The worst is none at all.
I’ve long been a proponent of two-factor (2FA) or multi-factor authentication (MFA). Most commonly it means that in addition to “something you know” — your password — you must also be in possession of something specific — often referred to as “something you have”.
When you have a choice, what should you choose?
Let’s compare the options.
Become a Patron of Ask Leo! and go ad-free!

Dedicated hardware devices are typically the most secure two-factor authentication alternative, but also possibly the least convenient. Google Authenticator and compatible apps are more commonly supported and more flexible. SMS and voice messaging, as well as email notifications, are all viable alternatives as well if Google Authenticator compatible two-factor isn’t offered. What’s most important is that you use two-factor authentication whenever you can.
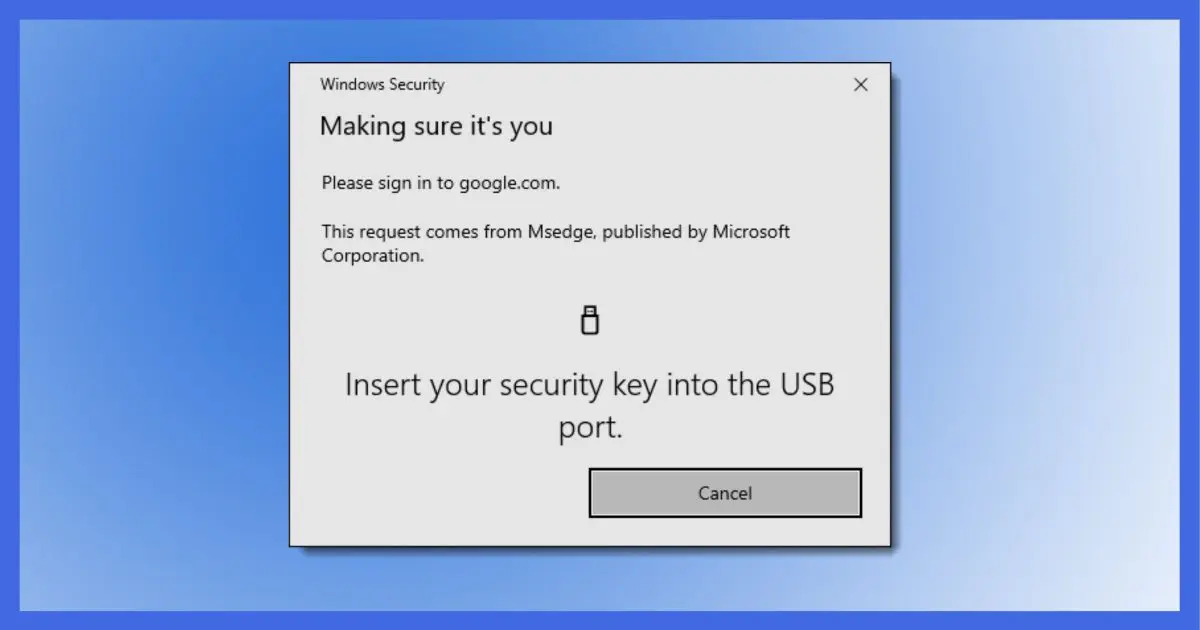
YubiKey or similar USB devices

YubiKeys are dedicated hardware devices specifically designed for two-factor authentication.
You associate your YubiKey with your online account when you enable two-factor authentication, typically by inserting the key and pressing the button on it when asked. The association is maintained uniquely and securely through the use of cryptography. YubiKeys cannot1 be spoofed.
When it comes time to sign in, the site, service, or application prompts you to insert your key into a USB port and press the button again. Information is exchanged proving you are in possession of your second factor, and you can log in.
The YubiKey and devices like it are probably the most secure of currently available two-factor options. They’re also one of the least convenient, because — very much like a physical key — if you don’t have it, you can’t get in. Yes, that’s the point of two-factor, but as we’ll see, there are alternatives that are a little less inconvenient. Unlike the options that follow, YubiKey is something you purchase. (It’s typically between $20 and $50, depending on the model.)
Google Authenticator
Google Authenticator and compatible applications are an option if you have a phone or tablet running Android OS, or have an iPhone or iPad.
Conceptually, the application works much like a physical device. You associate the application with your account by scanning a QR code or entering a key. Then, when you sign into your account, you’re prompted to enter the numeric code being displayed by the application. Entering the number proves you are in possession of your second factor: the device that was associated with the account — your smartphone or tablet.
