If they can, there’s something wrong.
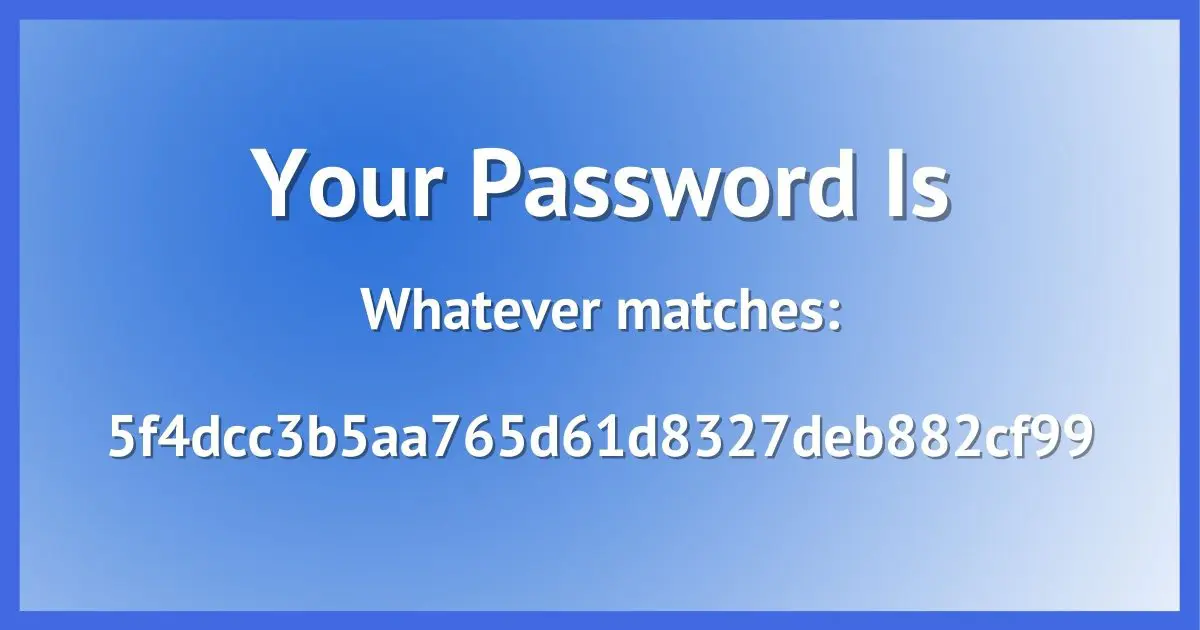
Wrong.
Believe it or not, most online services don’t know your password. Honest.
If they can tell you your password, that’s a really, really bad thing. It calls into question their understanding of all aspects of security.

Services don't actually know your password
Online services don’t know your password. Instead, they use mathematical calculations called hashes to confirm the string you typed today is the same as the string you typed when you set your password. Your actual password should not be kept or stored, and services should not be able to tell you what it is. This prevents breaches from exposing actual passwords. No matter what security measures your online services use, you still need to set long, unique passwords to remain safe.
Magic math
First, let’s look at why services don’t need to know your password.
There’s a mathematical concept called a one-way hash. A “hashing algorithm”, which is simply a series of mathematical calculations, transforms a string of characters (like a password) into a very large number — a “hash”. An appropriate hash algorithm has some important properties.
- It’s consistent. The hash will always return the same number for the same string.
- It’s unique. It’s extremely unlikely — so unlikely as to be pragmatically impossible — for two different strings to produce the same hash.
- It’s one-way. It’s impossible to take a hash and calculate the string used to create it.
It all sounds magical, and in many ways, it feels so. Hashes are a fundamental component of cryptography.
To be clear, this isn’t a simple formula. It’s complex, and can really only be done by a computer. But it works.
Checking your password versus knowing your password
Done correctly, an online service handles passwords like this:
- Setting a password. When you set or change your password, the service takes your new password (a string) and calculates its hash (a number). It stores the hash value in its account database and completely discards your actual password. All it knows thereafter is the hash.
