypt a second key that actually encrypts the data, specifically so that you can change the master without forcing a re-encrypt. Changing the iterations, on the other hand, does force it. (I believe it’s the iterations that are used when this intermediate key is created.)
Hi Leo,
just t be sure… when you say to raise iteration to at least 600000, are you also saying that better to raise to say a million? Is there any adverse effect to the higher amounts?
Good work mate, and thanks. Mike
You could, and some things would get slower. I don’t thin there’s real benefit right now beyond 600,000 (other than, say, switching from 600,000 to 600,001 to force re-encryption).
I’ve used LastPass for many years & decided to move to Bitwarden. I’m still in “transition”. The export / import csv process failed miserably. The problem seems to be the way text in the Notes field is converted. I ended up with most of my records been split up into multiple separate entries in Bitwarden. I’ve had to systematically work thru each entry in LastPass, find the corresponding entries in Bitwarden and merge them &/or fill in the blanks from LP. Took several days to do. I still have many hundreds of orphan fragments that still need to be reviewed and deleted.
Then I need to move my wife’s account across from LP to Bitwarden….
LastPass has a feature to roll back your master password to the previous password. This implies they maintain a record of the hash and either an older version of the database blob or they maintain 2 versions of the database blob.
Before purging records & deleting your LastPass account, it seems prudent to:
Change master password
Delete entries in LP
Change master password again
Leave a bit of time between these steps so local info syncs to LP cloud & backups.
That way anyone who has cracked you master password from an old backup – possible if your password was weak / short & iteration count low (cough… my wife) will not be able to reactivate your account.
LastPass doesn’t store your password. To revert to a previous password, LastPass reverts back to the previous vault. It’s the same as restoring from a backup. Since it rolls back to a previous vault, all passwords added or changed since that version are lost. It can be a useful feature.
Well, LastPass now has offered a discount to come back. My wife needs something bad, and she doesn’t want to try something new. So I signed her up for a family plan, and will join her in November when my 13 years of $12 / year finally runs out.