No need to worry about losing your second factor if you do this first.

I’m a big believer in using two-factor authentication for online accounts.
Two-factor authentication (often referred to as multi-factor authentication, 2FA, or MFA) adds the requirement of “something you have” to “something you know” to log in to an online service.
The risk is that “something you have” could turn into “something you’ve lost”. If you need it and don’t have it, you might not be able to sign in.
The solution? Preparation.
Become a Patron of Ask Leo! and go ad-free!

Two-factor authentication adds “something you have” (like a key fob, app, or mobile number) to “something you know” (your password) to allow you to sign in. You could lose your second factor, so it’s important to set up the recovery options offered by the online service to be able to get back in without it. Keeping the recovery options safe, secure, and up to date allows you to safely rely on the additional security of two-factor authentication while knowing you have a way back in should something happen.
Two-factor and “something you have”
You’re already familiar with “something you know” — that’s a password.
Something you have might be a mobile phone capable of receiving a text message, an authenticator app on a mobile device, a dedicated key fob, or even a specialized USB device. Two-factor authentication simply means that you must provide not only a password but proof that you possess a second factor. If you don’t, you can’t sign in, even if you know the password.
Neither can hackers — and that’s the point.
The scenario: losing “something you have”
It’s one of the first questions to come up when I talk about two-factor authentication: what happens if I lose my second factor?
It’s a valid concern.
In my case, for example, I have several accounts requiring my mobile phone in order to sign in. I can’t tell you the number of times I’ve attempted to log in on my family-room laptop1 only to have to go back to my office and get my phone.
What if I didn’t have my phone or it was broken?
What if I were traveling, and I lost my phone?
This scenario is something two-factor authentication designers realized would be an issue from the beginning. The solution? Recovery codes.
Two-factor recovery codes
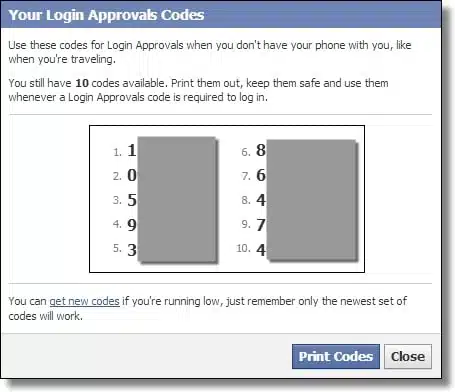
When you set up two-factor authentication, you’re also provided with, or prompted to create, recovery information. They typically include options such as:
- Recovery codes: complex codes you can use to sign in without the second factor present.
- One-time passwords: one or more passwords you can use exactly once each to sign in without the second factor present.
In addition, mechanisms you’ve already put in place to recover your account, such as an alternate email address or mobile phone number, are sometimes also used in lieu of two-factor authentication should you lose that “something you have”. In a sense, your ability to get messages at that alternate email address or mobile number is also a type of second factor.
Once signed in successfully, the idea is you would then re-establish two-factor authentication with a new replacement device or turn 2FA off completely until you can.
But wait… log in without the second factor? Doesn’t that negate the security offered by two-factor authentication?
Not at all.
Keeping recovery codes secure
Remember, you only need recovery codes if you lose your second factor. The rest of the time, they’re completely unnecessary.
I have yet to need one of my recovery codes.
The issue, of course, is that these recovery codes are like a magic key to get into your account. If anyone besides you could get them, they could get into your account.
That’s why it’s critical to keep them secure.
Suggestions include:
- Print the codes and keep the print-outs in a safe location, such as a personal safe or safety deposit box.
- Save them digitally to a known and extremely secure location, like your password vault.
- Save them digitally, encrypting the file(s) with tools like 7-zip, BoxCryptor, or others, and then back them up appropriately.
Needless to say, I use the last option. My recovery codes are encrypted and backed up in such a way that I would be able to recover them no matter where I am — even when traveling.2
Similarly, keeping your other account recovery information accessible and up to date is critical as well. You’ll need it if you ever need to regain access to your account, including possibly because you don’t have your second factor available.
