How to tell if that email is sketchy.

Emails are frequent targets of scammers trying to get our account credentials and more. I suspect many more people fall for fake emails, scams, and phishing attempts than we realize.
In this article, I’ll review a scam I received recently for signs of fakery.
Become a Patron of Ask Leo! and go ad-free!

Identifying scam/spam emails
- Look for odd sender information and mismatched or suspicious domains.
- Look for grammatical errors and inconsistencies in the message.
- Check the destination of any links; they may lead to phishing sites.
- If you’re a techie, check the email’s headers for additional clues.
- Suspicious? Delete the email without interacting with its contents.
- Worried? Visit your email provider’s website or contact them for verification if needed.
The spam in question
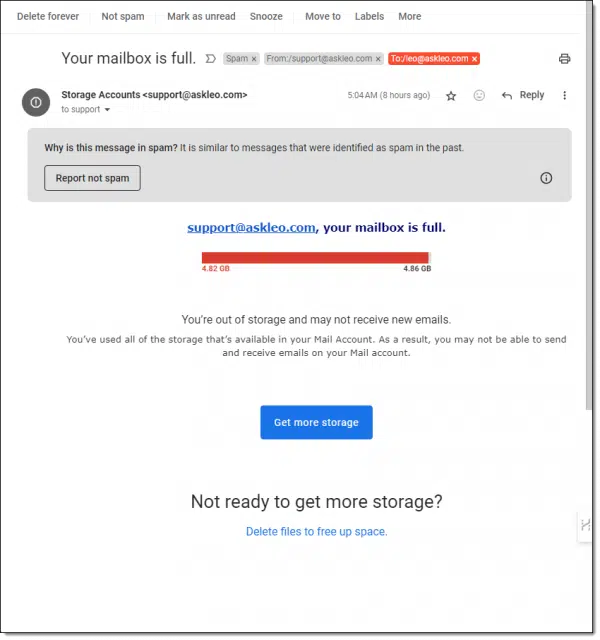
I’ve chosen this scam because I see different versions of it a lot. Some are simple, like the example above, and others do a better job of mimicking assorted email providers. In all cases, the threat is clear: you need to take action or you risk being unable to send and/or receive email.
In my case, Gmail has helpfully determined it’s spam, but your spam filter may miss it. Let’s look at a few clues.
Clues in the From: field
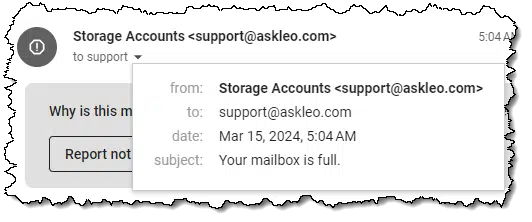
As you can see, I apparently sent this to myself. Of course, I did not. This is a great example of how spammers can put whatever they like in the From: field. I have no account named “Storage Accounts”, but support@askleo.com does exist.
Red flag:
- It’s being sent from the same email address that it’s being sent to.
Yellow flag:
- “Storage Accounts” is odd wording. I’ve never seen any email service use that term or structure.
Other flags:
Sometimes with this scam, the email will appear to be From: your actual email provider. Perhaps something like this:
Microsoft Email Support <a-completely-random-email-address@somerandomservice.com>
The random email address in the angle brackets will have no relationship with the service mentioned. It’s often some random, unrelated person’s email address. If it doesn’t match, that’s also a red flag.
Clues in the body of the email
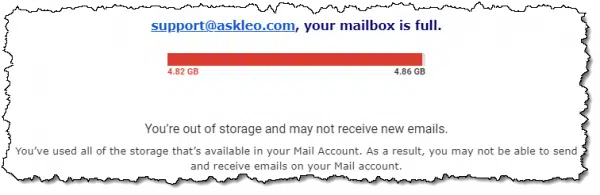
The clues to look for in the body of the message are inconsistencies and poor grammar.
For example, the bar graph goes from 4.82GB to 4.86GB. That’s a useless graph. Legit email services usually won’t include anything like this or will include a bar starting at 0% used. More commonly, they simply say “Your inbox is 95% full.”
Note that it claims that your mailbox is full, but never says what the limit is. It’s implying that the limit is a very common 5GB, but if that’s the case, the mailbox is not full, since it’s apparently at 4.86GB.
