It’s both a buzzword and a critical privacy component.

End-to-end encryption is a term we hear often. Whether it be the latest claims from a messaging app, or the kerfuffle about how a particular conversation was leaked because it wasn’t really end-to-end encrypted, the concept gets a lot of press.
Much of that press exposes how easy it is to either a) confuse, b) mislead, or c) both around this topic.
Let’s look at what end-to-end encryption means. Spoiler: there’s more than one definition.

End-to-end encryption
End-to-end encryption means that only the sender and receiver — and no one in between — can read a message. Period. Some apps claim to use it but don’t. If the messaging service can see your messages, it’s not truly secure. Also, if your device isn’t secure, the encryption won’t matter.
Encryption
What is end-to-end encryption? Let’s start with a high-level definition of encryption. There are two types.
Basic or symmetric encryption is pretty straightforward.
- Take some data you want to protect.
- Choose a large number.
- Scramble the data using that number and some very fancy math.
The result is scrambled data that can’t1 be unscrambled without knowing the large number. That large number is what you and I might call a password, passphrase, or key. They all boil down to numbers inside your computer. Symmetric refers to the fact that you use the same large number to decrypt as you do to encrypt. Knowing that large number gets you access to the data.
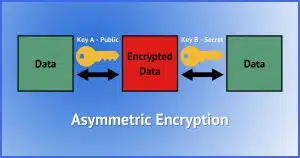
Asymmetric, encryption — also called “public key encryption” in some usages — refers to using a pair of keys: one to encrypt the data and another to decrypt it. Each key is just another large number, but they share a special relationship: while either can be used to encrypt, the data encrypted by one can be decrypted only by the other2. That makes things slightly more complicated.
- Using even fancier math, generate a pair of keys.
- Take some data you want to protect.
- Scramble the data using one of the two keys.
Once again, the result is scrambled data that can’t be unscrambled, this time without knowing the other key. Knowing the other key gives you access to the data.
Help keep it going by becoming a Patron.
End-to-end encryption type 1
The proper and pedantic definition of end-to-end encryption is that only the individuals at either end of the communication can view the communication.

A simple example: I encrypt a file with a password and then share that file and password with you. Only you know the password, so in theory, only you can decrypt the file. This requires that I somehow tell you the password first, ideally via a different communication path so that the password isn’t right there with the encrypted data for anyone to see.
A more common scenario for messaging is that I (or the tools we use) share one of a pair of asymmetric encryption keys with you and encrypt a message using the other. Then only you can decrypt what I send to you. This tends to be more common for communications tools because the tools can handle all this transparently without our having to decide on or manually share a password.
In either case, it doesn’t matter how the message gets from point A to point B; it’s impossible to examine along the way. It remains securely encrypted from one end of the conversation (me) to the other end (you).
There’s one risk: key compromise. If the key I give you — either the password, in the first example, or the first key of a pair, in the second — somehow lands in the hands of someone else, then they, too, can decrypt and examine the message I sent to you.
“End-to-end” encryption type 2
I put it in quotes because this isn’t really end-to-end encryption. The problem is that some messaging services claim it is.
Many services act as an intermediary for your communications. Rather than your message going from you directly to the person you’re talking to, it goes to the service, which relays it to you.

Either of two approaches may happen here.
- The message you send is encrypted and sent to the service, where it is relayed directly to the destination.
- The message you send is encrypted and sent to the service, where it is decrypted, re-encrypted, and relayed on to the destination.
#1 remains true end-to-end encryption. #2 is not.
Messaging services may claim that the second is still end-to-end encryption because it never travels across the internet in unencrypted form. It’s always encrypted and is thus safe from snooping… except from the service itself.
There are valid reasons to use the second approach. For example, group chats are extremely complex to set up fully end-to-end encrypted (not impossible, just difficult). By using the second style by default, the messaging app only needs to manage its encrypted connection with the service rather than trying to manage an entire mesh of encrypted communications.
As you might expect, some communications services are less than clear about which approach they use.
Why it matters
Honestly, for most of us, it doesn’t matter. We and our messages are not that interesting.
But if you are “interesting”, or even think you are, here’s the risk: you’re trusting both the app and the intermediary. Specifically:
- You’re trusting that the intermediary isn’t examining your data for reasons of their own.
- You’re trusting that the intermediary isn’t handing over your information to third parties.
- You’re trusting that the intermediary isn’t handing over your information to the government.

