When your data security matters.

BitLocker is one solution, and it’s much more than “just” password protecting the drive.
What you’re really looking for is encryption.
Become a Patron of Ask Leo! and go ad-free!

Protecting an external hard drive
If you have Windows Pro edition and plan to use your external drive only with other machines using Windows Pro, then BitLocker is a simple and quick way to encrypt your external drive with a password. If you need to support Windows Home edition or other operating systems, VeraCrypt can be an excellent solution.
A password alone is not enough
The reason you’re looking for encryption is that a password by itself isn’t enough.
For example, let’s say you somehow attach a password to a drive.1 Now someone steals your computer or gains access to that computer using some other operating system or technology that just ignores the password requirement. Or perhaps they perform some kind of forensic data recovery on the drive. Either way, they can bypass the password and access your files.
That’s not much protection.
What you want instead is to encrypt the data you care about. In your case, that’s everything on the drive. That means the data is inaccessible without your password or encryption key.
Approach #1: BitLocker
BitLocker is included in both Windows 10 and 11 Pro Edition. (A subset of Bitlocker was added to Home editions, but this serves only to perform full disk encryption on system drives.)
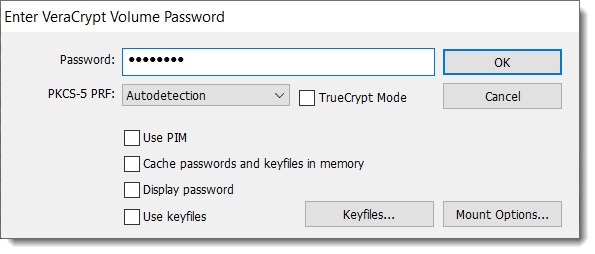
Right-click on the drive in Windows File Explorer and click on Turn on BitLocker.
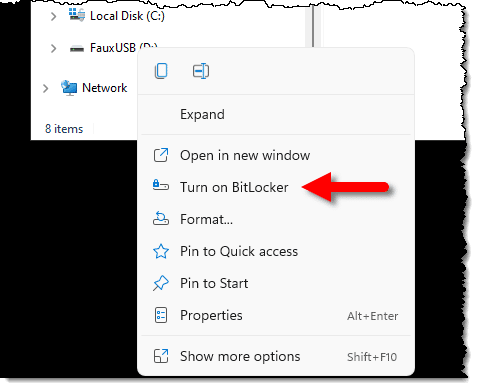
This will bring up a dialog to determine how you want to encrypt the drive.
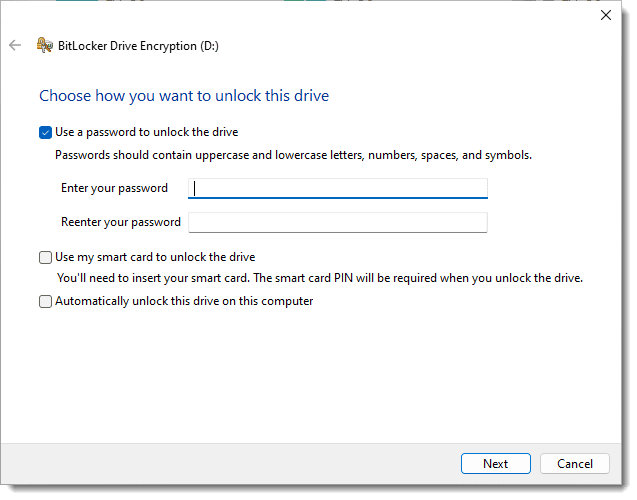
While there may be other options, “Use a password to unlock the drive” is perhaps the simplest and addresses your question directly. This is how you password-protect an external drive.
Windows encrypts the drive for you and requires the password you set to access that drive’s contents in the future. (When given the opportunity to save a recovery key, do so. That way, even if you forget the password, you’ll be able to regain access. Without the password or recovery key, the data is completely inaccessible.)
The only real “problem” that remains is that your drive can only be used with Windows and with Windows editions that support BitLocker. The drive cannot be viewed elsewhere even if you know the password.
Option #2a: VeraCrypt whole-drive encryption
VeraCrypt, the heir-apparent to the long-favored TrueCrypt, is a high-quality encryption program that supports everything we need: encrypting the entire disk like BitLocker, and requiring a password, also like BitLocker.
The difference is that it’s from a third party, works on any edition of Windows (include Home), and is compatible with other systems, including Mac and Linux.
