Two newly discovered vulnerabilities have been getting a lot of press recently. Much of it has been quite sensationalist, due to the nature of the underlying issues.
The flaws are in hardware design — specifically the CPU — and not just one CPU, but apparently a wide variety of CPUs — meaning that just about any computer or device using the most popular CPUs of the last couple of decades is probably vulnerable to the issue.
So, to answer everyone’s first question: yes, your computer or mobile device is likely affected.
The next question is, what to do about it?
Step one: don’t panic.
Become a Patron of Ask Leo! and go ad-free!
Protecting against Spectre and Meltdown
Protecting yourself is, honestly, nothing particularly exciting. In fact, it’s just the list of things that you’re hopefully doing already.
Back up. This is not unique to these vulnerabilities. Backing up protects your data from any malware that happens to make it to your machine, as well as a raft of other unrelated issues. If you’re not backing up, start.
Avoid malware. This seems obvious, but it’s one of the fundamental truths about almost all vulnerabilities: without malware to exploit them, the vulnerabilities are benign. Put another way, if you never, ever, allow malicious software on your machine, then it doesn’t matter that these vulnerabilities exist. Ultimately, it’s nothing more than best practices for staying safe online.
Keep all software as up-to-date as possible. Software vendors are rushing out updates and patches to address these vulnerabilities. Even chip manufacturers are developing firmware patches, in some cases. This is another reason why I so strongly recommend keeping updates on automatic, and always on: automated updates will install most of the fixes for these problems without you doing a thing. (Though there are a couple of catches in this case, which I’ll discuss below.) In short, enable automatic updates.
 And, of course, pay attention to update notifications from your software or hardware vendors. (I expect scammers to try and leverage all the fear and uproar, so make sure the notifications are legitimate before acting on them.)
And, of course, pay attention to update notifications from your software or hardware vendors. (I expect scammers to try and leverage all the fear and uproar, so make sure the notifications are legitimate before acting on them.)
That’s basically it. Back up, stay safe, keep up-to-date.
Like I said, the kinds of actions you should be taking anyway.
The caveats
There are two caveats to mention regarding the “keep up to date” step.
First, not all software will be updated. For example, older versions of Windows — like XP and Vista, which are well past end-of-life — are likely to remain forever vulnerable. If you must run no-longer-supported software, then the burden is on you to keep your system free of malicious software.
Second, it turns out that some anti-malware programs can cause your system to crash — as in blue-screen — if you take the operating system update before the anti-malware tool itself is updated to “play nice.” Microsoft has developed a signaling system via a registry key that anti-malware tool developers can set to indicate that it’s OK to update the operating system. What that means is that you will not get the update until your anti-malware tool has been appropriately updated as well. Needless to say, Windows Defender, which I recommend for most folks, will update in sync with the vulnerability patches.
The action here is simple: check with your anti-malware tool vendor to see if they’ve addressed the issue appropriately, and update those tools as soon as possible thereafter.
The Windows update you want to make sure you have will be some variant of 2018-01. Exactly which one — as indicated by the referenced KB number — will vary depending on your system.
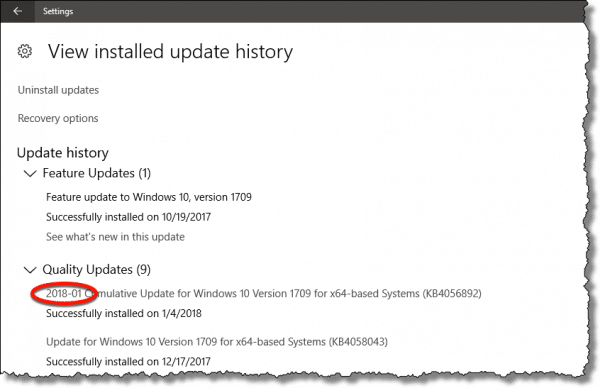
It’s more than the operating system
What’s fascinating, to me at least, is the scope of the response.
All current and popular operating systems — Windows, Mac, and Linux — are being updated.
Current and popular browsers — IE, Edge, Chrome, Firefox, Safari — are being updated, as apparently at least one of the vulnerabilities could theoretically be exploited by JavaScript code downloaded from a malicious web site.
I believe I’ve even seen firmware updates discussed. While I’m unclear on the specifics, these would be provided by your computer manufacturer.
What’s the risk?
