Probably not.

This can get confusing quickly. Most backup tools back up files in their unencrypted form. That’s what I recommend, and the tools I recommend do it that way by default. However, some situations and choices can cause data to be backed up in encrypted form.
Encyrption can happen to entire disks or individual files. Let’s look at how that happens and what you might want.
Become a Patron of Ask Leo! and go ad-free!

BitLocker Backup Basics
Most software operates on files as they appear to you. Therefore, backups from a BitLocker-encrypted drive typically store files in an unencrypted form. Exceptions include sector-by-sector backups and backups made without signing in, both of which can only back up as encrypted. Make sure your backups are accessible, and then choose secure storage or program-specific encryption to protect them.
How disks arrange files
A disk is comprised of sectors of information. A sector is just a fixed-size block of data — say 512 bytes. When information is written to a disk, it’s broken into sector-sized pieces.
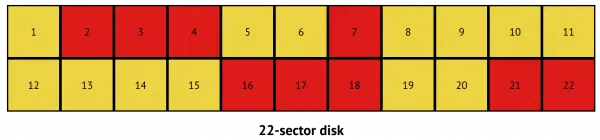
The example above shows a 22-sector disk. If each is 512 bytes in size, the disk has a capacity of 11,264 bytes of data.
The nine red squares (2, 3, 4, 7, 16, 17, 18, 21, and 22) indicate sectors to which data has been written. This represents 4,608 bytes of space used by data1, leaving 6,656 bytes of free space.
Note that the disk itself has no idea what those sectors contain other than that they contain “data”. This will be important in a moment.
Now let’s look at our disk, this time identifying individual files.
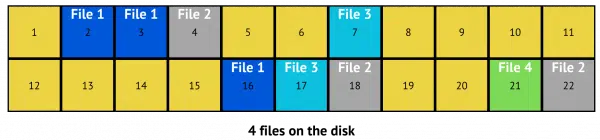
There are four files on this disk.
- File 1 is written to sectors 2, 3, and 16.
- File 2 is written to sectors 4, 18, and 22.
- File 3 is written to sectors 7 and 17.
- File 4 is written to sector 21.
When you access a file — say by opening up that file in a program like Microsoft Word — the operating system locates the various sectors containing the file and provides it to the program as a single file.

While the sectors are technically still there, the program using the file sees only a single file full of data.
With that out of the way, we can talk about encryption.
Bitlocker encryption
BitLocker (and other forms of whole-disk encryption) do their work by encrypting every sector on the disk.
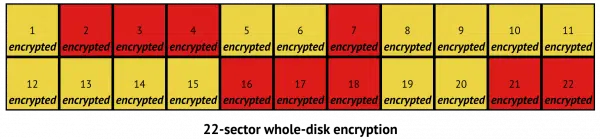
BitLocker has no knowledge of which sectors hold what or even if they’re holding files or not2; each sector is simply encrypted.
Again, when you access a file, as we did above, the operating system:
- Locates the various sectors containing the file.
- Decrypts each sector.
- Returns it all as a single file.