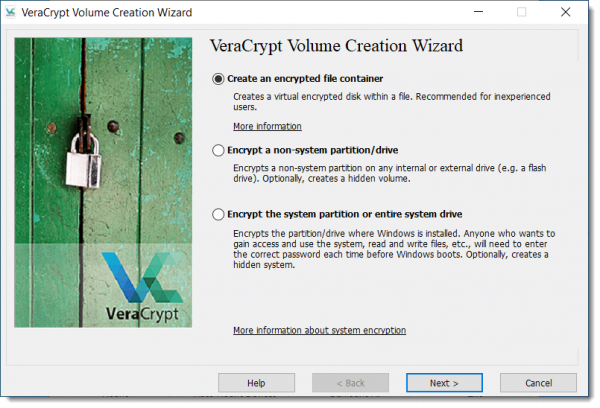
After installing and running VeraCrypt, click on the Create Volume button to open the Volume Creation Wizard. (A “Volume” in this context is a generic term for disk or partition.)
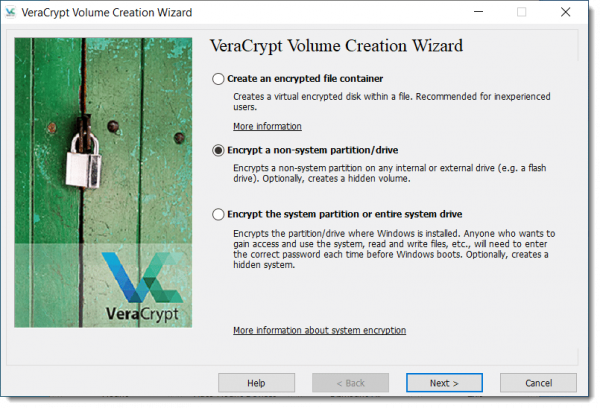
Select “Encrypt a non-system partition/drive” as shown above and click Next. On the next dialog, select “Standard VeraCrypt volume” and click Next. Then click Select Device… to select the drive you want to encrypt. You’ll then have the option to “Create encrypted volume and format it” or “Encrypt partition in place”. The former will erase everything on the drive, but is faster. The latter will preserve your data, but will take longer to complete. Click Next, at which point you’ll have some encryption options you can generally ignore. Click Next and confirm that the size of the device is shown correctly. Click Next to specify your password for the data you’re about to encrypt.
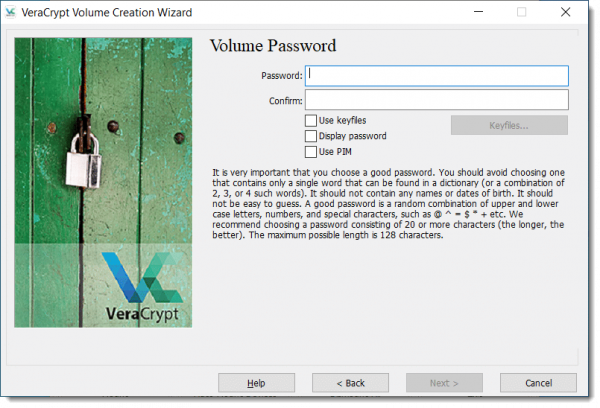
After completing a couple of additional screens, your drive will be encrypted.
Now in order to view the contents of the drive, you need to “Auto-Mount Devices” in VeraCrypt and assign it a new drive letter through which to access the encrypted contents.
There is no recovery key for VeraCrypt encrypted drives, so make sure your data is backed up and that you never lose the password you used to encrypt the drive.
When you encrypt a drive, the entire drive is encrypted, and you need the password to access any files (or folders) anywhere on that drive.
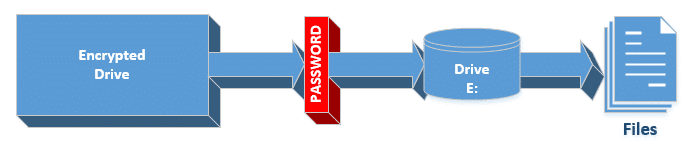
Option #2b: VeraCrypt volume encryption
A hybrid approach avoids encrypting the entire drive and instead creates a single (large-ish) file, which is then encrypted and used as a container for your files. Contaniers can be copied to other drives, and can be design to leave unencrypted space on the drive as well.
The process is similar to that above, but starts by selecting “Create an encrypted file container”.
Rather then mounting the drive, you mount that encrypted container and specify the password, at which point its contents become visible as if it were a separate drive. You can choose to place unencrypted data in the drive directly (accessed as E: in the diagram above), or deal with data that’s encrypted in the mounted file container (accessed in drive F: in the diagram below).
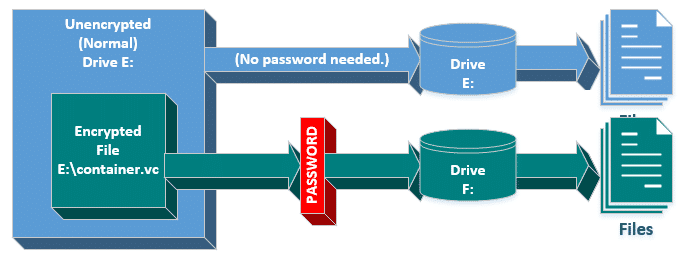
As long as the container is mounted and password provided, its contents are as available as on any drive. Once unmounted, the files are no longer visible.
