Hackers keep track of your passwords if they find ’em.

A reader recently commented:
I disagree.
You don’t need a password-strength tester.
You should, however, use a password-found tester. And while it’s not “some random website”, there is a website I suggest you use.

Don't reuse passwords
When hackers discover passwords in a breach, they try them out at other accounts associated with your user ID or email. They also use collections of previously discovered passwords in brute-force attacks. Once a password is discovered, no matter how strong, it is no longer a secure password. Use unique, long, strong passwords, ideally random, and enable two-factor authentication on all accounts that support it.
Strong passwords
Strong passwords are easy. If you’re using a password vault, use its password generator to generate passwords of at least 12 (I use 20) random characters.
Something like rGyk2fhfQAtAzoejLZFF. Or gzmkuRUgyhqY. That style of password is quite secure — as secure as it gets, as a matter of fact. And I didn’t even bother to use special characters. No strength testing needed.
Use a password manager to save your passwords, and it doesn’t matter that you can’t possibly remember them.
Security achieved.
However.
Help keep it going by becoming a Patron.
Reused passwords #1
Using the same password at multiple different sites is probably the single most risky thing you can do,1 no matter how secure the password might be.
Here’s why.
Let’s say you use the same nicely secure password — rGyk2fhfQAtAzoejLZFF — at service A and also at an unrelated service B.
Service A gets hacked. Not your fault; nothing you could have done about it; but it happened. What’s worse, service A did an even worse job than we thought with security: they stored passwords in a way that the hacker was able to recover the actual passwords. The hacker now has rGyk2fhfQAtAzoejLZFF as the password for your account, along with your email address, which is commonly exposed in breaches like this.
The hacker starts trying your email address and password at all sorts of other common services in case you happen to have accounts there.
Eventually, they reach service B, and when they try to sign in as you, it works, since you used the same password there as you did at service A. Security measures at service B never came into play because it was never hacked. The hacker simply signed in as you with your username and password: the password they had discovered somewhere else.
This happens all the time.
Reused passwords #2
This is a variation on the theme, but it’s not obvious. So far, we’ve focused on making sure two or more services don’t use the same password at the same time. But it’s worse than that. Even if you use a password in one and only one location, even if you later change it, you should never use that original password again.
Let’s say you have a nicely secure password — 9Fotvb7fb2J4BbEAFKk4 — at service A and only service A.
Service A gets hacked. Once again, it’s not your fault. Once again, service A’s security was poor, and they stored passwords in a way that the hackers could get them. The hacker now has 9Fotvb7fb2J4BbEAFKk4 as the password for your account, along with your email address.
Service A has been hacked, but only service A. The hackers try your email address and password at other services, but it gets them nothing. You used it in only one place. Good on you.
Now never use that password again. Ever. Why?
Password collections
Because something else happens when hackers discover account passwords: they save them. They build a list of all the passwords they’ve ever discovered anywhere.
And they use that list in the first volley of brute force attacks in the future.
We think of brute force attacks as trying all possible passwords, but a more effective hacking strategy is to try all previously discovered passwords first. Why? Because people insist on reusing passwords. If not right away, then eventually.
What this means is that once you’ve used a password, you should never, ever use it again, anywhere else, for all time.
One and done.
You can check
Dream up a password that doesn’t follow our rules above: something that would clearly be a poor password. I’ll choose pinkducky.
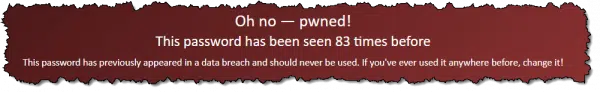
The image above shows the result of entering pinkducky at Pwned Passwords, a service of Have I Been Pwned. Pinkducky has been discovered 83 times across the breaches that Have I Been Pwned is aware of. (Maybe don’t use that as a password.)
I don’t consider Pwned Passwords a random site; it has a great reputation and does all the tech right. Your actual password isn’t really uploaded, and anonymity is preserved (you can read more on the site about how this is accomplished if you’re so inclined).
Here’s the thing: any password you’ve ever used could be on the list, particularly if you don’t use a technique like the “12 random characters” approach I used above. Even if you have been using long, strong passwords, if that password was ever discovered by hackers, it could be on their list to try.
