Whole-disk encryption is a form of data security that encrypts all the data on a hard disk, irrespective of what that data might be.
Encryption and decryption happen at a low level, making it transparent to normal usage. As long as you’re able to log in to your Windows machine, you’ll have access to everything on it as if it were unencrypted. Turn the machine off, and the data is inaccessible and securely encrypted until you sign in again.
Low-level encryption and decryption can happen either by the hard disk itself, as data is read from or written to the drive (hardware encryption) or by Windows (software encryption).
The problem? Some drives using hardware-based encryption have been discovered to have vulnerabilities that could allow encrypted data to be exposed.
Become a Patron of Ask Leo! and go ad-free!

- BitLocker is available only in certain editions of Windows — for all others, this is a non-issue.
- Some drives have vulnerabilities in their whole-disk encryption implementation.
- You can check to see if your BitLocker encryption is using hardware encryption.
- If it is, consider converting to software-based encryption instead.
Windows Editions
BitLocker, Microsoft’s encryption technology, is available in Windows 10 versions I refer to as “Windows Pro or better”. That means all editions other than Windows Home, or, conversely, only on the Windows Pro, Enterprise, and Education editions. (I refer to “Pro or better” because specific editions can change. Windows editions seem to come and go, but they all seem to fall on either side of that “Pro or better” delineation.)
Thus, if you have Windows Home, there’s nothing for you here. The vulnerability being discussed involves the hardware encryption that may or may not be present in your disk drives on your machine. If you’re interested in full disk-encryption, a tool like VeraCrypt would be fine, and because it’s a software-based solution, it should also side-step the issue.1
Vulnerabilities
The Register published an article titled Solid state of fear: Euro boffins bust open SSD, BitLocker encryption (it’s really, really dumb). The headline is both misleading and inflammatory (as is the body of the article, to be honest), but the meat of the issue is very real.
BitLocker is not at fault. The drives themselves are. And yes, it is kinda dumb. Quoting The Register:
…you can seize a drive and, via a debug port, reprogram it to accept any password. At that point, the SSD will use its stored keys to cipher and decipher its contents. Yes, it’s that dumb.
BitLocker’s mistake, if you want to call it that, is to trust that hardware encryption was implemented properly. Clearly, that’s a bad assumption.
However, BitLocker can be instructed not to make that assumption.
First, let’s see if you have a problem at all.
Checking for hardware encryption
To run a Command Prompt in Administrative Mode, right-click on Start and then click on Command Prompt (Admin).
In the resulting Command Prompt window, enter the command:
manage-bde.exe -status
Followed by Enter. This will print a short report for each drive internal to your system.
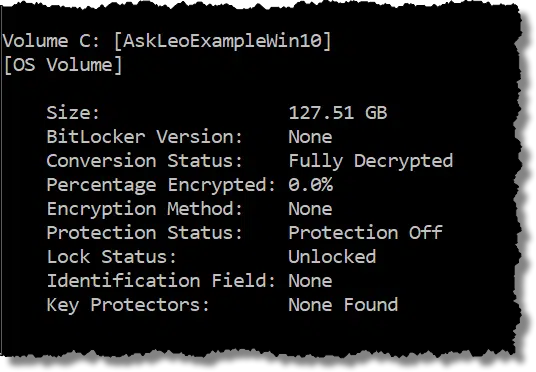
In the example above, “Conversion Status: Fully Decrypted” indicates that this drive does not have BitLocker full-disk encryption enabled.
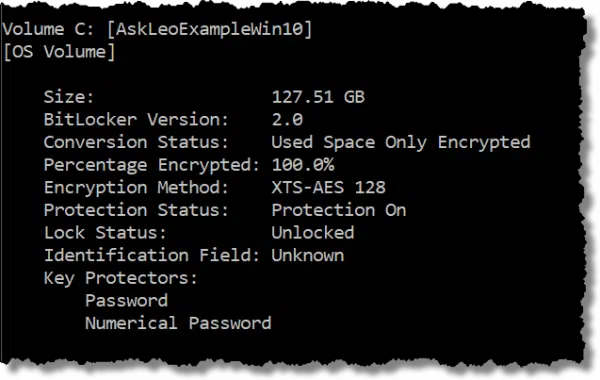
In this example, “Conversion Status: Used Space Only Encrypted” indicates that only actual files, and not free space, have been encrypted on the drive.
More importantly, though, “Encryption Method: XTS-AES 128” indicates software-based encryption. If the drive we’re using has the vulnerability we’ve been discussing, it doesn’t matter — we’re not using hardware-based encryption.
If the encryption method were listed as “Hardware Encryption”, BitLocker is relying on the drive to provide the encryption. If that drive suffers from the vulnerability, your data might be at risk of exposure.
Converting hardware- to software-based encryption
It’s a somewhat time-consuming process, but you can convert BitLocker whole-drive encryption that uses hardware encryption to use software encryption instead.
