Another day, another breach.
When I originally wrote this in January of 2019, there had been a breach (referred to as the “Collection #1 breach“) containing something like three-quarters of a billion email addresses and plain-text passwords. It was newsworthy because it was huge and contained passwords for anyone to see.
As I update this in June 2025, we have yet another report of 16 billion passwords exposed in a record-breaking data breach, opening access to Facebook, Google, Apple, and any other service imaginable.
Naturally, the question I (still) get most is: what should you and I do?
The same thing we do for every breach, my friends; the same thing we do for every breach.

If you're in a breach
In most cases, there’s little you can do in response to a specific breach other than changing passwords if you know the services involved. Use every breach you hear about as an opportunity to review your account security to ensure it’s as tight as you can make it.
Once more unto the breach, dear friends
Breaches happen so often that it’s hard to take them seriously. A more likely reaction is “Oh, another one”, with little attention paid to the specifics. The most recent breach is worthy of a closer look for a variety of reasons.
It’s huge. The original report cited 16 billion entries. It may be the biggest breach to date.
It has email addresses. This is not new, but it is what makes most breaches noteworthy. You want to know if your email address was exposed. The odds are high.
It has passwords. This is the most devastating. Most breaches contain “hashed” passwords or no passwords at all. In this breach, apparently, passwords are there for anyone to see.
It’s an example of what’s possible. It’s a great example of exactly what can go wrong.
Help keep it going by becoming a Patron.
What we don’t know
We don’t really know where the breach came from.
We can infer from some data what service or services are included and what accounts all those email addresses represent, but we don’t know how they were collected. Current theory is that this is an amalgamation of the results of several info-stealers, meaning malware that somehow scooped up credentials on individual machines.
If you find your email address is part of this breach (haveibeenpwned may1 tell you; more on that below), what then? What concrete action can you take?
What to do for any breach
Here’s what you can and should do for this and any breach.
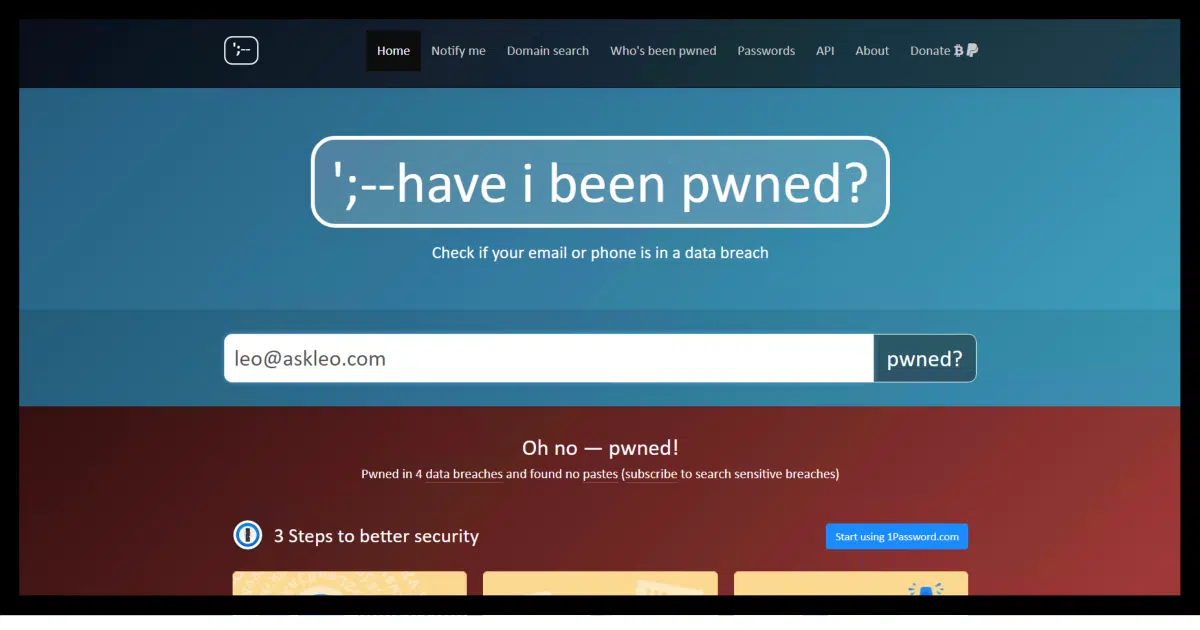
- Use haveibeenpwned.com to see if your email address is part of the breach. Consider signing up for notifications in the future. (If you own a domain (like I own askleo.com) you can also get notification of breaches for any email address on that domain.)