Similarly, if you write the file to a Bitlocker-enabled disk, the operating system:
- Figures out which sectors the file should be written to.
- Encrypts each sector as it’s written to disk.
From your perspective, the file is unencrypted; all the decrypting and encrypting happens at the sector level as the file is read and written from and to the disk.
Finally, we can talk about backing up.
Backing up data on an encrypted drive
As you use your computer, you see only unencrypted files. The data on disk is decrypted before you see it when reading the file and encrypted after you save it (when writing). This makes it easy for all programs to access the files on your hard disk whether the disk is encrypted or not. Those programs are just operating on files like they always have.
Most backup programs behave the same way: they operate on files that appear unencrypted. Even an image backup program operates without knowing or caring that data on the disk might be encrypted. It sees files, just like you do, in their unencrypted form. Hence, it backs up the files in their unencrypted form.
There’s one exception to this rule.
Of clones and sector-by-sector backups
To read the files on your disk, your backup software needs to understand how the disk is structured. That means it needs to understand the file system used, also known as the “format” of the disk, such as NTFS, FAT32, or others.
If the backup software doesn’t understand how the data is organized on the disk — perhaps something’s been corrupted or it’s a file system the backup program doesn’t understand — it may offer to do a “sector by sector” backup. This backs up the entire disk surface without regard to what it contains…
…or whether, or even how, it’s encrypted.
This type of backup is also called a “clone”, and you can also choose to perform this type of backup. It’s often used for forensic data recovery since it includes unused sectors as well as the exact sector-by-sector layout of the disk.
In this case,
- If the disk is encrypted, a sector-by-sector backup backs up the sectors, which are encrypted.
- If the disk is not encrypted, a sector-by-sector backup backs up unencrypted sectors.
Backups from rescue media
So far, I’ve assumed you’re signed into and running your backup software from within Windows. If your drive is BitLocker-encrypted, because you’re signed in, the files on it are accessible in unencrypted form.
If you boot from your rescue media (which launches a copy of your backup program) and attempt to make a backup image of your BitLocker-encrypted drive, we have a problem. You haven’t signed in to your PC, so the drive has not been mounted and cannot be decrypted.3
There are two options:
- Some backup programs notice that the drive is BitLocker-encrypted and ask you to provide the recovery key. This allows the backup program to mount the drive and back up unencrypted data just as if you had been signed into Windows.
- Back up the drive sector-by-sector.
The first gives you unencrypted backups. The latter results in an encrypted backup.
Dealing with encrypted backups
If you have an unencrypted backup, you can do what you like with it. You can restore it, extract files from it, whatever. The results will also be unencrypted.
But what happens if you have a sector-by-sector backup containing an encrypted BitLocker drive?
There’s little you can do with it other than restore it in full. That’s usually enough (for example, when swapping out a failed hard drive). Once you reboot and sign in, the BitLocker drive is mounted, and you can access it normally as before.
Unless your backup program can accept the BitLocker recovery key to decrypt the image, you cannot mount it using your backup tool to extract individual files.
What do I have?
The easiest way to determine what sort of backup you have is to try to look inside it. In many cases, that’s as simple as double-clicking the file containing the backup.
- If you can see its contents without specifying a key or passphrase, then it’s unencrypted.
- If you can’t, you may get a message about the contents being unrecognized or a message that the contents are encrypted.
- In some cases, the backup software may recognize the encryption and ask you for a recovery key or passphrase.
What about backup-program encryption?
Many backup packages allow you to password-protect your backups. This encrypts the contents of the backup files created by the backup program. This has nothing to do with BitLocker or other types of encryption on the disk you’re backing up. It’s just a way to secure the backups themselves.
You’ll need this password to access the backup later and either restore it or access its contents.
What about encrypted files?
If you have individually encrypted files — say a password-protected zip file or files encrypted by Cryptomator — nothing really changes.
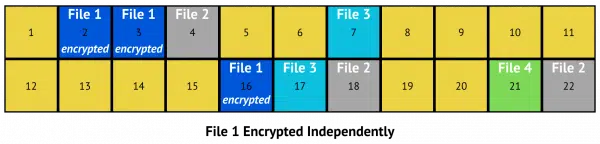
In the example above, File 1 has been encrypted by some external program. That each sector says “encrypted” is somewhat misleading because in this case, it’s the file, not the individual sectors, that have been encrypted. The entire file was encrypted before being written to disk, and it’ll be encrypted when it’s read from disk.

Everything discussed so far remains the same. If your backup program performs a sector-by-sector backup, you’d have to do a full restore in order to access the files. If your backup program is doing a more traditional file-by-file backup, then all the files are accessible, but the files that have been encrypted individually remain encrypted individually.
Those encrypted files have the distinction of being encrypted twice: once by whatever tool you used to encrypt them (Zip, Cryptomator, etc.) and again by BitLocker when written to disk. This is harmless.
Do this
Back up, of course.
I recommend you back up data in unencrypted form and secure it some other way for security. This could be keeping it physically secure (such as an external hard drive placed in a safe) or using a different form of encryption, possibly the encryption provided by your backup program. (This reduces the risk of two forms of encryption failing simultaneously: your original data stored in encrypted form and your backup of that data stored in a differently encrypted form.)
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




