If it’s malware, it’s not good.

Worried? Probably.
This is exactly the scenario security folks warn against so strenuously: running or opening something you shouldn’t and bypassing warnings from your security software.
Let’s look at your options.

Running what you shouldn't
If you run something you shouldn’t, the only 100% safe fix is a full reset or a complete restore from a backup image. Scans may show the computer is clean, but malware can hide. If the risk feels manageable, run complete scans with two tools (like Windows Security and Malwarebytes). Then watch for odd behavior.
The pedantic answer
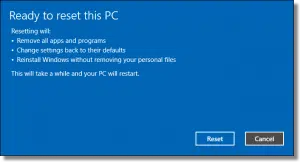
If what you ran could be malware, there’s only one true solution to the situation: a factory reset. (There’s one more answer that I’ll share below, but it involves preparation.) Back up your machine completely so things can be recovered as needed later, and then reinstall Windows from scratch.
It’s brutal, I know.
The problem is that once you allow it to run on your computer, malware can do anything — even hide itself so your security software doesn’t see it. In a real sense, once malware is on your computer, it’s not your machine anymore.
The only way to be completely, 100% certain that the malware is removed (if, indeed, it was malware) is to erase everything and reinstall.
Help keep it going by becoming a Patron.
Risk management
To be clear, the answer above is what most would call The One True Answer. When in doubt, that’s what you should do.
However, depending on what you know about what was run and the amount of risk you’re willing to take, we might be able to start with something less daunting than a factory reset.
Where did it come from?
Consider where the download came from. If it’s from a site you know or at least recognize, that’s less risky than what the original questioner experienced: being redirected to a URL you’ve never heard of.
The same thinking applies to an emailed attachment. If you’re certain you know and trust the sender, that’s less risky than having opened an attachment from someone you’ve never heard from before.
What did the security software say?
It’s usually a bad sign if your security software complains when you download something or run something.
I say usually because the specific wording of the security software’s complaint matters when assessing risk.
For example, Windows Defender SmartScreen might object to a download because it doesn’t recognize the application or its digital signature. That doesn’t necessarily mean the application is malware; sometimes we ignore its advice when downloading something we know is safe. In situations like this, it’s a data point.
However, if your security software tells you something along the lines of “This is malware!”, that’s a clear sign that something is amiss. Think twice about bypassing that warning.
The less brutal but riskier approach
In this situation, the risk is never zero. But if the risk seems low — perhaps you know where the download came from and your security software said nothing (or something amounting to a simple warning) — then you might consider sidestepping the nuclear option.
That looks like this.
- Run a full scan (not a “quick scan”, if that’s an option) with your existing security software of all drives connected to your system when the questionable program was run.
- Download a second security package — the free version of MalwareBytes is what I recommend as a good number two — and run full scans with it as well.
If both come up clean, proceed with caution. Watch for unexpected behavior, but you might have dodged a bullet.
If either scan detects malware, then what happens depends on the tool’s ability to remove and/or quarantine the malware. If it’s successfully dealt with, you may have dodged a bullet again. If the scans have difficulty removing the malware, then the nuclear option may be your only path to recovery.
If all this causes you concern, that reset might be worth the effort anyway. Back up your machine first (to preserve data). Reinstalling will help you sleep at night.
Learn from the experience
There’s no shame here; we’ve all made these kinds of mistakes at least once. I know I have1. So let’s focus on making sure that it remains a one-time thing.
Based on the description, I’d encourage you to:
- Slow down. The story sounds like you were in a hurry. That, as you’ve now seen, is a recipe for making mistakes.
- Pay attention to the URL, particularly if it’s redirected to a site you’ve never seen before. Your browser’s address bar is an important resource, not just for telling your browser where to go, but also for seeing where exactly you’ve been taken.
- Don’t run. Obviously, the point of most downloads is to run them. My advice here boils down to another variation of “slow down”: once the file is downloaded, take a breath and ask yourself whether you believe this download is safe. If you’re not sure, don’t run it.
- Listen to your security software. If it pops up, there’s a reason. It’s not something to panic over, but it is something to read (slowly) and understand before you proceed.
That other answer
You can avoid a factory reset by doing one thing: restoring your machine to the most recent full image backup taken before you downloaded and ran the questionable software. It’s the ultimate undo. It restores your machine to the state it was in before anything happened…
…without spending hours reinstalling and recovering everything.
The catch?
You need to be backing up regularly. Specifically, you need to be taking full image backups regularly. I recommend a process that gets you daily snapshots2.
Do this
Now you have a plan for what to do when you suspect malware may have reached your computer. But the first step is to employ caution so you’ll never need to use that plan.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and safety tips in your inbox every week.
Podcast audio
Footnotes & References
1: A long time ago.
2: Specifically, monthly full image backups with daily incremental backups.