- Change your password if the breach involves a specific service you use.
- Get and use a password manager to make using long, strong, and unique passwords significantly easier. I use and recommend 1Password, but any of the major equivalents will do.
- Stop using the same password on more than one site. Seriously, stop it. I can’t underscore enough how important this is. Hackers try the email address/password combinations they find on one service against many others. Given how many people are lazy and reuse passwords, they’re often successful in breaking in. Using a password manager makes using unique passwords significantly easier.
- Create long, strong passwords. Use 14 characters at a minimum; I currently use 20. I don’t care if you use completely random characters (as I do) or long phrases of unrelated words (as I do for accounts where I need to remember and type the password). Length is most important, but make them complex while you’re at it. Again, using a password manager makes this easy.
- Add two-factor authentication to your account if it’s available. Yes, yes, I know, it’s not perfect. But it’s still an order of magnitude better than not having it enabled. Even if your password is exposed in a breach, your account remains secure and protected.
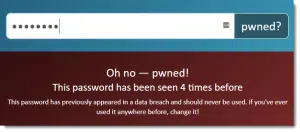
If you’re comfortable doing so, run passwords you’re worried about being breached through Pwned Passwords. I realize not everyone is OK with giving their password to a third party like that. I trust them, but you don’t have to.
It’s simple, really: if you have any concern about a password being compromised, change that password! Change it to something long, strong, and unique.
Do this
Every breach should remind us of the importance of account security. Security remains our responsibility. Even when taking the best steps to stay secure, stuff like this still happens.
Make sure your account security is as good as you can make it.
If you’re so inclined, also subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, reminders, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: As I update this, it doesn’t appear to include the results from this most recent breach yet.



This is nothing new. Collection #1, according to Brian Krebs, is actually a database of info that is several years old. I changed all of my important account passwords 2 or 3 years ago because of the last breach so I’m personally not worried. Not only that but I rarely use any form of my real name as a “user name.” I may be wrong but it feels like an extra layer of security to use a fake name as my user name.
It is and it isn’t. I think what’s new for most people is that is includes unencrypted passwords. We don’t actually know how old the data is .. could be several years old, could be more recent, but there’s no information on that. I suspect it’s relatively stale data, but given how many people a) use the same password everywhere, and b) never hear about or act on breaches, it’s still an important wake-up call.
I just learned about the Pwned Passwords this week when I got the email from Have I Been Pwned that my Yahoo email address was involved in a breach. That doesn’t surprise me. It was in the Yahoo breach a few years ago and I changed my password then and secured the account. So I’m at greater odds of being on subsequent lists from having been on the Yahoo breach list.
However, I ran a couple of my passwords through there (he doesn’t link your email address and passwords together, so is pretty safe) and found that I have one password that appears on a list. However, it’s not my Yahoo password. Without the links between email addresses and passwords, I don’t know if I have a problem or not. It’s a phrase (rather than a word) with a substitution scheme. It’s possible someone else chose the same phrase and used the same substitution.
Oh, well, time for a new password.
“I don’t know if I have a problem or not”. You do. Your password is “out there”. Change it, and never use that again. (Even if it wasn’t your account that caused that password to be exposed, it’s still a password that you use(d), and a password that is “known”. Hackers use the databases of known passwords against databases of known accounts. At some point your combination is likely to come up.
“At some point your combination is likely to come up.” – Likely? No, not really. If, by some bizarre coincidence, you and I share the same strong password and it’s leaked via a breach of one of my accounts, the risk of the password being used to attack the account on which you used it is exceptionally small. But why take that very small risk? If you use a password manager – and there’s really no good reason not to be using one – it takes seconds to replace the password. Seems like common sense, to me.
Absolutely agreed. That’s why I concluded “Oh, well, time for a new password.”
Another defensive step people can take is use more than one email address. Having a single email address serve as the userid for multiple websites/systems is a bad idea. Multiple email addresses does not mean multiple mailboxes. There are two approaches, that I know of.
1) Register your own domain and create an unlimited number of forwarded email addresses. For example, user1@mydomain.com and user2@mydomain.com and user3@mydomain.com can all be automatically forwarded to your current email address. Many domain registrars offer this service.
2) Pay for email with a service that allows for aliases. An alias, as the name implies, is just a second or 3rd or 4th or 5th name for one email inbox. This is probably a bit more reliable as there is no forwarding involved. On email provider that allows multiple aliases is Fastmail, no doubt there are others.
