Three approaches.

Sometimes encrypting a single file isn’t enough. Sometimes you want to encrypt all the files in a folder and its subfolders.
As you might imagine, there are several solutions, depending on your particular needs.
I’ll review some alternatives, as well as their pros and cons.

Encrypting a folder
Encrypting a folder keeps all its files safe from prying eyes. Windows Pro can do this with a simple right-click, VeraCrypt uses secure “containers,” and Cryptomator is great for cloud storage. Each has pros and cons, but all protect your data with encryption and a password.
Using Windows to encrypt files and folders
If you’re running Windows Pro Edition and your disk is formatted using NTFS (as most are these days), then Windows can encrypt your files and/or folders for you using EFS, or the Encrypting File System.
Right-click on the file or folder you want to encrypt — my example here is a folder called “Sensitive Documents” — and click on Properties.
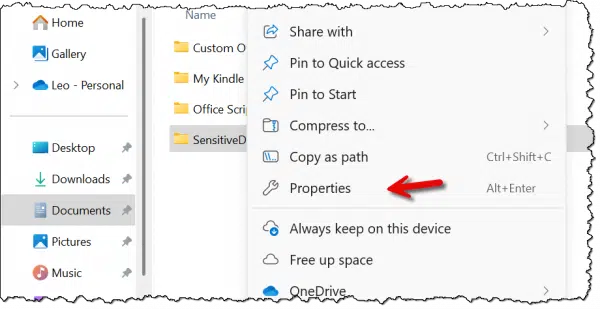
In the resulting dialog, on the General tab, click on Advanced.
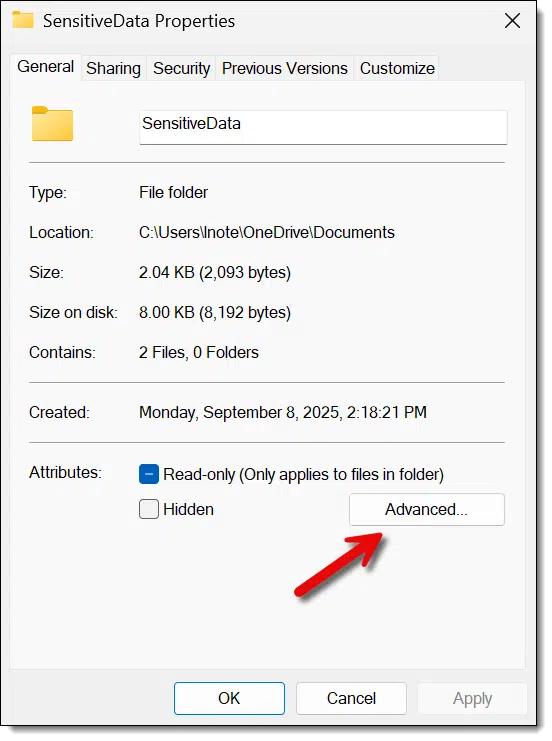
In the resulting Advanced Attributes dialog, make sure that “Encrypt contents to secure data” is checked.
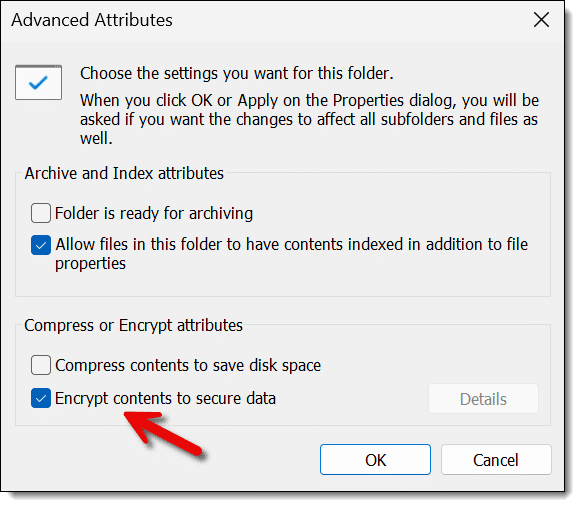
Click OK. You may be asked whether you want a single item or more than one item encrypted.
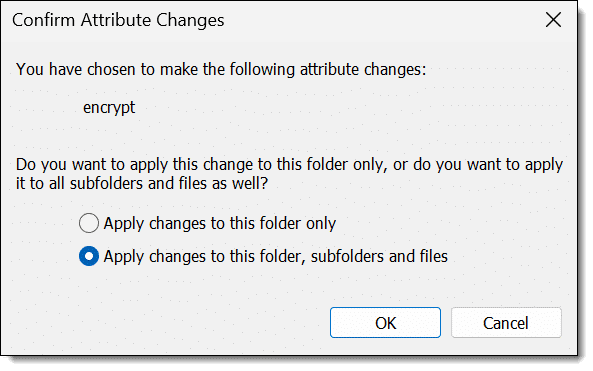
With folders, show above, the second option is to encrypt the folder and everything within it. When encrypting a file, the second option is to also encrypt the folder containing the file.