VeraCrypt-encrypted containers have an advantage in that the container can be copied to other drives or devices — even using other operating systems — and mounted there for access as long as the correct password is supplied.
Do this
I tend to use BitLocker for drives that are permanently mounted in the computer, such as the system drive.
If I want encryption on an external drive, I use VeraCrypt — either whole-drive or container — because that gives me the flexibility of using that drive or container in any of my systems, whether Windows, Mac, or Linux.
I’d also suggest you subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: Technically not possible in Windows.




Totally agree with Leo: Truecrypt is the way to go. I’ve used for years and it works well. As Leo says, the portability is important.
I am all for security but I always have an eye on “What To Do When I Die”! Sounds morbid but you should consider this when encrypting your valuable data: if it will be valuable to others that you care about after you die – how do they get to it if you have encrypted. With Truecrypt you can leave your password without fear of the account being closed.
Right now I’m using a Linux Mint box connected to a portable hard drive that I encrypted with Truecrypt using a Win 7 machine. Truecrypt is totally the way to go.
One other caveat with TVeraCrypt is that you need to run it from an account with Administrator rights on the computer you’re running it from.
How do you feel about SED drives?
It REALLY depends on the implementation, but yes – when done properly, in a way that works with your OS, a self-encrypting drive is just as good. I tend to prefer software solutions, since I feel like I have more control, but that’s a minor point I think.
When I saw the title of this article, I was excited thinking that it would give me a way to protect my external drive from ransomware. Unfortunately, for reasons that are unavoidable, I have to leave this drive always attached to my computer, making it vulnerable to any ransomware that decided to encrypt this USB external drive. Again, unfortunately, this is the drive that also contains my image backup, so any ransomware encryption would make my image backup worthless.
In the case of ransomware, any pre-encryption of my external drive wouldn’t help as the malware would encrypt it again with its own key anyway making it unreadable to me.
I was hoping that there might be a simple way to password protect the external drive from ransomware attacks, rather than from physical attacks as mentioned in this article. Basically, I want to keep the ransomware from accessing my backup USB drive somehow.
Any ideas?
@Thomas Tomaszewski
Caveat: I use Linux, so may be different in Windows. I just did a full volume encryption on a USB stick with Veracrypt. On Linux, the stick will not mount unless you first open Veracrypt and enter the password. Once the password is accepted the stick mounts normally. This says to me that the stick (or a USB disk drive) can be left connected to the system but unmounted until you need to use it. Malware (ransomware) could not access as long as the device isn’t mounted. My problem is this: I use my external HD to do a monthly offline (boot from a CD) bare metal backup. Since Veracrypt isn’t running when the system boots to a CD there’s no way to access the disk to do the backup. Should be no problem doing any backups when Linux is running however, so my daily file backups should work as long as I make sure the disk is mounted before and dismounted after.
An addendum to my previous post. I think the entire external volume would have to be encrypted. If you just use an encrypted “Container” file then the disk drive could seemingly be mounted by malware without a password and then the encrypted container is just another file on the disk drive to be encrypted by the malware. If the entire drive is encrypted then the password is required to mount it.
Don’t currently encrypt. But with so much going on these days with ransomeware maybe I should. I live in an area where I feel pretty safe with my always-at-home laptop. And when I am not using my external hard drive(s), these are physically dismounted. So I presume they could not be held hostage (unless there is ransomeware that could activate when I physically mount them again?!).
But do I understand that some ransomeware, etc. could infect my mounted external drives, even with these being password protected? If so, how?
Any one with a reply???
Since BitLocker is not for Windows 7 Professional, is this of some help, even though it is just at the file level?:
What is Encrypting File System (EFS)?
Encrypting File System (EFS) is a feature of Windows that you can use to store information on your hard disk in an encrypted format. Encryption is the strongest protection that Windows provides to help you keep your information secure.
Some key features of EFS:
* Encrypting is simple; just select a check box in the file or folder’s properties to turn it on.
* You have control over who can read the files.
* Files are encrypted when you close them, but are automatically ready to use when you open them.
* If you change your mind about encrypting a file, clear the check box in the file’s properties.
Note
EFS is not fully supported on Windows 7 Starter, Windows 7 Home Basic, and Windows 7 Home Premium. For those editions of Windows, if you have the encryption key or certificate, you can do the following:
* Decrypt files by running Cipher.exe in the Command Prompt window (advanced users)
* Modify an encrypted file
* Copy an encrypted file as decrypted to a hard disk on your computer
* Import EFS certificates and keys
* Back up EFS certificates and keys by running Cipher.exe in the Command Prompt window (advanced users)
Does taking a non-system disk offline using Windows Disk manager give any extra protection against malware or ransomware?
