Don’t be fooled.

A friend recently asked me to look at an email they’d received to confirm if it was legitimate.
It was not.
It was a good attempt, though, and it probably fooled many people into clicking through and potentially handing over their sign-in credentials to a crook.
I’ll review some signs in this email that flagged it as fake.
Become a Patron of Ask Leo! and go ad-free!

7 Signs of Phishing
- The message is received out of the blue with no prior context.
- The message contains no additional explanation for whatever you’re supposed to click on.
- Bogus or meaningless filenames for promised documents.
- Incomplete branding, like a Microsoft logo with no mention of OneDrive in an email sharing a document.
- Your email address does not appear in the “To:” line.
- The message consists of an image of text rather than a mix of images and text.
- A bogus link destination, or a destination inconsistent with the promised document.
While any of these can happen in legitimate email, each should give you pause. Multiple instances in the same email should cause you to question the legitimacy of the message.
Our example
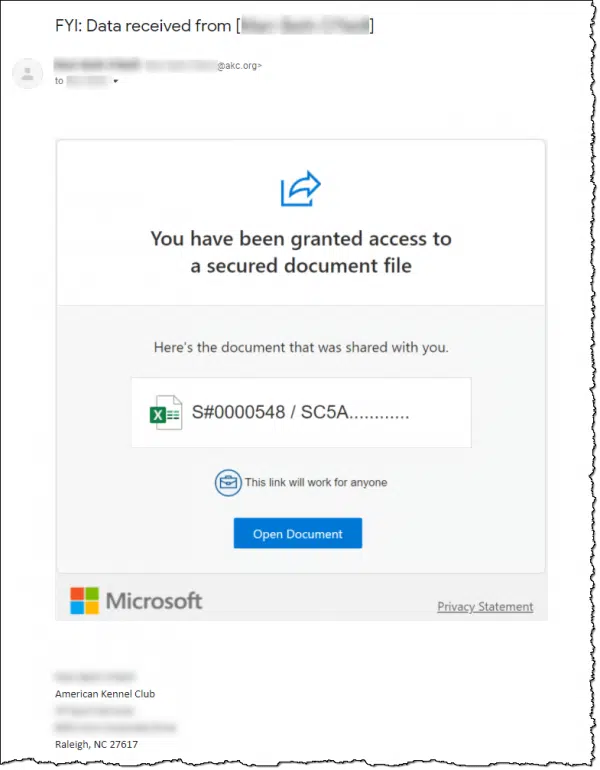
I’ve blurred out a few items for privacy, but:
- The blurred-out name in the “FYI: Data received from” subject line is someone my friend knows and has corresponded with in the past.
- The blurred-out name and email address in the “From:” line ending in “@akc.org” matches my friend’s contact.
- The blurred-out “To:” line is the same email address as the sender.
The email seems to contain a document shared by the sender for my friend to open and read. The icon suggests it’s a spreadsheet. Since it includes the Microsoft logo, one might expect it to be shared online in OneDrive.
And of course, the email closes with an official-looking business-like signature from the sender.
There are many lies in this message.
Clues you can use
It’s important to point out that these items are clues, not absolute indicators. All of them occur in legitimate emails as well.
It’s also worth noting that these clues are not unique to this specific phishing email. They are clues you can look for in any email you have second thoughts about.
1: Lack of preceding context
While my friend knows the sender and has had email conversations with them in the past, it had been months. There was no current email conversation between the parties. The email arrived completely unexpected and out of the blue.
2: Lack of included context
There’s nothing within the email message to give it any context. “You have been granted access to a secured document file”1 — great! But what does it contain? Why have I been given access? What am I supposed to do with it, other than the implication to open it?
3: Lack of an informative file name
Normally, files have names that indicate their content. “S#0000548 / SC5A” is (presumably the beginning of) a pretty uninformative name.
4: Microsoft logo without mention of OneDrive
Microsoft is not likely to share a link to a file on OneDrive without explicitly promoting the fact that it’s on OneDrive. Everything is a marketing opportunity, and that this wasn’t treated as such might imply that Microsoft was not really involved.
5: The email wasn’t “To:” my friend
The email didn’t show my friend’s email address at all; they were BCC’d. The email appeared to be sent from someone to themselves. This is often a red flag.
6: The entire box was an image
The entire box containing the “You have been granted” text, the document icon, the document name, the Open Document button, the Microsoft logo, and more was a single image. Clicking anywhere would take you somewhere. (The image might have been shown because it was included with the email and not a remote fetch, which is normally blocked, or because my friend had the sender’s address in contacts or as an “always allow images” setting.) This is one way spammers try to bypass spam filters.
