As I understand this problem is actually a pretty serious issue – or at least it could become one.
The real problem is that there’s no work-around other than not using USB for one of the things that it was intended to be used for: easy portability between machines.
Right now I’m honestly not quite certain how concerned we need to be, but I’m not panicking.
USB devices as small computers
To understand what this vulnerability is all about we need to first understand something that isn’t at all obvious about USB devices: many of them are actually small computers unto themselves.
This applies to any USB device. It really doesn’t matter if the device itself appears to be smart and complex – like, say, a printer – or as simple as a USB memory stick. It’s possible that inside that device is a small micro controller running software (more correctly referred to as “firmware”) that is performing the tasks of interacting with the USB interface and performing the functions that the USB device performs.
We might normally consider a USB device to be conceptually like this:
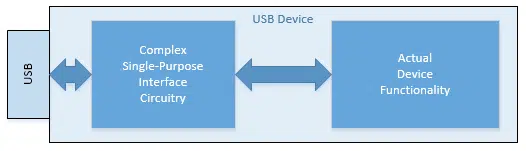
In this example there is hardwired single-purpose circuitry that’s designed to handle the USB interface on one side, and the hardware that implements whatever the device’s functionality might be on the other. That way the electronics behind the functionality can focus on whatever that might be, whereas the interface circuitry handles the “translation” to the USB interface.
The problem, of course, is that this interface circuitry is both complex and single-purpose. It can only interface to this specific device’s functionality. If you want to make a new device or change the device’s operation in any way, you need to build a completely new device with new circuitry.
That’s where micro-controllers come in:
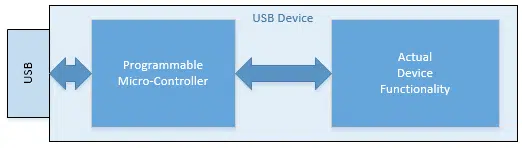
On the surface you might think that using a multi-purpose micro-controller might be overkill for many of these tasks – and you’d be quite right. But the irony is that it’s often much cheaper to build one micro-controller device and use it in hundreds of different USB applications than it is to build hundreds of different sets of dedicated interface circuitry.
The net result is that using a programmable micro-controller can be quite common. There could be one in your USB memory stick, your USB mouse, your USB keyboard … your USB anything.
Or not.
Programmable means re-programmable
And this is where things get interesting.
The issue that many are calling a design flaw in USB – even giving it the catchy name “Bad USB” – is that these micro-controllers, if present, can be reprogrammed.
More specifically, they can be reprogrammed to perform malicious acts.
For example:
- any USB device could suddenly decide to “look like” a keyboard, and start entering commands to your computer to install malware.
- any USB device could suddenly decide to “look like” a network card and redirect your network activity to malicious sites, or once again cause malware to be downloaded to your computer.
- the list goes on…
But wait! It gets worse
On top of what a maliciously programmed USB device could do is the fact that its malicious alteration would be undetectable.
If you receive a USB device that has been compromised, there’s simply no way to tell that that’s the case. Anti-malware tools don’t scan for it, and of course the USB devices themselves would be reprogrammed to lie about their condition to any kind of security probe.
And finally, the root of the flaw is that there are no safeguards built into the system to prevent USB devices with micro-controllers from being maliciously reprogrammed, or otherwise detect that it’s happened.
None.
How big a deal is this really?
We simply don’t know yet how big an issue this is.
There have been no reports of this flaw being exploited in the wild. None.
That doesn’t mean that there couldn’t be, or that there may be soon now that the information is out.
The problem is that exploiting it may, or may not, be worthwhile. To be useful or valuable to hackers it actually requires several things to be the case:
- A large number of USB devices use micro-controllers (we don’t know)
- A large number of those USB devices use the same micro-controllers, or micro-controllers that are reprogrammed the same way (we don’t know how many micro-controller types there might be)
- Those micro-controllers have enough reprogrammable memory to contain the additional malicious instructions to perform the malicious activity (we don’t know how much capacity or capability these micro-controllers might have)
It also relies on the existence of re-programming software; either in the form of infected PCs, or at some central location before entering general use.
Right now, to me, it seems like that’s a lot to have to happen for this to become a big issue. Based on what we know today I’m not terribly concerned.
Yet.
Help keep it going by becoming a Patron.