You get the idea. If the intermediary has access to your unencrypted conversation, you’re trusting that they won’t abuse it.
Even if they are trustworthy, though, they may be required to respond to government requests. Since they have access to the unencrypted conversations, they’re able, and perhaps even required, to do so.
If, on the other hand, the conversation is truly end-to-end encrypted, the intermediary is only passing on encrypted data they can’t themselves decrypt. They don’t have access to your conversations and thus have nothing to hand over, even when requested.
The fly in the encryption ointment
As many people seem eager to point out, end-to-end encryption is not absolute security.
It means no one can intercept your communications as they travel across the internet from your device to whomever you’re talking to. Intercepted data is only so much noise that can’t be understood if it’s truly end-to-end encrypted. That’s great, but…

That leaves your devices as the next point of vulnerability. If your device is compromised3, then even though a message might be securely transmitted to or from that device, while on the device it can be captured. You have to be able to see or type it — that’s the point, of course — but while you see or type it malware could be doing things like capturing your keystrokes or taking screenshots of the messages.
That has little to do with end-to-end encryption. It’s just important not to assume that end-to-end encryption is all you need. You must keep your device secure as well.4
Do this
Like I said: for most folks, this is not something you need to worry about. It’s interesting, but not something you need to act on.
However, if you are one of those “interesting” people — a government gadfly, an investigative reporter, a political organizer, or similar — then understanding how best to communicate is critical. In some cases, it can even be a matter of life and death. Visit the EFF’s Surveillance Self-Defense site for guides on the tools and behaviors you need to consider for your specific situation.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: “Can’t” is technically wrong. More accurate is “Can’t be unscrambled in a reasonable amount of time using current technologies”. Today’s encryption would take hundreds of years at a minimum to be unscrambled as long as a suitably large number was chosen (i.e., you picked a strong password).
2: Literally. Data encrypted by one key in a key pair cannot be decrypted by that same key. The other key in the pair is required to decrypt. As I said, it’s very fancy math.
3: Though I don’t subscribe to this way of thinking, some believe that all devices are compromised due to untrustworthy operating systems, vendors, and manufacturers.
4: And, of course, avoid adding the wrong people to your chats.




Whatsapp offers true (maybe) end-to-end encryption, but they collect metadata (a log of all your calls and messages to whom and when) and share them with other Meta (Zuckerberg’s) products. That’s fine for chatting or talking to family and friends, but could be a serious risk if you are discussing political things as they can tell a lot about you from who you communicate with.
This end to end encryption Causes me to lose my pm’s on Facebook on a desktop.
When I close my browser, it normally clears tracking history.
How can I stop that?
Clearing your browser history, specifically clearing cookies and other site data, appears to be the problem.
“some believe that all devices are compromised”
I have to say I am one of those people. Last Sunday I sent two emails to a friend on email addresses we have been using for years. He was concerned about claims that the current U.S. administration snoops on social media, messaging apps etc. I replied, writing about President Obama demanding access to Lavabit’s servers. Both emails were returned as spam. A third email I sent just said my emails about the President Obama/Lavabit incident were returned; that email was returned as spam. The next email where I sent an article link, adding that I hoped he was well, and his reply that he was off to a spa, went through with no trouble.
You will alread have read about our Home Secretary demanded access to all iCloud storage of every person in the world.
I have never trusted governments or so called big tech.