There are several compatible applications that can be used in place of Google’s Authenticator. Of particular note is Authy, which can be installed on multiple devices and synchronizes your authentication tokens across them. You can use any of the devices on which you have the Authy app installed to provide your two-factor code.
Google-Authenticator-compatible two-factor has become one of the most common approaches used by online services. It’s the most convenient for many people and is extremely secure. It’s what I recommend, and what I use myself when given the option.
SMS Text messaging
Texting uses any device capable of receiving an SMS text message as your second factor. You provide your mobile number to the service when you establish your account. At login time, a text message is sent to your phone containing a code. Your ability to enter that code when requested proves you’re in possession of your second factor: the phone.
Should you lose your phone you simply replace it and the number is ported to your new device. Future SMS messages, including two-factor authentication, automatically arrive at the replacement device.
SMS text messaging is generally secure, but it subject to a couple of risks. The most common is what’s called “sim swapping”. This is a social engineering attack where someone calls your mobile provider claiming to be you, and says that you’ve lost the phone. If they successfully impersonate you, your number is transferred to their device, and they start receiving your two-factor (and all other) text messages.
Voice messaging
Voice messaging is rare, but when available is a viable two-factor approach for anyone who doesn’t have a smartphone, tablet, or SMS-capable device.
Just like text messaging, when you attempt to sign in, your phone number of record is called, and an automated voice speaks a multi-digit code. Your ability to enter that code proves you have access to your second factor: the phone at that number.
Email messages
Many online services require you to have an email address for service-related communication. Many of those, including the email services themselves, allow you to configure an “alternate” email address as well.
When used for two-factor authentication, a message with a code or link is emailed to the specified address. Your ability to enter that code, or click on links within the email, proves you are in possession of your second factor: access to that email account.
Additional alternatives
There are a variety of additional, less frequently used approaches to two-factor authentication. Some that come to mind include:
- A dedicated device that displays a constantly changing number, much like Google Authenticator.
- Pre-printed lists of codes, each of which can be used once.
- Pre-printed grids of randomized numbers. At login time, you’re requested to enter the number at coordinate X/Y.
I’m sure there are others that I haven’t encountered.
Not an alternative
NOT using two-factor authentication should not be considered an alternative.
Even with flaws (SMS being the most common example), any two-factor authentication is better than not using two-factor at all.
Given that any approach to two-factor authentication adds barriers that attackers must overcome, choosing not to use it is choosing to make it easier to hack your account.
My preference
So, let’s finally answer the question: what’s the most “effective”? I’ll define effective as secure and convenient (or least inconvenient). From most effective to least, my answer would be:
- Google Authenticator for anyone with a smartphone or tablet. I recommend the compatible Authy app specifically, because it allows you to back up your tokens, and makes switching to a new device very easy.
- YubiKey for anyone needing the extra level of security that only a physical device can provide. This is overkill for most people, hence #2 on my list.
- SMS text messaging for those who have the ability to receive texts.
- Email messaging.
- Voice messaging, if supported.
- Almost anything other than no two-factor at all.
It’s worth pointing out that not all services support all techniques, so you may need to use something lower on the list than you might like simply because the service you’re using doesn’t support the others.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
Footnotes & References
1: I use absolutes (“never”, “cannot”, and so on) because that’s the pragmatic reality. Yes, it might theoretically be possible to reverse-engineer technology or brute-force encryption keys, but the fact is that it would take years, if not centuries, of computing power to stand a chance of success.




The hundreds of accounts we all have with assorted companies/services/websites vary in their importance. Some deserve the extra hassle of 2FA, some do not.
That said, I would have rated voice messaging higher. If it is linked to a land line then the account can only be accessed from your home.
With each flavor of 2FA, the rubber hits the road when something goes wrong – what is the fallback? Without understanding the fallback options, any decision is flawed.
I use YubiKey on my Google account. but one thing you forgot to mention, which is important, in relation to the YubiKey is this…
while one YubiKey will technically work, it’s unwise to only have one YubiKey registered to a account that uses YubiKey because it would be possible one could be locked out of your Google account if you happen to lose your single YubiKey. but with two Yubikey’s, which I have, I use one in general and keep the other stored in a secure location in case I happen to lose my primary YubiKey I can always use the other to log into my Google account. so with two keys if one gets lost/stolen… one can simply log into the account with the backup key, then remove the lost/stolen key from the Google account, then buy another YubiKey and register that on the Google account and then you have two YubiKey’s registered to your Google account once again and keep one in a secure location and use the other in general. this is much safer since it’s unlikely you would lose access to both of the YubiKey’s, assuming you store one of them in a secure location you know will be available to you should you happen to lose your primary YubiKey.