Protection
Protection is simultaneously excruciatingly simple and annoying.
Only get USB devices from trusted sources, and don’t share them.
On one hand, for things like mice, keyboards, printers and the like, it’s not that annoying. You buy it, you install it and you use it. There’s no real “sharing” involved.
USB memory sticks, the focus of much of the current press about the issue, are another story. Sharing is what they’re used for. They’re the floppy disks of data transfer today.
And as long as you use them on only trusted machines, you remain safe. But plug them into a computer you don’t know – like say a public computer – then theoretically all bets are off. That public computer could have malware that knows how to reprogram the micro-controller in your memory stick. What you get back might well be compromised.
And the same applies to all USB devices – including phones and cameras.
What would Leo do?
If you know me at all, you’ll know one thing I’m not doing is panicking.
In fact, I’m not doing much of anything. I don’t regularly use USB devices with computers I’m uncertain of, so there’s little for me to change.
Even if I did, today I would probably not even change those habits. At least not until there was more information, and perhaps more confirmation of this flaw actually being exploited in the wild, since right now I don’t expect it to be particularly common.
But from now on I will be on the look out for new USB devices that incorporate some sort of safety measures that prevent random reprogramming.

Re: “Is USB safe”
The reasons stated during this conversation are exactly why the US Military has banned them or at least from using them from outside sources. Some completely innocuos e-mail or website or even a game could contain a bug that could bring down a our security or nation.
Again, you’re talking about the content of a USB device, which is bad enough, but is NOT what this issue is about. A completely empty flash drive could contain malware.
Another good timely article. Thanks.
I believe Stuxnet counts as exploiting a USB memory stick as an attack method in the wild, even without modifying the firmware. Yet, you are correct, the flaw of being able to reprogram the USB firmware still hasn’t been seen in the wild as an attack. Stuxnet does illustrate how the way we trust and use USB memory sticks makes systems vulnerable.
Having “Write Once” firmware in USB would be helpful but enforcing and ensuring such was done for a particular device and remained unmodified would be difficult. Might be going towards having a class of secure USB devices that are digitally signed and verified. Kickstarter anyone?
Couldn’t the “good guys” also reprogram these USB devices so they couldn’t be sabotaged? If that is possible maybe programs could be initiated where you exchange a hackable device for an unhackable device for a fee if necessary. Maybe the necessary fee would help you decide to update or replace.
Could DBAN be adapted to wipe out / format a USB stick?
Probably not, but using any wipe utility with a wipe once option should be enough to completely wipe the USB drive. CCleaner has this option.
CCleaner – Windows Cleaning Tool
Again that wipes only the disk contents of the USB device. It does not affect the firmware that is vulnerable.
I was just responding to the question. It didn’t mention anything about protecting against any possible exploit of that vulnerability. I didn’t associate the question with the context of the article.
Yes, of course, but not the firmware portion that’s currently the topic of discussion.
I have McAfee Total Protection installed on my desktop – every time I plug in a USB drive, the McAfee provides an alert: “Removable Media Drive Detected”. I must then affirmatively indicate whether the drive should be scanned or not (McAfee allows the user to choose) before I access the data on the drive. This seems to be a pretty good defense against introducing a compromised USB drive to my computer.
The firmware that this article is about will not be scanned, so there’s no protection in this scenario.
I have an old USB drive (512 MB) that has a locking switch on it to turn it into a read only device. I’ve used it many times to disinfect either suspected or known virus laden computers. That type of functionality would help with using a USB drive on an unknown computer, but it does rely on someone manually setting and checking the switch before inserting it in the computer.
Would it? The contents of the drive are protected by the read only switch, but does that protect the controller? I think that’s an unknown factor.
If we’re going to add a switch, I’d want it to. 🙂
I really wish more (i.e. all) USB flash drives had this switch.
I have one such USB drive. The problem is that the switch just don’t work at all. You can write to it no mather in whitch position the switch is set.
Also, I’m not sure that it can protect accessing the frimware, if there is a programable one, and reprogramm it.
How about this solution? When you buy the USB device that is reprogrammable, the original firmware and a device to load that firmware on the USB must accompany it. Any time the USB device has been attached and removed from another computer, reprogram the USB with the original firmware before connecting it back to your computer.