I wish I read this article before making changes, but even so I am not sure I still understand or misunderstand. I did two things. I turned off encryption on my machine (through Settings, .. and I do not remember all the path), and switched from sign-in with Microsoft Account to sign-in with Local Account. One day I hope I learn to make full image back-ups and rescue-boot disks, and not have any worry about bitlocker and keys.
That day should be today. This is a superstition of mine, but when I say I’ll fix it soon. That’s the time it decides to break.
Follow these instructions and set up a backup today:
Leo has a series of articles explaining the basics of backing up with EaseUS Todo. The articles are a bit old so there might be minor differences, but the principles are the same.
Download and install Easus Todo and perform step 1 “How to create an image in EaseUS Todo Free
1. https://askleo.com/how-to-create-an-image-backup-in-easeus-todo-free/
2. https://askleo.com/restoring-file-easeus-todo-image-backup/
3. https://askleo.com/restoring-image-using-easeus-todo/
4. https://askleo.com/creating-easeus-todo-emergency-disk/
5. https://askleo.com/saved-backing-up-with-easeus-todo-choosing-a-backup-strategy/
6. https://askleo.com/saved-backing-up-with-easeus-todo-the-image-reserve-strategy/
From the blue box: “backups from a BitLocker-encrypted drive typically store files in an unencrypted form”.
So, anytime you are signed into BitLocker then a malware that uses similar coding as a backup software can access your “encrypted” files.
Let that sink in.
And that’s 100% NOT WHAT WHOLE DRIVE ENCRYPTION IS FOR. Let that sink in.
It doesn’t even have to have “similar coding as backup software”. Any software running on your machine can access your files. THAT’S THE POINT.
Bitlocker protects you from forensic data recovery, hard drive theft, laptop loss and the like. Any access to your machine or hard drive when you’re not logged in.
As I’ve said for decades: if you let malware on to your machine, it can do anything. And BitLocker and other whole-drive encryption is not intended as protection against malware.
I use Windows 11 PRO on my desktop and primary laptop PCs, and Windows 10 PRO on my older Dell laptop PC. For a time I used Bit-locker on all three devices, but after encountering multiple non-critical issues (for the most part, the repeated need to enter my recovery codes for all the partitions I had encrypted), so I decided to remove it.
Now, I ensure that my computers are locked when I’m away and I keep them all as up to date as possible, both the systems with Windows Update, and installed software with Patch my PC. I now use 1Password (formerly LastPass) as my password manager, and I practice what I call Cognitive Security, a paradigm that employs a healthy dose of skepticism about anything that comes from the Internet, and downright suspicion about any hyperlink I encounter, either on webpages or in email messages. Before I click any hyperlink, I compare its URL with its label. If they don’t correspond, or I can’t understand/read the URL (e.g.: it looks more like some encrypted code than a web address), I don’t click. In some cases where I want to check out the purported destination of a hyperlink, I search for it using my web browser.
In any case, while I used Bit-locker, my backup images contained unencrypted copies of the content of the partitions I backed up. FWIW, I use Macrium Reflect Free here.
Ernie
Hi Leo,
A lot of my files are stored in my OneDrive for business folder, therefore, synced to the cloud. I back all my files up regularly to external hard drives. I use a .bat script that I wrote using “robocopy” to copy the files to external drives. If I encrypt the files in my OneDrive folders, will they also be re-uploaded to the cloud encrypted (so they are also encrypted on Microsoft servers), but the robocopy backup remain unencrypted? I would like to encrypt my files in case they ever get hacked online etc. Kind regards.
It depends on exactly HOW you encrypt them.
Nice article! I always appreciate the thought and detail that goes into these articles and the YouTube videos.
I’m backing up my Windows 11 laptop to my Synology NAS using Synology Active Backup for Business. This is an agent that runs as a service on my Windows machine. I’m backing up the entire C: drive that is encrypted with BitLocker. The backup itself is unencrypted since I can restore portions of it on the NAS without needing the BitLocker key. I created a bootable USB drive (running Active Backup for Business Recovery Wizard) to allow me to restore the entire C: drive. My question is can an entire system recovery be made to a disk that is BitLocker encrypted or will it be blocked from writing to it?
You would need to unlock or disable Bitlocker to do that.
This seems like a chicken and egg thing. When I booted off the recovery thumb drive I never was prompted to unlock BitLocker. I’m assuming that if I needed to restore the entire system drive, my system would be in a state that was not bootable (corrupted, etc) so I could not get to Windows to disable BitLocker. Running off the thumb drive I could bring up a CMD prompt but could not access C: because it was encrypted. Are there commands that I could run from the command line to unlock BitLocker on C:?
There are ways.
Example: manage-bde -unlock E: -RecoveryPassword YOUR-RECOVERY-KEY
but as you can see it does require that you have the recovery key available.
That’s great! Thanks. I can get the key from MS. I have done that before. It is a pain typing that whole key but at least it’s not very often. Thanks again!
It depends on the recovery software/technique. Some will overwrite the bitlocker encryption, resulting in an unencrypted drive, others will restore to the drive, but might require the recovery/access key in order to do so.