These days, there’s more on your computer network than your computer.
It’s definitely a concern. Two things are excruciatingly clear:
- We’re connecting more and more non-traditional devices to the internet, or Internet of Things (IoT).
- Security on those devices is, apparently, abysmal.
So how do you protect yourself from being part of the problem? Well, as with so many things, there’s no clear or absolute answer.
But I do have a couple of ideas.
Become a Patron of Ask Leo! and go ad-free!

IoT Security (or lack thereof)
With so many non-traditional items being rushed to market and connected to the internet, it’s no surprise that security is often an afterthought. The best you can do is make sure to change default passwords for those devices that have them. While IoT devices can be incredibly convenient, make sure that you’re making a conscious, conscientious choice when adding them to your home network.
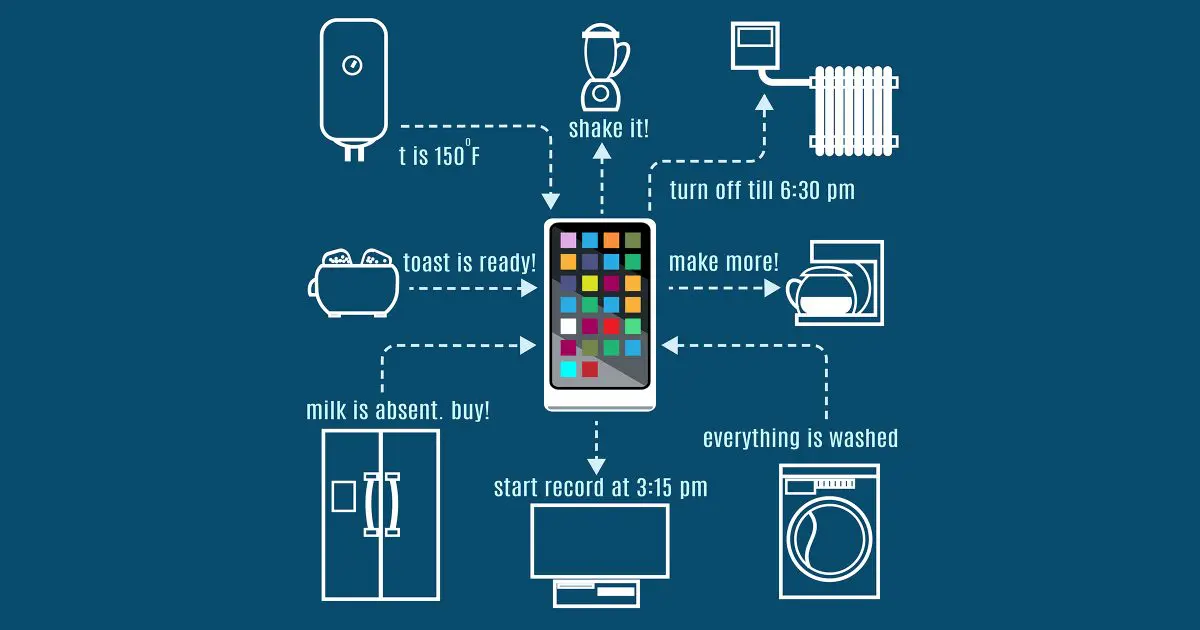
IoT: the Internet of Things
The IoT is nothing special, really. It’s not another network, it’s not something super-secret or super complex. In fact, you probably already have devices that are part of it.
All “the internet of things” really refers to is non-traditional devices connected to the internet. And by “non-traditional”, I mean anything you wouldn’t think of as a computer.
Your PC, laptop, smartphone, and tablet are all things we conceptualize as computers. Even your printers and gaming consoles are easily understood to be computers on the inside. Naturally, your router and other networking devices are also what we’d call “traditional” things connected to the internet.
On the other hand, so-called “smart” TVs, security cameras, light switches, light bulbs, refrigerators, washing machines, and perhaps even toasters1 are being connected to the internet for a variety of purposes. Whether you think it’s the best thing since remotely-controlled sliced bread or the silliest thing you’ve ever heard, the internet is being used for all sorts of things we’d never considered before.
That whole “never considered” thing is actually part of the problem.
The (lack of) security of things
Who would want to hack a light bulb?
That appears to be exactly the kind of thing that appears to be happening in distributed denial of service (DDOS) attacks. This occurs when of a bunch of infected computers are all instructed to access a specific website or service simultaneously, crashing it.
Hackers aren’t interested in playing with your lighting. They are interested in using the tiny computer inside your light bulb (or other internet-connected smart devices) for their purposes elsewhere.
Computer in your light bulb?
Indeed. The easiest and cheapest way to make a device connect to the internet is through a general-purpose interface that is, for all intents and purposes, a computer. It may not run Windows (though it might be running Linux), and it may not have as many functions as your desktop, but it’s a computer nonetheless. The protocols used to connect to the internet, as well as interface with the device itself, are complex enough that a fair amount of computing power is required to make it happen.
And computing power is dirt cheap these days.
Sadly, security is not. Security requires forethought.
What we’re finding is that security is often an afterthought.
At best.
What can you do?
Being behind a router is the first step. The problem is, it’s a step most people have already taken — yet internet-connected devices are being hacked on a regular basis anyway.
The single most important step? Change the default password on every internet-connected device you own that has a password.
Apparently, a large number of hacks have been simply attackers discovering the device through some means and then being able to log in to the administration of the device because the owner never changed the default password.
In this case, it seems just about anything other than the default will cause attackers to move on, looking for a vulnerable device elsewhere. Use a strong password anyway, to future-proof yourself from the day when hackers get more aggressive. It’s very likely, for example, that devices do not have brute force log-in protection, and could allow an attacker to try to log in using every possible password.