But as it turns out, keeping recovery information secure and/or up to date isn’t even the biggest issue.
Keeping recovery codes at all
Too many people fail to save the recovery codes at all. Or they forget where they put them. Or they let their alternate email address fall out of use. Or they got a new mobile number and don’t update it in their recovery information.
You can guess what happens when they lose their second factor without any way to recover: they lose their account. It’s gone, completely, permanently, and without recourse.
When you add a second authentication factor, the advice is simple: don’t lose the recovery codes. Keep them secure, and remember where you kept ’em. And of course, keep your other account recovery information up to date as well.
Do that, and you’ll have all the security of two-factor authentication without inadvertently locking yourself out should you lose your phone, fob, USB device, or other second factor.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!





How do I set up 2-factor authentication? You described the problems and possibilities of recovering the lost 2nd factor but don’t tell how to set up the system to begin with.
Recovery codes are good, but the belt and suspenders choice is to use Authy.
https://www.authy.com/
I’ve never worried too much about losing my phone, but resetting it is a huge pain because I have so many accounts with two-factor authentication. Now, because of Authy, resets are simple and straightforward. And if, by some bizarre chance, I should lose my phone and my computer should crash–without a backup–all in the same day, I’ll still be okay.
Leo, here is my problem with Gmail 2-step authentication. I have used it off and on, but always end up doing away with it. Here is the reason: no matter how many times I check the box that says “Do not ask for codes on this computer”, it asks me every single time, and I simply get sick of that. Can you help me solve that issue? If so, I will be happy to do the 2-step with Gmail again. Many thanks!
That’ll happen if you clear cookies for any reason. Your “remember me” state is saved in a cookie.
There is a brilliant place to hide computer passwords: Inside the case of the desktop computer. A laptop could have the passwords inside the battery compartment. If you are totally paranoid, you could add a character or two to the front and/or back of the passwords, as long as you remember what you did, so the passwords won’t work even for a determined thief.
Write your passwords/codes in an adres-file or -book, using fake telephone-numbers or email adresses
I wish more websites would allow you to provide a landline phone number to receive a voice message with the security code for those who don’t check their emails wherever they go. No need to worry about losing a landline phone, plus it seems more secure than a mobile phone. Is there any particular reason why some websites, such as Yahoo email, insist that only a mobile phone number be provided for 2-factor authentication?
So I researched Yahoo’s 2FA, and they support voice. I added my land line, and got a call. Then logging in to an in-private browser session I got a number of options for the seceond factor including my landline, mobile (text or call on either), as well as email to an alternate email address. Here’s pic of all my options:
So even though it asks for a mobile number, I’m thinking you have many more options than just that.
In all my years of establishing online accounts with various small and large financial institutions, I don’t recall ever receiving recovery codes or one-time passwords as part of the process of setting up Two-Factor Authentication. It would be great if I did because my big worry is that, as this article mentions, the second factor could be lost, stolen, or broken. And if that happens, then what?
I sure hope Leo was exaggerating a bit about the risk of “losing access to that important account … forever.” What if that 2FA account held a substantial chunk of change?!
I better check with my financial institutions to see whether they had offered any recovery methods for 2FA accounts. Hopefully, it wasn’t an oversight on my part – and hopefully they have recovery methods now.
Most websites which offer 2FA let you set up several recovery emails in addition to the phone number.
Banks, businesses, and financial institutions will always have another way to get you access. For example if I lost access to my online banking, I walk in to the bank where they vet me and restore access.
It’s free accounts with no customer support (Gmail, Facebook, etc.) that are most often “lost forever”. Generally people that take the time to set up two-factor generally do all the other things right (like recovery addresses) so they rarely lose things.