So even if you think you’re properly obfuscating (0bF45c4T1ng) your passwords, you might want to check them with Pwned Passwords.2 If anyone anywhere happened to use the same password, and that password was breached, you could be setting yourself up for a problem eventually.
Two-factor helps a lot
Passwords are kind of a mess. I definitely prefer the 20-random-character method for new passwords, but changing old passwords, compromised or not, is a big job. My last password vault backup had over 1,000 entries.3
The good news is that an account protected with two-factor authentication is still reasonably secure, even if the password is weak or even known. As I’ve said elsewhere, even if they know your password, with two-factor authentication enabled, they still can’t get into your account.
Do this
Enable two-factor authentication on all accounts that support it. While you’re there doing that, change any weak or reused passwords.
Stop reusing passwords, including passwords you used once but aren’t using currently. Always start with brand-new passwords. (Ideally, use the random-character method, but I know not everyone will. Just make sure your password is long and strong.)
Consider using Pwned Passwords as an extra layer of detection of whether or not your password is already known in the wild. If it is, stop using it. Period.
Also, subscribe to Confident Computing! It’s my weekly newsletter with less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: Well, aside from posting your password publicly, or giving it to someone you shouldn’t, I suppose.
2: Pwned Passwords is not a canonical list. Hackers may have longer, more extensive lists that haven’t been discovered yet. But it’s what we have available to us.
3: I’m probably exceptional in this regard, but I expect most people have over 100 accounts.


But using a service like Pwned Passwords means you have to give them your password in order to check it out, doesn’t it? Isn’t that a breach in its own account?
No. Your password never leaves your machine. It’s hashed, that hash is uploaded and compared against a database of hashes calculated from discovered passwords. You cannot get a password from the hash, so while PwnedPasswords can tell you that your password was found, it still has no idea what your password actually is. This is the same technique services should be using to store your password in the first place (though, sadly, not all do).
I agree with everythong you just said, Leo… mostly.
I have a minor quibble about password-strength checkers. They have their place, and can be useful. But, absolutely, they aren’t really necessary. But it you DO use one, DON’T use one online; that’s just begging to be hacked. Get an app, and use that instead.
But as zLeo says, they’re not necessary. A good, strong password or passphrase has eight characteristics:
1. lowercase letters.
2. UPPERCASE LETTERS.
3. Numbers: 0123456789.
4. Punctuation: .,’:;-!?.
5. Symbols: @#$%&+=*£©™π.
6. Spaces: [ ].
7. Respelling: Never use any word you can find in a dictionary — hackers USE dictionaries to hack passwords! In other words, use “kwean,” not “queen.”
8. Length. The longer, the better. In fact, length is arguably THE most impirtant element in ANY password; it can even compensate for passwords that are otherwise weak.Believe it or not, “passwordpasswordpasswordpasswordpassword” is nice & strong! (But even so, please don’t use it!).
Ooops, forgot to add that the length should be at least 18 characters, and preferably even more. As I said above, the more, the merrier.
I agree with most of that, but there are a couple of points that may not be necessary.
Special characters and punctuation add complexity, but random letters and numbers are not bad. Add a couple of letters to a password and you’ll have a strong password, much stronger than the same length with special characters.
As long as you use a random string of words, they will not be able to be guessed by a dictionary attack.
“Yes, adding and using special characters makes your password better, but significantly better yet is to add one more character.”
“Its fleece was white as you know nothing John Snow”, at 50 characters, is wonderfully long, secure, and most of all, memorable. Much like the now canonical example of “Correct Horse Battery Staple“, you might even have a difficult time forgetting it.5
Ho Long Should a Password Be?
Spaces: maybe. Many logins don’t allow spaces.
For an example of what can go wrong, see the following National Post article from August 29, 2022, about Canadian citizens’ Canada Revenue Agency (CRA) accounts getting hacked. The article mentions that the CRA believes (or believed) that many citizens’ online accounts were hacked due to “credential stuffing” using stolen login credentials. But the fraud didn’t just affect citizen tax records, but extended to other government departments and programs:
https://nationalpost.com/news/politics/nearly-13000-canadians-potentially-victims-of-cerb-fraud-after-hackers-accessed-their-mycra-account-in-2020
so let me see if i got this right. in order to check if my password has been compromised, i have to “give” my password to have i been pwnd. anybody see the irony?
See Leo’s answer to Bill Holland in the first comment in this article.