Grammar issues are also common in scams. In this case, I have a couple of quibbles with the wording. Not being able to send or receive email “on” your mail account is odd. Using “Mail Account” (capitalized) in both sentences is cumbersome. I’ve seen legitimate email with worse grammar; it’s just something to pay attention to, as it’s often a sign that something may be questionable.
Red flag:
- Nowhere in this threat — or the entire email, for that matter — does it mention which email service it supposedly is. While many spam messages try to be more convincing, this one isn’t. This lack of identification is a big red flag. A legitimate email from your email service would identify itself clearly by name and logo.
The URL reflected in the button
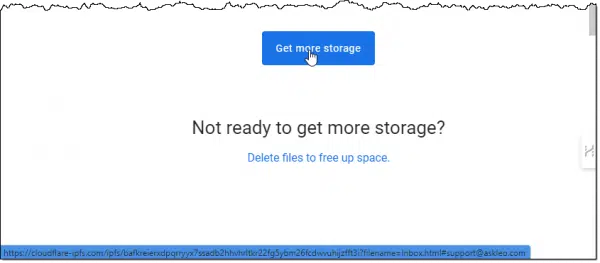
This is where things get really interesting. When I hover over the button, the link it goes to is shown by my browser below. Since it’s difficult to read in the image, it’s:
https://cloudflare-ipfs.com/ipfs/bafkreierxdpqrryyx7ssadb2hhvhrltkr22fg5ybm26fcdwvuhijzfft3i?filename=Inbox.html#support@askleo.com
The red flag:
- The domain, cloudflare-ipfs.com, has nothing to do with my email provider. Particularly for messages relating to email usage, limits, or other problems, this domain should be related somehow to the email service you’re using, be it outlook.com, gmail.com, google.com, or something else.
The orange flag:
- The link “Delete files to free up space” goes to the exact same destination. That the link to get more storage is the same as the one to free up space is suspicious.
Let me click that for you
Never click the links in spam. For the sake of education, I’ll show you what you get if you do.
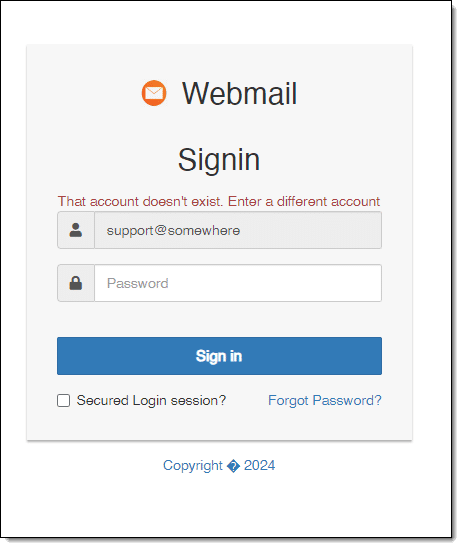
(I changed the “support@askleo.com” in the original URL to “support@somewhere” to avoid letting the scammer know that “support@askleo.com” is legit and reading emails.)
Red flag:
- This is likely a webmail sign-in page you’ve never seen before.
Some scammers set up a “sign in” page that looks very similar to the real thing.
The goal is simple: to get you to enter your email address and password. When you click on “Sign in,” your credentials are given to the scammer. In return, you’ll get a message that says, “The account doesn’t exist”, regardless of how many accounts you enter correctly.
Deeper into the headers
If you’re inclined to dive into a little geekiness, you can find more information that helps; you just normally don’t see it. You’ll need to “view original” or “view headers”. How you do that varies depending on what email program you use.
Here are the headers from our example spam. I’ve added line numbers to make referencing individual items easier.