A legitimate email is typically a combination of text and images, not just a single image that looks like text. Normally, only the “Open Document” button would be clickable.
7: The destination was bogus
Given that the email attempted to look like a Microsoft email (because of the logo) linked to a Microsoft document (the Excel-like icon) implying it would be shared on a Microsoft property like OneDrive, we’d expect the link to go to a Microsoft-owned domain. Hovering anywhere over the image showed that the destination URL was no such thing. It went to a domain similar to 48c0ef1.somerandomservice.com.
(I’m not mentioning the specific domain (somerandomservice.com is my own) because sometimes spammers own them, but more often it’s someone else’s domain that’s been hacked and put into service for this type of thing.)
Again, I have to point out that many of these clues occur in legitimate email. And some — like a bogus destination — are more strongly indicative of a problem than others. The important takeaway here is:
- All of these clues were visible. It just took a little time to look at and think about the message before acting on it.
- The presence of multiple clues strongly implies that this was a phishing attempt.
More clues you can look for
One of the first things I did when my friend asked me about this email was to look at the email headers you don’t normally see.
They were much longer than those shown above. The results were difficult to interpret, and to my casual eye, inconclusive at first glance.
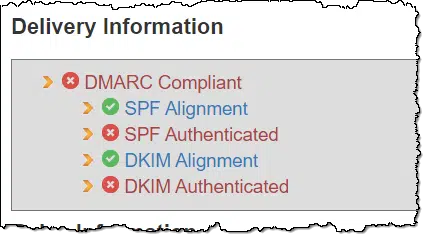
However, we have tools for this type of thing. MxToolbox has an email header analyzer. Copy/paste the headers from an email message, and it’ll perform several interpretations and validations on the information. Most tellingly in this example, near the top of the results was this:
To grossly oversimplify:
- SPF is an email standard that defines whether a specific email server is authorized to send email on behalf of a specific email domain.
- DKIM is an email standard that confirms whether an email message was sent by the email domain it claims to be from.
This message failed both tests, further cementing our evaluation that it was spam.
Why didn’t a spam filter catch it?
So with all these indicators that the message is spam, why didn’t a spam filter catch it before it reached my friend’s inbox?
Two reasons.
First, many of the clues listed above are subjective. A spam filter, for example, won’t know that you do or don’t know someone, whether or not you’ve been having conversations with them recently, or whether the message itself contains reasonable context. These are all things only you and I can judge when we see the message and take the time to think.
Second, many of the clues — even the SPF/DKIM failures — are common even in legitimate emails2. This is part of what makes fighting spam so excruciatingly difficult. Suddenly enforcing one factor — say DKIM compliance — would work only if every single email server and service implemented it completely and correctly, and even then, there would be side effects.3 While possible in theory, in practice it’s just not happening.
If you click
Messages like this phishing attempt have a simple goal. It works like this:
- They look legitimate (or at least relatively legitimate).
- They promise something — either vaguely, as in our example, or important, as in fake delivery documents, or something else.
- They include a link to click on.
- When you click on that link, you’re taken to what appears to be a sign-in page related to the document promised.
- The sign-in page is bogus. It only collects your sign-in credentials, which are then passed on to the hacker.
Once the hacker has your login credentials, they can change the password, lock you out, use your account to impersonate you, hack into your other accounts (perhaps including your bank), and cause other mayhem.
So in our example above, clicking on the “Open Document” link would probably have taken you to something that looks like (but is not really) a Microsoft account sign-in. If you had entered your Microsoft account credentials, you would have handed them over to a crook.
Do this
Think before you click.
I listed many “clues you can use” above that don’t require complex header analysis or any kind of technology. All you need to do is pay attention.
Unfortunately, in the rush of our day-to-day, it’s all too easy not to. It’s easy to simply glance at a message and act on it without fully understanding what’s about to happen.
Don’t be that person. Think first. The time you take to do so will be well worth it compared to the possibility of having your account compromised.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: While that’s technically bad English (“document file” is redundant), and the sentence should be terminated with a period, I’m not going to flag that as suspicious. It’s close enough, and sadly, many legitimate senders’ English skills are poor enough that this could easily be legit.
2: Having implemented these for my domains, I can confirm they are complex and easy to get wrong.
3: Some years ago, for example, Yahoo Mail began enforcing one aspect of their email configuration, and it caused almost all mailing lists across the internet to suddenly fail if @yahoo.com email addresses were used. Multiple mailing-list software packages had to either implement a cumbersome workaround or be abandoned.