but sadly, not enough services take advantage of YubiKey and the like. but it does seem like the cost of those have went up a bit since I got mine (I just use the standard YubiKey’s (the blue ones)) at a discounted price where as currently they are a bit steep for two of them at about $49 as when I got mine roughly a couple years ago I think I paid around $36 for two of them, which is reasonable. but at $49 that’s a little steep if you ask me as I can’t see paying more than $40 tops for two of them. but for those who got the $, it’s still a decent option for increased security.
just on a personal level though… I never been a fan of non-Yubikey/email based 2FA. I don’t bother using smart phones for anything important in general either as, while that might be inconvenient for some people, it’s more secure to do all of your important stuff on a proper computer for example like a desktop/laptop. so nothing is tied to the smart phone should that stop functioning or someone steal it etc.
NOTE: YubiKey works on Linux (I use Linux Mint), but not by default. basically follow instructions under the “How can I setup my Linux instance for use with U2F?” section at the following link to get the standard blue YubiKey working on Linux (this works on Linux Mint)… https://www.yubico.com/authentication-standards/fido-u2f/ NOTE: if your running your browser (Firefox/Chrome) in a Firejail sandbox YubiKey won’t work. but a simple workaround is to load the browser normally, sign-in with the YubiKey, then close the browser and reload it under the Firejail sandbox and at this point you will still be signed in (since it will use the cookie from your previous log-in as long as you did not log out).
Great point. Everything digital needs to be backrd uo.
I understand the that SIM swapping is theoretically possible but wouldn’t the chances of it happening be infinitesimally small? First of all, the hacker would have to have the passwords of the accounts they want to hack into and know your cell number. They would probably have to know your birth date, home address, account number and/or other piece of information that a hacker wouldn’t normally know. My mobile provider always asks for my account number. I feel perfectly safe with SMS authentication, at least with my provider.
It’s funny that it’s called SIM swapping as this method isn’t only used with a SIM card. If I lose my phone and call my mobile provider, the number isn’t moved to a new SIM card, they send a new one. I once had an old phone number moved to a new SIM, but in the case of a lost phone, they would normally send a new SIM card. It would be much more common on a GPRS phone which doesn’t use a SIM card.
I’ve tried several authenticator apps and my personal favourite is the one by Microsoft.
With respect to YubiKeys, this is something I’ve been meaning to look at for some time but keep putting off for one reason or another. Isn’t procrastination grand? Based on the limited reading I’ve done so far am I correct in thinking one key can support multiple services?
Yes.
@ Len ; Yes, your correct that you only need one YubiKey and it will work on multiple services/accounts as there is no limit.
but… like I mentioned in my initial comment in here, you really need two of them at minimum otherwise I would say don’t bother using a YubiKey since it’s more risky to only have one registered to your Google account for example as if you happen to lose that single YubiKey, or it gets lost/stolen etc, it’s going to be a big problem regaining access to your Google account. but if you have two YubiKey’s, this will help ensure that does not happen. but obviously, during setup of the YubiKey on your Google account you need to register both YubiKey’s so this way both can be used to log into your Google account. so should one get lost/stolen etc, you can simply log into your Google account with the backup YubiKey, remove the lost/stolen YubiKey from your Google account, then you can buy another single YubiKey and register that on your Google account again so that there are two YubiKey’s registered to your Google account once again.
but like the article mentions, YubiKey is probably a bit overkill for the common person. but it is a nice peace of mind for someone who wants the best 2FA available and has a bit of $ to spare.
I don’t think you need two YubiKeys specifically. As long as you have some recovery mechanism, which boils down to any other two-factor approach, in addition to the YubiKey, you’re fine. Standard additions are things like your alternate email address, or a pre-defined set of one-time passwords created when you set up your YubiKey.
Leo,
I am retired from the Federal Aviation Administration. I do not have a smart phone or a tablet computer. I have a Windows 10 run desktop PC on a land line. I don’t have 2FA and use Norton to keep me secure on the internet. As of May 26, 2022, the government will require me to have 2FA through login.gov in order to log in to the OPM web site (and all other US Government web sites – Social Security, Medicare, etc.) I frequent.
I am on a budget so I wish to save money doing this 2FA thing. I have an extra USB flash drive stick. I learned that using an free app (e.g. predator) I can convert that USB stick to a 2FA key, thereby saving the expense of a YubiKey. Is that as secure as the Yubikey? Do you recommend some other app besides “predator” to get this done?