The choice is yours, depending on what you’re attempting to do. (I find encrypting a folder and everything within it the most straightforward choice.)
The good news: It’s simple, easy, and almost completely transparent to encrypt a folder. Your folder is encrypted, as are the files it contains. As long as you’re not logged in, anyone who steals or otherwise gains access to your hard drive cannot gain access to that folder.
The bad news: Anyone (including malware) who can access your computer while you’re logged in can access your files.
Help keep it going by becoming a Patron.
VeraCrypt

VeraCrypt is a successor to the once-popular TrueCrypt. It has a couple of different approaches to high-quality encryption, one of which we can use to encrypt a folder — or at least we can do something very similar.
You can use VeraCrypt to create an encrypted container secured with a passphrase. This is a single encrypted file kept on your computer’s hard drive. You then “mount” that file using VeraCrypt, supplying the passphrase to decrypt it. Once mounted, the unencrypted contents of that file appear as a separate drive — often called a virtual drive — on your system. Reading data from and writing data to that virtual drive transparently decrypts and encrypts the data stored in the container file. Once the drive is unmounted, the data is once again inaccessible without re-mounting the container and providing the passphrase.
The specific details are beyond the scope of this article, but as an example, you might create a container C:\Users\%username%\Documents\MySensitiveDocuments and give it a nice, secure passphrase. When you mount MySensitiveDocuments using VeraCrypt and type in the passphrase, you can then assign it a drive letter — I’ll use “S:” for this example. Now any program can read and write files and folders to drive “S:”, and when doing so, the data is stored inside the file MySensitiveDocuments in encrypted form. Once you unmount the container, drive S: disappears, and the data is no longer visible in unencrypted form.
Using VeraCrypt to manage an encrypted container in this way is very similar to having an encrypted folder.
The good news: VeraCrypt provides high-quality encryption and is available on multiple platforms. Containers created by VeraCrypt are not tied to your login, but are secured by a passphrase. The containers can be copied from machine to machine and opened anywhere. Once mounted, encryption and decryption are transparent to any program reading and writing data on the virtual drive.
The bad news: Containers are monolithic, meaning that regardless of how many files they contain, they are still a single container file. The container size is specified when you create it. The only way to move encrypted data from one place to another is to copy the entire container.
Cryptomator

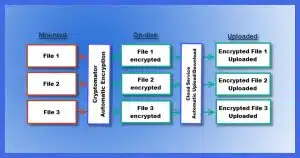
Cryptomator uses a model similar to VeraCrypt but is designed to work optimally with online/cloud services. Rather than storing everything in a single container, Cryptomator maintains individually encrypted files.
When you install and configure Cryptomator, you point it at an empty folder on your machine, which will contain your encrypted data, and specify a passphrase to use for encryption.
You mount that folder using Cryptomator and your chosen passphrase. Much like VeraCrypt, a virtual drive appears. Files and folders transparently written to and read from that virtual drive are encrypted and stored within the folder you originally specified. Once you unmount the folder, only the encrypted copies remain accessible.
The major difference between Cryptomator and VeraCrypt is that Cryptomator maintains the encrypted files and folders as individual files and folders rather than using a single, monolithic container. The article Cryptomator: Encryption for Your Cloud Storage goes into the differences in more detail.
The good news: Cryptomator provides high-quality encryption and is available on multiple platforms. It’s highly suited to storing encrypted data on online storage services. Like VeraCrypt, your data is protected by a passphrase and is not tied to your login. Once mounted, encryption and decryption are transparent to any program reading and writing data on the virtual drive.
The bad news: You cannot easily copy individual files encrypted using Cryptomator to other machines in encrypted form. The entire encrypted folder is designed to be replicated to other machines and cloud storage providers.
Do this
Normally, I’d make a recommendation as to what technology might be best. But this is a case where different tools solve the generic problem — how to encrypt a folder — in different ways that involve different trade-offs. You must evaluate those trade-offs for yourself and your needs.
What I can tell you is what I use myself: Cryptomator.
I don’t use operating-system encryption at the file or folder level. I use cloud storage heavily, and Cryptomator ensures that anything I consider even somewhat sensitive is stored securely encrypted.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.