There’s been a lot of hands-in-the-air, world’s-coming-to-an-end press about the impact of these two vulnerabilities.
Sigh.
Don’t panic.
As of this writing, there’s no known exploit in the wild. No malware has been discovered that tries to use these vulnerabilities to do anything. As I understand it, it turns out to be somewhat difficult to do. Not that there won’t be — I’m sure malware authors are rushing to see if they can exploit this before the majority of systems are updated, but as of right now, they haven’t done so.
The risk is information leakage. Theoretically — and I have to stress that this has not happened yet — malware could examine the contents of memory (RAM) that it shouldn’t be able to. Depending on what’s in the memory, that could be useless, or it could expose sensitive information. The press I’ve seen likes to focus on the potential to expose passwords that happen to be in memory, but my prediction is that authors are probably more interested in retrieving information that would allow them to somehow gain administrative access to the device and install more invasive malware.
Remember, reading anything in memory is nothing new. Malware that happens to gain administrative access — which is the goal of most malware — can do anything. That includes reading anything that’s in RAM or stored on your hard disk. This is simply a new way to do so.
That’s why it’s so important to avoid malware.
OK, but, what are these two things?
Spectre and Meltdown are two exceptionally complex, esoteric side effects of how modern CPUs try to run software as fast as is possible.
In all honesty, you don’t need to understand them in order to know they’re there and keep yourself safe. And, I’ll say it again, they are complex. But I know that folks are insanely curious about such things, so I’ll try my best to simplify my (admittedly limited) understanding of these two critters.
And to be clear: every analogy is flawed. Almost by definition, trying to come up with a simple analogy to a complex situation leaves information out. If you’re a whiz at CPU architecture, this section — and my gross over-simplification — is not for you. 🙂
First: reading memory versus calculating memory
Both vulnerabilities share one common feature: they gain access to areas of RAM, not by reading it directly but rather by using characteristics of the CPU cache to calculate it.
Let’s say I have a shuffled deck of cards. I place one card at random in my shirt pocket. Normally, you could reach into my pocket, pull it out, and see what it is.
In our analogy, though, you’re never allowed to see the face of the card. In fact, you can’t even see me or my pocket. All you can see is the table between us.
You now ask me to place a specific card face down on the table. For example, you might say “Put the Ace of Spades on the table.” I look through the deck, find the card, and put it on the table — face down — and then put it back in my deck. Then you say, “Put the Two of Spades on the table”, and I repeat the process.
We repeat this, working our way through the cards, until you ask for the card that happens to be in my pocket. When you ask for that card, I reach in my pocket, pull the card out, and put it on the table, and then remove it from the table once again.
All you’ve seen is the backside of cards appearing on the table each time you ask for one. It’s just that one of them happened to appear faster than the others, because it’s quicker for me to reach into my pocket than it is to look through the deck.
You’ve just calculated which card I have in my pocket without ever having seen it.
My pocket is a “cache”, where I can put things to be accessed quickly. The goal of both Meltdown and Spectre is to cause something that you shouldn’t be allowed to see to be placed into a cache, and do so in such a way that you can calculate what it is without even needing to see it.
That timing that allows information to be discovered without actually accessing it directly is what many of the reports on these issues refer to as a “side channel.”
Meltdown
Meltdown gets its name from the fact that it effectively “melts” the barriers put in place to protect data within a running computer.
It takes advantage of the fact that modern CPUs are always “looking ahead” at what’s coming next, and begin processing instructions before they’re needed.
Let’s say you’re allowed to look at all the cards in our deck of cards except the Clubs.
I have a shuffled deck of cards.
You ask me for the first card, and I bring it out, look at it myself, see that it’s not a Club, and then show it to you.
You ask me for the second, and we repeat the process. I’m pretty quick to catch on to what’s happening, so while you’re looking at card #2, I grab the third card and put it in my pocket.
You ask for the third, which I quickly grab out of my pocket, see it’s not a Club, and show it to you. Once again, while you’re looking at card #3, I put the fourth card in my pocket, since I know what you’re going to ask for next. (My pocket can only hold one card.)
You ask for the fourth, I look at it in my pocket, and see that it’s the Three of Clubs. I tell you that, no, you’re not allowed to see this card, and I put it back in my pocket.
I left the card in my pocket/cache. You can now use the technique above to calculate what’s in my pocket without seeing it.
