How to keep your safety net ready when you need it.
When available, recovery codes are an important part of keeping your account safe by ensuring you can regain access to your account should something bad happen.
I strongly recommend you create/retrieve them and keep them safe and secure.
The question is: exactly how are you supposed to do that?

Keeping recovery codes secure
There are two general approaches to saving recovery codes: printing them or saving them in digital form. In both cases, keeping them secure is important. This means storing the printed paper somewhere secure or securely encrypting the digital versions. In either case, be sure to create recovery codes before you need them so you can regain access to your account should you ever need to.
Getting codes
Recovery codes, sometimes referred to as one-time passwords, or backup codes, are codes you generate, save, and then use if for some reason you can’t sign in normally.
Exactly how you get recovery codes depends on the service. Many services offer them as part of their two-factor authorization implementation. Recovery codes are often a safety net for having lost your second factor.
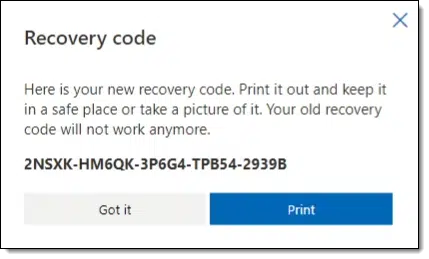
Some codes are long single codes, such as the Microsoft account recovery code shown above. Others are collections of 8 or 10 shorter codes. There are probably other variations as well.
They share a few things in common:
- They appear to be random numbers or strings.
- Typically, each code can be used only once.
- Your ability to provide a recovery code when requested verifies that you are the legitimate account holder and should be allowed access to the account.
It’s that last item that makes it so important to store recovery codes securely: anyone with access to the codes can potentially gain access to your account.
Help keep it going by becoming a Patron.
Storing codes
There are two approaches to storing recovery codes securely: print a hard copy or save a digital copy.
Print the codes
This is perhaps the most common recommendation I see when I create recovery codes. It’s also the one I like the least.
The concept is simple: print the recovery codes on paper and then store that paper somewhere secure, such as in a safe or a locked drawer.
I don’t like this technique because unless you print multiple copies and store them in different locations, there’s only one copy of the code. On top of that, the media is volatile, meaning it’s easy to lose due to fire or other issues.
But it’s certainly an easy approach, and if this is what you feel most comfortable with, by all means, print your recovery codes and store them somewhere safely. Just make sure that “somewhere” is indeed safe and secure.
Encrypt the codes
In my opinion, the best way to store recovery codes is to copy them and secure that file with strong, secure encryption.
First, make a digital copy of the code. You can:
- Take a digital picture of the code.
- Take a screenshot of the code.
- Copy/paste the code into a simple text file.
Then encrypt that file. That could include techniques such as:
- A password-protected ZIP file
- A VeraCrypt volume
- A Cryptomator-encrypted collection of files
Storing it as part of your password vault — either with its associated account entry, or as a separate secure note — is also a useful approach, since password vaults are also encrypted by default.
The big advantage of this technique is that it makes backing up your recovery codes a snap. Since they’re securely encrypted, these encrypted files can remain on your hard disk, where they’ll be included in your regular backups.
Do this
Always generate recovery codes for accounts that offer them. Hopefully, you’ll never need them, but if you ever lose access to your account, you’ll be very glad you have them.
Store your recovery codes in a secure location that works for you. I prefer the digital approach (I use Cryptomator), but whatever works for you and remains appropriately secure will do.
If you found this article helpful, you’ll love Confident Computing! My weekly email newsletter is full of articles that help you solve problems, stay safe, and increase your confidence with technology.




I do both methods. I keep the digital files primarily for my own use. The printed copies of my recovery codes and instructions for their use are kept with my will and other documents for when I go 404.
Just a few minutes before reading or even seeing this article, I went into Facebook settings and got my recovery codes after having set up two-factor authentication the prior evening. I copied and pasted the codes into the Facebook entry in my password program (KeePass). I then immediately backed up my password database to my cloud backup.
I hadn’t even known about recovery codes until this morning, when I was in Facebook settings looking for something else.
I use all 3 encryption methods mentioned in the article. For single files, I use encrypted .zip files. There are many programs that manage .zip files, so you can decrypt them on any computer. I use Cryptomator for all my sensitive files on my computer because I can work with those files on my computer as if they were not encrypted. A disadvantage of that is that unless I have Cryptomator installed on a computer, those files are inaccessible, so I don’t see that as the best way to encrypt a recovery code. I use VeraCrypt for collections of files and for system encryption on my older computers that don’t support Bitlocker.