Yet another way to encrypt files is to Zip them. All good Zip programs today — freeware included — makes secure AES encryption available. An added benefit is that all Zip programs (unless explicitly told not to) will compress your files before encrypting them, thereby greatly enhancing the encryption.
An even greater benefit is that Zip programs are both ubiquitous, and multiplatform. The file I compress & encrypyt with WinZip on our desktop computer running 64-bit Windows 7, decrypts abd decompresses perfectly using the program “B1 Free Archiver” on my Amazon Kindle Fire HD8, running a modified Android operating system… and vice-versa!
My ONLY reservation is a completely personal one: the use of AES gives me grave misgivings. Its ubiquitouness makes me nervous because every hacker and his uncle will be out to break it, and God help us if they succeed because then practically the whole (AES-using) world will be at their feet.
My own personal preference is for Twofish. It came a close second in the very same contest which gave us AES, but it is very much less commonly used — and is thus (think I) a far less likely target.
Good write up.
I’d disagree with the user comment that ZIP encryption is a good alternative. It USED to be IMO, but by todays standards it isn’t secure enough.
I have found online services that will for a nominal fee decrypt encrypted ZIP files.
What millennium are you from? 7Zip offers AES- 7Zip is a tiny quick download and should be in everone’s toolkit.256 encryption, some of the strongest encryption available to consumers. Windows can’t natively decrypt 256-AES. It would require the recipient to have 7Zip installed. In that case, it might be best to use .7z compression and encryption which is truly state of the art.
There is an open-source program called Paranoia Works that will either encrypt individual files or folders to a single file. If the encrypted files is renamed, it doesn’t matter because all of the original file/folder info is contained inside the encrypted file. It’s also cross-platform so you can send your encrypted files from your laptop to your phone, where you can decrypt them.
The bad (not limited to this particular app, but needs mentioning): There is no back door, so if you lose/misplace your password, you will NOT get your files decrypted.
That might be a good program, but ZIP files are ubiquitous and can be opened natively in Windows and other OSes. If an ecncrpted ZIP file is incompatible with the native ZIP decompressor, 7ZIP is well known and many people already have it.
With Windows Pro folder level encryption what happens if my CPU dies and I replace it? Does the encryption key die with the CPU?
If you mean literally the CPU chip, then nothing changes.
If you mean the computer (which includes CPU, motherboard, RAM, etc.), then you need the recovery key you saved when you enabled BitLocker.
Is encrpting a file the same as protecting the file with a password? If one forgets to log out one’s own PC and is hacked so that a hacker still can descript a folder, why encrypt any folder or file? In other words, if one’s PC is protected from hackers or malware by a router’s and OS’s firewalls, isn’t everything on the PC is safe? If a file is well protected, then this particular file is safe from hacker while all other files are not safe from hackers that has access to one’s PC. Is that right?
“Is encrpting a file the same as protecting the file with a password?” Yes and no.
If it’s ONLY a password (like, say, your Windows sign in), then as you say, hacking the account will gain access.
However if you encrypt separately, as outlined in the article, then the file remains encrypted and can only be decrypted by providing the encryption password.
Hello,
Thank you for your answer. I use Windows 11 Home Edition on my PC with SSD. I seem to remember reading somewhere on the Internet that all files on the hard drive is encrypted. I don’t remember I have ever been prompted by Windows 11 (ie. Microsoft Account) to create an encryption password. Can I encrypt a folder on my PC that has the home edition OS?
Thanks in advance for your answer!
Sounds like you’re thinking of Bitlocker: How Do I Know If My Hard Disk Is BitLocker-Encrypted?