- Checking a password. When you log in later and enter your password, the service calculates the hash of whatever you type. If that hash matches the hash calculated when you set the password, you must have typed the same thing both times. You typed in the correct password.
So the service only saves the hash. It never needs to keep your actual password.
Help keep it going by becoming a Patron.
Why it matters
I’m sure you’ve heard of various database breaches in the news. A hacker breaks into the servers of some service and steals their database of user accounts. If the database contains only properly-created hash values, the hacker can’t get your password. There’s no way to turn that hash value back into the string that created it: your password.
If, on the other hand, the database contains actual passwords, the hackers will have complete access to all of the accounts, including yours.
So if you encounter a service able to tell you what your password is, they’re not doing security right. And I’d be very wary of what other kinds of security-related things they might also not be doing right.
You still need strong passwords
Properly implemented hashes are fundamental to good security. But that doesn’t mean you can let your guard down. There are potential weaknesses — not in design, but in implementation — of password storage schemes. They’re all thwarted by actions you can take.
First, if a standard hashing algorithm is used, it’s the same algorithm everywhere. For example, the bcrypt algorithm (a currently-recommended algorithm) returns this for the password “password”:
$2y$10$4V9fL5v/jy9/SZ.vzyaX4uvkyd13NS0o5kJqFTDA5Cso9wntPGGPG1
Anyone, anywhere, using the password “password” on a system that uses the bcrypt hash on the unmodified2 password will have that same hash value.
Hackers know this, and have built tables (called “rainbow tables”) of all possible passwords up to a certain length (typically 8 characters) hashed using common hashing algorithms. You can’t calculate the password from a hash, but if you’ve calculated all possible hashes for all possible passwords beforehand, you can just look it up. Even tables of less than all possible passwords are useful to hackers. Tables containing hashes of the million most common passwords, for example, allow hackers to succeed a surprising amount of the time.
Your solution: make a long password that’s unique. The best would be some number of random characters. Creating a rainbow table of all possible 16 character passwords, for example, isn’t feasible. As long as your password is long and unique, you aren’t vulnerable to this possibility.
In that same vein, if two different services use the same password hashing algorithm, breaches at both might expose the fact. If you use the same password at both, they’ll find the same hash at both. If your password at one ever becomes known by other means, it’s immediately clear that it’ll work at both.
Your solution: use a different password (again, long and unique) everywhere. That way, no matter what gets exposed at any service, none of your other accounts are put at risk.
The best way to keep track of all those long, unique, random-character passwords is using a password vault. They are safe and highly recommended by security experts and random tech-advice writers like me. Here’s why.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
Footnotes & References
1: While displayed and stored as a string, technically, it’s still just a very large number.
2: Good security practices by the service would modify your password with something called “salt”. This is something added to the password, unique to the service, to prevent this situation. But not using salt is still common.




If you have a simple password, they may be able to use a rainbow table to convert the hash into your password. If your password is PASSWORD for example, if they know how the passwords are hashed, the run various simple passwords like PASSWORD through the hash and create a table called a rainbow table. That can then be used to go from the hash to the password.
A website should salt the hashes, then the rainbow tables become useless.
Absolutely. And yet some (still) do not. And occasionally the salt is hacked, allowing new rainbow tables to be generated.
Thanks for the opportunity to get an answer to my biggest computer problem. I have been using computers since my first Radio Shack (no hard drive) computer. Now I am 72 and have been diagnosed with memory problems. This has caused much stress! I try to keep my passwords in a book but there are times it doesn’t work. This could be because I had to change the password and forgot to change the book or lately, I just don’t know. I am on my iPad a lot and will miss it!
Is there a safe program I can use on the iPad and lap top (not Mac) that will remember passwords? Hope you can keep me using my computer!
Doug
I use and recommend LastPass for remembering passwords. So does Leo. The PC version is free, and the version for iPad, iPhone and Android costs $12 a year, but that $12 covers all your phones and tablets, and keeps the passwords in sync for all of them. It’s a great deal.
http://askleo.com/lastpass_securely_keep_track_of_multiple_passwords_on_multiple_devices/
It’s now gone up to $36 a year and still worth it.