Prevent hardware use
First, run “gpedit.msc”, the Group Policy Editor. Once open, navigate to (expand each node in turn by clicking the “>” to its left):
Computer Configuration
> Administrative Templates
> Windows Components
> BitLocker Drive Encryption
> Fixed Data Drives (optional — seems to be present only on some systems)
There, look for “Configure use of hardware based encryption for fixed data drives”.
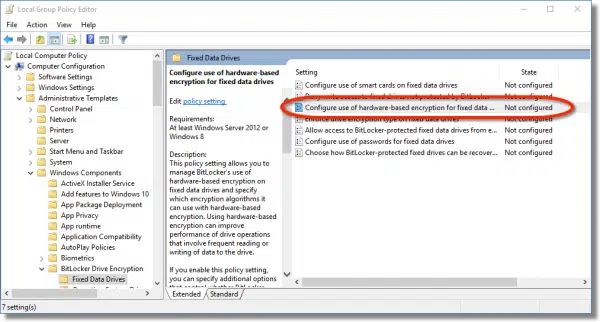
Double-click on that to open it.
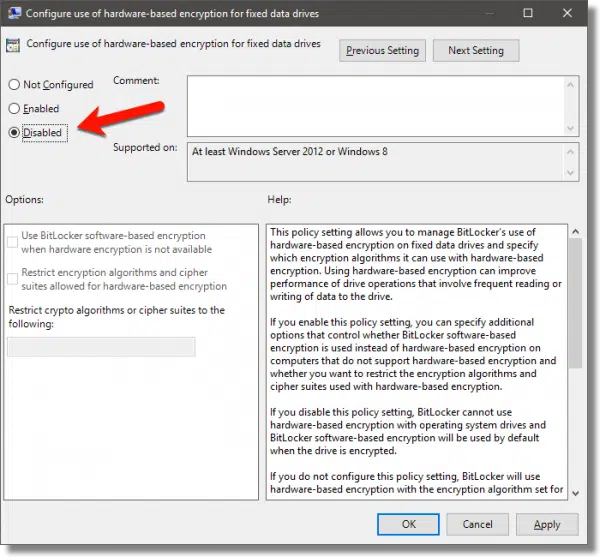
Change the setting to Disabled, click OK to close the dialog, and close the Group Policy Editor.
Re-encrypt the drive
Re-encrypting the drive means nothing more than turning encryption off and then back on again.
Right-click on the drive in Windows File Explorer and click on Manage BitLocker.
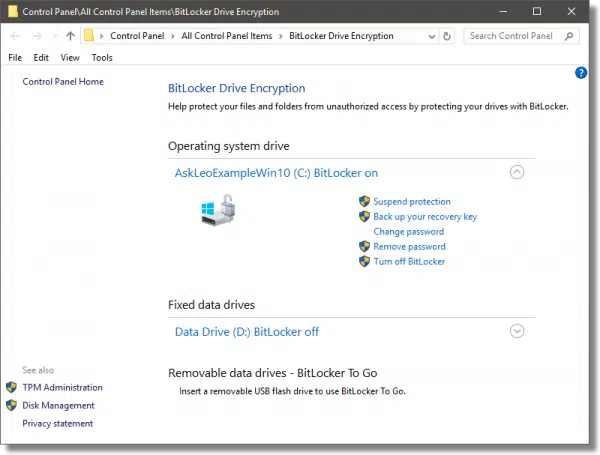
Click on Turn off BitLocker. After confirming this is what you want to do, the drive will be decrypted in place. This may take some time, depending on the size of your drive.
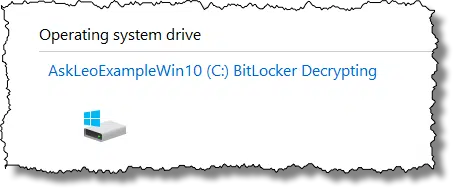
When complete, the status will change from “BitLocker Decrypting” to “BitLocker off”.
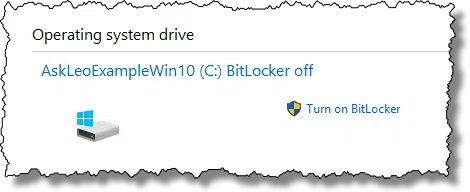
Click on the “Turn on BitLocker” link to begin the process of encrypting the drive. Because we disabled the option to use hardware encryption, software encryption will be used.
Is there a downside?
One of the reasons hardware encryption is lucrative is that it doesn’t place an additional computational load on your computer’s processor. Since we’ve taken that option off the table, your computer will be doing the work of encryption and decryption.
In theory, you could notice a small performance degradation, depending on the characteristics of your computer. In practice, it’s unlikely you’ll notice a thing.
And even if you did, the extra security of encryption that actually works is worth it.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!




What software do you recomnend to encrypt files archived on a 1TB external HD?
As Leo mentioned in the article, Veracrypt is good for that.
