Phishing
All the “Ishings” Trying to Scam You
The concept of phishing has spawned a variety of “ishing” terms. They represent different ways scammers try to achieve a common goal: to scam you. I’ll review what they all mean.
Many Ways Your Account Can Be Hacked and What to Do About It
There are many ways accounts can be compromised. There are also many simple ways you can protect yourself.
7 Signs of Phishing to Watch For
A friend received a fairly convincing phishing attempt. I’ll cover the signs that showed it was bogus.
Social Security Number Compromised — What to Do?
Billions of records of personal information, including Social Security numbers, has been exposed. What to do?
Are Zip Files Safe to Open?
ZIP files are useful for compressing and containing collections of files. Unfortunately, they’re also useful to hackers, spammers, and scammers.
One-Time Code Contradiction: When to Share and When to Beware
You’re told not to share your two-factor or other authentication code. And then you’re asked for it.
Behind the Scam: Decoding the Secrets of Fraudulent Emails
Scam emails often have clues ranging from obvious to obscure. I’ll take a scam email and show you what I see.
How Can I Tell If a Web Address Is Safe?
URLs are simple in concept, yet can be constructed in ways that might fool you. I’ll look at some examples and discuss what’s important.
What Is a Pig-Butchering Scam?
Pig-butchering is a nasty term for a particularly painful type of scam. Here’s how to protect yourself.
Why Is There So Much Spam?
Even though most of us might never fall for it, the reason there’s so much spam is simple: spam works.
12 Steps to Keep from Getting Your Account Hacked
Here are the steps you need to take to prevent losing your account forever to a hacker.
What Is Smishing?
Smishing is simply text-messaging spam. Learn to recognize and respond appropriately to it.
The Biggest Risk to Your Security
The biggest risk to your security might just be you. Learn why and what to do.
I’m Told to Change My Password. Why?
If you’ve been told to change your password, do so, but do so in the right way. I’ll explain what that means and why it’s important.
Phishing: How to Know It When You See It
Phishing is a way scammers trick you into providing personal and financial details. Phishing opens the door to identity theft and more.
Five Steps to Better Security Working from Home
Security threats for people working from home are increasing. I’ll review steps you need to take to keep yourself, your company, and your job safe.
Are HTTPS Connections Really Safe?
HTTPS is an important part of keeping your data safe, but it’s only a part. It’s important to understand what it does and doesn’t mean.
Why Does Legitimate Email from PayPal Instruct Me to Click a Link?
The rule is, never click on links unless you are 100% certain that they are from who you think they are. The question is, how can you be certain?
What Is It About Attachments?
Email attachments are useful, ubiquitous, and convenient. They’re also abused, dangerous, and responsible for infections and data breaches.
Is Online Banking Safe?
You can bank online safely, as long as you know what to look for and what steps to take.
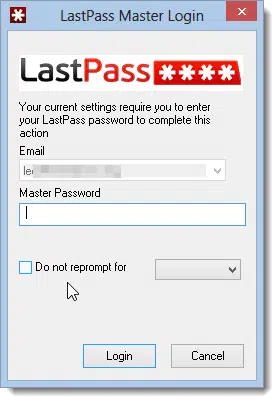
Possible LastPass Phishing Vulnerability
News broke over the weekend regarding a potential phishing vulnerability that could lead you to give a hacker your Lastpass master password.
Is My ISP Calling Me to Clear Up My Problems with Windows?
In a brazen scam attempt, you may get a phone call from someone claiming to be your ISP or other service provider to “help” you with your Windows problems. Don’t fall for it.
Should I take the security protection offered after the most recent security breach?
Hackers are very good at sending emails that look like they come from legitimate companies. So, how do you tell the truth from a lie?
Is the internet just full of scams?
Many advertisements of computer products include promises that they can’t keep, or know that they won’t keep. By making things seem much worse than they actually are they attempt to entice – or even scare – you into purchase tools you simply don’t need.
Why Does this Email Message Ask Me to Enable HTML When It Already Is Enabled?
Viewing an email in HTML seems to be the default in the new Outlook.com. There is no easy way to change it. So why are you seeing this message?