I use Microsoft’s free outlook.com email and that allows aliases.
I have been doing that multiple email address thing for 4 years. I own my domain and I currently have 30+ email addresses. My theory when I started this was that when I start getting spam I will know where the hacker found my email address. But it doesn’t really work. Turns out I would need over 600 (yes, six hundred) different email addresses just to give each subscription a unique email address, and then there’s all my email correspondents – Thunderbird doesn’t tell me how many email addresses are in my Address Book but I bet I’ve got as many as everyone else – a lot. It take several minutes to create a new email address and set Thunderbird up to manage it. No thanks. Only 1 or 2 spams get through each day so I have stopped creating new email addresses except for banking and other financial stuff.
One thing I am still doing, I don’t use the same identity on more than one site. Here I am “Boatman”. If you see that identity/username anywhere else it isn’t me.
I have one email address for all questionable signups. It gets more spam than my real accounts but that’s what it’s for. Surprisingly, I don’t get that much spam, even on that account. I believe the reason is that Yahoo has a great spam filter.
At Leo’s recommendation, I started using Simple Online Solutions for my domain name and email years ago. I couldn’t be more pleased, and would recommend them to anyone. (They are not free, but they are fair; as far as I am concerned, they’re worth every penny.)
So, you give your email or password to some website to “check” if it has been “breached”?
Do you also want to know a site where you can check your SSN?
You can also hand over all your personal and financial information to some site to check if you’ve been “breached”.
And don’t forget to tell Facebook that you’ll be on vacation for two weeks.
About this particular Collection #1: by most indications this was not a breach (such as hacking into the Equifax database) – this was a collection of data from 2000 previously stolen databases. Yes, a collection of several years of previously stolen databases will be large, and yes, the data would have been scrubbed so that there are plain text passwords. Leo, someday you should write an article about the distinction between a stolen database and a breached individual.
That’s why you don’t check your account on some random website. I trust Leo’s recommendation and I’ve looked into it myself. I truly believe this website is about protecting you, not stealing your info. Other websites I wouldn’t trust.
Hi Leo,
Is it true that with using LastPass that you don’t know what your passwords are? If true it seems nonsensical that you do not know what your passwords are.
Mike Wilhelm 🙂
I cannot tell you my banking password, for example. I can look it up in LastPass, if I need to, but since it enters it into the website for me I have no need.
If you want to know your passwords, and haven’t written them down somewhere, LastPass will save your info (and form fills as well) to a file on your computer. You can then print that and post it on your wall. 🙂
Good point. The following article on Ask Leo! explains how to do that:
How Do I Back Up LastPass?
So my email address has been breached – on Onliner Spambot
This is a sit I’ve never heard of before so does this imply that ALL of my passwords are at risk .
It does explain (maybe) why I’ve suddenly been getting more junk/spam
It means only that the one email address was breached. It’s typically unrelated to getting spam.
Looks like me in trouble;
Checked at the website Leo give and this is the result.
“Oh no — pwned!
Pwned on 4 breached sites and found no pastes (subscribe to search sensitive breaches)”
What now?
Change the passwords for those four accounts, and stop using those old passwords anywhere ever again.
Leo, it might just be me being a little dense, but what sites?
I was apparently breached on 1 site, again on the ‘record onliner spambot dump’, but what site does this relate to?
I can’t see what site I need to change my password on.
I really don’t fancy changing them all!
Andy
This particular dump doesn’t tell you. What you can do is check your high-value account passwords using the password checking function and then changing any and all accounts that show up there.
I give you credit for correctly quoting Shakespeare and saying “Once more *unto* the breach.” Most people, including several English teachers I know, think it says “*into* the breach.” Good for you.
Thank you Mark but I did read the article and I did follow the instructions regarding changing password etc.
But I can’t find what we need to do to remove Onliner Spambot. Or am I missing something blindingly obvious?
Your email address being listed with Onliner Spambot doesn’t necessarily mean you’ve been infected. It just means they have your email address and probably have sent you spam with malware attached. If you haven’t opened that attachment, you shouldn’t be infected. If you opened the attachment, you would follow the normal procedures for removing malware.
How do I Remove Malware?
Leo:
Thanks for your help leading us through what is now the minefield of internet security.
I was pwnd in this breach, and Starwood Hotels sent me this invitation:
“IdentityWorks℠ Global Internet Surveillance monitors whether your personal data is available on public websites, chat rooms, blogs, and non-public places on the internet where data can be compromised, such as “dark web” sites, and generates an alert to you if evidence of your personal information is found.“
Here, I can enter my credit card numbers, passport numbers, email addresses…. everything.