Hi Leo,
I found this article very informative and interesting but it has prompted one question and that is why we may have to change all of our passwords as a result of Heartbleed ?
Because they MAY have been captured by hackers during the time the various servers were vulnerable to the HeartBleed problem. That means it’s theoretically possible that any time in the last two years when you logged into a service which was HeartBleed vulnerable a hacker could have stolen your password. I don’t know that this is/was common, but since we can’t prove it one way or the other changing your passwords is the safest option.
If I have understood correctly, (and I found your explanation brilliantly clear), every one of the major thefts of passwords which have been publicised over the years, (as well as the Heartbleed thefts), are actually a manifestation of the fact that the host is maintaining the actual passwords on their servers. If they were storing only the hash, the hackers could not steal them. This speaks volumes to the security services of the major sites we all subscribe to.
This is not quite correct.
First, most major thefts have not been “of passwords“. They’ve been of account databases with hashed passwords. Nonetheless, common best practice after such a theft – even without passwords – is to encourage people to change their passwords “just in case”. (Obviously if the theft was truly “of passwords”, then yes, those were bad security setups. But as I said, if you read the accounts closely more are not.)
Second, the situation is more complex than I got into. (Remember, the question was only why a service couldn’t tell you your password.) It can sometimes be possible to use tables of hashed passwords to break into accounts 1) if the hash is done “poorly”, and 2) if poor passwords are used. I think someone else mentioned rainbow tables – compute, off-line, the hashes for all possible 8 character passwords, then just look up the hash to find the password. There are techniques to make this more secure both on the server (do hashes properly) and in your control (longer passwords being the one in your control).
Finally, poor password choice remains a serious issue. Very often simply knowing the account login ID, which is stored clearly in the database, and then just trying the top 1000 most popular passwords (slowly, over a few days on a distributed botnet) will break in to an alarming number of accounts.
Another good article Leo, but a couple things I’d add:
As far as Heartbleed goes:
DO NOT CHANGE YOUR PASSWORDS UNLESS YOU CAN VERIFY THESE 3 THINGS:
1) The website was running the affected version of OpenSSL (v1.0.1 and v1.0.2 beta)
2) The website has applied the necessary patch for the affected versions of OpenSSL
3) The website has updated their certificates
Very basically, if your website is still running OpenSSL v1.0.0 it is not vulnerable to Heartbleed. Heartbleed allows the affected OpenSSL memory to be read on the website’s server. If it wasn’t patched and certificates updated, the site is still vulnerable and you’re putting a new password into the memory (which remains active until rebooted) for the hackers to access. Servers can go for months or years without rebooting. Wait until all 3 of these things are verified, or you’re wasting your time and putting your new password into memory to be hacked.
I’m still not a fan of changing passwords without a good reason – you’ve given it to someone intentionally or unintentionally, or malware has infected your system. A password which was strong a decade ago remains strong today. 🙂
Which is why I referenced the LastPass tool – it’ll advise you whether or not the password should be changed based on those criteria.
Most passwords will be locked out if you make a set # of attempts without success, so why would a botnet attempt be able to work where there are 1000 attempts?
That’s why I said slow & distributed. Slow enough to not trigger the “too many failures too quickly” problem and distributed to not trigger “too many failures from the same IP address”. Even if it takes a few days the results would be valuable to the hackers.
Let me see if I understand correctly. If I click on the “LostPassword” link at a site where I have an account, and they actually email me my password, that is not good, but if they email me a link to enable me to reset my password or give a me a “hint”
I have provided previously, that is ok?
Yes.
If they can mail you a password, it means they have your password on their servers, and that is vulnerable to mass theft. If they send you a password reset key, that is essentially a new one time password with which you can create a new password. This one time password is sent to an email address which only you *should* have access to. I stress should because there may be ways of gaming that system if they’ve hacked that email account, but it protects the vast majority of passwords on their system.
Thank you for making the password reset situation clear. You answered a question I had not thought to ask and I will now cease being frustrated when the situation arises. I have been using Password Safe for years but it is not always handy when I am away from home.