And what about the frimware of the USB controller of the computer itself. A BadUSB can probably reprogramm that one to. In fact, it would be it’s PRIME target !
The proof of concept successfully infected the USB controller of a few computers of various brands, including Macs. It’s totaly OS independent. That controller, in turn, infected the frimware of any USB device connected to it, keyboards, mice, printers, external drives, USB sticks, game pads, smart phones, you name it.
It seems to me that for now, until we know more, practicing safe computing, like Leo has been preaching for years, is probably the best defense. In order for your USB device to get reprogrammed, something (for example, malware) needs to be let into your computer to be able to get to the USB device. If you reduce the risk of allowing bad stuff in, you automatically reduce the risk of having your USB device reprogrammed.
The real take-away here is to not insert “gift” or “found” USB devices – you don’t know what they might carry.
Well, regardless, I am putting money down that the price of “fixed” USB drives is going to go up, possibly dramatically. Eh, I’m a pessimist when it comes to computers and it has saved my behundy many a time!
Leo, this article is timely and very recently published. But it would be a good idea to “timestamp” every article with a date, so if we search your articles, we know the general context.
Although dated reader comments offer a clue, it would be even more helpful to have a date on the article, itself.
Every Ask Leo! article has a time stamp. It’s located just under the Read more: list of articles and just above the article tags.
There appears to be only one way to prevent this problem, use only USB devices without programmable controllers. That way if the manufacturer of the USB device is trusted, no problem. Maybe all USB devices, at least USB memory sticks, should be labeled as to what kind of controller they include.
Another thought. Aren’t most current electronic devices manufactured in China? Should we trust anything so dangerous coming from China?
I bet the Iranians are very careful of what they connect to their computers.
Would something like Panda USB Vaccine prevent this problem?
It appears not. That deals with traditional autorun issues and malware stored on USB devices normally. It doesn’t appear to deal with firmware at all. (And it’s unclear that any anti-malware tool could.)
AV programs have no way of detecting if this vulnerability has ben exploited.
It seems to me that if they made the microcontroller so that its firmware could either only be programmed once, at the time of manufacture (safest), or at least so reprogramming it required access to contacts not accessible via the USB contacts, with tamper-evident packaging, this issue would largely not exist.
PROM (Programable Read Only Memory), whitch date back from the 70’s, cost more than flash ROM.
But, having flash ROM demanding +12V, or even -12V, to be programmed could be looked at. The USB connector have only +5V.
Well it looks as if it’s starting…i.e., fear of the unknown…
either you take them as they are and hope no problems will arise and ‘then’ handle them on a case by case basis OR,
have industry start doing something about it now B4 it becomes a problem and that would be somewhat of a re-tooling
process and obviously, increase the price per unit/byte size and have industry create a ‘Standard’ for the safety of USB usage.
Couldn’t the manufacturers make it read only by shorting pins out with some solder(a permanent write protect switch) in the factory, after it was assembled. or have two ends, one for reading and one for writing, that was capped off and sealed, the customer would never see the writable side. Yes, this would make the devices more expensive and bigger, but maybe worth it.
I was watching a video on youtube and the guy said he can put usb in someones pc pretending he needs some files and in the background usb would download all the passswords, cookies, browser history etc…of that pc. Can every usb do that or this guy enable it itself by reprogramming or something?
It would only be done if the USB has software on it to perform that function. So this guy programmed something. Also, he’s getting passwords from people who save them in their browser – never a good idea. I’d like to point you at this article: https://askleo.com/how-safe-is-it-to-let-my-browser-save-my-passwords/
Thank you for replying, you guys rock. So usb that you buy at stores dont have such software on it unless you do some programming yourself? If i understood corectlly.
All standard USBs come with no user software, especially not hacking software which would be malware.
That is correct.
A malicious USB device can indeed do this.
Is there any way of scanning a USB device’s firmware from the computer side?
And — here’s an idea! — If USB firmware is rewritable, then why not have the host computer’s operating system rewrite that firmware when it’s first plugged in… not just to something innocuous, but to something actually tailor-written to work well with it? 😮
That last point is infeasible — the PC would need to know the details of each and every possible USB device. The whole point of firmware on the device is to prevent the target computers from ever needing to know that level of specificity.
As for the first part — it could be done, and checked, but it would require a design change to all of USB. Again, almost by definition USB devices are things that just work without the computer needing to know how.