As much as I like Password Managers (my current favorite is Dashlane), they come and go, raise prices above what I want to pay, etc. So, I still keep my password protected Excel file that I started over 30 years ago. Now over 900 entries I have everything in there, logins, passwords, recovery codes, which credit card is on the account so when I get a new number or expiration date, I can sort Excel to find all the accounts with that card so I can update them quickly. A few years ago, I moved all my files to OneDrive, so I keep that password protected spreadsheet in my OneDrive Personal Vault for another layer of protection. From time to time, I create a backup copy of that file and store it locally and in my safe deposit box at the bank.
Password protect a spreadsheet: https://support.microsoft.com/en-us/office/protect-an-excel-file-7359d4ae-7213-4ac2-b058-f75e9311b599
OneDrive Personal Vault: https://www.microsoft.com/en-us/microsoft-365/onedrive/personal-vault
I’m nor sure if this is still the case, but in the past, it was very easy to crack MS Office protection. It’s probably improved, but I don’t fully trust it. I’d use another encryption method. Even .zip encryption is fine.
How do I remove password protection from an Excel document?
If they are single-use haven’t they already been used and are no longer valid?
Yes, but this article is about protecting them before using them. Once they are used, you’d need to generate a new code.
I add each recovery code to the online account entry I have for that specific account in my Bitwarden vault. Click EDIT for any account set up in Bitwarden and you’ll see a NOTES field where you can add any text. Paste it there. Now its in the cloud, secured, encrypted, and accessible 24/7 from any computer/ anywhere. I also save them in a .txt file in a Cryptomator vault, but as was stated before, if you don’t have Cryptomator on the computer you use to retrieve it you can’t get to it.
I keep my recovery codes in my password manager. There is a ‘Notes’ section where I copy/paste the code with an indicator of what it is. Since my vault password is very long, and the encryption on my vault is strong, I feel very secure in keeping this information there. As an added measure, I export the entire contents of my vault annually, then encrypt it in a password protected zip file on my primary computer, replacing the previous year’s copy. I also store a copy of the password to that zip file in my password vault and in my OneDrive vault so it’s being stored in two places. This may seem like a bit of over-kill, but I’d rather be safe than sorry.
Ernie (Oldster)
Definitely not overkill. Overkill and security are an oxymoron. There’s never too much security. Password managers are a great place to store recovery keys. That’s one of the things they are designed for.If they can protect your passwords, they can protect sensitive data.
Some recovery codes are unique, and can be used any number of times. That’s how the encrypted mail provider Tutanota does it.
Its recovery code can be used instead of the password, or instead of your 2FA secret if you have lost either. You only have a single recovery code at any given time, but you can swap it for another one whenever you like.
This ability can be put to work if you have been hacked. Suppose a hacker gained entry, and locked you out by changing the password. If he did not think of changing the recovery code, you can regain access with it, then change the password to lock the hacker out, then change the recovery code to be 100 % safe.
Naturally, if a hacker was able to get in in the first place, it means you have rotten security habits (poor or reused password), so you shouldn’t count on the recovery code as an anti-hacker tool.
But it’s nice to know it’s possible in theory.
“it means you have rotten security habits” – not always. If the password were exposed through some other means (rotten security at the provider, for example), it wouldn’t be your doing.
I recently had trouble logging in to an account I had for about five years. Since 2FA was established for this account, I felt safe. However, my phone number for 2FA was changed abruptly and I lost access to my account. I had backup codes but I was not able to locate them and therefore had to start all over again with a new version of my permanently lost account.
So I set up 2FA again and downloaded new backup codes. The new codes are printed and encrypted on a separatee drive in case of computer system failure. I believe that it is not safe have backup codes stored on computer systems because of possible corrupted backups that will not restore the system to operational status. About two months ago, my system failed and the backups were unable to reset my system. No usable backups, no recovery codes – a hard lesson to learn.
I have Dropbox and OneDrive. However, I am a bit skeptical about putting valuable information on online platforms because hackers always seem to find a way of getting around security strategies of online storage providers. I welcome commentary o the subject under discussion.
If you encrypt those sensitive files with a long (16 or more characters) they should be safe in the cloud. As a backup, you can keep a copy in OneDrive and Dropbox. Zip encryption using 7Zip is as good as any encryption method.
” hackers always seem to find a way” -> this is misnomer. Yes hackers do gain access to accounts, but if you do security properly, the chances of them getting your specific account is low.
As Mark pointed out encryption is the key. In addition to the tools he mentioned I’d recommend looking at Cryptomator as well.
The only Recovery Code I have is for Google data (a total of10 codes and they consist of just 8 numbers each). And it’s for Google personal data such as contacts, messages, calendar, etc. I have never been introduced to such codes from any other website. What would be the other typical websites that offers this? I apologize if I missed something.
It varies. Many include it as a 2-factor recovery option.
I know Microsoft offers it: https://askleo.com/microsoft-account-recovery-code-what-why-instructions/