There is a difference between a hack from outside the company and a hack from inside the company, with a hack from inside a company much more dangerous. A hack from outside the company mostly only gets the data in the form the company stores it in. If the password checking file is encrypted, then they get the encrypted file with hash.
But all passwords for a site are run thru the same hashing algorithm. If this hashing algorithm is known, or found, then either a rainbow table can be made for that algorithm, or a hash file can be deconstructed by reversing the algorithm. A hack from inside might be able to get the hashing algorithm, since that has to be stored in the system somewhere for the computer to use it. Some companies have not changed their hashing algorithm for decades. It is sort of hard to, since once the passwords are hashed, changing the algorithm would result in a different hash than what is stored.
Updating or changing the algorithm after an hack should be normally done, this would require all the users to reset their passwords, resulting in a new hash for each user. Then the old hash file could be deleted after some time. Anybody that has not changed their password by that time would have to set up a new account.
Just like longer passwords, longer more complicated hashing algorithms are more secure, but can slow down the processing in the computer. (Not as much of a concern as it was in the past)
“If this hashing algorithm is known, or found, then either a rainbow table can be made for that algorithm” Yes, that’s possible if you use a short password.
“or a hash file can be deconstructed by reversing the algorithm.” No, that’s not possible. Good encryption algorithms can’t be reversed. That’s the beauty of encryption.
Couple of things:
“a rainbow table can be made for that algorithm” — True, but a rainbow table (a table that lists all possible passwords and their hash values) is practical only up to a certain password length. This is why we harp so much on password length. A rainbow table for, say, all possible 16 character passwords is completely impractical at this point in time. (And why I default to 20.) It’s also why common passwords should be avoided, since generating a partial rainbow table of all common passwords is pretty trivial.
“a hash file can be deconstructed by reversing the algorithm” — No. That’s the point of a hash, it’s one way only. You cannot get the passwords from the hashes by calculation.
Hi Leo, This article really made me think twice about security on sites that I use. I recently subscribed to a site using PayPal to pay for the subscription. When I couldn’t logon the next day, I submitted a “forgot password” request. I was shocked when I received an email that had my user name correct, but had combined it with my PayPal password. There was no option in the email to reset the password. I was actually able to logon to the subscription site using the PayPal password. I immediately changed passwords on both accounts, but this really left me worried about 1. How could this happen? 2. The security of both sites, and 3. How do I better protect myself?
Hard to tell what happened exactly, but see below for some speculations. To respond to your 3rd question: Never cross-contaminate account credentials across sites. That means, for example, don’t use your Google login credentials to sign up on another site or don’t use your PayPal credentials to subscribe to anything else. Each account should have its own distinct set of username and password. In the current situation you’re describing, just changing your password may not be sufficient. I’d delete/close the subscription account entirely and change your PayPal password again. But, before you create a new PayPal password, clear your browser cache (cookies, etc). Then get online and investigate this subscription site to check its reputation. Start with the various URL check sites, such as offered by Google, Norton, TrendMicro, etc.
The fact that you got your current PayPal password in the email is disconcerting. It suggests that PayPal is storing your actual password text in its database, which is a HUGE security hole. On top of that it suggests that their database is accessible by other sites. So, when you ask “how do I protect myself”, first ask yourself “why do I need PayPal”? Why would you interject a third party entity between you and your money? If you paid directly with your credit card the parties involved would be you and your bank. Now you have PayPal sticking its nose into your financials. If you use a major bank and a credit card, you have sufficient protections. Another safeguard is never use the same email address for financial sites and social/subscription sites.
About what could have happened? Optimistically, that subscription site may be an affiliate of PayPal, in which case all your info is being shared. If you were on the subscription site’s page and there was a PayPal link where you logged in and typed your PayPal password, the password could have been taken directly from that page. (Yes, they can do anything on a web page). Or, depending on the site you thought you subscribed to and how you created your account, you may have been phished and hacked.