“The same thinking applies to an emailed attachment. If you’re certain you know and trust the sender, that’s less risky than having opened an attachment from someone you’ve never heard from before.”
Yes, but still be careful. Make sure you were expecting that attachment. Hackers can easily create an email to look like it was from your friend. Call them before opening the attachment if you weren’t expecting that email.
There are some warnings from Microsoft, for example that say, “Windows Defender SmartScreen prevented an unrecognized app from starting. Running this app might put your PC at risk.”
or “SmartScreen can’t be reached right now.”
or “The app you’re trying to install isn’t a Microsoft-verified app.”
If you know the source of what you are installing, it’s usually safe to ignore those messages because they aren’t warning of malware, they are just essentially saying that software hasn’t ben verified by MS and hasn’t been whitelisted. It’s Microsoft basically saying “We don’t know this software, so we’re warning you.“
Under the topic of “The less brutal but riskier approach”, there are a few other checks you can make, assuming you have previously prepared for this scenario. The first thing you do is to disconnect from the internet.
Scan all your running processes (in Task Manager) and make sure you have an idea of each process is. Research any unrecognized entries. Of course, being able to identify your processes assumes you would have previously taken a snapshot of the running processes when you believed your machine was clean (such as after first image installation). Do a similar check for startup processes. Do a similar check of running services.
Then explore the folders and files in C:\Users\\AppData\Roaming and Local. Look for entries that you don’t recognize. Of course, there are many more places you can check, but that takes patience and knowledge.
If you have the tools, you can connect to the internet and check for connections and network traffic. This is an involved and difficult process.
You’d think that malware scanners would do all this automatically, but they don’t (because there are almost infinite variations of configurations). On the other hand malware scanners check for other signs of malware that you can’t do manually.
You can also run these Windows utilities to check system integrity: scf, sigverif, DISM.
Unfortunately, these are mostly placebos and won’t actually fix a broken or infected system.
Let’s face it, it’s a lot easier and faster to install a clean image (but there are caveats to that also). There is a side benefit to going through this type of investigation of your machine. You’ll discover programs, files and folders that you didn’t know existed. You’ll discover remnants of software that you thought you deleted … and data and log files with your information. You’ll discover Microsoft processes with obvious names that tell you they are watching your every move.
“Look for entries that you don’t recognize.”
When I look at the Task Manager or AppData, I see dozens of entries I don’t recognize. I can’t speak for Leo, but I’ll bet thare are dozens of entries he doesn’t recognize.
The topic is titled: “I opened something I shouldn’t have…” What is meant by “opened?” For instance, I sometimes get emails from a sender I don’t recognize with a subject line that is ambiguous. I believe (and this is where I need clarification) that simply opening the email to see what, indeed, it says, is not a risk in itself, so long as I don’t click on a contained link or otherwise activate something contained in the email. Am I correct in this belief, or is the act of merely opening the email what is being referred to in the discussion?
In general, it’s safe. More: Can I Get Malware From Opening an Email?