1: Delivered-To: [redacted]@gmail.com 2: Received: by 2002:a05:7022:1090:b0:77:59e4:eee6 with SMTP id ep16csp980098dlb; 3: Fri, 15 Mar 2024 05:14:56 -0700 (PDT) 4: X-Forwarded-Encrypted: i=1; AJvYcCUA7FatUr89eqdD1WBsGrT8E4vIsFImPpuW0+AO512tBoD2qsNC1MumZVEmq/1mvy2PyrhdCisgfcOjsJ+ZfLd+ 5: X-Google-Smtp-Source: AGHT+IEDwh28KzBxvhXyUXNShHUGaoCAhxmKU+WdjQVV7DA5KjYhIHBWHM7ZCg3q+NLuCBD0iYyQPTJg+U4= 6: X-Received: by 2002:ac8:6211:0:b0:430:b0f3:20e8 with SMTP id ks17-20020ac86211000000b00430b0f320e8mr1908959qtb.0.1710504894958; 7: Fri, 15 Mar 2024 05:14:54 -0700 (PDT) 8: Authentication-Results: mx.google.com; 9: spf=softfail (google.com: domain of transitioning support@askleo.com does not designate 141.98.10.124 as permitted sender) smtp.mailfrom=support@askleo.com 10: Received-SPF: softfail (google.com: domain of transitioning support@askleo.com does not designate 141.98.10.124 as permitted sender) client-ip=141.98.10.124; 11: Received: by 2002:a05:622a:1051:b0:42c:65ee:2133 with POP3 id f17-20020a05622a105100b0042c65ee2133mf1189909qte.0; 12: Fri, 15 Mar 2024 05:14:54 -0700 (PDT) 13: X-Gmail-Fetch-Info: leo@askleo.com 10 mail.askleo.com 995 leo@askleo.com 14: Return-Path: <support@askleo.com> 15: X-Original-To: support@askleo.com 16: Delivered-To: leo-askleo.com@ec23.pugetsoundsoftware.com 17: Received: by ip-172-31-59-11.us-west-2.compute.internal (Postfix) id 3BC3341D05; Fri, 15 Mar 2024 05:04:10 -0700 (PDT) 18: Delivered-To: questions-askleo.com@ec23.pugetsoundsoftware.com 19: Received: by ip-172-31-59-11.us-west-2.compute.internal (Postfix) id 39D043EAA0; Fri, 15 Mar 2024 05:04:10 -0700 (PDT) 20: Delivered-To: support-askleo.com@ec23.pugetsoundsoftware.com 21: Received: from askleo.com (unknown [141.98.10.124]) by ip-172-31-59-11.us-west-2.compute.internal (Postfix) with ESMTP id AEA2641D05 for <support@askleo.com>; Fri, 15 Mar 2024 05:04:09 -0700 (PDT) 22: From: Storage Accounts <support@askleo.com> 23: To: support@askleo.com 24: Subject: Your mailbox is full. 25: Date: 15 Mar 2024 13:04:07 +0100 26: Message-ID: <20240315130407.6018636BB80BC4A1@askleo.com> 27: MIME-Version: 1.0 28: Content-Type: text/html; charset="iso-8859-1" 29: Content-Transfer-Encoding: quoted-printable
The very first thing to locate is From: line on line 22. (The colon is significant, as there may be other “From” lines without it.)
Then move to the first “Received” line above, and closest to the From: line. In our case, that’s line 21. This line tells us the origin of the message.
It claims to be “from” askleo.com, but the IP address it includes (bolded above) is suspicious because of the “unknown”. A legit server will have a legit name here. Doing a “whois”1 on the IP address tells us something very, very important.
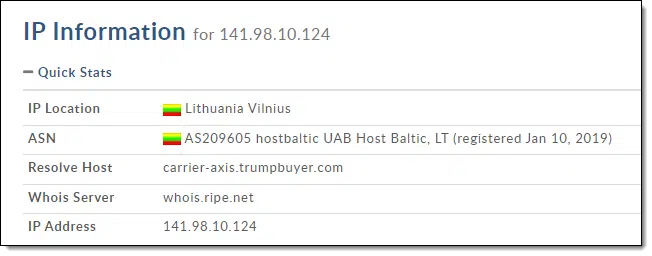
This might be the biggest red flag of all. It’s hosted in Lithuania, and the domain name associated with the IP address has nothing whatsoever to do with askleo.com.
Everything else above that “Received” line (line #21) is legit. It documents the message’s travel across the internet as well as the anti-spam measures it failed along the way.
Do this
Always remain alert and skeptical, particularly if you receive an email warning you of some dire consequences for not taking action.
If you’re concerned that the email is authentic and you need to take action:
- DO NOT click on anything in the email.
- Delete the mail.
- Visit your email provider’s website yourself, and log in normally. If there’s an issue, you should see a notice of some sort (though not by the same email in your inbox).
- If you’re still concerned, and it’s an option, contact your email provider directly and ask.
No scams here! Subscribe to Confident Computing, and you’ll see it regularly. Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: I happen to use whois.domaintools.com, but many different services provide similar functionality.





Recommended if you get an impersonation email like this one on your domain setup DKIM and dmarc and the case of office365 email or called exchange online setup impersonation protection. this will prevent scamers from even being able to send emails out when they do not own the domain.