I also learned that there is a way to enable Google Authenticator on a PC for use of a key (How to use Google Authenticator on a Windows PC https://crgsoft.com/how-to-use-google-authenticator-on-a-windows-pc/).
I realize that I can set up 2FA without a key by going the landline called voice code or e-mail sent code route, but I think the key would be more secure.
What do you think?
I’m not at all familiar with “predator” or how it operates as a 2FA key. I would prefer to use 2FA on my PC. The link you provided looks like a reasonable approach, though I’ve not tried it myself.
True, but it defeats the purpose of using a YubiKey in the first place which is to have the most secure 2FA available tied to your Google account since if you enable weaker 2FA options as a backup in case you lose your YubiKey it defeats the purpose of using a YubiKey in the first place which is to have the most secure 2FA available as the only way to access ones Google account. so with only two YubiKey’s tied to your Google account for example, your solely relying on those for gaining access to the account which is more secure since there is no way around the YubiKey 2FA which there would be if you enable weaker 2FA options as a backup to the YubiKey.
so that’s why I said to either buy two YubiKey’s (and only use them as a sole means of gaining access to ones Google account) or avoid them altogether and stick with more standard 2FA options.
Using SMS to my cell phone will fail when I travel internationally (not a problem now, I admit). I get a new SIM card and a local number for the foreign country. I fon’t know the new number until it is assigned. Does Google Authenticator work on a laptop?
The google-authenticator compatible Authy does. (And Google Authenticator will also work on your mobile device anywhere — it doesn’t require a network connection.)
A recent Leo Article talks of the importance of performing test recoveries of your backups. The same is true of 2FA!
The 2FA that works so well at/near home may let you down in a new location or when you use a ‘foreign’ device. I was locked out of my bank account while in Europe when the bank could not send SMS messages to my cell phone there. (Long story. Anticipating issues, I had disabled 2FA on the account before departure , only to have the bank reinstate it without notifying me. Now I have a different bank.) Fortunately I tested upon arrival abroad, and had time to set up access to another financial institution.
Try to insure that the account provider has multiple ways to give you 2FA on your accounts – in particular – have the possibility of getting a code by email to a secure email account. You can find email access in most parts of the world. And test that all the 2FA access methods your provider advertises actually works for your account!
Good points. My European bank has an app for 2FA so it’s not dependent on SMS. And my Bank of America app works anywhere as long as it’s on the phone it’s been installed on regardless of the SIM card installed.
I agree with all but one thing. My only exception would be Yubikey. I left mine at home one day and the site allowed no other way to access it. My key now hangs on my keyring. But it is a pain to use…not user friendly. And if someone takes it they can access your sites. It is not finger print specific. It only needs any finger press. I would rate it lower because of user friendliness.
“if someone takes it they can access your sites” — technically not true. They would ALSO need your account ID and Password.
Check whatever site you’re using it with to see if there’s a backup plan for losing your YubiKey. There should be.
@ Ron ; at least with Google that’s not true as you still need your username/password to sign-in. so even if someone has your YubiKey they can’t get into your account without also having your username/password, which they likely won’t have. so your still safe even if you lose your YubiKey.
but that’s the whole point of YubiKey is it being the only way to get into your Google account for example (along with your usename/password like usual). because if there are ways to bypass it, then there really ain’t much point in using a YubiKey in the first place. that’s why I say to either register TWO YubiKey’s to your account, or don’t bother using the YubiKey. this helps ensure maximum security (which is the whole point of YubiKey to begin with is to get maximum security) and gives you some insurance to in case you happen to lose one key, you can access the other (which you should be storing in a secure place). then just log-in to Google, remove the lost/stolen key, then buy another and register that. so then you will now have two YubiKey’s registered to your Google account once again.
Personally I would avoid SMS in general if people are concerned with security given recent articles like this… https://krebsonsecurity.com/2021/03/can-we-stop-pretending-sms-is-secure-now/ (later in the article it mentions some tips for securing ones accounts which seems to be to don’t use SMS or phone calls and remove phone number from accounts etc)
that article I linked to says… “The most common way thieves hijack SMS messages these days involves “sim swapping,” a crime that involves bribing or tricking employees at wireless phone companies into modifying customer account information.” ; so given that info, I would imagine the common user is probably not a high risk to use SMS and will probably do more good using SMS than not for some people. but, just on a personal level, I am not a fan of SMS as the risk is not super low as it appears it’s the easiest thing to exploit for shady people out there so I just remove it from the equation.
so personally I just outright don’t use SMS and just be more cautious on entering ones username/password in general as, like I have heard others say, if you did not seek something out, just assume it’s a scam, then manually go to the website in your browser by manually entering it. so if you get a email (or if some random site out of no where asks for something you did not seek out) asking you to ‘click here’ to sign in etc, just assume it’s something shady and don’t do it.
so for me I would be more along the lines of something like…
1)YubiKey (but this is not free and is much more limited on what supports it, but for what does support it, it gives maximum security assuming you using two of them as the only means to sign-in etc).