As you say, it’s hard to know what happened, but my theory is that the subscription site presented the login dialog, and slurped up the PayPal password. I’m absolutely convinced that Paypal does NOT store actual passwords, and does NOT share password information with anyone, anywhere, at any time.
Without more details and specifics, though, it’s all just speculation.
Just to clarify…this was a subscription service for archived newspapers. I have used it on and off for years, and already had a password for the account, and was logged in when re-subscribing. I used PayPal at checkout and was presented with the screen to log on to PP with my account credentials in order to complete payment. Have done this many times over the years without a problem. The process completes, the purchase has been made. All of the steps from order, through checkout, and through completion of the purchase were normal. After doing a few searches, I logged off of the site. You know the rest of the story from my original comment. Technically, I am using a CC, just linked to PP so that I don’t have to give out my CC number. Maybe this is no longer a safe option.
“Slurped up the password” has the sound of Phishing. Is that what you meant?
I’m reluctant to call it that, specifically, because we Just Don’t Know. I like your theory of accidentally entering the password elsewhere due to confusing layout. (I’ve done that.)
PayPal doesn’t send you your password when you forget it. It sends a reset link as best practice dictates. It doesn’t appear that she used her PayPal cedentials to open the site. She used PayPal to pay for access. Those are different. PayPal is a safer method of payment than entering a credit or debit card number as it protects you against the site you are sending money to from misusing it.
That site she opened that account on did security wrong and stored her password. The only way I can think of that would allow them to send her the password was if she accidentally typed the PayPal password in the field to set a password for that site. Changing the passwords should be enough as long as they were long strong (at least 14 character) unique (not used on any other sites) passwords
Thank you, Mark. It was the subscription site that sent me an email containing my user name for that site and the password to my PayPal account. As I previously stated, there was no reset link. I have been using the internet almost as long as it has existed, and have never had any site send me a User Name\Password combination. I don’t use the same email addresses for all accounts. I have unique long passwords for every account. I use CCleaner regularly, two-step authentication on financial accounts, etc. It is extremely disconcerting to be expecting a reset link and receive the email with a password to another account.
I could be wrong, but the only thing that comes to me is that that website has a confusing signup page and you accidentally entered your PayPal password on their page. When a purchase is made via PayPal, you are sent directly to the PayPal login page and you log into PayPal directly on the PayPal web page. It it happened any other way , you would have entered your password on the subscription page.
Good day, how do I recover my facebook account. Even if I activated the two-factor authentication. I can’t use the phone number also my Gmail account that I added to. Please me to recover my account. I also try the Trusted reveals and when I’ve changed the password and try to log in using the new password it’s still not working. Please help me to recover because I that for my studying. I’m looking forward to your reply. Thank you I’m from Philippines
For each of the affected accounts, follow the “I forgot my password”, or “Having trouble logging in” options that they present. Follow them CAREFULLY. If they do not work then your account may not be able to be recovered.
Remember: it is CRITICAL that you maintain your recovery, and two-factor information currently. If you change or lose your phone number you MUST update your account. If you do not you run the risk of losing your account forever.
Good day, how do I recover my facebook account. Even if I activated the two-factor authentication. I can’t use the phone number also my Gmail account that I added to. Please help me to recover my account. I also try the Trusted reveals and when I’ve changed the password and try to log in using the new password it’s still not working. Please help me to recover because I that for my studying. I’m looking forward to your reply. Thank you I’m from Philippines
Unfortunately, if you no longer have access to the recovery email account or phone number, your account may be lost forever. It’s important to always keep these up to date on your account.
https://askleo.com/a-one-step-way-to-lose-your-account-forever/
Plz my Facebook account back plz
We cannot recover hacked accounts, lost or forgotten passwords. Please see these articles for more information on your options:
https://askleo.com/how_do_i_recover_my_facebook_log_in_password/ and/or
https://askleo.com/how-do-i-recover-my-hacked-facebook-account/
Unfortunately, if you no longer have access to the recovery email account or phone number, your account may be lost forever. It’s important to always keep these up to date on your account.
https://askleo.com/a-one-step-way-to-lose-your-account-forever/