When those phishing attempts came into the Ask Leo! question queue, I hovered over the link and copied it to the clipboard. I pasted it into the mywot.com website to see if it was a legitimate site, and the comments indicated it was a scam site.
My first impression was that the warning came from FreeScout as they handle our questions and answers, but I didn’t click because clicking is the one thing you should never do until you’re sure it’s legit.
I found the language a little suspicious, but as you said, legit emails can have bad grammar. Some IT geeks have notoriously bad language skills. Bad grammar is a sign, but many scammers are getting better at making the language sound professional.
More hints :
– Mail account is spelled “Mail Account”, then “Mail account” right afterwards in the phishing email.
– The phishing page is called “Webmail”. This means the scammer did not care to design a phishing page dedicated to each of his targets’ specific mail provider. No mail provider will have a log-in page called “Webmail”.
– There’s a silly tick-box called “Secured Login session” on the phishing page. This does not mean anything, and no service displays such an option.
Here are three sites to check the safety of a link; right-click on the link in question and select Copy link address (if the link copied is different than the printed link, then that is an immediate giveaway that the link is likely fraudulent):
https://www.scam-detector.com/validator/
https://www.scamadviser.com
https://www.emailveritas.com/url-checker
(Those with a Safe Link generated by a Microsoft email client (Hotmail, Outlook.com, Msn.com, etc.) can decode it at: https://www.o365atp.com .)
When I get the spam and flag it as spam, I often get the message asking me if I want to unsubscribe or mark as spam. Always mark it as spam.
That’s good advice. If it’s spam, unsubscribing opens you up to more spam because it verifies your email address to the spammers as valid.
I love this! And…with the advent of excellent AI spam creation tools, I have begun to advice clients to not try to figure out on their own if something is spam or a scam. To assume that EVERY mail or text that is creating urgency or wants you to log in through that its own link is a scam. And follow the steps listed in “Do This” above.
That said, it is very good practice for people to understand the email domains/mismatches. I had one Macaffee renewal scam that came from SomenameGambino at Gmail. I thought it was so funny that they had gone to the trouble of doing this and picked the name of a well known mafia family!
That was very Childish of them.
When I receive ANY email message from an unrecognized source, the first thing I check is the name to whom it’s addressed (if there is one). If there is no name, or it’s not my name, the message’s spam, and I send it to my email account’s spam folder. This scenario accounts for nearly 99% of the spam mail I receive. As for the few messages not covered above, I do as Leo suggests in this item.
Ernie (Oldster)
Closely examining certain suspicious E-Mail can provide entertainment. Regarding the example message: When I saw the graph, I knew instantly that whoever had composed this had failed fifth-grade math! When yo right-clicked the “Get More Storage” link to get the target address, I said, “Iiiiiiii seeeee…!” in a nasal voice (viewers of a certain “Honeymooners” episode will know what I’m imitating). That target link ALONE would be more than enough to tell me the message was Spam and would guarantee that, no matter what ELSE I found, I would treat it accordingly. For me, any further delving would just be for fun.
Yes, I might try plowing through the headers, but I’m not as good at it as Leo; I would probably have overlooked the “Unknown” header, and even if I had caught it, I wouldn’t know what to do with it. (Now I know — thanks, Leo! — but in most cases, such as this one, I would usually consider “it not worth the effort.” But had I done so, the “Lithuania” source would have had me howling with delight, and sending to my Spam folder in triumph. See? Spam can be FUN!!!) 😮
I’ve seen phishing emails purportedly from a bank that have inline links to the banks website with logo, privacy statements & other artwork. These look quite realistic.
There is also a theory that a lot of mistakes & inconsistencies are to weed out anyone who is in the least bit suspicious & discerning. They are essentially a test of gullibility.
I have a feeling that theory is just a conspiracy theory. I’ve read it in a few places, but it doesn’t make any sense in weeding out the non-gullible. They may vary the spelling of certain words that are red flags to spam filters, but I don’t see how this would do anything to weed out the non-gullible.
For a while I was receiving a particular set of advertising emails at my work address. They were supposedly from an individual named “Matt Hacker”. I snickered at their choice of name as I submitted them to my employer’s “Report Phish” service.
After sending over a whole bunch of them (Matt was a persistent fellow) our security team did a detailed investigation and discovered that Matt Hacker wasn’t a computer hacker. He was a real salesperson at a real business.
It wasn’t a scam, but it was spam, so he and his organization were still blocked. Even today I still occasionally laugh at the unfortunate coincidence of his name.