Sounds comforting, but if this place is ever breached I could not possibly be more in a world of pain. Am I wrong?
Should I take this offer up?
Many thanks for your thoughts here.
Lee
I honestly don’t know about “IdentityWorks”. I don’t currently have a monitoring service in place, though I’ve been offered. My approach has been to a) lock my credit reports at the three major credit bureaus, and b) sign up for CreditKarma so I can proactively watch myself. The problem is that, yes, for monitoring to work you do need to give some agency the sensitive information you’re concerned about. I don’t know that there’s a simple answer.
Monitoring is not a cure, solution or prevention. At best, all they will be able to tell you is that your data may be in some database where it shouldn’t be, or tell you, after the fact, that you have been breached. You should check your accounts on a regular basis and not wait for someone else to inform you that your bank account balance went to zero. You should put alerts on your accounts (through your own financial companies). You should also take time to research what is meant by “scanning the dark web”. Information that can be scanned is already public information (such as data dumbs of already compromised databases). Scans cannot get into proprietary databases (especially on the dark web). Besides, you don’t have to go very dark to dig up information on yourself – just pay a few dollars for a report on one of those personal information search sites.
IdentityWorks belongs to Experian. I decided to dig up the terms of user service agreement, which was not easy:
https://www.experianidworks.com/terms/. Naturally, you would expect that every word in there is designed to protect Experian, but this one caught my eye “… make no warranty that (i) the services are accurate, timely, secure, uninterrupted or error-free; and (ii) any results that may be obtained from the use of the services will be reliable.” Cool.
“Monitoring is not a cure, solution, or prevention. At best, all they will be able to tell you is that your data may be in some database where it shouldn’t be, or tell you, after the fact, that you have been breached.”
In and of itself, monitoring may not be a solution or preventention in the same way going to the doctor for a checkup without taking further action isn’t a solution or prevention. What you do with that information is the solution. In the case of the doctor, it’s taking his advice for medication or treatment, and in the case of a data breach, it’s changing your passwords.
Rather than relying on an emailed invitation, try a Google search for Starward Hotels. I don’t have to search. I know them as a chain of hotels. Now ask yourself if a hotel chain would be interested in protecting your credit card, passport number, email address, etc. If it was me, I would be running in the opposite direction.
I have always taken data breaches very seriously.
I have had my 2 primary email addresses registered with the Have I been Pwned website for notifications (should either be encountered in a breach) for many years.
I started using the free version of LastPass many years ago. Recently I signed up for Last Pass Premium, so I have access to the services found in their Security Dashboard (well worth the price). All my email addresses are now monitored by Last Pass (I have a few that are not used for communication [and that I have not registered with Have I Been Pwned], but as alternate addresses for websites that require/request one) too.
After upgrading my LastPass service, I found that a few of my accounts stored there were ‘at risk’ because their passwords were weak, so I changed the ‘weak’ passwords with longer, stronger ones.
About a year or two ago, I enabled 2FA on all my Internet-based accounts that supported it using Microsoft’s Authenticator app on my mobile phone. For any accounts that did not support this feature, if the account was not important to me (or I did not need it), I closed/deleted it if I could, otherwise I removed as much personal information as possible from the account’s user profile and changed the associated email address to one I created for non-2FA accounts.
Over the next few months (as time permits) I plan to go through all the Internet accounts I have stored on LastPass, and for any I find that I no longer want/use, I will go to the site and attempt to remove/delete the account, then delete it from LastPass. For the accounts I cannot delete (no delete/remove functionality available, etc.), I will do as I did with non-2FA accounts (described above).
Ernie
Leo, you wrote:
“Change your password if the breach involves a specific service you use.”
Contradictory.
Since breaches happen all the time, you would end up changing your password practically every other day…
But the you tell us we shouldn’t be regularly changing our passwords! 😮
(Yeah, yeah, I know. Facetious. But there’s a point: if breaches happen frequently then you have to change passwords just as frequently… which is a pain in the freakin’ ass…
Passkeys and a passwordless future would solve this.
Good luck with that wishful thinking. Did Congress pass a law against breaching anything not labeled as “password”?
Not at all. It’s just that when using passkeys there’s nothing useful to steal.
Do you actually think that laws do much if anything to prevent hacking? 🙂
That was sarcasm. Not much is going to stop breaches, hacking, scam, or stupidity.
Especially the last one.