Spectre
Spectre gets its name from a CPU optimization technique known as “speculative execution”. It sounds like so much magic, but as it runs programs, a CPU attempts to guess or “speculate” what might be needed, before it’s clear whether or not that need will arise.
Back to our deck of 52 cards. You’re still not allowed to see any of the Clubs. This time, however, all the suits in the deck are sorted together — all the Hearts, then the Diamonds, then the Clubs, and lastly the Spades — but within each suite, cards are in random order. You know the order the suits will come in, but you don’t know what value each card will have.
You ask me for the first card and, since it’s not a Club, I grab it from the deck, show it to you (it’s a Heart), and put it back.
You then ask me for the fourth card in the deck. Since it’s also not a Club, I grab it, show it to you (Heart), and put it back.
You then ask me for the eighth card in the deck. Since it too is not a Club, I grab it, show it to you (Heart), and put it back.
But I’m sensing a pattern here. I speculate you’re about to ask for the 12th card, so while you’re looking at the eighth, I grab the 12th (another Heart), and put it in my pocket/cache.
Sure enough, you ask for the 12th card. I quickly grab it from my pocket and show it to you. I speculate that the 16th card (we’ve moved into Diamonds by now) is what you’ll want next, and place that in my pocket while you look at #12.
This pattern works quite nicely until you’re about to ask for the 28th card. Thinking you’re about to ask for that card, which would be one of the Clubs, I put it in my pocket. You haven’t asked for it yet — so I haven’t told you that you can’t see it — it’s just my speculation that put it into my pocket.
But you don’t ask for it. You stop.
You’ve successfully placed something into my pocket/cache that you’re not supposed to see: the Two of Clubs.
You now use the method we discussed above to calculate what it is without needing to see it.
Performance
Both Meltdown and Spectre rely on performance optimization techniques used by the CPU. In one case, it leverages the CPU’s ability to say, “I know what you’re going to do next, so I’ll get it ready for you”, and the other takes advantage of the CPU’s ability to say, “I’m guessing you’re going to do this next, so I’ll have that ready for you just in case.”
As you might expect, mitigating these vulnerabilities will have an impact on performance. Some of the assumptions, techniques, and optimizations that the CPU can make will have to be avoided.
Speaking of speculation, estimates gauging the performance impact of avoiding these problems run wild – possibly making things anywhere from 5% to 30% slower. The reality is there is no single number: it depends on exactly how you use your computer and how your software was written.
Honestly, I expect most of us won’t notice a thing.
As long as we keep our software updated, of course.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!


Thanks very much for this easy to understand and non-sensational treatment of the security risks.
So, you’re not advising us to enable site isolation in Google Chrome then, Leo?
I was just about to do so, then I thought to consult your website, which has never failed to come up with helpful solutions in the past.
Apparently, the next update for Chrome will do just that for you.
I must admit that most of my “screen time” is on my iPad, but I still use my Win 10 laptop at least once or twice a week. All of these security issues reported above makes me think it is time to give up on my laptop, and simply use my wife’s new MacBook. I can’t even get my Win 10 to do updates. I live in a rural area and pay by the MB for internet, so I configured Win10 to be on a restricted connection, and it never seems to update. Getting way too complicated for this old guy.
Firefox and edge have already updated and chrome is suppose to update on the 25th of Jan. Just check the updates and see, they will tell you if the update is for these problems. Chrome may update early since Firefox already has.
This makes the Spectre and Meltdown threats so very clear to me. Thanks once again. I’ve a question about WindowsDefender. I use Norton360, which I keep updated, and use the quick scan daily and the complete scan every few days. I also keep my Windows Updates current. So, I disabled WindowsDefender because it seemed to slow my pc down and/or maybe be clashing with Norton360. Is what I do enough, or am I making a mistake by disabling Windows Defender?
Thanks for all you do.
What version of Windows? In Win 10 Defender is your anti-virus/malware tool, and you should have only one — EITHER Defender OR Norton. In Windows 7 and earlier Defender is only anti-spyware, and you need an anti-virus/anti-malware tool in addition.
Ralph, these problems are on all CPU’s Including intel, amd, arm, etc. even the iphone is affected along with all apple computers. The only thing not affected “YET” is android. That may just be that they haven’t found that android is affected. No need to panic, just get all updates to all OS’s and programs, there is not much else you can do.