No irony. See a prior comment: you are NOT giving your password to anyone — it never leaves your machine.
I tend to suggest at least 20 characters if possible to as it should be reasonably secure for the foreseeable future. from what I read it seems they say the single biggest improvement to a passwords level of security is simply it’s length.
basically password generation from a password manager is probably the all-around best/easiest for good password security. but if someone don’t mind taking more time Diceware (eff[.]org/dice ; the wordlist I use is linked there eff[.]org/files/2016/07/18/eff_large_wordlist.txt ) is a guaranteed secure way to generate passwords using real dice. to put it another way the security of a 20-character randomly generated password with a password manager should be of similar level of security as a 10-word Diceware passphrase (but the Diceware passphrase is easier for a person to type than a bunch of random characters since you are typing words). but I figure even one with less words (say 5-6 words) but add in ones own characters in-between words (i.e. WORD1aWORD2/WORD3 etc) will be plenty secure enough. just make sure you let the dice pick the words otherwise your security won’t be guaranteed if you only pick words you like using. but I guess at the bare minimum, even for people who want to put a very low effort into online security, a person wants to avoid the ‘low-hanging-fruit’ standard (i.e. so ones passwords are not TOO easy to guess) as that will probably keep a person from getting compromised most of the time as you don’t want to use the really easy stuff like ‘password’ or ‘1234’ and the like as you are just begging to get hacked if you do stuff like that on anything you care about.
anyways, Diceware 10-word passphrase (using that wordlist I mentioned above) is about 129.2bits of entropy where as a 20 character random password using 94 keys on the keyboard (which I think is all but spacebar) I think comes out to 131.1bits of entropy. so the 20-characters is more secure but not all that much basically as neither is likely to be cracked for the foreseeable future. but I use that stuff between words which I am sure further raises the already high security. because the 10 words security I mentioned above just assumes… Word1Word2Word3etc all typed as a continuous words stream. but simply adding in ones own characters/letters/numbers/symbols between words will further strengthen a already high level of security. I would especially do this if your using less words(say 4 or 5 words).
if someone is paranoid and don’t trust the security of a password manager to generate say a truly random 20-character passphrase you can use Dice to do that also using the following… theworld[.]com/%7Ereinhold/dicewarefaq.html ; go to the ‘How do I use dice to create random character strings?’ section. but basically you need 3-dice and each roll of those dice will give you one character on a keyboard (it’s possible to roll a ‘blank’ but you simply re-roll the dice) which you can get from that chart there as the first die is one of the first few sections, the 2nd die is vertical section, 3rd die is the horizontal section. they include spacebar in there (as ‘sp’), which would be 355 on dice roll, but I would just consider that a ‘blank’ and then roll again.
“My last password vault backup had over 1,000 entries. (I’m probably exceptional in this regard, but I’d expect most people to have over 100 accounts.)”
Damn, ‘over 1,000 entries’ is a lot!
I think you are right in guesstimating most people probably ain’t got more than around 100-200. my password manager says I got 63, but it’s basically less since some entries I kept in there that are outdated/no longer used. it’s probably closer to around 41 accounts, maybe a bit less. every once in a while I will go through there and clean things out/organize it. but after a while things tend to be stable to where you ain’t really adding in new entries (or more rarely).
not every password I use is stored in my password manager but nearly everything is. basically a small amount of things I use, with a dummy email etc, I use the same password on. but if these were compromised, it would not be that big of a deal for me since the email tied to them is a dummy one and the accounts ain’t of high importance, which is why I took a chance.
Originally I went through my password vault to clean out any accounts I’m no longer interested in on a monthly basis, bus since I’m no longer opening so many new accounts anymore, I take the time to go through it twice a year, in January, and July. I have my password manager generate sixteen character passwords. I based my decision about password length on the fact that most rainbow lists don’t go higher than twelve character passwords AFAIK. If that’s no longer the case, someone please let me know so I can prioritize twenty-character passwords!
I used Pwned Passwords to check the passwords for my four most important accounts, my bank, my password manager, and two email accounts. They all check out OK, but I think I’ll add Pwned Passwords to my bi-annual routines along with going through my password vault for unused/no longer wanted accounts, and while I’m at it, maybe I’ll increase the length of my passwords to twenty characters this January, since that seems to be the length everyone I respect most are already using.
Ernie