What you can’t fix
What you can’t fix is bad design.2
There are so many ways these inexpensive internet-connected devices can communicate, there’s a near endless supply of things that could go wrong.
For example, many devices use unencrypted connections to reach out to the internet because https takes more work. That means it’s possible for hackers to see and perhaps intercept traffic to and from the devices behind your router. It’s possible that a single compromised device could expose other devices behind your router. Or it could mean nothing at all, depending on the device.
Unfortunately, aside from paying attention to news reports listing specific brands, devices, and models, there’s no practical way to know if your devices are involved.
Aside from disconnecting it from the internet, it’s almost impossible to know whether or not your refrigerator — or your toaster — is helping to take down websites.
What I do
I have more IoT devices now than when I first wrote this article.
Many devices fall into the category of “traditional” devices. Computers, laptops, mobile phones — even Amazon’s Echo — all qualify as more-or-less full-fledged computers.
The big addition for me has been light switches. It’s very (very) convenient to be able to say “Alexa, turn on the patio lights”, or even have Alexa manage a schedule for automatically turning lights on and off whether or not we’re home.
I do have so-called “smart” TVs, but it didn’t take long for me to feel they weren’t smart enough. Mostly in the interest of preserving internet bandwidth, I leave them disconnected. I notice no function or feature loss by using them without connectivity. The Roku streaming devices plugged into them have their own connectivity.
I do not have an internet-connected fridge or toaster.
What is frustrating
What’s particularly frustrating for internet technologists is that we’ve been here before.
All the lessons we’ve learned over the years from technologies like Bluetooth (originally very insecure), wireless keyboards, and even the Wi-Fi protocols we use every day have been, for the large part, ignored by the manufacturers of these new internet-connected devices. They opted for cheap and fast-to-market over keeping things secure.3
So we learn the lessons again.
We hope.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
Footnotes & References
1: One concept toaster gets the daily weather forecast from the internet and burns it onto your toast.
2: I was tempted to title this section “You can’t fix stupid”, but that’s not actually fair. Most of the decisions that have lead to this situation aren’t as much about stupidity as they are about time pressure, ignorance, and failing to learn the lessons of the past.
3: It’s actually a complex equation. Consumers don’t care about their refrigerator being secure, as long as it works. It’s a hard sell to convince consumers to pay extra or wait longer so their fridge can’t participate in the take-down of some random site on the internet.




I have changed the password to the router and the wi-fi connection is also password protected. I thought it also made sense to limit the number of DHCP connections to the number of devices I wanted connected to my router. Does that make sense? Does that give even a bit more protection? I figure that even if they can manage to figure out the wi-fi password, they still can’t get on my network because I haven’t made any space available. Make sense? Or am I just fooling myself?
As long as you’re always at 100% capacity … but even turning off one of your devices could free up a slot that someone could slide into. Personally: not worth the effort.
Okay I am not too informed on a lot of stuff you talk about…way beyond me but saying that How do you know or where are default passwords and how does one change them? it?
Do ZigBee chips cause these problems?
thank you
The default password is the original password that comes preset with the device. It is often found on the devices’ labels. As for how to change them, you would have to check with the manual which came with the device or download it from the device manufacturer’s website.
You have to check with the documentation for each specific device to see if it has a default password and what it might be.
Some of the problems are, especially with older devices :
Some devices may not have any password, and may not have the capacity to have any.
Some devices have hard coded passwords that you can’t change, like they are burned in ROM or PROM.
Many just don’t have the capacity to encrypt their transmissions.
Some will always accept any anonymous request over WI-FI.
How about putting the IoT devices on a separate subnet?
Ubiquiti ER-X router does this for $50 (need to add a wireless access-point.) So can DD-WRT and PfSense software.
Ward, that won’t make IoT devices any more secure. If an unsecured device can reach out to the Internet it can also be seen and hijacked from the Internet regardless of how many layers deep you bury it.
Another approach is the approach I take with my Internet enabled refrigerator. I turned the Internet connectivity off on that device. It’s just as easy for me to go up to my fridge and adjust the settings as it is to do it from my phone. And why would I want to change the temperature of my fridge when I’m not at home. Seriously, some IOT devices make sense. Not all do, and turning off any useless features is an easy way to prevent hacking of those devices.
Leo:
I’m a little confused (not an unusual state) concerning your IoT article. I thought that if an IoT device was behind your router, it couldn’t be hacked from the Internet; the same as your computer devices. Yes if the device “phones home” without using https, the traffic can be read but that shouldn’t mean the hacker can connect back to the device & the local network through the router or am I mistaken? If the Wi-Fi network is also secured with a good password, then someone shouldn’t be able to get to these devices by hacking into the local Wi-Fi network bypassing the router.
Is my thinking screwed up?
Basically, any communication that can be intercepted (like your non-https example) opens the device to having vulnerabilities exposed. There are a variety of ways that can happen. That’s one of the many reasons we keep saying “keep your software updated”, so that those vulnerabilities when discovered can be fixed. Unfortunately, IoT devices rarely have a mechanism for update, and these days come with an unfortunately disproportionate number of vulnerabilities.
The router supplied by my cable company links me to the internet. There is a password on the bottom label, looks random. Do I have to change it?
Do you HAVE to? Probably not. Would I? Probably. (Leave the sticker, because if you ever reset-to-factory this would probably be reset as well.)
… and take a picture of the sticker in case it falls off.
Leo, you wrote:
“…the decisions that have lead to this situation aren’t as much about stupidity as they are about time pressure, ignorance, and failing to learn the lessons of the past…”
Hmmm, that sounds pretty darn “stupid” to me…
“Those who fail to learn from history are doomed to repeat it.”
–George Santayana