What concerned me the most was: 6: The entire box was an image … Clicking anywhere would take you somewhere.
I am careful not to click on links in pretty much all emails, but I can see I could easily accidentally do a random click without having known the danger.
Thanks for reminding us, we can never be told too often to be careful clicking on links.
I would add: Never click on a link in an email. Always type the URL in question into the address bar of your browser. That way, you won’t be going to the rogue site.
Using a password manager like LastPass is also a layer of protection. If you accidentally click on a phishing link, the password manager won’t try to enter the password for you because the phishing site is not in their database. If your password manager can’t log in, it’s extremely likely that it’s a phishing attempt. Password managers may mess up and not enter the password on the real site, but this is rare. In any case, if this happens, look very closely at the email again.
I always hover over the ‘from’ to find out where anything unexpected is really from.
“From:” can be spoofed.
I only today received an email supposedly from ‘voicemail@hotmail.com’ with 6 lines of text beginning with ‘routing information’ and a little box with a link within titled ‘play voicemail’.
Included in the 6 lines was a telephone number, which, after I Googled, gave an address for the phone number and a google map, indicating it was a tiny little house in Kerala, India.
Hovering my mouse over the link showed the following address, {link removed}
I forwarded the email to ‘spoof@hotmail.com’ and also an Australian Government anti-spam website.
Many thanks for the wonderful work you do! Informative, educational and easy to follow safeguards. Such a comfort.
I received an email from a site I use rarely that said: “Okay Jeannie! Let’s change your password!” Nope, didn’t go for it because I didn’t request it. Marked as SPAM and scurried away to enjoy my carryout!
Note: I’m 76 years young and really a “horse n’ buggy gal.” As a Senior I’ve received countless phishing emails purporting to be from legitimate sources. Thankfully, I’ve kept a keen eye open and avoided any mishaps.
There used to be a government site/link where a SPAM message could be sent to and they were supposedly keeping track of all of them but I have not seen that site//link anywhere for quite a while. Is there a site at present where BOGUS messages can be sent? I get quite a few messages about “shipment of an order” or a “charge has been made to my “xxxxxx account” and they are checking to see if I actually made the purchase.
Cecil
Here is the link to report cybercrime to the FBI. Unfortunately, reporting it is unlikely to do any good because most cybercrime originates in other countries who don’t get involved. Most cybers-cams originate in Russia, East Asia, or Africa.
To avoid prosecution, Russian scammers avoid targeting Russians so the government won’t go after them.
There are, but I don’t bother. They can easily set up a honeypot and get all the spam they might want for analysis. I don’t think our reporting more really helps anything.
I’d like to hear commentary about the use of SPAMCOP.NET that analyzes the raw content of an email and will report SPAM to the appropriate webmaster or abuse authority.
Does it actually work in reducing SPAM? Is there some global impact that might not be apparent to the user, but good for the system?
“Delete” follows “spidey.” Is a general rule that works for me.
Cheers,
Aaron
My latest suspicions were justified when receiving a Dropbox message. I sent a separate email to the friend who supposedly sent the email & it was confirmed “NO, I don’t use Dropbox!” Googling Dropbox scams 2021 brought up a raft of links.
I’m 72 years young, and I look at EVERY email I get. Most of what I get are newsletters I have subscribed to. Others are from Amazon, where I make frequent purchases, and a very few are from other legit sources.
When I receive something I do not expect, I go into alert mode. I look very carefully to determine the legitimacy of the email. One thing I look at is if the email references me by name. If the name is wrong, it’s spam. I close it and move it to the spam folder. If it appears to be legit, does not refer to me by name, and comes from a source I have corresponded with (for example, a web site wanting to update or change my password), I open my web browser and navigate to that site to see if there is any sort of alert on the site. If not, I ignore and delete the email. If the email purports to be from someone I know, I call the supposed sender to see if they actually sent it. If not, it’s spam, and goes to my spam folder.
My email rules are simple:
1. NEVER click a link in ANY email, unless it is from a friend, AND I have verified that the friend sent it.
2. NO email is urgently important. If I cannot verify the sender, or I am the least bit suspicious of the validity of the message, I delete it.
3. If the message promises me millions of dollars, but I must click a link (even from Publisher’s Clearing House), IT IS SPAM!
4. If an email purports to be from a site I do business with, I can go to the site to do whatever the email wants me to do, rather than to click a link in the email.
I make a few small exceptions to these rules:
1. If I have just ordered something from a web site, and they told me they would send me a confirmation email, I cautiously consider it legit.