2)Email (I figure this is especially secure (and seems more convenient than using a additional application like my option #3 below) if you got only Yubikey’s as a way to sign-in to ones email with no way to bypass the Yubikey which is the whole point of using YubiKey’s in the first place is for maximum security. because as the saying goes, “your security is only as strong as your weakest link”.)
3)Google Authenticator (and the like) (I personally don’t use stuff like this but this seems like it’s pretty much secure unlike SMS.)
after those three I would probably just avoid 2FA personally (assuming your being a bit cautious (although I would imagine some would argue even with being cautious that some 2FA is better than no 2FA and it’s plausible they are correct to)).
but as a general rule for me… I never use smart phones for doing anything important online even though I do realize many will just because it might be convenient for them and I would guesstimate there are probably many people who only have a smart phone for online access. so they might not have much of a choice and then stuff like Google Authenticator (and the like) becomes more appealing.
but I understand why the article lists YubiKey a bit lower as it’s not free and can be a potential inconvenience (but personally I don’t really see it any more inconvenient than programs like Google Authenticator etc (I generally avoid doing anything important on a smart phone as a general rule which further lowers my risk)). but I figure if your already using 2FA there is some level of convenience the user is willing to accept already, so I figure why not go for YubiKey (two of them at the minimum as the only way to get into ones account(along with usual username/password)), especially if you don’t mind spending a bit of cash for maximum security (even though like the article said, it’s probably a bit overkill for the common person. but I like the peace of mind 😉 ).
just for me personally I generally opt for Option 1 or Option 2, otherwise I generally avoid 2FA. I figure if one is generally cautious it’s not necessarily a bad idea to not use 2FA. but I can easily understand the reasoning why any 2FA is a good idea for the common person, since many of those types don’t really care much about security in general. but at the same time, someone who does not really care about their online security in general, probably won’t be using 2FA unless they got burned in the past or it’s semi-force on them etc.
but that’s all for now as I mainly made this post so others could see a recent article on saying why SMS is generally a bad idea.
SMS is vulnerable to SIM swapping BUT in order to use SIM swapping to hack an account: First of all, they would need to know who you are and target you specifically and also need to know your account password. I don’t see that as significantly more vulnerable than losing a Yubikey. In other words nearly zero for the average person. Only a friend, enemy, relative, or co-worker would be capable of this kind of hack. If you are a public figure, boss, or log in to those accounts at work or on public computer (danger of keylogging), SMS can be a risk.
You lost me at “after those three I would probably just avoid 2FA”. ANY two-factor (INCLUDING SMS) is better than no two-factor. In fact, I even wrote about that: Why ANY Two-Factor Is Better than No Two-Factor at All.
I cannot recover my account
We cannot recover hacked accounts, lost or forgotten passwords. Please see this article for more information on your options:
https://askleo.com/would_you_please_recover_my_password_my_account_has_been_hacked_or_ive_forgotten_it/
If this is a Hotmail, MSN.com, Live.com or Outlook.com account, then this article discusses recovery options for the various ways that these accounts can be lost or compromised:
https://askleo.com/what_are_my_lost_hotmail_account_and_password_recovery_options/
If this is a Facebook account then please see:
https://askleo.com/how_do_i_recover_my_facebook_log_in_password/ and/or
https://askleo.com/how-do-i-recover-my-hacked-facebook-account/
Unfortunately, if you no longer have access to the recovery email account and phone number, your account may be lost forever. It’s important to always keep these up to date on your account.
https://askleo.com/a-one-step-way-to-lose-your-account-forever/
I have been using Authy for a few years now, in part based on your recommendation. One aspect I particularly liked about Authy was the Desktop application option. I frequently travel overseas and I am always concerned that I could lose my phone at anytime, and hence access to two factor authentication. Authy provided multiple device support, including a laptop application (which I used as a backup for my phone). However, this morning I received an email from Twilio Authy advising that the Desktop application will reach end of life on 19 March 2024. Do you have any suggestions for any alternative backup strategies? I do record Backup Codes (stored in my Password Manager), but they are not as convenient as the Desktop application.