It depends on the malware software and how much effort its programmer put into it. Remember that a malware, especially ransomware, is software written by a very knowledgeable programmer. It can easily get into the Registry and do anything it wants (and it does), including mounting all “hidden” drives and then attacking them. But hiding drives in Disk Manager is additional protection against the lazy malware programmer. If you’re doing that, remember to also hide your system recovery partition.
It should yes, for most ransomware. While it’s POSSIBLE that ransomware could be written that deals with it, I’m not aware of any that would.
One thing to remember, if the malware just wants to destroy your data without demanding a ransom (I suppose it’s possible) then any drive that’s connected to the system can be foermatted whether it’s encrypted or not.
Not having used VeraCrypt before, I’m wondering how often you have to enter the Password. If you make it a real long one, and you have to enter it whenever you save a file, that’d be a pain. So is it only when you first boot up?
You log in with a password to Veracrypt which mounts the volume as a logical drive. It stays mounted and open for reading and writing until Veracrypt is closed.
You only have to enter the password once. The encrypted container will be accessible as long as you don’t reboot or dismount the container. Just have your password manager generate a strong password, then save it in a secure note (that’s for Lastpass… I’m sure you can do it in any PW manager). When you want to open the encrypted container, just bring up the secure note in password mgr and copy/paste the password. For safety, though, write the password down and put it in a safe place.
When you boot or mount the drive.
One thing to remember: any drive that’s connected to the system can be formatted whether it’s encrypted or not. If the malware is just designed to screw up your system it could format the encrypted drive just as easily as any other.
“Included in Windows 7 and later, in all editions except “Home” or “Starter”. Unfortunately Bitlocker’s not available for Windows 7 Professional – only Ultimate & Enterprise. Too bad – it would be very useful in the office.
Good point, I was mistaken. I’ll update the article. In the mean time: VeraCrypt. 🙂
I’ve used TrueCrypt and now VeraCrypt for years. Wonderful, but that’s only folders. I need to encrypt my entire 1TB EXT USB drive but the directions on VC are horrible! [great software, terrible help]
I can’t find the steps. Yes, it’s known it can be done but does not explain how.
Does one begin with an empty drive?
Then run VC to that drive?
Then move data to the drive and then, what? Close VC?
Or…?
I am confused
I’d go with VeraCrypt over Bitlocker in this case for the sake of compatibility. Bitlocker requires a version of Windows Professional or better. VeraCrypt works on Windows Home, Linux, and MacOS.
Like bob, I tried VeraCrypt, but I used it only for a folder containing sub-folders and about 500 documents. Luckily, before I created an encrypted folder using VeraCrypt, I first copied all the files to a USB. I wanted to make sure VeraCrypt worked. Unfortunately I had too many problems with VeraCrypt especially when I wanted to add a document. I gave up. Since I have Windows 10 Pro, I decided to use BitLocker but I created an encrypted file container as a VHD (“subset” of one of my drives). It works. My only beef, and I can not figure out how to do it, I can not easily re-mount the VHD after I dismount it. I have to use Disk Management to mount the VHD. Someday I’ll find an easy to make batch file (*.bat) that will properly dismount the VHD so I can mount it again by clicking on my [some name].vhdx file and entering my password.
I fixed my problem (My only beef, and I can not figure out how to do it, I can not easily re-mount the VHD after I dismount it.). I decided to get rid of the VHD and re-partition my 2T Hard Drive. I turned on BitLocker for the new partition. That partition has my important documents.
I hope your important documents are backed up.
Hi Leo, first of all thanks for your informative videos.
I have both a Macbook pro and a desktop windows PC and Veracrypt seems perfect for my external SSD.
The only thing I’m wondering is whether this affects the speed. My SSD is a Samsung 2.5″ SATA one with transfer speeds of around 500 MB/s, which is already noticeably slower than my internal SSD and probably just about enough for my requirements (I have apps, games and large media files on the SSD). I’m wondering whether Veracrypt might slow it down even more or is the performance difference negligible once it’s mounted?
Thanks
My guess is the speed difference is not the SSD itself, but rather the interface (I assume USB) which is slower than the internal connections available to the system.
Two things:
1) I expect speed will be roughly the same VeraCrypt or not. It’s the amount of data being transferred that seems the bottleneck here, not the encryption, and the amount of data will be roughly the same.
2) Why not try it?
I use VeraCrypt full disk encryption on my system drive. I don’t notice any speed difference in operation, but it takes a minute or so longer to log in to Windows.