I keep a copy of my recovery codes encrypted in my one drive folder. That way, I have it always available on all my computers, Android & iOS devices and the Web. I use zip encryption so I can decrypt the codes when I download them from the Web on a work or friend’s computer.
What about fingerprint recognition?
What about it? You still need to set up backup authentication mechanisms, if that’s what you’re asking.
I used to have fingerprint recognition on my Lenovo laptop until last week when the driver became incompatible with the latest Windows update. I contacted service and got a completely wrong solution and when I went to the forum, Lenovo customer service said they didn’t plan to update the driver. Bottom line, don’t rely on a fingerprint as your only method of logging in. You should always have a backup method. The computer is only two years old. Last Lenovo I’ll ever buy. Losing the fingerprint reader is a minor inconvenience, but I can’t deal with incompetent tech support.
Hi Leo:
I use 2FA on many accounts that use it. My recently purchased iPhone intermittently would not connect to the VZW network, so Apple sent me a new one for free. I reloaded it from iCloud. My 2FA link to GoDaddy was there, but the link to 2FA for Splashtop was not there. The Splashtop 2FA link was for an additional user on Splashtop, so it wasn’t my regular email address, which compounded my recovery. I followed their instructions to re-install 2FA, but it didn’t work. They’re not taking calls due to Covid, so I had to email them. Three days later, I hadn’t received a return correspondence or callback, so I emailed them again. Another couple of days, I finally received an email with instructions to re-install my 2FA link. I was able to re-install 2FA, but what if I had needed access sooner? Yes, I realize that I should have kept my recovery codes, but I didn’t. This made me think, do I have to store all my various recovery codes on my computer (or in a filing cabinet)? I regained access and I turned OFF 2FA for this account. They still use a one-time email authorization if my signon is used from a new computer, so I will have to live with that. I have over 50 passwords to maintain, so I started a NOTE on my iPhone and one my Computer with all my signons and passwords (all strong p/w’s), all coded with abbreviations (i.e. one password starts with “H” so my hint is “H.”) So I downloaded an app to store passwords, then I thought “Where are they in the cloud?” “Who has access to them besides me?” It’s a difficult decision, but each of us will need to decide which one works best. Yes, I know, don’t lose the recovery codes.
Try using a password app to manage all of your various password, PINs, and codes? It’s much simpler and safe (e.g., Dashlane, LastPass, 1Password).
I’ve always been leery of setting up 2FA, but now after reading this article, I an definitely going to avoid it whenever possible, and if it is not possible I will find an alternative service.
The deciding factor was “they lose their account. It’s gone, completely, permanently, and without recourse.”
I do not want to live my life with a loaded, cocked gun pointed at my head. One day it will go off. Definitely. And when that happens, I really would like some recourse.
Until that recourse is available, it’s not for me.
You’re in more danger of that without 2FA than with it. As you sit without 2FA you are MORE likely to get hacked and have your account “gone, completely, permanently, and without recourse.”
And as the article goes discusses, preventing that “gone, completely, permanently, and without recourse” with 2FA is almost trivially easy.
Did you read the same article I did, the one above?! Accounts “secured” with only a password are already at risk. Ignoring the remedy, and the simple means of securing recovery codes, isn’t doing you any favors.
Hello,
I have read most of Leo’s memo’s and find them informative and accurate. I have been a supporter of “Ask Leo” for 15 years. I am a retired person with IT knowledge and have found that Leo offers straight forward advice without hoops or twists to jump through. User’s can always ask questions but just how many questions can one ask before they see the light? I will continue to support Leo and his efforts to help we user’s. Continue on my friend.
I’ve never been offered recovery codes when setting up two factor authentication. In fact, I’d never heard of them until now.
Hopefully you were offered something. Not all services support all recovery options, but they should all support something.
Gmail (Google account) offers lots of options including recovery codes. They’re great! I’m glad I read this so I understood how I would use them.
Paypal – nothing except to add an additional phone, text only so can’t even use a land line. Very poor for such an important service.