Again it’s not “Android” that is or is not affected — it’s the CPU. As I understand it the CPUs used by many Android phones is.
As most of the Android devices run on affected CPU, your device is probably affected. Just hope that your device maker actually do offer OS updates.
The down side is that to many makers don’t bother to allow the OS to be updated, let alone offer those automatically.
Have you heard anything of the Windows 10 v1709 patch affecting the Trusted Platform Module (TPM)? I have a Dell Latitude E6510 and recently enabled the TPM in BIOS to support BitLocker. After doing so, I was able to see the TPM in TPM Management, and I encrypted my OS drive (along with 2 others).
After getting a Norton update to create the registry key and then installing the MS “2018-01” update (and rebooting), I was now required to enter the BitLocker Recovery Key for my OS drive (and only my OS drive) on every boot. I also noticed that I can no longer see my TPM in TPM Management . I tried recreating the recovery key for my OS drive, but I was still required to enter the BitLocker Recovery Key for my OS drive (and only my OS drive) on every boot. I finally decrypted my OS drive. Any assistance you can provide in this area would be greatly appreciated!
A number of experts have claimed, you should avoid installing the recent KB4056892 in WinUpd, as it may cause additional trouble related to processor drivers, awaiting updates/fixes in their turn.
I have set this update on hold for the next 35 days (Windows 10 Pro).
What will your advice be in this matter?
Since the update problem affects only a few (those with certain AMD chip configurations as I understand I) I recommend instead a full backup and then taking the update. If you encounter problems (which most people won’t) restore the backup and wait for updates addressing this issue.
Thanks for taking time to respond.
It has been confirmed, infected machines are unable to boot. I cannot see how a backup kan restore anything if this happens.
Anybody for a good suggestion?
Restoring from a backup bypasses all malware on your system. To restore a system image backup backup you first boot int the OS from a bootable optical disc or USB flash drive, run the restore from and reboot. The result is a restored bootable system. It would restore your system to a state exactly as it was before the malware installed itself.
Thanks, very good tip, I will keep this in mind, should I ever experience such a situation.
You boot from your rescue media, and restore the backup image you created prior to the update. Thus your machine is restored to the state it was in before you took the update.
It is not “infected Machines” that cannot boot. It’s is the KB4056892 itself that is causing the problem for some machines (PCs). Before one can install this update, it is well-advised to make sure that you have the following registry key with its values in the right pane:
– Registry key: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat.
– Values in right pane for QualityCompact: Value Name=”cadca5fe-87d3-4b96-b7fb-a231484277cc” Type=”REG_DWORD” Data=”0x00000000
If one doesn’t have the aforementioned key & values, MS won’t let you install the update because doing so will cause the PC not to boot or have BSOD. Lastly , to have this key & values, your A-V software vendor has to issue an update. That’s what most like Avast, Norton, ESET, have already done. Even with this registry key (QualityCompact)& values, some users couldn’t install the update. They had to completely uninstall their third-party A-V software in order to do just that. For others still having difficulty in installing the update, the best thing they can do for now is just to pause Windows Update (Windows 10 pro version) or put themselves on “metered connections” (Windows 10 Home version)
Excellent explanation! Thank you!
Rhetorical questions: How many fatal security flaws do we have on our devices? Could we be really safe (even with VPNs/Tor, anti-virus protection, etc.) while connected to the Internet?
I’m sure there are many, but if no one knows about them (and I do mean NO ONE) then they’re not really an issue, are they? Once they’re discovered and exploited then patches are made available to fix ’em (and scanners updated to catch the exploits).
Here we go again. Last week the world of PCs was wonderful. Today all hell is breaking loose. These CPU vulnerabilities have been there for 20 years or more. The CPU processing techniques identified as vulnerable are taught in schools. What’s interesting is that apparently these issues were recently “discovered” nearly concurrently by several different research teams. Given the way these CPU vulnerabilities can be exploited (see paper written by original researchers, Paul Kocher, et al) the probability of your PC being targeted and you actually losing critical personal information is very small. In this case I agree with what Leo often says: You (we) are not that interesting or important for anyone to bother with us. For a hacker, it would be more profitable, simpler and quicker to rob your house than to mount an effort to hack your PC with these methods.
Here’s a free tool from Steve Gibson’s GRC to check your machine for Spectre and Meltdown vulnerabilities.
https://www.grc.com/inspectre.htm