That, or BitLocker. We’ve done that at work.
“And even if you did, the extra security of encryption that actually works is worth it.” – Hmmm. This should really be put in perspective. This issue isn’t something that the average home user needs to be the least bit concerned about. To quote Micron, “This vulnerability can only be exploited by an individual with physical access to the drive, deep technical SSD knowledge and advanced engineering equipment.” Unless you’ve got state secrets or super-valuable IP on their system, it’s very, very VERY unlikely that you’ll ever be targeted by such a person. In fact, it’s pretty much a near-zero chance. Your collection of cat photos, emails from your mother-in-law and even your tax returns simply aren’t that interesting.
Sure, go ahead and make switch to software-based encryption if you’re completely paranoid; otherwise, you really don’t need to worry about this. It’s very much a non-issue for Joe Average.
I originally thought the same thing but when I thought about it, anybody who uses encryption in a business might be interested in this advice. A business might want to protect against rogue employees. You’re right about the average home user but there are definitely many readers who would benefit from this advice.
Sure. My point was simply that this is a complete non-issue for home users. It’s not something they need to be worried about and there’s really no reason at all from them to switch from hard to soft encryption – especially as it’ll involve a small performance hit.
“The average home user” is most like likely using Windows Home, which Leo clearly states is not affected by this issue. I also don’t think Leo’s readership is limited to “home users”. There are lots of us who are home users that run businesses out of our home, are users that run small businesses out of an office, support business clients, etc., AND we aren’t dealing with Windows Home, AND we use encryption. Whatever one’s reasons for using encryption, they obviously feel it’s important. If it’s important enough to use, it’s important enough to rely on it, and this article addresses that reliability. I think Leo’s comment stands as is, without qualification.
What happens if my laptop dies? How can I still decrypt the data on the SSD?
A former boss had her laptop die and the bitlocker-encrypted hard drive was unrecoverable on another machine.
Don’t know more details than that but it was enough to scare me off that option, especially for a laptop. Instead, I use VeraCrypt to create a partition/drive within that hard drive and store ALL of my data in there. There rest of it (OS/apps etc) is reloadable/re-installable and I could care less if it needs to be re-installed.
*AND*, I know with complete confidence, (barring disk error) that I could still unlock/access my encrypted data if I had to move it to another machine.
If someone knows more about bitlocker and is able to explain how/if there’s a way to make the encrypted drive machine-independent, I would love to hear about it – or even a link that explains it further – or even a clarification if I’ve misunderstood something.
Thanks.
When you set up BitLocker on the drive you’ll be prompted to save a certificate/key. SAVE THAT KEY. It’s used, then, later to access the contents of the drive when attached to another system.
Perhaps more pragmatically: BACK IT UP. So that you don’t have to access the data on the SSD, and can simply reformat it and start over.
Ahhh, the certificate/key was the missing piece. Thanks for that!
Yep, she lost that piece and therefore lost the data.
She made the faulty assumption that the I.T. group was backing up her local data remotely to the network – nope.
It can’t be over-stated but it’s stunning to see the number of people who don’t back up their data – from any of their devices.
If anything, the abundance of free/accessible cloud storage should make it simple for even the most rudimentary periodic copy, never mind copying to cheap external storage drives and USB sticks.
If you back up to the cloud, don’t forget you’d need to encrypt that data with a program like Cryptomator or Boxcryptor. They would be doubly encrypted on your hard drive but if you don’t encrypt them, they remain unencrypted on the public computers of the cloud.
Agreed – you guys put me onto Cryptomator – crazy-easy to use and now I have it on all of my machines.
It’s a beautiful thing!
And thanks to you guys for gems like that!
I did not have a good experience with Bitlocker and here is why. Windows 10’s update policy and its sloppy debugging left me unable to properly boot my computer. I have several computers and the one that was hosed by an update error cobooted into Ubuntu, so I limped by for 3 months going up to 3rd level MM support. I really wanted them to find the error because it prevented any user from going to any future updates.
They couldn’t get me out of the mess. I had to wipe the disk clean. But I couldn’t find my Bitlocker key! Fortunately, I had a cloud backup. This was related to the fast boot option. Once a bad state is stored, you are in jeopardy of never getting to a good start. So a corollary of being careful to have a realtime nonbitlocker backup is to turn off fast boot.
Yes, I strongly recommend unencrypted backups of the data which are then secured in some other way, regardless of whether the whole-disk encryption process has been smooth as silk, or problematic. There are just too many ways things can go wrong and data can end up being lost otherwise.
Still using the pre NSA TrueCrypt version whole disk encryption. Easy peasy. It is still good enough and I am not that interesting. Just do not feel like climbing another learning curve to split hairs on the best encryption.
It’s probably better to switch over to VeraCrypt. TrueCrypt is no longer supported and may have some unpatched security vulnerabilities. VeraCrypt is the replacement for TrueCrypt and the learning curve is minuscule.