2. If I then receive a second email from the same site, providing a tracking link, I cautiously consider it legit.
That’s it. Like I said, my rules are simple, but they require that I pay attention to the email I receive MY rules have worked well for me. As far as I know, I have never been the victim of identity theft, and I have never been hacked, or been plagued by malware. There is much more to avoiding malware than watching my email, but it is one of the routes the bad guys seem to use, so it is very important
Here’s a phish I got today that, except for the fact I use Linux and thus don’t have a Microsoft account, I would have fallen for. Got an email from the veterinary surgeon I consulted about my dog. It was ostensibly sending me a final statement, which I was expecting, from a firm I had business with, and the signatories work at the firm. Clicking on “View Attachment” took me to a supposed Microsoft signon screen, asking for email and password. Except for the fact I don’t have a Microsoft account I would have fallen for it (I should have realized right away this was a scam but I’d been completely taken in by the email). The nickel didn’t drop until I return emailed the vet (the return address was valid) asking them to send me a pdf of the document, and got a reply saying to delete the email – they’d been hacked. Obviously the hacker has gotten into their customer database, not just their email and remained undetected long enough to construct the scam. Scary. Here’s a text copy of the email with names deleted. The “View Attachment” link pointed to an https address
=======================================================
Hello,
You have been granted access to view your document.
FINANCESTMT Summary (INV_STMT-#44092.pdf)
Reference #: 0d38d55b-a2d3-4284-9457-29230eeabbe0
Status: Executed
Executed: 09/21/2021
Sender: VRSP Consult
VIEW ATTACHMENT
To view this document Click View Attachment:
Disclaimer
The information contained in this communication from the sender is confidential. It is intended solely for use by the recipient and others authorized to receive it. If you are not the recipient, you are hereby notified that any disclosure, copying, distribution or taking action in relation to the contents of this information is strictly prohibited and may be unlawful.
Regards
[Vet Surgeon’s names]
Referral Coordinators
Veterinary Referral Surgical Practice
Another tip is that if your invited to click on a link, right-click on it to see the destination address. It will probably bear no relationship to the organization purporting to email you.
The problem with that is you might be sent to a website that injects malware. Not common, but it happens.
One thing you can do which is safer: Right-click on the link and click ” copy link” or “copy link location” or something similar and past it into notepad or another text editor
I had the privilege of watching over email for many years for a manufacturing firm. We would regularly see phish emails, like this one. The psychological “push” to click the link and provide credentials is quite evident in the composition of these. All the signs you mention are things I would regularly talk about with our people, and proved to be quite useful in helping to keep us safe.
I had noticed the addition of the “This link will work for anyone” phrase above the Open Document button to emails like this some time back. The question that statement should raise is “If it is available for anyone, why should I have to supply credentials?” A document available to anyone doesn’t need to be secured, that disconnect should raise a red flag.
Also, I always encouraged people to contact the sender of this sort of email by phone, not email. (And don’t use a phone number in the email signature as I have seen those modified, as well.) A compromised email account can usually be recovered pretty quickly, it seems, but more than once one of our people did reply to the email questioning the link and was quickly encouraged, by return email, to “just click the link!” The scammer still controlled the compromised email account and really wanted the click and the credentials. That is just how tenacious they can be!
If you want to see what is behind a shortlink works different on many sites who are providing them. This webpage can show you a lot of them. Also the more exotic ones like bit[.]do http://checkshorturl.com/ . I have been searching for it because bit[.]do does not mention it in their faq. But I spoke to the maker and he kindly sayed: just add a dash “-” (minus signal) at the end of the url with the short link.
Thank you, Leo, for this and all the work done over the years to make the internet a safe and useful place. As a newly minted member of your legions, I’ve learned much already. Shame there is all this junk out there from so many bad actors.
If I get a questionable email, I usually just go to my account using my keepass vault. If there is no message there, then I figure the email is phishing
.
If I am on the fence if it is legit or not, I will enter my altered username and altered PW for that site. If the resulting webpage accepts this false credential, then I know it is phishing.
The first part of your comment is good advice. Where you say “no message there”, I think you mean no stored website.
There is a risk of a drive-by attack if you go to a questionable site.
We recently resigned from our country club; a few days later, I received an email from the club director that there was a document for me. I assumed it had to do with the resignation. The link to one drive did not work (I don’t use One Drive) and when I contacted the director, got ab email back that he had been hacked!
Got fooled on this one (sort of) because there was a plausible context,
Good article (as usual(